How CryptoFBI manifests
|
The CryptoFBI is downloaded and run on your PC via a malware belonging to the family Trojan.Win32.Sathurbot.
Il Trojan.Win32.Sathurbot is loaded when the computer starts by grabbing the Windows shell, and more precisely using the registry key:
[HKEY_CLASSES_ROOT\Drive\ShellEx\FolderExtensions\{stringCLSID}]
where {stringCLSID} matches to the key:
[HKEY_CURRENT_USER\Software\Classes\CLSID\{stringCLSID}]
in its interior it contains the sub-key "InprocServer32" where the path of the .DLL file is present containing the Trojan.Win32.Sathurbot
%allusersprofile%\{random_stringCLSID}\<randomname>.dll
The Trojan.Win32.Sathurbot performs tasks downloader, by downloading other malware and allowing their execution in stealth mode (invisible / hidden)
Usually the infection is carried from some vulnerabilities in:
- Java;
- Flash Player;
- Adobe Reader;
that is activated when browsing the compromised websites.
The CryptoFBI file is saved in the user's temp folder (%TEMP%).
Examples of the CryptoFBI files collected from C.R.A.M. are shown in the list below to the left.
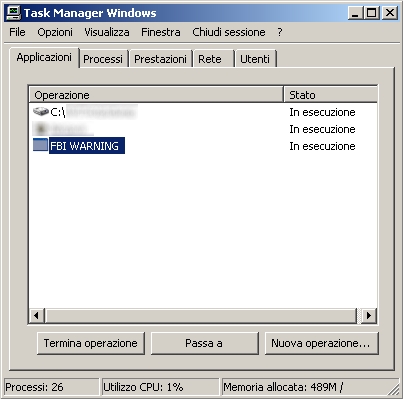
On the right image, however, you can see on the windows task manager how the cryptomalware's screen presents while it is active: the window is called "FBI WARNING".
- FILE NAME: ABDB.tmp.exe
- SIZE: 195584 byte
- MD5: 187DC47FB1455B3B47E5913DFE8D03E1
- FILE NAME: 1627.tmp.exe
- SIZE: 168960 byte
- MD5: 32219BB4A2F998364B120598FAF7929B
- FILE NAME: 321.tmp.exe
- SIZE: 160256 byte
- MD5: 45812BED1F5CAB8E30968AEE64A2D425
- FILE NAME: C3C3.tmp.exe
- SIZE: 192000 byte
- MD5: 5BD91CB7BD1768D61A1AEE960097C022
- FILE NAME: 365F.tmp.exe
- SIZE: 136192 byte
- MD5: 9CCD5A0FAB7F9DCC27E6685E310B9CCA
|
Click to enlarge |
|
The ransom demanded by CryptoFBI
Files that are encrypted by
CryptoFBI to be encrypted require a payment in BitCoin.
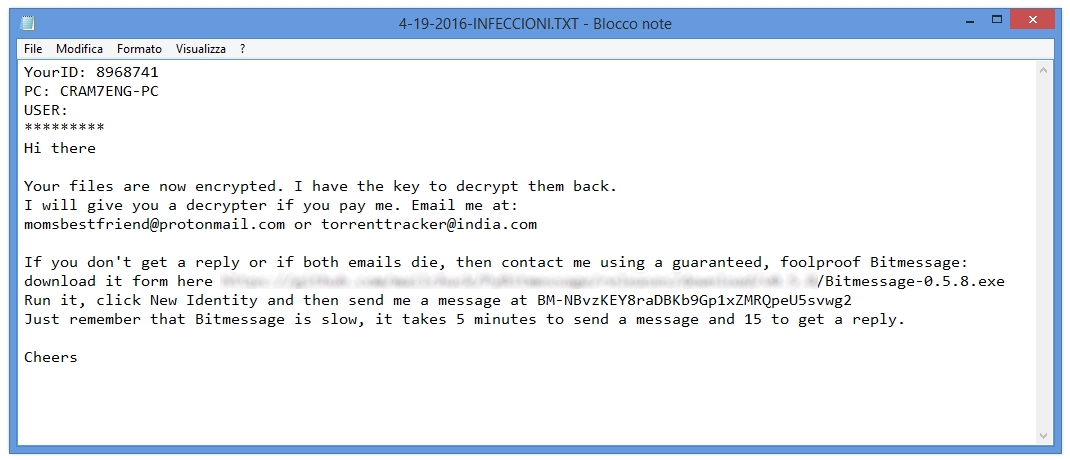
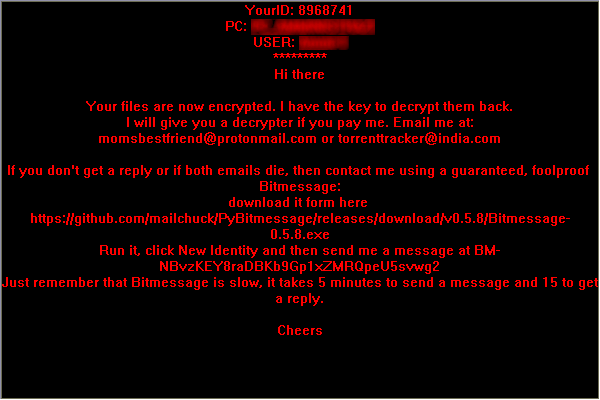
To obtain the information about the payment of the ransom you need to consult the files generated by cryptomalware, as indicated below:
- 4-19-2016-INFECCIONI.TXT
- 41920160000000.KEYHOLE
In the instruction file for the payment of the ransom is indicated to contact the blackmailers or by email at:
momsbestfriend@protonmail.com;
torrenttracker@india.com or using the
BitMessagemessaging program.
In the information mesaage are also indicated your own infection ID and the name of the infected PC.
How to protect yourself from CryptoFBI
As already reported, the Vir.IT eXplorer PRO's Anti-CryptoMalware technology when properly installed, configured, updated and used, has held up very well to these attacks managing to save the encryption up to 99.63% of the files and allowing the recovery of encrypted files in the initial phase of the attack up to 100% thanks to the integrated BackUp technologies:
- BackUp-On-The-Fly;
- Vir.IT Backup.
Assuming the correct:
- INSTALLATION;
- UPDATE of both the signatures and the engine;
- CONFIGURATION in particular of the resident shield Vir.IT Security Monitor with the "Anti-Crypto Malware Protection" flagged from the options window in real time, as well as Vir.IT BackUp activated, an advanced backup that allows you to have a copy of your work files preserved from encryption from which to proceed to recovery.
Back to top
What to do to mitigate the damage from CryptoFBI
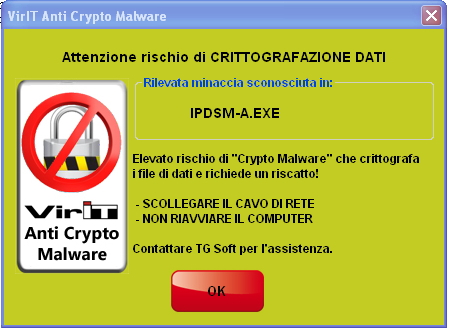
When the Alert screen on the side appears means that the Vir.IT eXplorer PRO's Anti-CryptoMalware integrated protection is acting and so, avoiding getting caught by the "panic" NOT close the window and perform the steps that are indicated:
- Make sure that Vir.IT eXplorer PRO is UP-TO-DATE;
- UNPLUG ETHERNET and/or EVERY NETWORK CABLE - by doing this, the computer will be phisically isolated from the network, thus containing the attack inside just one machine.
- PERFORM a FULL SCAN using Vir.IT eXplorer PRO.
- DO NOT REBOOT OR TURN OFF THE COMPUTER in order to avoid further encryption, as stated before.
In case of cryptomalware attack you should get in touch with Vir.IT eXplorer PRO's Tech Support as soon as possible. You can write an email to assistenza@viritpro.com, or call +39 049 631748 - +39 049 632750, Mon-Fri 8:30-12:30 and 14:30-18:30. |
Click to enlarge
99,63%*
Average percentage Expectation of protected files from encryption thanks to Vir.IT eXplore PRO's Anti-CryptoMalware protection ==> Check the information
|
Can I restore the encrypted files?
With the Anti-Crypto Malware protection integrated in VirIT, the number of encrypted files by CryptoCrypt will be at most a few dozen.
The "sacrificed" files during the mitigation must be replaced with a backup copy.
In the analyzed cases by the TG Soft's C.R.A.M., it was possible to recover files by using the shadow copies of the days preceding the attack.
Final thoughts
If you opened an infected attachment and has been started the encryption, you could:
- you have Vir.IT eXplorer PRO installed, correctly set up, up-to-date and running on your pc - in this case, you must follow the instructions on the Alert message and you will manage to save AT LEAST 99.63% of your data;;
- you have a AntiVirus software that DOESN'T DETECT, signal and halt the ongoing encryption - in this case you still could do
- UNPLUG EVERY NETWORK CABLE
- LEAVE YOUR COMPUTER TURNED OFF - every time the computer is rebooted and the malware is still active, a new encryption key will be used and the amount of money demanded as ransom will increase (note that paying the ransom does not guarantee the decryption and is therefore highlynot recommended)
Either way, remain calm and do not panic.
TG Soft
Anti-Malware Research Center