|
Ryuk ransomware, a modified version of Hermes, is used by Grim Spider, a cyber-criminal group whose first appearance was in August 2018.
C.R.A.M. (Research Center Anti-Malware) of TG Soft has analysed ransomware evolution in the last few months.
Last update: 2019-07-23
|
INDEX
|
Introduction
Grim Spider a cyber-criminal group, operates using Ryuk ransomware for targeted attacks to large organizations. The Ryuk ransomware is not spread through malspam campaign, but through cyber-attacks exploiting other malware as Emotet or TrickBot. These malware, in addition to being Trojan Bankers, have the ability to exfiltrate confidential information such as login credentials, but also inherent to the victim's network structure.
In the last months Ryuk has become sadly famous for several attacks in the USA and Italy. On 11 June 2019 "Bonfiglioli" company was attacked by Ryuk malware requesting a ransom of 2,4 million euros.
Ryuk ransomware analysis
The sample analysed dates back to 26
th June 2019.
Name:
etzivrs.exe
Size: 186.880 byte
MD5: 060374D93D83ED5218B63610739AB5A8
Date of compilation: 26/06/2019 19.14.12
The executable file of
Ryuk malware could be executed with a parameters depending by the function, as we can see below:
<malware Ryuk.exe> <arg 1> <arg 2>
The default execution of
Ryuk starts without parameters. In this case all "steps" necessary to carry out local and network encryption will be executed.
If only the parameter
<arg 1> is executed, the ransomware treat the parameter like a file and will try to delete it. After the execution it will continue like it was executed without parameters.
Assuming that
Ryuk ransomware is run without parameters, the first step is to enumerate all disk drives.
It is interesting to note that the mapped network and the cd-rom drives are not considered.
When identified the first unit of a hard disk drive, the original executable file is copied with a random name, for example
TIMMhwH.exe, and then it is executed with the following parameteres:
<random name>.exe 5 <drive>:
For exemple:
TIMMhwH.exe 5 C:
Ryuk runs new process of itself for each hard disk unit identified in the victim's system.
At this point we will have several
Ryuk processes active in memory, at least one per unit in addition to the original parent process.
The original process, which we call
Ryuk's father, after finishing to create new child processes, verify the version of the host operating system of Windows.
Ryuk runs different process depending on operating system, If the host operating system is higher than version 5, it means that operating system is between Vista and Windows 10, otherwise it is operating on Windows XP/Server 2003.
For Windows Vista or higher,
Ryuk creates a
Thread to terminate
38 processes and stop
62 services, as we can see from the following table:
| Processes |
Services |
veeam
backup
backup
xchange
sql
dbeng
sofos
calc
ekrn
zoolz
encsvc
excel
firefoxconfig
infopath
msaccess
mspub
mydesktop
ocautoupds
ocomm
ocssd
onenote
oracle
outlook
powerpnt
sqbcoreservice
steam
synctime
tbirdconfig
thebat
thunderbird
visio
word
xfssvccon
tmlisten
pccntmon
cntaosmgr
ntrtscan
mbamtray |
veeam
back
xchange
ackup
acronis
sql
enterprise
sophos
veeam
acrsch
antivirus
antivirus
bedbg
dcagent
epsecurity
epupdate
eraser
esgshkernel
fa_scheduler
iisadmin
imap4
mbam
endpoint
afee
mcshield
task
mfemms
mfevtp
mms
msdts
exchange
ntrt
pdvf
pop3
report
resvc
sacsvr
savadmin
sams
sdrsvc
sepmaster
monitor
smcinst
smcservice
smtp
snac
swi_
ccsf
truekey
tmlisten
ui0detect
w3s
wrsvc
netmsmq
ekrn
ehttpsrv
eshasrv
avp
klnagent
wbengine
kavf
mfefire |
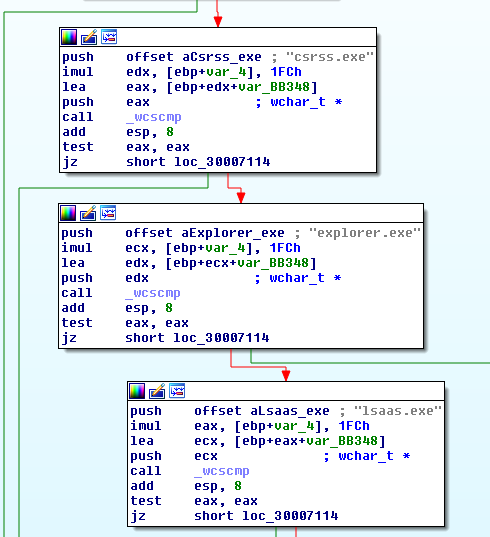
At this point the ransomware enumerate all active processes of the system, and if it has enough privileges, runs a
injection with ransomware code. The following processes are excluded from the injection:
- csrss.exe
- explorer.exe
- lsaas.exe
as we can see in the figure on the right. |
 |
The injection uses API
CreateRemoteThread that execute the thread called "
StartAddress", as we can see in the figure below:
The
"StartAddress" function creates a file called
sys inside the user's public folder, then it starts encryption process, once it was completed, is created a file called
finish inside public folder.
So until now, were generated
Ryuk's father process, child processes and all running processes infected (via
injection) by
Ryuk, all ready to encrypt computer files.
File encryption
Ryuk uses Microsoft's CryptoAPI for file encryption by setting a CSP (cryptographic service provider) of the type PROV_RSA_AES.
Inside Ryuk's file is stored a RSA public key, which we can see below:
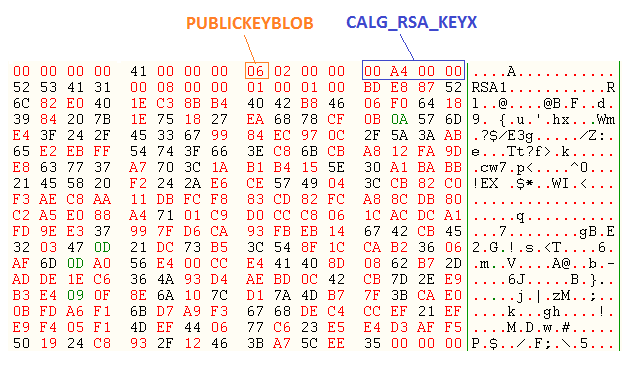
The public key is of type CALG_RSA_KEYX and is embedded inside the Ryuk malware, this is imported through the CryptImportKey API and will be used to encrypt the key used to encode the victim's file.
The nex step is to decrypt email adresses for the ransom, in the sample analysed these are:
- chris-morris-1976@protonmail.com
- tasha-williams.91@protonmail.com
After decrypting html page, this will be stored in the RyukReadMe.html file.
Once again Ryuk terminates processes and stops services that are listed above.
The RyukReadMe.html file is created in %temp% with the ransom instruction, this file will be created later in each folder.
The Ryuk executable file, based on execution parameter, performs the following steps:
- If it is 5 then encrypt the hard disk according to the letter of the unit given as parameter
- If it is 7 then enumerates network resources and encrypt them
- If it is 2 then encrypt all units starting from A:, B:, C:, etc.
- Otherwise encrypt all units starting from Z:, Y:, X:, etc.
Instead, the processes that are "injected" by Ryuk, will encrypt all units starting from Z:, Y:, X:, etc.
The next step is to enumerate the files and folders for encryption.
The following folders will be skipped by Ryuk, therefore the files stored in them will be not encrypted:
- AhnLab
- Chrome
- Mozilla
- $Recycled.Bin
- WINDOWS
The folder named "
AhnLab" refers to the homonymous Korean anti-virus, as we indicated previously
Ryuk has extreme similarities to
Hermes ransomware, which was probably developed from North Korea and its sources were sold in forums on the dark web.
Furthermore, the following files are not encrypted:
- RyukReadMe.html
- UNIQUE_ID_DO_NOT_REMOVE
- PUBLIC
Furthermore even the following system folders are also skipped during the encryption process:
- "\\Windows\\"
- "sysvol"
- "netlogon"
All files except the following extensions will be encrypted:
The encryption algorithm used is AES-256, the encryption key is generated per each file, using the function CryptGenKey, as we can see in the figure below:

The encryption takes place calling the API CryptEncrypt, as we can see in the figure:
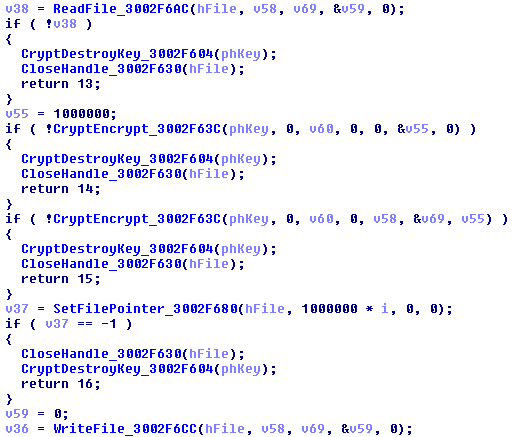
At the end of each encrypted file is attached:
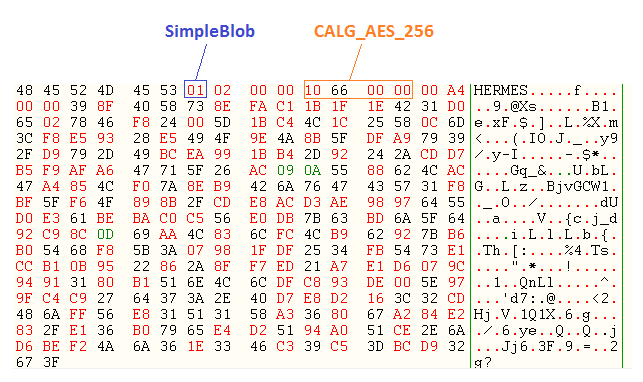
- Marker: HERMES
- <simpleblob>
The "simpleblob" is a data structure of the "blob" type, which contains the AES-256 encrypted key, which was pre-encrypted with RSA embedded public key, indicated previously. This is done by exporting the encryption key of AES-256, as we can see in the figure, and its subsequent writing to file:
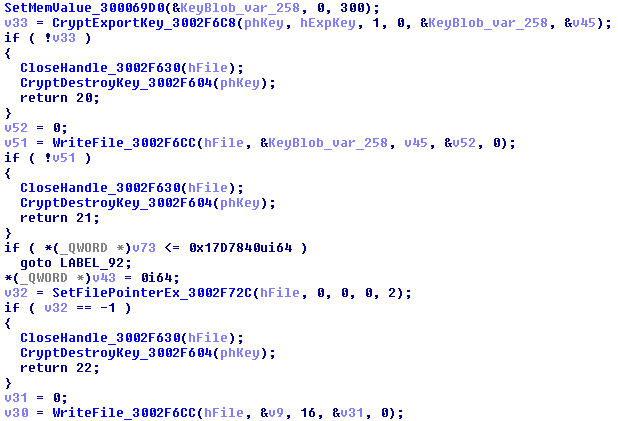
If the size of the file to be encrypted is larger than of 25000000 bytes, additional 16 bytes of the original file are attached after "simpleblob".
In the figure below we can see the "HERMES" marker and the "simpleblob" containing the AES-256 encryption key:
Back on Top
Network file encryption
Ryuk does not consider mapped network drives, but it directly acesses to shared network routes.
In the figure below, we can see 2 methods used to enumerate network resources:
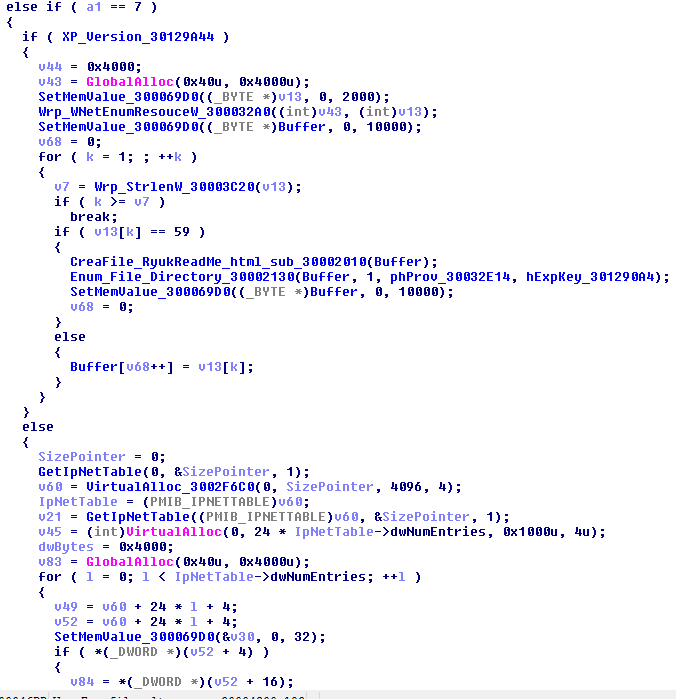
If operating system is Windows XP / Server 2003, the ransomware will uses the WNetEnumResource API to enumerate all shared network resources.
If operating system is between Vista and Windows 10, Ryuk will uses the GetIpNetTable API to obtain the Address Resolution Protocol (ARP) table. ARP is responsible for mapping of IPv4 adresses to a physical ones "Mac Address". The ransomware will be able to enumerate the network through the IPv4 adresses obtained from ARP table using "WNetEnumResource", with calls like: "\\<address IPv4>"
Ransom demand
The image below showing the
RyukReadMe.html file contents:
At the top left corner are provided two email adresses to contact for redemption information,while in the lower right corner are reported "
balance of shadow universe".
Conclusion
The
Ryuk ransomware uses an RSA public key embedded in the executable file, which is used to encrypt the AES-256 bit key used to encode the victim's file.
Ryuk does not send any information to command and control server because all informations to decrypt are attached at the end of the encrypted files.
The encryption scheme used by
Ryuk assumes that each sample is created for the intended victim, which can obtained "decipher" program containing
RSA private key using to decrypt
the AES-256 bit encryption key, only paying the ransom, in order to retrieve their files.
Ryuk is an atypical ransomware specifically used by Grim Spider an eCrime group, to target large organization worldwide. Unlike the common ransomware, systematically distributed via massive spam campaigns, Ryuk is used exclusively for tailored attacks to organizations that are capable to pay a high-ransom return.
IOC
MD5:
060374D93D83ED5218B63610739AB5A8
Autori: Gianfranco Tonello, Michele Zuin
TG Soft - Centro Ricerche Anti-Malware (C.R.A.M.)
How to protect yourself
Experience and common sense are the first weapons not to be victims of this kind of fraud.
A
careful reading of the e-mails is essential, in all its elements. Be wary of attachments in
ZIP format and if possible, do not enable the automatic execution of
macros, a setting that could make the hasty opening of
Word and
Excel files dangerous. Another little help can be to check where any link is pointing, even if this type of evaluation can be very difficult.
In the event that you were infected by a
Banker, the advice from the
C.R.A.M. (
TG Soft) is to take appropriate security measures
even after the remediation of the systems involved as the change of passwords most commonly used on the web navigation.
In the event that the workstation involved was used for home-banking operations, it is also advisable to check with your
credit institution.
How to send suspicious e-mails for analysis as possible viruses / malware / ransomware and / or phishing attempts
Sending materials to be analyzed at the TG Soft Anti-Malware Research Center for analysis that is always free and can be done safely in two ways:
- Any e-mail that can be considered a suspect can be sent directly by the recipient's e-mail choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify" to the following mail: lite@virit.com
- save as an external file to the e-mail program used the e-mail to be sent to the C.R.A.M. TG Soft for analysis. The resulting file must be sent by uploading it from the page Send Suspicious Files (https://www.tgsoft.it/italy/file_sospetti.asp). Of course, to have a feed-back compared to the analysis of the infected files sent, you will need to indicate an e-mail address and a brief description of the reason for sending the file (for example: possiible / probable phishing; possible / probable malware or other) .
Tutto questo per aiutare ad aiutarvi cercando di evitare che possiate incappare in furti di credenziali, virus/malware o ancor peggio Ransomware / Crypto-Malware di nuova generazione.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
Vir.IT eXplorer PRO has been designed and implemented in such a way to increase the security of your computers, PCs and servers alike, Vir.IT eXplorer Lite -FREE Edition-.
Vir.IT eXplorer Lite has the following features: |
 |
- freely usable both in the private sector and in the business environment with Engine + Signature updates without time limitations;
- It works with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PC and SERVER, recommended to be used as an integration of the AntiVirus already in use as it does not conflict or slow down the system but significantly increases the security in terms of identification and remediation of infected files;
- identifies and, in many cases, also removes most of the viruses / malware actually circulating or, alternatively, allows it to be sent to the C.R.A.M. Anti-Malware Research Center for further analisys;
- thanks to the Intrusion Detection technology, made available also in the Lite version of Vir.IT eXplorer, the software is able to report any new generation viruses / malware that are placed in automatic execution and proceed to send the files reported to the C.R.A.M. of TG Soft.
- Proceed to download Vir.IT eXplorer Lite from the official TG Soft site distribution page.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners it is always possible to contact or forward suspicious e-mails for free to the TG Soft technical support, the e-mail address for sending suspicious e-mails is: assistenza@viritpro.com (the suspicious e-mail goes sent as an attachment). C.R.A.M. Technicians will analyze the material recived to evaluate every possible danger without any risk for our customers.
|
Go check our
TG Soft support.
C.R.A.M.
Anti Malware Research Center by TG Soft
Back on Top