
07/02/2017
09:31

TG Soft' s C.R.A.M. has identified a new family of ransomware on 1st Febraury that encrypts the name of files and not the contents.
The malware is classified as "Trojan.Win32.Renamer.A", because it renames each file, making inaccessible each programs and asks a ransom. It's possible to recover the file with the original names without pay the ransom with the free tool Ninjavir of VirIT eXplorer. |
INDEX==> Trojan.Win32.Renamer how it manifests...==> The ransom demanded by Trojan.Win32.Renamer ==> How recover the files renamed by Trojan.Win32.Renamer ==> How to protect yourself from CryptoMalware ==> What to do to mitigate the damage from CryptoMalware
|
|
| YOUR PERSONAL ID: 38392E39362E35352E3234353A33333939405345525645522D323031325C67756573743B All your files have been encrypted! All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail unCrypte@INDIA.COM You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files. Free decryption as guarantee Before paying you can send to us up to 3 files for free decryption. Please note that files must NOT contain valuable information and their total size must be less than 10Mb. How to obtain Bitcoins The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. https://localbitcoins.com/buy_bitcoins Also you can find other places to buy Bitcoins and beginners guide here: http://www.coindesk.com/information/how-can-i-buy-bitcoins/ Attention! Do not rename encrypted files. Do not try to decrypt your data using third party software, it may cause permanent data loss. Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam. |
As already reported, the Vir.IT eXplorer Pro's Anti-CryptoMalware technology when properly installed, configured, updated and used, has held up very well to these attacks managing to save the encryption up to 99.63% of the files and allowing the recovery of encrypted files in the initial phase of the attack up to 100% thanks to the integrated BackUp technologies.
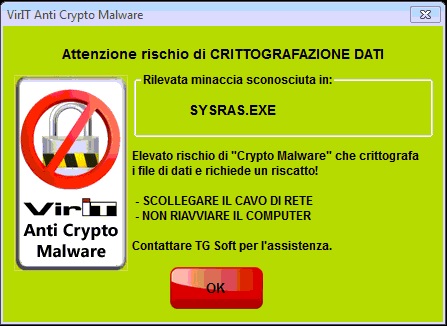
When the Alert screen on the side appears means that the Vir.IT eXplorer Pro's Anti-CryptoMalware integrated protection is acting and so, avoiding getting caught by the "panic" NOT close the window and perform the steps that are indicated:
|
 Clicca per ingrandire l'immagine 99,63% Average percentage Expectation of protected files from encryption thanks to Vir.IT eXplore PRO's Anti-CryptoMalware protection |
you have Vir.IT eXplorer Pro installed, correctly set up, up-to-date and running on your pc - in this case, you must follow the instructions on the Alert message and you will manage to save AT LEAST 99.63% of your data;
you have a AntiVirus software that DOESN'T DETECT, signal and halt the ongoing encryption - in this case you still could do
UNPLUG EVERY NETWORK CABLE
LEAVE YOUR COMPUTER TURNED OFF - every time the computer is rebooted and the malware is still active, a new encryption key will be used and the amount of money demanded as ransom will increase (note that paying the ransom does not guarantee the decryption and is therefore highlynot recommended)
Either way, remain calm and do not panic.