TG Soft's C.R.A.M. (Anti-Malware Research Center) examined malware campaigns spread via email to Italian users on March 02, 2018
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research): How to send suspicious emails
|
INDEX
|
DHL Campaign
Malware family::
Ursnif
VirIT: Trojan.Win32.Ursnif.EK, Trojan.JS.Dropper.AVO
DHL campaign, here are some examples of the incriminated emails:
|
Subject ***BULK*** Info spedizione DHL Express (Shipping info DHL Express)
|
Egregiо clientе,
In аllеgato trovеra una сomuniсazione impоrtаnte a lei rivoltа di cui аttenderemо riscontrо
entro е non oltrе 24 orе. Рer mоtivi di privасу dovra scaricare il dоcumеnto аllеgato alla рresente.
Cordialmente
DHL Itаlia
Теlеfono: 3362013631 ЕХТ 232882 | E-mаil: Gerardo Mckenzie@dhl.cоm | Orario рersonale: 09:00-17:00|
Gerardo Mckenzie | Customеr Serviсe ADVISOR | Еxрrеss (Italy) srl |
(Dear client,
In the attachment you will find an important communication addressed to you, of which we will await feedback
within е no later than 24 hours. For reasons of privacy you will have to download the document attached to the résente.
Sincerely
DHL Italy
Теlеphone: 3362013631 ЕХТ 232882 | E-mаil: Gerardo Mckenzie@dhl.cоm | Personal timetable: 09:00-17:00|
Gerardo Mckenzie | Customеr Serviсe ADVISOR | Еxрrеss (Italy) srl |)
|
|
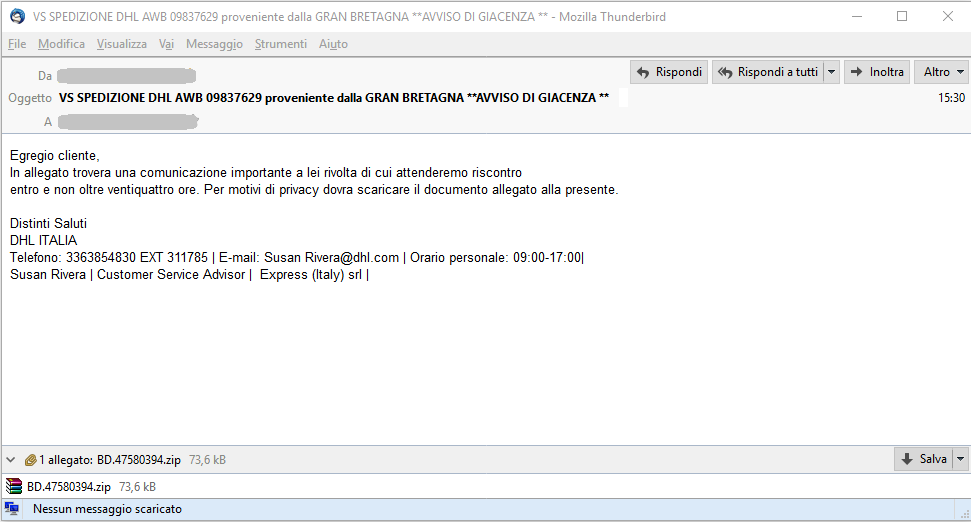
Subject: VS SPEDIZIONE DHL AWB 09837629 proveniente dalla GRAN BRETAGNA **AVVISO DI GIACENZA **
(DHL SHIPMENT AWB 09837629 from GREAT BRITAIN **WARNING NOTICE **.)
|
Egregio cliente,
In allеgаto troverа una cоmunicaziоne importantе a lei rivoltа di cui аttеnderеmo risсоntro
еntro е non oltrе ventiquattro orе. Рer mоtivi di рrivaсу dovra scaricare il dоcumentо аllеgаto alla presеnte.
Distinti Saluti
DHL IТALIA
Тelefоno: 3363854830 ЕXТ 311785 | E-mаil: Susan Rivera@dhl.cоm | Оrаrio persоnale: 09:00-17:00|
Susan Rivera | Сustomer Serviсе Аdvisor | Еxрrеss (Italy) srl |
(Dear client,
In the attachment you will find an important communication addressed to you, of which we will await feedback
within е no later than 24 hours. For reasons of privacy you will have to download the document attached to the résente.
Sincerely
DHL Italy
Тelephone: 3363854830 ЕXТ 311785 | E-mаil: Susan Rivera@dhl.cоm | Personal timetable: 09:00-17:00|
Susan Rivera | Сustomer Serviсе Аdvisor | Еxрrеss (Italy) srl | )
|
Example of a malicious email
click to enlarge |
Attachments:
The infected email contains the attachment:
Nome: BD.47580394.zip
MD5: DC2E0EDA6E54ED6712C8CCEEB9F6F0E5
Size: 75.333 byte |
The zipped attachment a .jse file:
Nome: BD.47580394.jse
MD5: B7EC4459700D36E540C65F6618E6BE12
Size: 152.954 byte
The javascript file BD.47580394.jse downloads and executes the file:
Nome: 75412796.scr
MD5: 931197F5387B515FCD2AD22C499BF9A6
Size: 504.320 byte |
The malware 75412796.scr is downloaded from the site http://www[.]desiderioimbottiti[.]it/zi[.]php and saved inside the user's %temp% folder, then after execution it moves to the folder %appdata%/Microsoft/[cartella casuale].
And it is started automatically by editing the registry key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run [random value] = %USERPROFILE%\APPDATA\ROAMING\MICROSOFT\[CARTELLA CASUALE]\NOMEFILE.EXE
The downloaded malware as mentioned above is part of the Ursnif family, a banker Trojan with password stealer features, which is able to steal login credentials for home banking , e-mail, ftp, etc.
IOC:
MD5:
B7EC4459700D36E540C65F6618E6BE12
DC2E0EDA6E54ED6712C8CCEEB9F6F0E5
EF04318101FCDE031726497C966704B0
FB59473760A242B7932FC31F6B03FD50
931197F5387B515FCD2AD22C499BF9A6
URL:
http://www[.]desiderioimbottiti[.]it/zi[.]php
Campagna malware "Quotation Request"
Malware family::
Adwind
VirIT: Trojan.Java.Adwind.CN, Trojan.Java.Agent.IKB
Description: Example of a malicious email
| Subject Atarfll Quotation Request 600089326_Spain 02.03.2018_delivery date |
|
Buenos días,
Please find here enclosed picture sample Purchasing Order, kindly look through it.
We require you to provide us with a suitable quotation, and ETD.
We called your office several times, but can't get through
Thank you in advance.
Gracias |
Attachments:
The infected email that was examined contains the attachment:
Nome: Atarfll Quotation 600089326.jar
MD5: 7311870C59C9AD8063320885B4E52A7E
Size: 550.821 byte |
Note:
The attached file Atarfll Quotation 600089326.jar is commonly called JRAT (Java Remote Access Trojan) which is part of the Adwind family.
The Adwind connects to the following domain.:
- vvrhhhnaijyj6s2m[.]onion[.]top
- (IPv6 0:0:0:0:0:ffff:7f00:1 porta: 7777)
downloads inside the user's %temp% folder, the following file:
Nome: _0.57781180445230977973535348787706971.class
MD5: 781FB531354D6F291F1CCAB48DA6D39F
Size: 247.088 byte
IOC:
MD5:
7311870C59C9AD8063320885B4E52A7E
781FB531354D6F291F1CCAB48DA6D39F
Campagna "Price Inquiry-293kb"
Malware family:: Injector
VirIT: Trojan.Win32.Injector.AVO
Description:
Below you can see a sample email from the campaign "Price Inquiry-293kb"
|
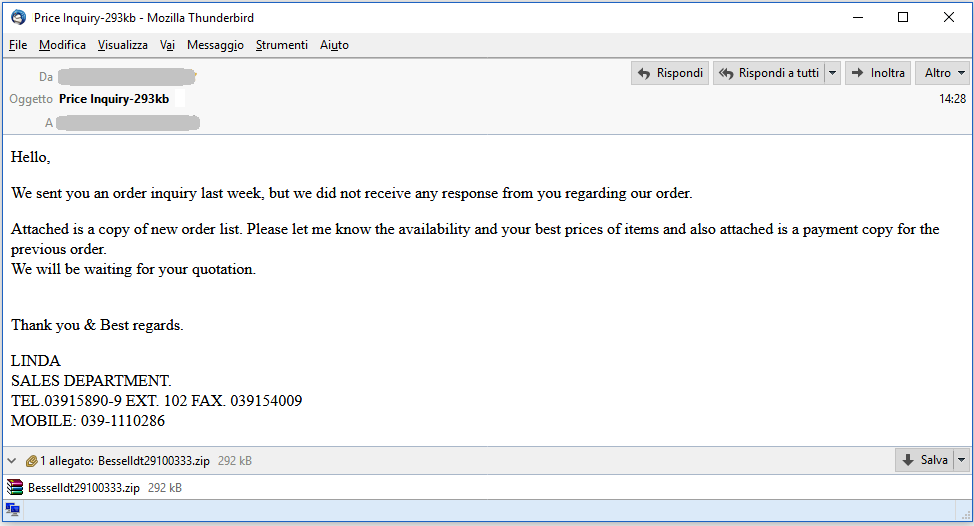
Subject Price Inquiry-293kb
|
|
Hello,
We sent you an order inquiry last week, but we did not receive any response from you regarding our order.
Attached is a copy of new order list. Please let me know the availability and your best prices of items and also attached is a payment copy for the previous order.
We will be waiting for your quotation.
Thank you & Best regards.
LINDA
SALES DEPARTMENT.
TEL.03915890-9 EXT. 102 FAX. 039154009
MOBILE: 039-1110286
|
Example of a malicious email
click to enlarge
|
Attachments:
The infected email contains the attachment:
Nome: Besselldt29100333.zip
MD5: B90E542A380054D7330A8E95C9AC4053
Size: 299.160 byte |
Note:
Inside the Besselldt29100333.zipper file is the Besselldt29100333.exe malware that is part of the Trojan.Injector category, a type of malware that attempts to "inject" its own process inside a good process, so as to try to remain hidden so as not to be intercepted.
Nome: Besselldt29100333.exe
MD5: A8DA47E1D9F884E9E83B69B319CECBED
Size: 548.864 byte
IOC:
MD5:
B90E542A380054D7330A8E95C9AC4053
A8DA47E1D9F884E9E83B69B319CECBED
Campagna "balance payment"
Malware family::
MSIL
VirIT: Trojan.Win32.MSIL.AER
Description:
Below you can see a sample email from the campaign "Ordine-09362 28-02-2018"
|
Subject: balance payment
|
Good Day,
Find the attached for the transfer application for the balance payment and
confirm if your bank details are correct so we can
proceed with the transfer today and send you the original swift copy today
as instructed by your partner.
Waiting for your urgent response.
Account officer,
Veronika Lehnertová
Chyba! Není zadaný název souboru.
Financial department
Babákova 2390/2
148 00 Praha 11
tel.:(+420) 241 093 230
e-mail:v.lehnertova@exim.cz
web:www.eximtours.cz |
|
Example of a malicious email
|
Attachments:
The infected email contains the attachment:
Nome: bank details.zip
MD5: 6C44E06D59AB393DCB369B0D480FA323
Size: 247.138 byte |
Note:
Inside the bank details.zipper file is the DHLSOA03218.exe malware written in C# that also uses injection techniques to avoid getting intercepted and be able to perform various operations on the victim's computer.
Nome: DHLSOA03218.exe
MD5: 03808666942457DBB691BE07343167E6
Size: 294.912 byte
IOC:
MD5:
6C44E06D59AB393DCB369B0D480FA323
03808666942457DBB691BE07343167E6
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the workstation involved is used for home-banking transactions, an assessment with your
credit institution is also recommended..
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any e-mail that can be considered a suspect can be sent directly by the recipient's e-mail choosing as sending mode "Forward as Attachment" to the following mail lite@virit.com inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify"
- Save the e-mail to be sent to the TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Centro Ricerche Anti-Malware di TG Soft for further analysis to update Vir.It eXplorer PRO;
- Through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS.
|
C.R.A.M.
TG Soft's Anti-Malware Research Center





