Researchers at
TG Soft's CRAM found several campaigns of the
Trojan Banker Mekotio, transmitted via bogus e-mails during the March/April 2023 period, with hypothetical
electronic invoices as their subject.
Below is an example of the emails used to spread the Mekotio malware:
Inside the email we find a fake button which, when clicked, executes the link to the site "https://eurt-emf5vs6xwq-uc[.]a[.]run[.]app". From here a compressed file is downloaded called, in our case, ID-FACT.1679993928.zip, containing the dropper inside.
The compressed file, after being opened and unzipped, extracts the dropper in the form of a Windows installer (.msi) from which, once executed, the initial phase of the infection starts.
In the initial stage of the infection, a folder with a random name is created in the %localappdata% directory, which will be used as a support folder for the prosecution of the infection.
Three files are extracted in the created directory :
- An AutoHotkey executable file -i.e., a legitimate file of a programming language used to launch programs and send click sequences or keystrokes for Microsoft Windows systems.
- A compressed file containing the Mekotio DLL.
- A script file with parameters for the correct execution of the DLL.
In the second step of the infection, the AutoHotkey process is executed, which launches the script "Qoh.E.ahk" extracted in the previous step, containing the following parameters:
#NoEnv
#NoTrayIcon
#SingleInstance Ignore
#ErrorStdOut
SetWorkingDir %A_ScriptDir%
N4H3V04J919SVIAGJ0J2Z6C := "HQIWUUDTEA.AQe"
DllCall(N4H3V04J919SVIAGJ0J2Z6C "\UO13UUM0WI8Q3HUORQE5T") |
The script's task is to make a call to the
DllCall function with the parameter "
N4H3V04J919SVIAGJ0J2Z6C," which contains the name of the extracted Mekotio's DLL "
HQIWUUDTEA.AQe," and the exported function to call "
UO13UUM0WI8Q3HUORQE5T." Afterwards, the DLL is loaded into memory and executed by the AutoHotkey process. This operation is not visible to the user as it is executed surreptitiously so as not to be traceable. With the loading into memory, the
Mekotio payload is executed.
In the above image is highlighted the function exported from the DLL, called by the script "Qoh.E.ahk," which allows the Mekotio payload to start correctly. The DLL (SHA-256: ef3d267a35457e1b16d484465b12b0f8eab2a414f9f2eedc3a1c42c4e7242a3a) was compiled on date "2023-03-27 01:28:30".
Among the first tasks performed there is a call to "
https://ipinfo[.]io" to detect the IP and geolocation of the victim's machine. This check occurs because
Mekotio is designed to run only on machines located in certain countries. Depending on the finding, positive or negative, the process is terminated or continues with the next step.
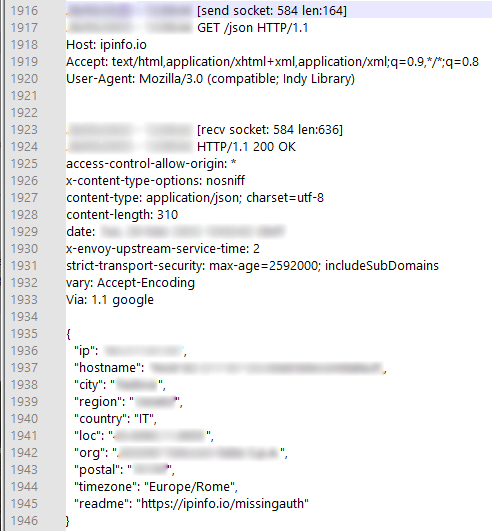
In the case of a positive match, the payload moves on to the main stage of infection, where the TXT file "googledocs1.txt" which contains the encrypted C2, is downloaded. Then takes place the theft of the victim's various credentials/passwords and monitoring/control of the infected PC .
The TXT file with the encrypted C2 is downloaded from the "
gamesloipsdos3.serveirc[.]com/googledocs1.txt":
The file contains a string with base64 parameters that are separated using the following character sequence "^^^":
| ^^^ClDCapscpzCMvesEhg4zjs8E+zex78ddv4SRSL1ZWe69helopb6uPAxRby6BZvTC^^^1SOiYLy9viBQLfHIiUh0Sw==^^^01--13-03^^^OSE8ef4CN+QDGK0Q/kqQPQ==^^^9rRJ6D2jsmyVTZck90BnEF/fLX9jHm2DD3QEs20PnUk3Q4z7dZ0O5+43HKBYtVFA^^^ScrFnY/Xk+mngHYR0IGSzw==^^^ |
The parameters are encoded in base64 and appear to be encrypted. The only parameter in the clear is "01--13-03" which could indicate the version/flag and a date most likely related to the configuration. In the case of the analyzed sample the version could be 01 and the date in the form "day/month" is 13-03. Based on the analysis of the various campaigns, we noticed the use of the same configuration with the same date (13-03) on different days. As the configuration changed, the date changed too.
Mekotio, as we said, is similar to various spyware/keyloggers: monitoring and control functions of the victim's PC - including peripherals - and screenshot functions of the currently active window at regular time intervals. It also assumes password stealer features to search the various passwords saved in the machine.
Below are the dump sequences, where are highlighted the various typical controls of a malware with espionage and control functions :
The stolen data are copied to a text file allocated in the mentioned folder placed in %localappdata% . These data will later be sent to the command & control server (C2).
Mekotio, in case the PC is rebooted or shut down, creates persistence within the Windows registry RUN key to run at every system startup.
The malware therefore remains active in the infected PC, with spyware and monitoring functions, performing regular communication with the command and control server (C2).
IOC:
|
FACT6422a.msi - b7677c08dc583df86dfcead29b605a04aa3c2444bce43d0e786ff831ed76ef40
Qoh.E.ahk - d11af53ffe7b9dd49489487d389942a1782aa0fb10315bbe3d23eb4f377b4a32
Qoh.E.exe - de87c8713fac002b0b0a0f9b02c4e3ebcccf65282a22f5ab5912a9da00f35c2a
HQIWUUDTEA.AQe - ef3d267a35457e1b16d484465b12b0f8eab2a414f9f2eedc3a1c42c4e7242a3a
|
Drafted by :
Breabin Radu
Callegaro Samuele

