The CRAM (Anti-Malware Research Center of TG Soft) team has recently discovered and analyzed a new threat that targets users of the Android operating system. This is the first example of Rogue-Antivirus for Android analyzed by the CRAM (Anti-Malware Research Center of TG Soft). A Rogue-Antivirus is a particular kind of FraudTool which pretends to be an Anti-Virus software that has found one or more infections on the victim device.
The purpose of such a malware is twofold. On one hand, indeed, it aims to trick the victim in order to get him buying a theoretical premium version to clean the non-existent infection. On the other hand, generally, these kinds of malware try to obtain/steal personal data of the victim.
| Package: com.example.androiddefender2 |
 |
| MD5: 1CA532F171A0B765A46AF995EBAAB1D2 |
| Size: 2.481.301 Byte |
When one tries to install this malicious app, it requires the following permissions:
- android.permission.ACCESS_NETWORK_STATE
- android.permission.CALL_PHONE
- android.permission.GET_TASKS
- android.permission.INTERNET
- android.permission.PROCESS_OUTGOING_CALLS
- android.permission.READ_CONTACTS
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.READ_PHONE_STATE
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.VIBRATE
- android.permission.WRITE_EXTERNAL_STORAGE
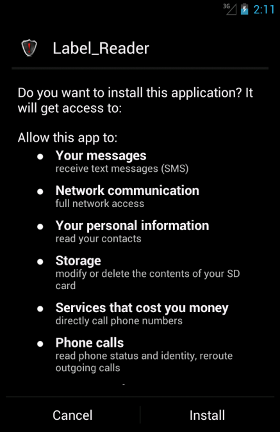
In particular, between the various permissions, we want to point out
CALL_PHONE, which allows the app to do a phone call without the user confirmation,
PROCESS_OUTGOING_CALLS, which allows the app to monitor/modify/abort outgoing calls, and finally
RECEIVE_SMS, which allows the app to monitor incoming SMS messages in order to record them or to perform further opertations on them.
Remind that it is highly recommended to READ the permissions that an app requires CAREFULLY before installing it!
Once installed, the malicious app shows itself in our app menu with the name of
"Android Defender".

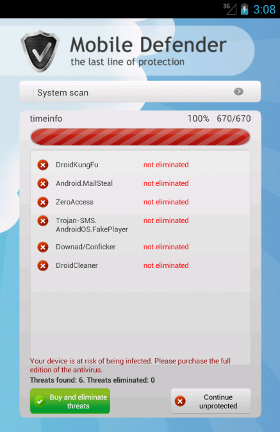
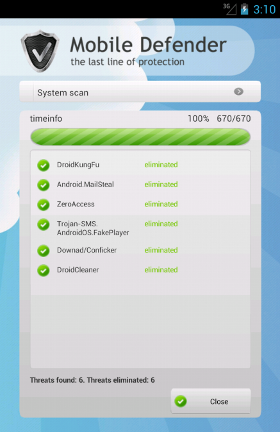
When we launch it, the malicious app shows a fake scanning in which it pretends to find some threats on the victim's device (of course it finds everything and more but itself). Now, a victim might be fooled, since some of the threats shown have real Android malware names (such as:
DroidKungFu) and others have well-known Windows malware names (such as:
Conficker and
ZeroAccess). Of course, and here the victim should start to be a little bit suspicious, in order to eliminate these threats a full edition of the Anti-Virus is required.
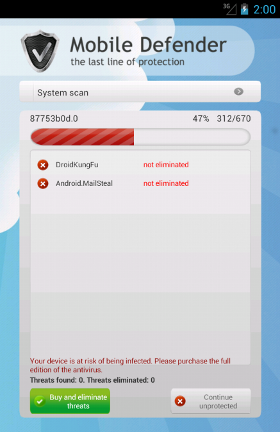
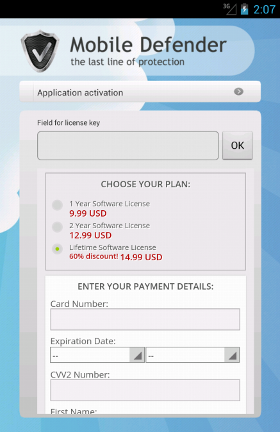
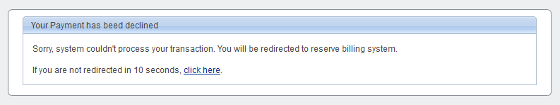
If a victim falls into the trap and tries to buy it, it is redirected to a proper page.
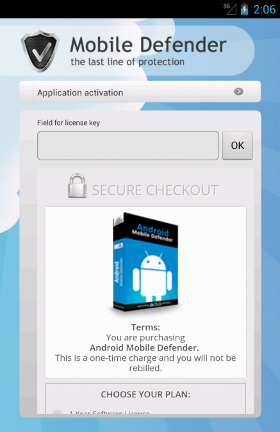
This page is dinamically loaded from the
URL:
http://pdblprotect.com/p/amd/droid/?ver=0001&affid=85000&group=amd&reject_url=[...]&ps=[...]
In particular, the rejected field contains another
URL:
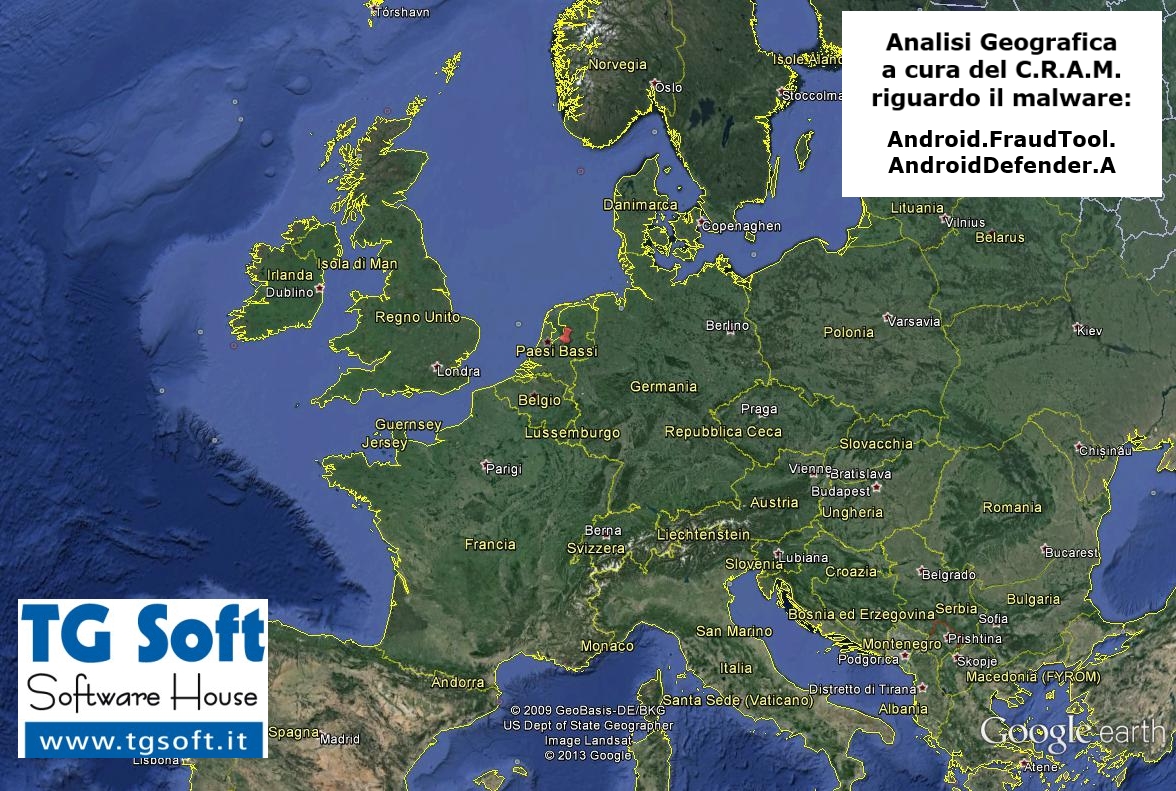
http://pdblprotect.com:80/p/decline/?affid=85000&ver=0001&group=amd&ps=[...]. This domain results to be dislocated in the
Netherlands, to have the name
customer.worldstream.nl and
IP Address
217.23.5.104.
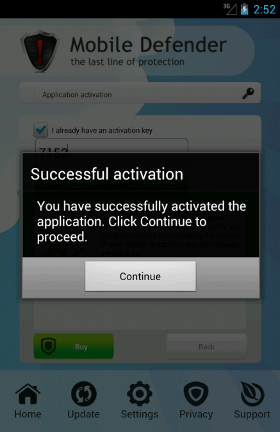
Now, looking at the plans available we can see there exists a
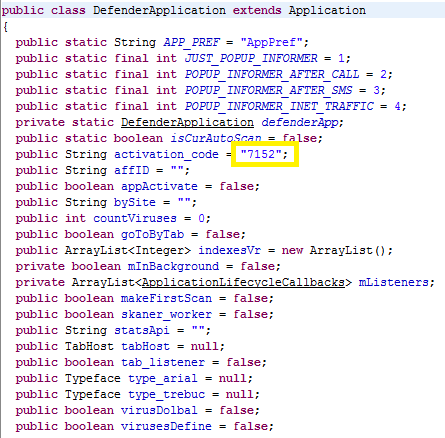
"lifetime license". This should definitively trigger a little bit of suspiciousness in the victim's mind. Is there any known AV firm who sells a lifetime license? By the way, if you are wondering, the activation code is hard-coded inside the malware itself (into the
DefenderApplication class).
Anyway, let's have a look under the hood.
The malware supports both English and Russian languages.
We can find all we need to understand that this is a FraudTool in the
assets folder. Indeed, here there is a file called
VirusesDescription.xml which contains the name and the description of 15 malware, used by this Rogue-Antivirus (
i.e. Trojan-SMS.AndroidOS.FakePlayer,
Geinimi,
Android.Plankton,
DroidKungFu,
Android.DDoS.1.origin,
ZeroAccess,
Downad/Conficker,
DroidCleaner,
Android.SmsSend,
Android.AntaresSpy,
Android.Anzhu,
Android.GoldDream,
Android.MailSteal,
Android.Moghava and
Android.Spy).
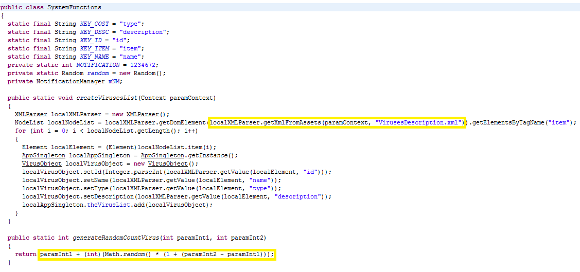
Glancing at the
SystemFunctions class we can also see a
generateRandomCountVirus() method which simply returns a random number, that is the number of malware that have theoretically infected the device.
Furthermore, always in the assets folder, there are also an SQLite database (
AndroidDefender.sqlite) and a file called
VirusesDescription.xml, which contains the previous mentioned
URL (under the
"buysite" string) as well as another
URL to which the app connects (under the
"statsapi" string), that is:
http://219.235.1.127/api/dom/no_respond/?group=amd&ver=0001&ts=[...]&token=fya14oiYU&affid=85000
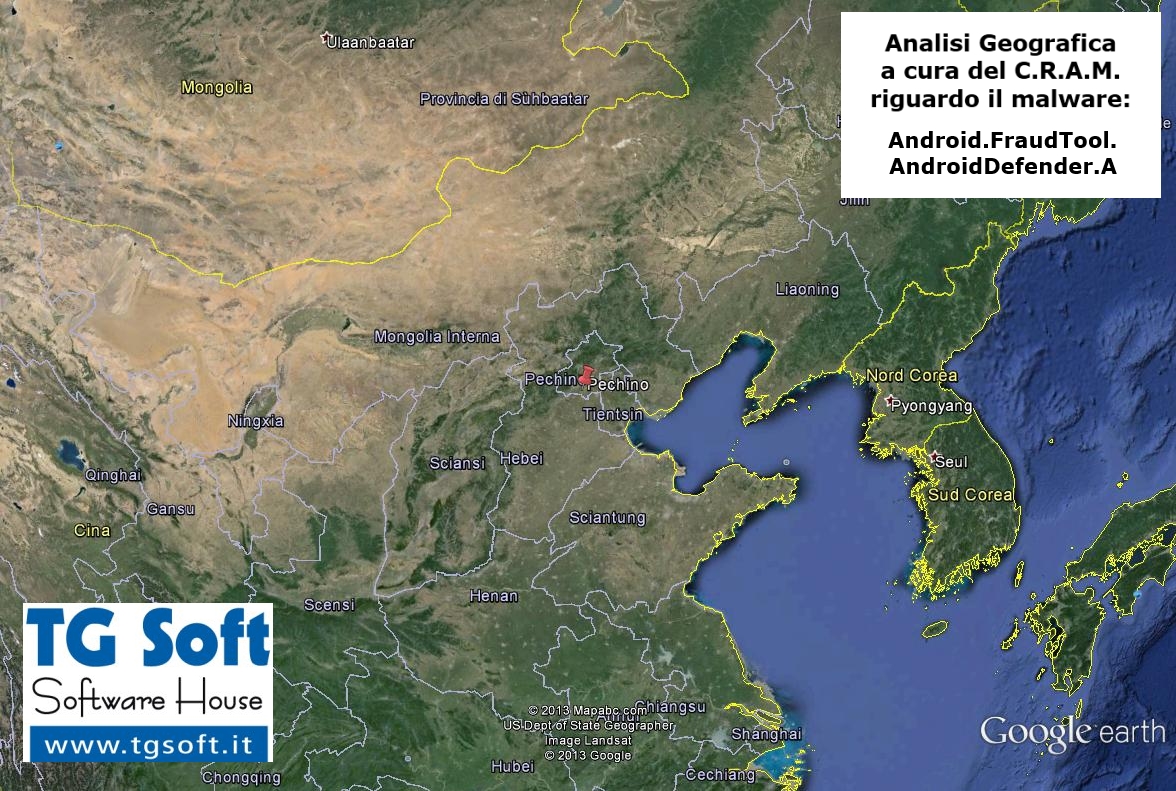
This domain results to be dislocated in
Beijing,
China, to have the name
host-219-235-1-127.iphost.gotonets.com and
IP Address
219.235.1.127.
Regarding the SQLite database, this has 5 tables (
i.e. android_metadata,
black_list,
scan_settings,
sqlite_sequence and
viruses_index). In particular, inside both the
CallReceiver and the
MessageReceiver classes, the malware uses the
black_list table to check if a number is blacklisted or not.
---------------------------------
Paolo Rovelli
Mobile Developer & Malware Analyst
CRAM (Anti-Malware Research Center) of TG Soft














