The CRAM (Anti-Malware Research Center of TG Soft) team has carried out a little study on the Android apps distribution platform by Google.
In order to perform a real-world protection test, we decided to connect on Google Play Store and download some of the most popular apps of the market. We have downloaded
a total of 500 apps, of which 9 were found to be malicious. According to these number, then,
1.8% of the apps on Google Play are actually malicious.
Of course, this study should definitely not be considered complete. Indeed, the dataset studied is rather too small to asses the overall safety of Google Play Store. However, it can give a rough idea.
| Icon |
App |
Downloads |
Malware |
 |
Talking Tom & Ben News Free
com.outfit7.talkingnewsfree |
10.000.000-50.000.000 |
Adware.Youmi |
 |
Tom ama Angela
com.outfit7.tomlovesangelafree |
10.000.000-50.000.000 |
Adware.Youmi |
 |
FIFA 2014 - The Soccer Game
com.tam.soccer.free.game |
500.000-1.000.000 |
Adware.Airpush |
 |
File Manager Pro
org.tellmej.filemanager |
100.000-500.000 |
Adware.Airpush |
 |
Sketch Pad
dex.dex.dex5 |
50.000-100.000 |
Adware.Plankton |
 |
Naked Scanner Magic
com.naked.scanner.magic.fun.app |
10.000-50.000 |
Adware.Airpush |
 |
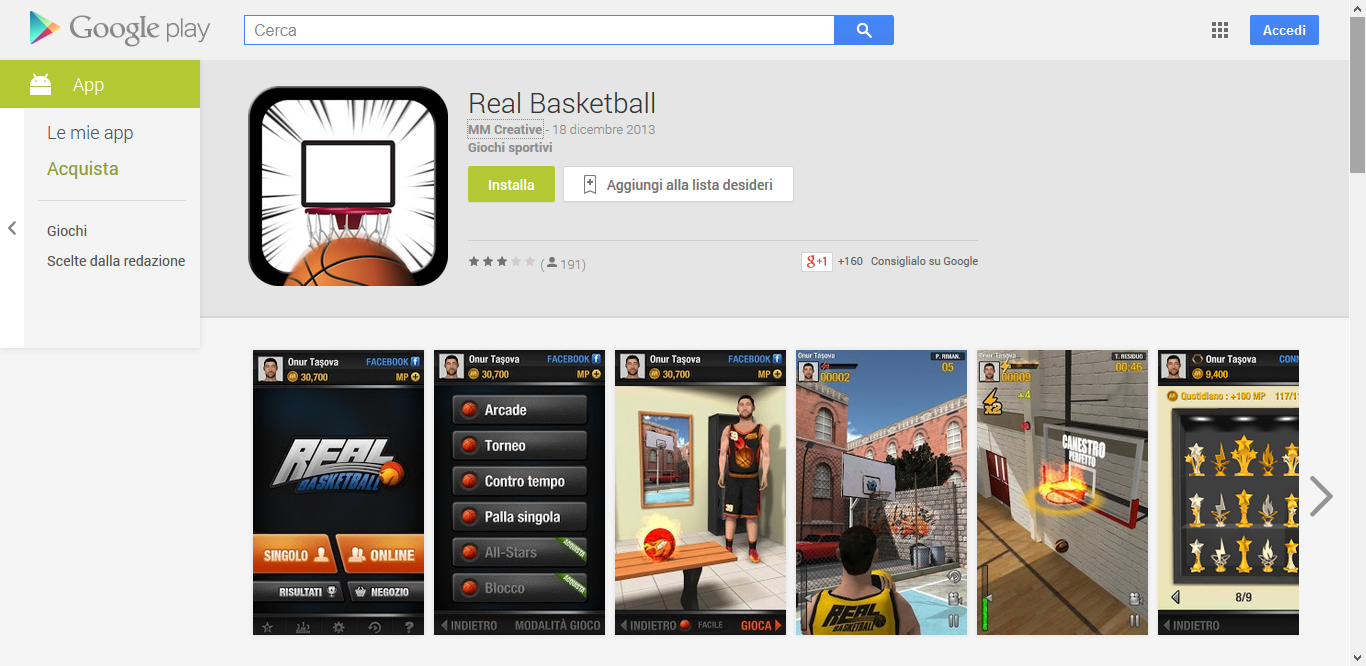
Real Basketball
com.bktballelite.com |
10.000-50.000 |
Trojan.FakeMarket |
 |
Cricket 2014
com.tam.cricket.free.game |
1.000-5.000 |
Adware.Airpush |
 |
Mp3 Cutter - Ringtone Maker
com.best.ringtone.maker.music.cutter |
1.000-5.000 |
Adware.Airpush |
In particular,
8 of the malware discovered are Adware which just display annoying, often misleading advertisements and are detected by most of the commercial Android Anti-Virus solution. However, one of them (i.e.
"Real Basketball") is a zero-day, or next-generation malware that is
not yet detected by any of the commercial Anti-Virus solutions. This is
a Trojan which pretends to be nothing less than Google Play itself (which is quite funny since it is distributed on the real Google Play Store)!
Browsing the Google Play Store, the Trojanized app pretends to be a basketball videogame.
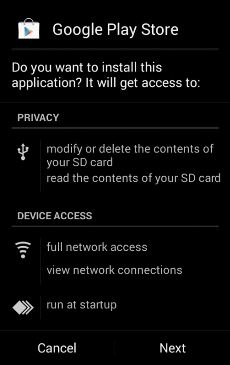
However, when you download it, the Trojan will be installed as:
"Google Play".
If we launch it, the malware will open the Google Play Store page of Facebook. However, in background, it will start to connect to several web pages at the unbeknownst of the user. Some of these websites are:
- redirects.ero-advertising.com
- banners.ero-advertising.com
- adspaces.ero-advertising.com
- www.fethullahhocam.com/advertising.php
- www.mobilefilmizle.com/ipzaman.php
In particular, the
URLs of the
ero-advertising.com website are of the form:
http://redirects.ero-advertising.com/speedclicks/in.php?pid=[...]&siteid=[...]&spaceid=[...]&mdoc=[...]
Where
pid,
siteid and
spaceid are differents IDs while
mdocwill contain the actual
URL that will be opened, such as:
- www.xnxxvideosesso.com
- www.youpornitaliano.tv
- www.maxsesso.com
It is very likely the Trojan uses this technique to earn money through the imitation of user's
"clicks" on various ads. This cyber attack is known as:
click fraud.
All the apps have been all reported to Google. Hopefully, Google will proceed to remove these malware from the market soon.
-------------------------
Paolo Rovelli
Mobile Developer & Malware Analyst
CRAM (Anti-Malware Research Center) by TG Soft S.a.s.