The objectives of the C.R.A.M.:

- PROMOTE and SPREAD in our country the culture and awareness of IT security in all its aspects.
- SUGGEST and PROPOSE conscious attitudes about Information Security and, in particular, which behavior user and IT consultants should take care about in order to deal with new virus/malware infections.
- PROVIDE support about IT security to private and industry customers.

- FOCUS on behavior methodology to deal with the C.R.A.M. team to send virus/malware or suspicious files not detected or removed by your Antivirus software. Take a look at [I have problem with virus/malware what should I do?] to see how to deal with infections.
When you get in touch with virus, spyware, trojan, backdoor, adware, dialer, BHO, hijacker, fraudtools, rootkit and generally speaking malwares, you are presumably in front of one of the following situations:
- Some files are identify uniquely from Vir.IT eXplorer, but I can't remove them.
- Some file are identify from Vir.IT eXplorer as a possible variant of {virus name}.
- A software has put itself in auto execution and the Intrusion Detection technology, integrated in Vir.IT Lite Monitor and Vir.IT Security Monitor, has warn me about what is happening.
- I have the suspect that my computer is infected (computer slowdown, strange behavior, advertising popping-up everywhere when surfing or simply when I use my computer, [other]) by a new malware/virus generation or not yet detected by my current AntiVirus signatures.
Click on the elements that more is close to your situation, in order to understand what to do to get rid of the infection thanks to the TG Soft's C.R.A.M. team.
- The virus/malware is detected uniquely but it is not removed:
If you are facing an infection that is detected uniquely by Vir.IT eXplorer there should be no problem. If Vir.IT eXplorer is used correctly the infection can be removed with no problem. If not, it is suggested to contact the C.R.A.M. team in order to get support. By using assistenza@viritpro.com you can get in touch with the team (Available only for costumers of the PRO version of Vir.IT eXplorer PRO);
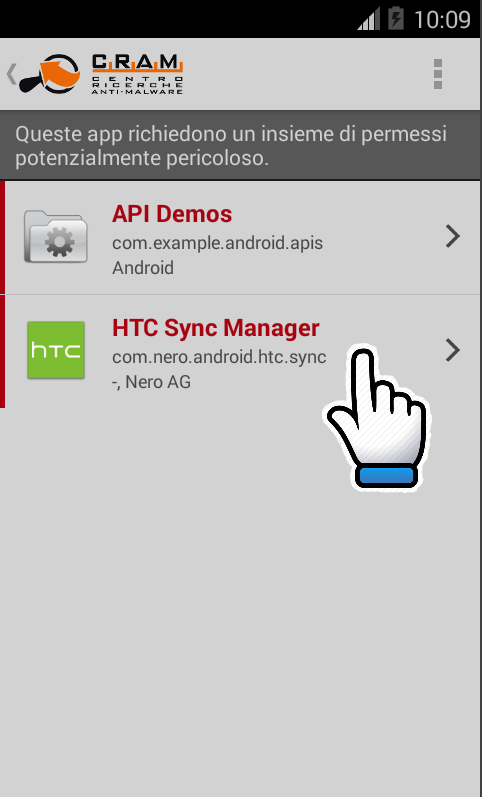
- The virus/malware is identified as a possible variant of {virus_name}:
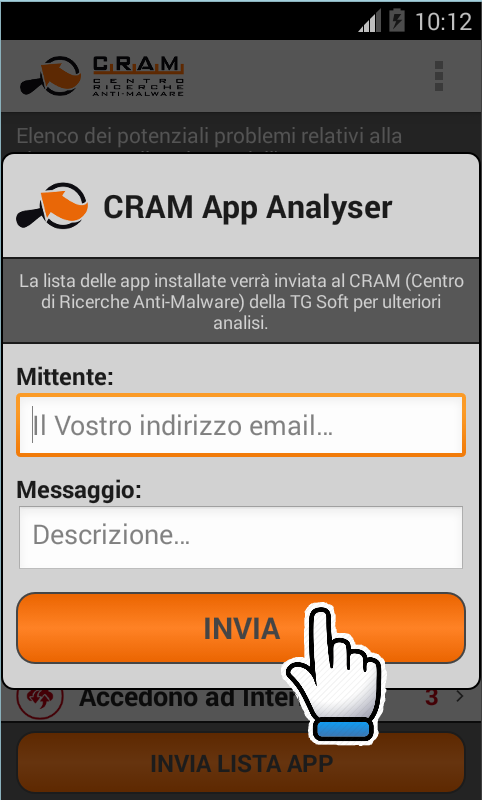
if you have come into contact with a virus / malware identified by Vir.IT eXplorer as a possible variant of {virus_name}, being a variant, the software will not be able to correctly remove the problem. In this case it is necessary to send the file reported to the CRAM (AntiMalware Research Center of the TG Soft).
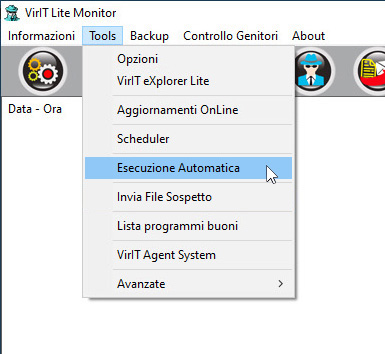
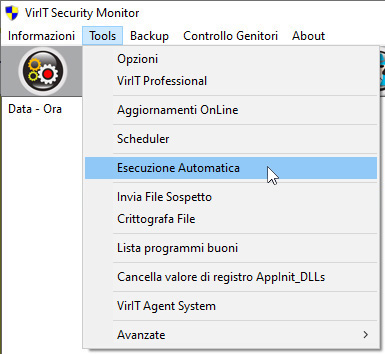
From Vir.IT Lite Monitor or from Vir.IT Security Monitor, come you can see from the pictures, it will be files marked as possible variants can be selected and sent.
Sending files to CRAM (AntiMalware Research Center) it does not involve any expense for the user. Priority analysis will be given to customers in assistance of the AntiVirus, AntiSpyware, AntiMalware and AntiRansomware CryptoMalware protection suite Vir .IT eXplorer PRO.
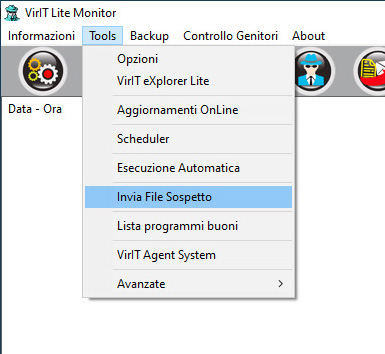
Send suspicious files from Vir.IT eXplorer Lite with Vir.IT Lite Monitor
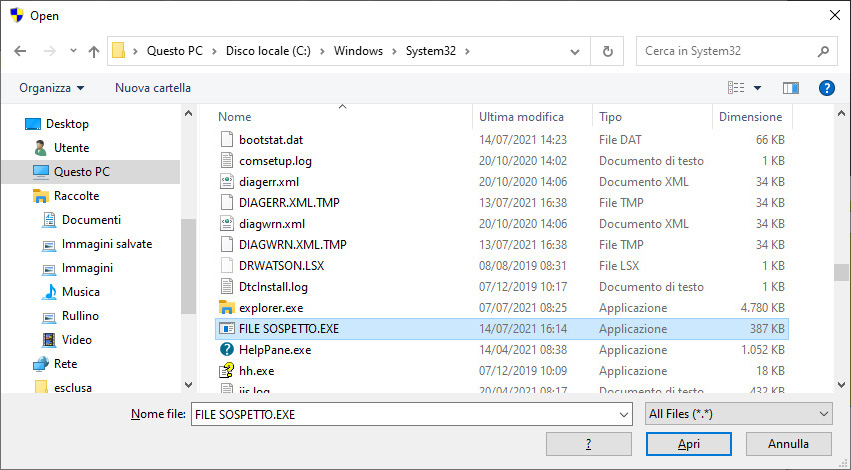
Send suspicious files from Vir.IT eXplorer PRO with Vir.IT Security Monitor 
In both cases a standard window of Microsoft Windows will pop-up and let the user choose the file detected by Vir.IT as a {virus_variant}, the image above shows the window displayed after clicking on the Send a suspicion file (PRO/Lite version).


Many user and many security consultants think that AntiVirus can stop all types of virus/malware affecting nowadays networks. This belief, as can be simple understood, is not true. Indeed, if it would be true, AntiVirus software would not have the necessity to be constantly updated. An AntiVirus software receives new signatures across with new engines only when a new type of infection is discovered in the wild, ie after a user is hit by the infection and one of the may end user that are experiencing the same issue is quick enough to send the sample to its research center of reference.
The research center will proceed with the extraction of an identification signature and implement, when possible, algorithms for its removal.
There is no need to wonder if AntiVirus software can't identify a virus/malware. No anti-virus software is exempt from this reality. It is in this situation that some products can make differences taking care about the end user and offering a high level of support that other company doesn't consider.
TG Soft S.r.l., Software House specialized in Information Security since 1993, develops AntiVirus and AntiMalware software solutions, has always had the intellectual honesty to present this problematic and focus not only on already known infections, but also and especially on new generation of virus/malware and/or not yet detected by the current version of their software.
TG Soft with the goal of support end users with its security software solutions, makes available the Vir.IT Intrusion Detection technology that allows a constant protection of the system. In the case the computer is hit by a new generation virus/malware, Vir.IT displays an information window in the center of the monitor warning the end user about a new strange activity detected on the computer. With a simple 'click' the user can decide to send the detected file to the C.R.A.M. for a first analysis. In the case the file is discovered to be a new type of virus/malware, new signatures and algorithms are created to sanitize the infection and clean the computer.
As already stated some users and IT consultant are thinking (wrongly) that AntiVirus can detect all virus/malware already discovered and not yet discovered.
When your AntiVirus software doesn't detect a virus/malware, generally in the mind of the end user and sometime in the retailer of the software solution as well, is popping up the idea that the purchased software isn't infallibility. The problem can't be found in the fallibility of the product, instead, in the wrong idea, that the software is INFALLIBILY.
Unfortunately no AntiVirus software is foolproof and as already stated, the only way a company can be sure that its AntiVirus is detecting and removing infections is making analyse the infection to its team. This is obviously possible only if an infected user is quick enough in sending a sample of the infection to his research center of reference.
It is in this situation that it is possible to see the quality of the delivered service. If the AntiVirus software has no tools for sending suspicious files or program set in Auto Run mode it does mean that the AntiVirus software has no care about end users problematic.
From long time TG Soft makes available the possibility to send suspicious and/or infected file to its laboratory. The steps to follow in order to send a file can be done in few clicks.
We want to emphasize one more time that in order to get a solution it is fundamental send the problem. Prevent sending suspicious file does mean that in further version of the AntiVirus software it is possible that your specific infections will not be detected and remove.
We suggest to follow the steps below:
- Send suspicious and/or infected files to TG Soft, through the Vir.IT Intrusion Detection technology;
- Aside from sending suspicious and/or infected files, it can be useful send the list of Auto Run programs; from its analysis TG Soft researcher can understand if there are malicious files;
- After this two actions are made, the user has to wait the C.R.A.M. analysis, in the meantime the user is free to try to discover new solutions to fix as fast as possible his/her problem but we suggest to avoid this approach. If something get wrong, the end user can make more damage than the infection;
- After the solution developed by the C.R.A.M. team is made available to the end user, stick to the instructions written in the email to get rid of the infection/problem detected on the computer.
Take up to date your computer with all security patches proper of the Operating System (with Microsoft Windows Update), and take always an eye on the IE browser security updates. Going to http://www.update.microsoft.com/;
Take up to date your AntiVirus software and make cross check with different IT software solutions. For this purpose we suggest to try Vir.IT eXplorer Lite, that is developed with the idea to be interoperable with any other AntiVirus solutions already installed on the computer: download Vir.IT eXplorer Lite;
Avoid to open attached elements coming from unknown people or strange messages coming from known person, for example your director sends you a file or a link with explicit pornography images or videos;
Avoid to get played from social engineering technique, by tricky messages that informs you about a winning price, goods or services, because in most of the cases you will be asked to click on a link.
The link can refer to a virus/malware or to 'form' that needs to be compiled. If the user is using his/her true personal information the 'bad guy' will store your date and sell them to others or just force you to download a new generations virus/malware on your computer;
Avoid the use of peer-to-peer software. Peer-to-peer solutions like eMule, KaZaA, DC++, and many others, are used by virus-writer to distribute their new creations that are masked as genuine files. In most cases these files are inside the top ten files more downloaded from users.;
Prevent to visit non institutional website. (example. Pornography, cracks, illegal sharing website, etc).
Some of these website tracks users activity in order to send advertising Pop-Ups while the user is surfing on the web;
Prevent to fall in the fraudtool tricks. These are scareware software, like fake AntiVirus that thanks to an attractive interface convince the end user that the computer is infected, at the same time they try to play the user to buy the full protection of the rouge AntiVirus in order to get rid of all the detected (false) infections. Of course if the user wants to buy the fake AV (in most cases) the proposed solution is through a credit card;