CRAM researchers at
TG Soft have detected a new variant of Mimic Ransomware called "Hairysquid".
Mimic Ransomware has already been known to the IT community since the summer of the year 2022, while there was no information until now about this new variant which adds the .
Hairysquid extension, the Ransomware name, to the files.
Below is an example of an encrypted file:
| [ORIGINAL_FILE_NAME].[ORIGINAL_TYPE_EXTENSION.[HAIRYSQUID] |
Below is an image of the
Hairysquid dump thas looks like a modified version of the original
Mimic Ransomware.
Another interesting feature is highlighted when we examine the date the file was compiled :
28-10-2022. This clue is further evidence that
Hairysquid turns out to be a newer version of the previously mentioned
Mimic Ransomware.
The ransomware is extracted from an executable file with dropper functions. In this case it is a "
dropper-unpacker" malware that contains within it the final ransomware payload and all the
libraries necessary for its proper functioning. The unpacking step is done through one of the
libraries inside the dropper called 7
Zip.
Once the dropper is double-clicked, the ransomware is extracted and executed within the directory "%localappdata%" where a folder is created (with the name in the form of CLSID [Class Identifier])
which contains the libraries.
The "session.tmp" file is used to continue the encryption in case of an interruption.
To make it more "efficient" and fast, the initial process is replicated several times to divide the tasks and perform more operations simultaneously.
The faster the encryption, the less chance the antivirus has of thwarting the ransomware at the initial stage of encryption.
In the
first phase, the
DC.exe (DefenderControl) process is executed, through which the ransomware disables
Windows Defender protection and modifies Windows
GroupPolicy:
|
RegCreateKeyExW -> HKLM\SOFTWARE\Policies\Microsoft\Windows Defender
RegSetValueExW -> ValueName: DisableAntiSpyware
|
The Windows registry key is modified to disable Real-Time-Protection of Windows Defender:
| Key: SOFTWARE\Microsoft\Windows Defender\Real-Time Protection |
Disabling Windows Defender is essential for the ransomware to work properly because if no antivirus program is present on the PC, Windows Defender is the first to thwart the malicious program.
A file called "Registry.pol" is also created inside the path "C:\Windows\System32\GroupPolicy\Machine\" which disables Windows AntiSpyware via Windows policies. Below are the contents of the above file:
| "PReg[Software\Policies\Microsoft\WindowsDefender;DisableAntiSpyware;]" |
In the
second phase, a list of all physical and/or virtual directories (folders/disks) is created. This is done through
libraries included in a software called "
Everything".."
Everything" is a utility that allows the user to quickly locate all files/directories on the victim's computer and then proceed with their encryption. Once the directories and folders on the PC have been identified, they are entered into a text database called "
Everything.db" used to later retrieve information useful for data encryption.
The extensions that are considered by Hairysquid for data encryption are as follows:
3g2;3gp;3gp2;3gpp;amr;amv;asf;avi;bdmv;bik;d2v;divx;drc;dsa;dsm;dss;dsv;evo;f4v;flc;fli;flic;flv;hdmov;ifo;ivf;m1v;m2p;m2t;m2ts;m2v;m4b;m4p;m4v;mkv;mp2v;mp4;mp4v;mpe;
mpeg;mpg;mpls;mpv2;mpv4;mov;mts;ogm;ogv;pss;pva;qt;ram;ratdvd;rm;rmm;rmvb;roq;rpm;smil;smk;swf;tp;tpr;ts;vob;vp6;webm;wm;wmp;wmv;video;ext:ani;bmp;gif;ico;jpe;jpeg;
jpg;pcx;png;psd;tga;tif;tiff;webp;wmf;pic;ext:bat;cmd;exe;msi;msp;scr;exe;ext:c;chm;cpp;csv;cxx;doc;docm;docx;dot;dotm;dotx;h;hpp;htm;html;hxx;ini;java;lua;mht;mhtml;odt;pdf;potx
;potm;ppam;ppsm;ppsx;pps;ppt;pptm;pptx;rtf;sldm;sldx;thmx;txt;vsd;wpd;wps;wri;xlam;xls;xlsb;xlsm;xlsx;xltm;xltx;xml;doc;ext:7z;ace;arj;bz2;cab;gz;gzip;jar;r00;r01;r02;r03;r04;r05
r06;r07;r08;r09;r10;r11;r12;r13;r14;r15;r16;r17;r18;r19;r20;r21;r22;r23;r24;r25;r26;r27;r28;r29;rar;tar;tgz;z;zip;zip;ext:aac;ac3;aif;aifc;aiff;au;cda;dts;fla;flac;it;m1a;m2a;m3u;m4a;
mid;midi;mka;mod;mp2;mp3;mpa;ogg;ra;rmi;spc;rmi;snd;umx;voc;wav;wma;xm; |
In the third phase, a series of powershell.exe processes are executed to search for virtual machines present within the PC; this search is important because large companies very often use server machines that host within them virtual machines used by various users inside the company.
Obviously, these virtual machines turn out to be a great "loot" for criminals since, once encrypted, they will no longer be usable by users.
|
powershell.exe -ExecutionPolicy Bypass "Get-VM | Stop-VM"
powershell.exe -ExecutionPolicy Bypass "Get-Volume | Get-DiskImage | Dismount-DiskImage
powershell.exe -ExecutionPolicy Bypass "Get-VM | Select-Object vmid | Get-VHD | %{Get-DiskImage -ImagePath $_.Path; Get-DiskImage -ImagePath $_.ParentPath} | Dismount-DiskImage"
|
In the fourth phase, all ongoing remote connections are closed, so that connected users are disconnected and have no longer control over the machine. At the same time, the TaskManager is shut down and disabled. In addition the registry key is changed to completely disable its execution. In this way the user is not given the opportunity to close the running malicious process before it finishes encryption.
In addition the processes include:
- powercfg.exe with which it disables system shutdown, suspension and hibernation
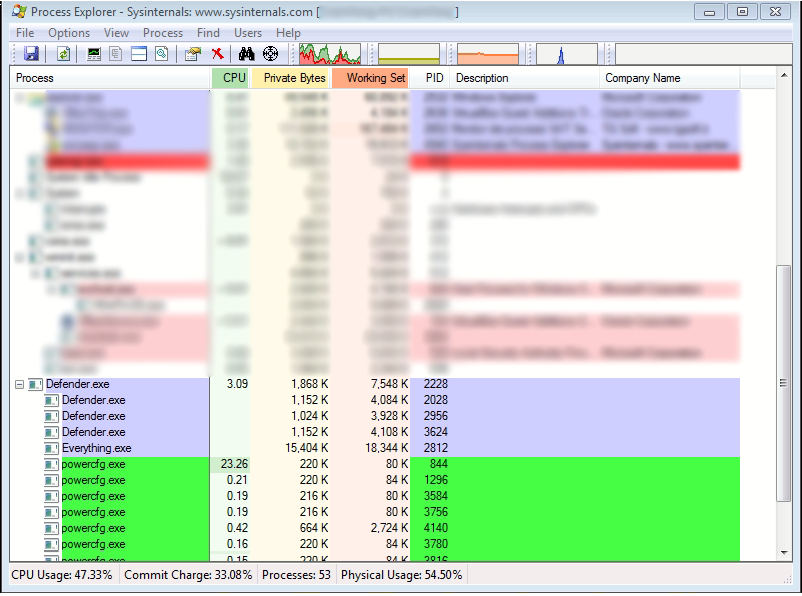
- bcdedit.exe used to inhibit system configuration restoration:
- wbadmin.exe Used to delete backups of the system configuration
- wmic.exe with which it deletes shadow copies of Windows
When the encryption is finished, a folder named "temp" is created on the C: drive. It contains a text file called "
READ_ME_DECRYPTION_HAIRYSQUID.txt" in which we find the contact details of the crimnals, instructions for making the ransom payment, and information for receiving the decryptool useful for decrypting the data.
Immediately after that, a registry key is created inside the path
| HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
with the name:
Defender.exe with the value > notepad.exe "C:\temp\READ_ME_DECRYPTION_HAIRYSQUID.txt"
which, each time the PC is started, shows the ransom request. See below:
In the ransom payment instructions we also find ways to contact the criminals via various messaging channels such as:
- Tox Messenger
- ICQ Messenger
- Skype
- eMail
Vir.IT Anti-Ransomware Crypto-Malware protection
Vir.IT eXplorer PRO when installed and properly configured and running in the machine, through AntiRansomware protection with heuristic-behavioral technologies, protects user's data from encryption operated by Hairysquid ransomware..
Cases like this are proof of the importance of defending our data with proper anti-cryptomalware security systems.
.
 TG Soft
TG Soft has developed and integrated since May 2015 in the
Vir.IT eXplorer PRO suite - the only product with a proprietary engine developed 100% in Italy - AntiVirus, AntiSpyware and AntiMalware,
AntiRansomware Crypto-Malware protection technologies. These through the heuristic-behavioral approach, are able to block the encryption process in the initial phase of the attack saving, on average, at least 99.63% of the data files otherwise potentially encrypted without this protection.
In addition, as a last parachute for some data files that may be neither restorable nor recoverable by the integrated restore/recovery tools, we can restore them from
Vir.IT BackUp integrated in the Vir.IT eXplorer PRO suite.


For more information on these technologies which are 100% developed in Italy, you can contact the
TG Soft Cyber Security Specialist administrative office, sending an email to
segreteria@tgsoft.it or calling the telephone number 049.8977432.
IOC:
|
Defender.exe - C79880E4F6EEAED9DB48F90B38194921
7za.exe - B93EB0A48C91A53BDA6A1A074A4B431E
DC.exe - AC34BA84A5054CD701EFAD5DD14645C9
Everything.db - D7FEAD971A5662B49246B0C6853C5E47
Everything.exe - C44487CE1827CE26AC4699432D15B42A
Everything.ini - 8AD3CA3A5B7714356966A44FEFA60033
Everything2.ini - 51014C0C06ACDD80F9AE4469E7D30A9E
Everything32.dll - 3B03324537327811BBBAFF4AAFA4D75B
Everything64.dll - C1FEB33322A621C16474E3C56DB9A3FF
sdel.exe - 803DF907D936E08FBBD06020C411BE93
sdel64.exe - E2114B1627889B250C7FD0425BA1BD54
|
written by :
Breabin Radu
Callegaro Samuele
Canova Massimo
C.R.A.M.
TG Soft's Anti-Malware Research Center


 TG Soft has developed and integrated since May 2015 in the Vir.IT eXplorer PRO suite - the only product with a proprietary engine developed 100% in Italy - AntiVirus, AntiSpyware and AntiMalware, AntiRansomware Crypto-Malware protection technologies. These through the heuristic-behavioral approach, are able to block the encryption process in the initial phase of the attack saving, on average, at least 99.63% of the data files otherwise potentially encrypted without this protection.
TG Soft has developed and integrated since May 2015 in the Vir.IT eXplorer PRO suite - the only product with a proprietary engine developed 100% in Italy - AntiVirus, AntiSpyware and AntiMalware, AntiRansomware Crypto-Malware protection technologies. These through the heuristic-behavioral approach, are able to block the encryption process in the initial phase of the attack saving, on average, at least 99.63% of the data files otherwise potentially encrypted without this protection.
