
15/03/2016
17:29

| A new variant of the TeslaCrypt ransomware, namely TeslaCrypt 4.0, has been identified. The evolution seems to have taken place in two phases. The first phase has been the release of a newer core for the TeslaCrypt; a different library for AES encryption is used, and then files are renamed by adding the .mp3 extension. In the second phase has been the evolution of TeslaCrypt into its fourth version, TeslaCrypt 4.0, which encrypt files without renaming them (i.e. without adding an extension like its "predecessors"). |
INDEX==> How TeslaCrypt 4.0 works==> The ransom demanded by TeslaCrypt 4.0 ==> How to stay safe from TeslaCrypt 3.0 ==> How to contain TeslaCrypt 4.0 encryption damage ==> Is it possible to decrypt encrypted files?
|
|
| So far, it looks like TeslaCrypt 4.0 is being spread via infected websites - navigation on such websites causes infection and execution of this new variant. | ||
| !secp256k1_fe_is_zero(&ge->x) pubkey != NULL input != NULL outputlen != NULL *outputlen >= ((flags & SECP256K1_FLAGS_BIT_COMPRESSION) ? 33 : 65) output != NULL seckey != NULL secp256k1_ecmult_gen_context_is_built(&ctx->ecmult_gen_ctx) result != NULL point != NULL scalar != NULL |
This only occurs if Vir.IT eXplorer PRO is:
Starting with version 8.1.31, Vir.IT eXplorer PRO can "snatch" TeslaCrypt 4.0 encryption key on-the-fly in the early stages of the attack, thus making a decryption feasible - it can be done with the assistance from TG Soft's tech support.
Remember - every time the malware is executed, a new encryption key is used. This means that every time the computer is rebooted and the malware is still active, TeslaCrypt will use a different key (n reboots → n+1 different keys).
Since a new key is created every time the malware is executed - which only happens when the computer is rebooted - the computer should always stay turned on, in order to have the minimun number of keys possible, and qualified tech support (such as TG Soft's) should be contacted immediately.
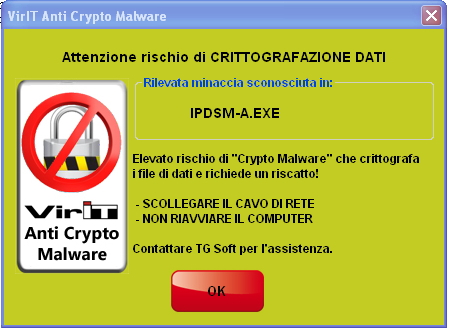
When the Alert shown in the picture pops up on the screen, Vir.IT eXplorer PRO's Anti-CryptoMalware module has come into action, halting the malware. Do not panic and perform these operations:
In case of cryptomalware attack you should get in touch with Vir.IT eXplorer PRO's Tech Support as soon as possible. You can write an email to assistenza@viritpro.com, or call +39 049 631748 - +39 049 632750, Mon-Fri 8:30-12:30 and 14:30-18:30.
|
 Click to show the picture fullscreen 99,63%* Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO |
| We invite you to be very careful when opening email attachments. If you are not waiting for a parcel then you really shouldn't open emails like the one we analyzed. Always double-check the sender's email address (which is not the sender's name) before opening an attachment. If you opened an infected attachment and an encryption started to take place, you could either:
TG Soft Public relations |