C.R.A.M. by
TG Soft discovered a new cryptomalware, detected by
Vir.IT eXplorer PRO 8.1.35 like
Trojan.Win32.CryptoRokku.A
FILE NAME: bg.jpg.exe
MD5: 97512F4617019C907CD0F88193039E7C
SIZE: 681894 byte
How CryptoRokku manifests itself
There are currently no further information about the nature of the sample and the methods of spread of this cryptomalware.
After the encription process, the malware creates information about ransom in folders in two separate files:
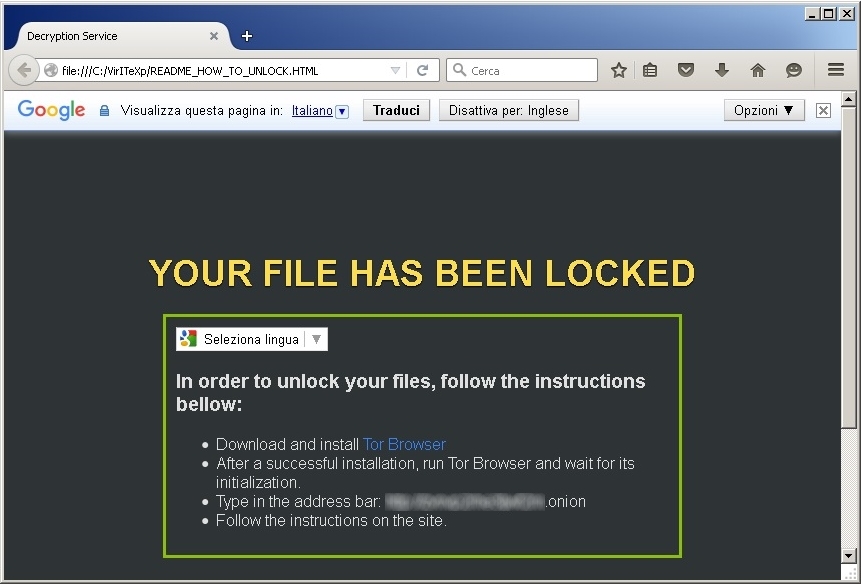
- README_HOW_TO_UNLOCK.TXT contains:
YOUR FILE HAS BEEN LOCKED
In order to unlock your files, follow the instructions bellow:
1. Download and install Tor Browser
2. After a successful installation, run Tor Browser and wait for its initialization.
3. Type in the address bar: http://zvnvp2rhe3ljwf2m.onion
4. Follow the instructions on the site.
- README_HOW_TO_UNLOCK.HTML contains the ransom in HTML format. As you can see they are using Google Translate components for easy and fast translations.
Click to enlarge
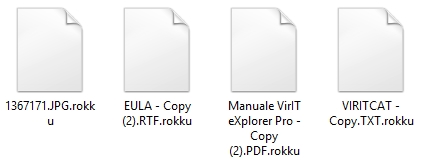
| In the right image the Trojan.Win32.CryptoRokku crypt files keeping names and their original extensions but it adds a second extension .rokku. |
Click to enlarge |
Back to top
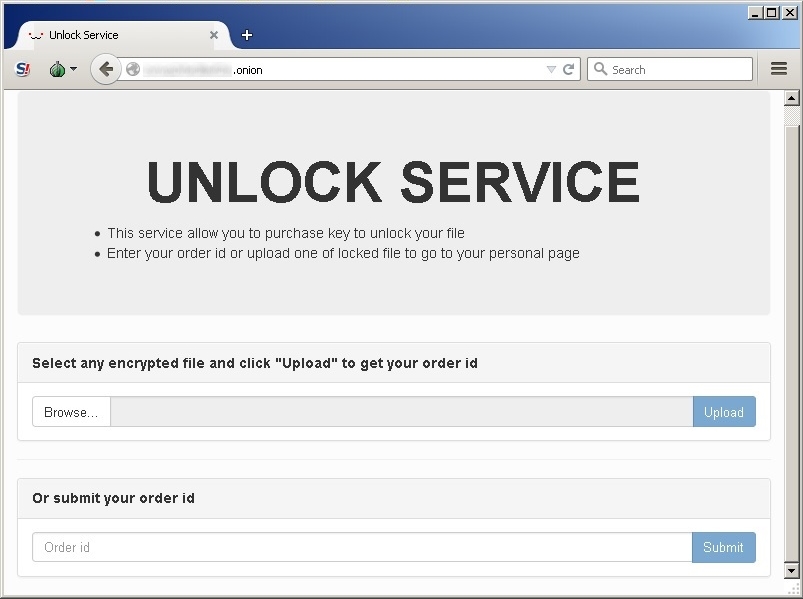
CryptoRokku's ransom
In the right image you can see Unlock page: first you need to upload a crypted file to recover your personal infection code (order-id).
You can reconnect to the page also later without the need to upload again the file but inserting the personal code. |
Click to enlarge |
Click to enlarge |
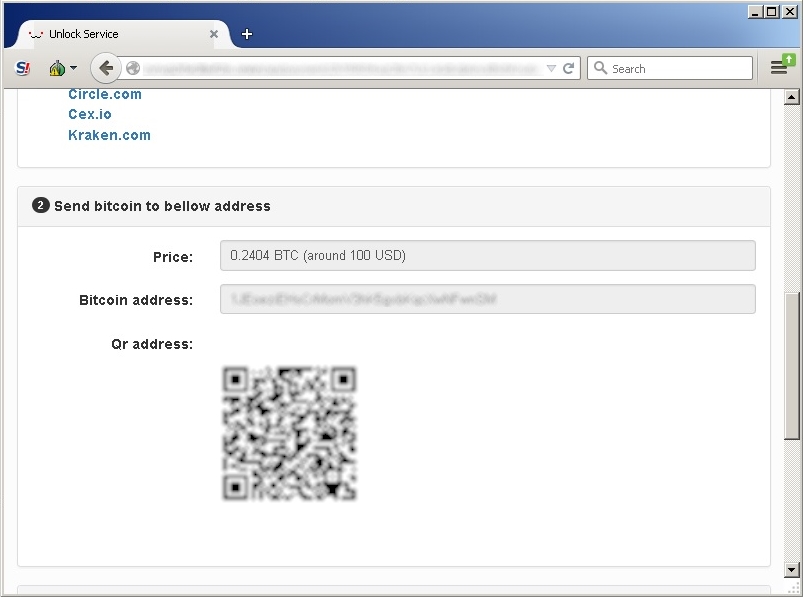
The ransom amount is about 100$, one of the most economic from the cryptomalware family.
The bitcoin address is also avalaible with qr code. |
From the unlock page there is the possibility to download the decryption tool.
The ROOT KEY is the key that permit you to decrypt all files and will be realeased only after the payment.
It's also available the possibility to decrypt only one file: you need to upload a file and will be realease a single key that can decrypt only the uploaded file. |
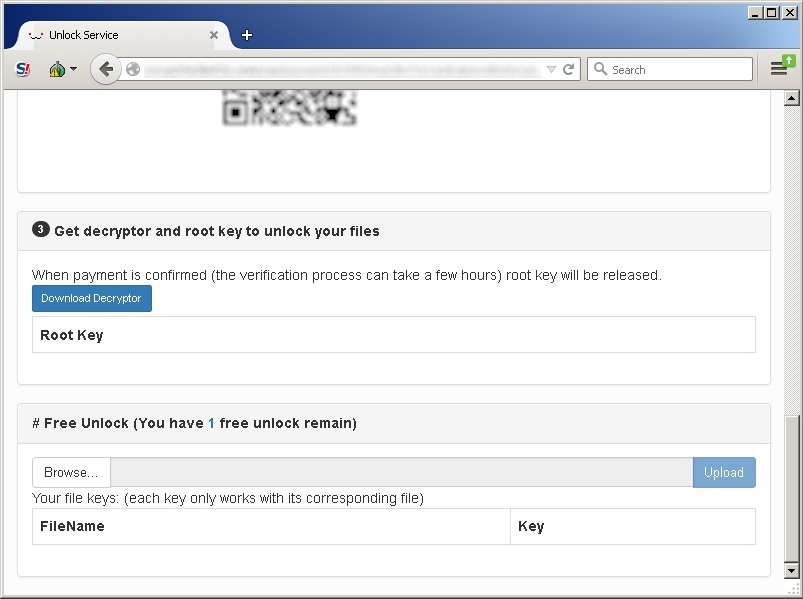
Click to enlarge |
Back to top
How to protect yourself from CryptoRokku
As a general rule, we should never forget that behind every link or any attachments of each email could hide malware or Crypto-Malware.
Good practice would avoid clicking on links or on e-mail attachments that arrive as strangers or by people who seem known but with unexpected attachments.
If you unfortunately have executed the mail attachment which unleashes the hell of this new family of Crypto-Malware called CryptoRokku and you are customer of Vir.IT eXplorer PRO, we have one or more possibilities to save our precious files from the cryptography!
As already reported Anti-CryptoMalware's technology integrated in Vir.IT eXplorer PRO, if correctly installed, configured, updated and used, can block these attacks and save files from the cryptomalware until 99,63% of files and it permits the recover of crypted files in the initial phase of attack until 100% thanks to Backup's technologies integrated:
- BackUp-On-The-Fly;
- Vir.IT Backup.
We remember that this can only happen if certain proper:
- INSTALLATION;
- UPDATING of signatures and engine;
- CONFIGURATION of real time protection Vir.IT Security Monitor with activated flag "Anti-Crypto Malware Protection" from the option menu and activated Vir.IT BackUp, an advanced backup that give the assurance of having a secured copy of files that is protected from cryptomalware's attack.
Back to top
What to do to mitigate damage from CryptoRokku
When the alert message (like the one you can see in the right image) shows itself means that the Anti-CryptoMalware protection has blocked the attack and avoiding panic you need to:
- UPDATE Vir.IT eXplorer PRO signatures;
- DISCONNECT LAN CABLE ==> in this way it'll isolate that PC/SERVER from others pc that are connected with the infected one.
- DO A FULL SCAN with Vir.IT eXplorer PRO on the entire disk to eliminate the CryptoRokku.
- DON'T REBOOT THE COMPUTER ==> If you shutdown or reboot the pc the CryptoRokku can re-start to crypt your files so we encourage you to keep your PC/SERVER turned on and contact, as soon as possible, our technical support by writing an email to assistenza@viritpro.com and next, if you are in Italy, contacting telephone numbers 049.631748 e 049.632750 available, for free, in labor days from Monday to Friday 8:30am-12:30am e 2:30pm-6:30pm.
|
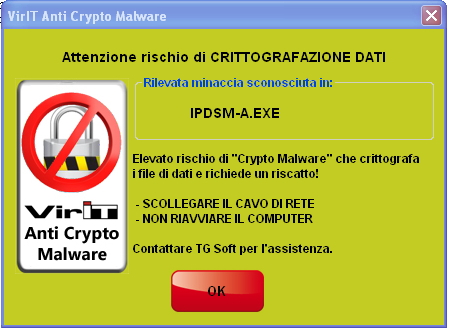
Click to enlarge
99,63%*
Expectation average percentage of saved files from encryption thanks to Anti-CryptoMalware protection of Vir.IT eXplorer PRO
|
Back to top
Are there possibilities to recover cipher files?
With the Anti-CryptoMalware protection integrated in Vir.IT Security Monitor, the number of crypted files from CryptoRokku won't be more than ten.
Files lost between the cryptomalware's attack and the Vir.IT's block should be replaced with backup copies. Currently there aren't any tools to decrypt crypted file with .rokku extension.
Back to top
Final thoughts
We invite everyone to be careful with opening and/or executing email attachments or clicking on link even if email arrives from known sender.
We advice you to check in advance sender before opening and/or executing email contents.
If you unfortunately has been executed the mail attachment which unleashes the hell of this new family of Crypto-Malware we invite you to keep calm because you can find yourself in one of these situations:
- you are customers of Vir.IT eXplorer PRO and when it's properly installed, configured, updated and you follow informations from alert message of Anti-CryptoMalware technology will permits you to save from cryptomalware's attack your files until 99,63% of your hard work;
- you don't have an Antimalware software that can report and/or block the cryptomalware's attack but anyway it will be worth always do the following sequences:
- DISCONNECT LAN CABLE;
- DON'T REBOOT your PC / SERVER for limit the damage. In this way, with some cases different from this cryptomalware, you can avoid to pay more than one key to decrypt your files.
Either way, remain calm and do not panic.
TG Soft
External Relations
Back to top







