The three-headed dog Cerberus from mythology to reality.
It has arrived also in Italy Cerber the talking crypto-malware, which encrypts the document files renaming them in .cerber.
The CryptoCerber had been identified for the first time earlier this month, but had not yet spread to Italy.
This new crypto-malware, uses the "SAPI.SpVoice" object to talk through your sound card, so it can alert the unfortunate victim that his documents have been encrypted.
Encrypted files by CryptoCerber will have random name withe .cerber extension. |
INDEX
==> Can I restore the encrypted files ?
==> Final thoughts

|
| |
CryptoCerber how it manifests...
|
For now it seems that the CryptoCerber has spread via compromised sites, surfing on these sites would result in the infection and then the execution of this new variant.
Filename: makecab.exe
MD5: 76dcde9e79f291a40276d402ad1e20b0
Size: 152543 byte
TimeStamp: 20/03/2016 09.25.56
|
|
When you run the CryptoCerber, the carrier file is moved from the current user folder %appdata% with name makecab.exe This file is put on automatic execution in several ways:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
[makecab] = %appdata%\Roaming\{2FC5AFB6-1BDA-FA2C-4A7C-3BC9BCCA37EE}\makecab.exe
HKEY_CURRENT_USER\Control Panel\Desktop
[SCRNSAVE.EXE] = %appdata%\Roaming\{2FC5AFB6-1BDA-FA2C-4A7C-3BC9BCCA37EE}\makecab.exe
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Command Processor
[AutoRun] = %appdata%\Roaming\{2FC5AFB6-1BDA-FA2C-4A7C-3BC9BCCA37EE}\makecab.exe
The encrypted files will have random name with .cerber extension:
At the end of encryption are issued the redemption instructions in the file "
# DECRYPT MY FILES #.txt":
C E R B E R
-----------
Your documents, photos, databases and other important files have been encrypted!
To decrypt your files you need to buy the special software – "Cerber Decryptor".
For more specific instructions, please visit your personal home page, there are a few
different addresses pointing to your page below:
---------------------------------------------------------------------------------------
1. http://decrypttozxybarc.dconnect.eu/54A0-7C12-B1E9-004E-XXXX
2. http://decrypttozxybarc.tor2web.org/54A0-7C12-B1E9-004E-XXXX
3. http://decrypttozxybarc.onion.cab/54A0-7C12-B1E9-004E-XXXX
4. http://decrypttozxybarc.onion.to/54A0-7C12-B1E9-004E-XXXX
5. http://decrypttozxybarc.onion.link/54A0-7C12-B1E9-004E-XXXX
---------------------------------------------------------------------------------------
If for some reasons the addresses are not available, follow these steps:
---------------------------------------------------------------------------------------
1. Download and install the "Tor Browser" from https://www.torproject.org/
2. Run it
3. In the "Tor Browser" open website:
http://decrypttozxybarc.onion/54A0-7C12-B1E9-004E-XXXX
4. Follow the instructions at this website
---------------------------------------------------------------------------------------
"...Quod me non necat me fortiorem facit."
|
Note the phrase in latin language written by the authors of the cryptomalware, bad omen: "...Quod me non necat me fortiorem facit" (what doesn't kill me, makes me stronger).
Ransom instructions in html format into file "
# DECRYPT MY FILES #.html":
Moreover CryptoCerber creates the following file "# DECRYPT MY FILES #.vbs" in VBScript:
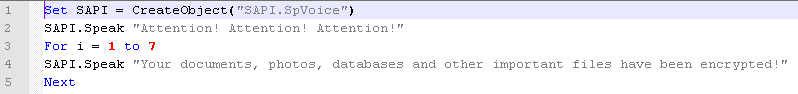
This script allows the Cerber talking to his victim, as you can listen to the following audio files: "DECRYPT MY FILES.mp3"
Back to top
The ransom demanded by CryptoCerber
Files that are encrypted by Crypto Cerber in order to be deencrypted require the payment of a ransom of about 1,000 dollars in BitCoin if it is paid within five days, otherwise it doubles to 2,000 dollars in Bitcoin..
How protect yourselves from CryptoCerber
As a general rule, we should never forget that behind every link or any attachments of each email could hide malware or Crypto-Malware. Good practice would avoid clicking on links or on e-mail attachments that arrive as strangers or by people who seem known but with unexpected attachments. If you unfortunately has been executed the mail attachment which unleashes the hell of the CryptoCerber variants and you are customer Vir.IT eXplorer PRO, you can restore any files encrypted by the attack using da Vir.IT BackUp, when properly configured and used!
As already reported to the Anti-CryptoMalware technology of Vir.IT eXplorer PRO when properly installed, configured, updated and used, has held up very well to these attacks managing to save the encryption up to 99.63% of the files and allowing the recovery of encrypted files in the initial phase of the attack up to 100% thanks to the integrated BackUp technologies:
- BackUp-On-The-Fly;
- Vir.IT Backup.
Giving for certain the correct:
- INSTALLATION;
- UPDATE both the signatures and the engine;
- CONFIGURATION in particular the resident shield of Vir.IT Security Monitor checking the "Crypto Anti-Malware Protection" from the real time options window of the resident shield as well as activated Vir.IT BackUp, advanced backup that allows you to have a copy of your work files preserved by encryption from which to proceed to recovery.
Back to top
What to do to mitigate the damage from CryptoCerber
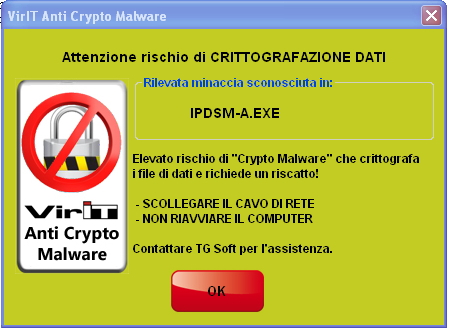
When the Alert screen appears, here on the side, means that the Anti-CryptoMalware integrated protection of Vir.IT eXplorer PRO is acting and then, avoiding getting caught by the "panic" NOT close the window and perform the steps that are indicated:
- Proceed to UPDATE the virus signatures;
- DISCONNECT THE LAN CABLE ==> In this way the PC / SERVER will be isolated from other computers that may be connected in the same LAN network, keeping confined the attack only on that computer.
- RUN a SCAN with Vir.IT eXplorer PRO all over the disk to detect the presence of TeslaCrypt variant.
- DO NOT REBBOT THE COMPUTER ==> Shutdown and subsequent restart of the PC / SERVER, in this particular situation, could gradually increase the number of files that the CryptoMalware is able to encrypt eluding the protection of Vir.IT eXplorer PRO. Then we invite you to KEEP the PC / SERVER TURNED ON and to contact, as soon as possible, our technical support writing an email, reporting the situation in place, at assistenza@viritpro.com and then contact the technical support numbers 049.631748 and 049.632750 available, for free, in the working days from Monday to Friday 8:30a.m.-12:30p.m. and 14:30p.m.-18:30p.m.
|
Click to enlarge
99,63%*
Average percentage expectation of saved files from encryption thanks to Anti-CryptoMalware protection Vir.IT eXplore PRO==> Check the information
|
Can I restore the encrypted files ?
With Anti-Crypto Malware security integrated in VirIT, the number of encrypted files from Cerber will be at most a few dozen.
The "sacrificed" files during the mitigation must be replaced with a backup copy, currently there aren't tools for recovering files .cerber.
Final thoughts
|
Of course we invite everyone to be careful when opening/run email attachments, even if they arrive from a known sender or browsing disreputable sites..
We point to preventively check the e-mail address of the sender before try to open/run the attachment..
|
| |
| |
In case you open/run the attachment and/or has been unleashed the encryption we invite you to keep calm, you could be in one of these situations:
- you are a customer of Vir.IT eXplorer PRO, if properly installed, configured, updated, used and following the indications of the Alert screen of the Anti-Crytpo Malware technology will allow you to save from the encryption your precious data files, on average, NOT less than 99,63% of your work;
- NOT have installed an AntiVirus software able to alert you and block encryption of files, anyway, proceed to:
- DISCONNECT THE LAN CABLE;
- DO NOT REBBOT THE COMPUTER in order to limit the number of different encryption keys through which, every time you restart, the remaining files are encrypted. This way, you will limit the cost of the ransom if should you decide to make the payment, choice absolutely not recommended.
Whether you are in case 1, where, thanks to Vir.IT eXplorer PRO and integrated Anti-CryptoMalware technologies you will have a really hope of saving from the encryption up to 100% of the data files of your work, both in the case 2, we invite you to keep calm.
TG Soft
External Relations


