
06/04/2016
15:10

| Il C.R.A.M. di TG Soft ha individuato una nuova famiglia di cryptomalware, quella del HydraCrypt (CryptoXXX). Questo cryptomalware crittografa file di documento (come .txt, .doc, .ppt, .mdb, .xls, etc), e li rinomina aggiungendo l'estensione .crypt. Per decrittografare i file, anche in questo caso viene richiesto un riscatto in BitCoin. |
INDICE==> Come si manifesta HydraCrypt==> Il riscatto richiesto da HydraCrypt ==> Come proteggersi da HydraCrypt ==> Come comportarsi per mitigare i danni derivanti da HydraCrypt ==> Posso recuperare i file cifrati? |
|
| HydraCrypt crittografa i file con estensioni, come quelle riportate nella tabella sottostante, e li rinomina aggiungendo al nome originale l'estensione .crypt. |
| .3dm, .3ds, .7z, .accdb, .aes, .ai, .apk, .app, .arc, .asc, .asm, .asp, .aspx, .bat, .brd, .bz2, .c, .cer, .cfg, .cfm, .cgi, .cgm, .class, .cmd, .cpp, .crt, .cs, .csr, .css, .csv, .cue, .db, .dbf, .dch, .dcu, .dif, .dip, .djv, .djvu, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dtd, .dwg, .dxf, .eml, .eps, .fdb, .fla, .frm, .gadget, .gbk, .gbr, .ged, .gpg, .gpx, .gz, .h, .htm, .html, .hwp, .ibd, .ibooks, .indd, .jar, .java, .jks, .js, .jsp, .key, .kml, .kmz, .lay, .lay6, .ldf, .lua, .m, .max, .mdb, .mdf, .mfd, .mml, .ms11, .msi, .myd, .myi, .nef, .note, .obj, .odb, .odg, .odp, .ods, .odt, .otg, .otp, .ots, .ott, .p12, .pages, .paq, .pas, .pct, .pdb, .pdf, .pem, .php, .pif, .pl, .plugin, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prf, .priv, .private, .ps, .psd, .py, .qcow2, .rar, .raw, .rss, .rtf, .sch, .sdf, .sh, .sitx, .sldx, .slk, .sln, .sql, .sqlite3, .sqlitedb, .stc, .std, .sti, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tbk, .tex, .tgz, .tlb, .txt, .uop, .uot, .vb, .vbs, .vcf, .vcxproj, .vdi, .vmdk, .vmx, .wks, .wpd, .wps, .wsf, .xcodeproj, .xhtml, .xlc, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .zip, .zipx, , .3g2, .3gp, .aif, .asf, .asx, .avi, .bmp, .dds, .flv, .gif, .iff, .jpg, .m3u, .m4a, .m4v, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpg, .png, .pspimage, .ra, .rm, .srt, .tga, .thm, .tif, .tiff, .tmp, .vob, .wav, .wma, .wmv, .yuv |
NOT YOUR LANGUAGE? USE https://translate.google.com
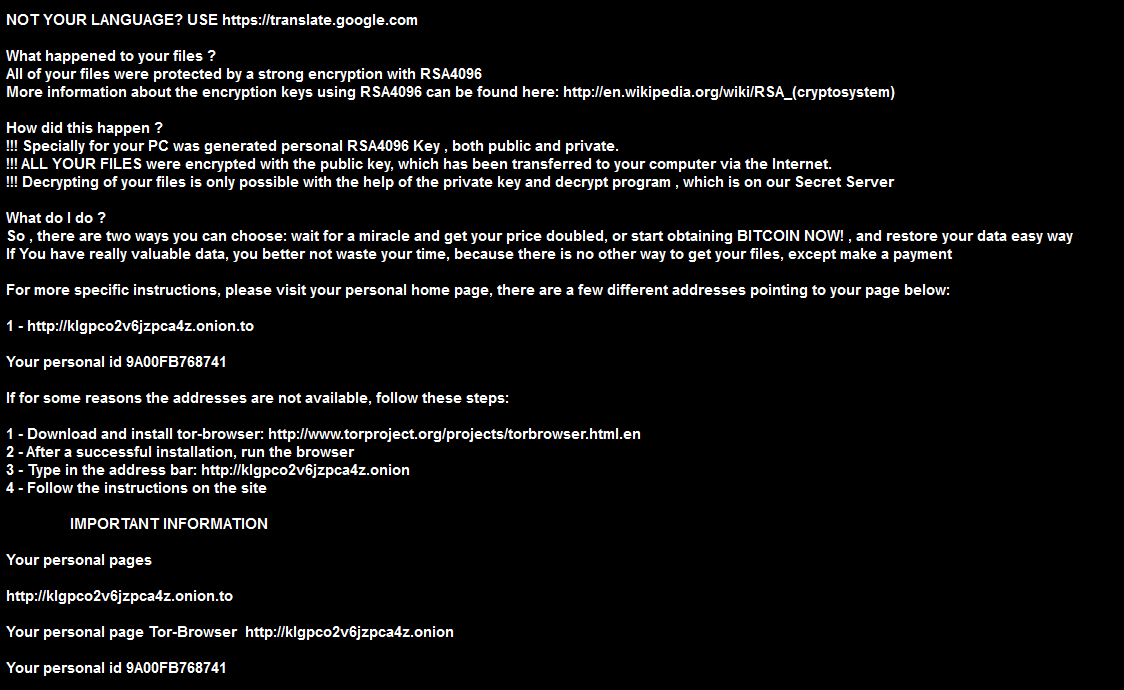
What happened to your files ? All of your files were protected by a strong encryption with RSA4096 More information about the encryption keys using RSA4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem) How did this happen ? !!! Specially for your PC was generated personal RSA4096 Key , both public and private. !!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet. !!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server What do I do ? So , there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BITCOIN NOW! , and restore your data easy way If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below: 1 - http://klgpcoXXXjzpca4z.onion.to Your personal id 9AXXFB768741 If for some reasons the addresses are not available, follow these steps: 1 - Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en 2 - After a successful installation, run the browser 3 - Type in the address bar: http://klgpcoXXXjzpca4z.onion 4 - Follow the instructions on the site IMPORTANT INFORMATION Your personal pages http://klgpcoXXXjzpca4z.onion.to Your personal page Tor-Browser http://klgpcoXXXjzpca4z.onion Your personal id 9AXXFB768741 |
 |
Dati per ragionevolmente certi i corretti:
Quando compare la videata di Alert qui a fianco significa che la protezione Anti-CryptoMalware integrata in Vir.IT eXplorer PRO sta agendo e quindi, evitando di farsi prendere dal "panico" NON chiudere la finestra ed eseguire le operazioni che vengono indicate:
|
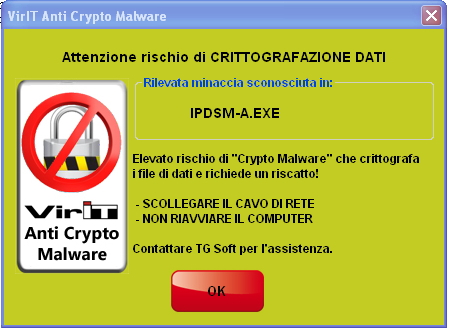 Clicca per ingrandire l'immagine 99,63%* Aspettativa percentuale media di file salvati dalla crittografazione grazie alla protezione Anti-CryptoMalware di Vir.IT eXplore PRO ==> Consulta l'informativa |