
06/12/2013
15:33
Bad news with CryptoLocker
New variant of Trojan.Win32.CryptoLocker.B that encrypt all documents and ask to pay a ransom in order to unlock their files.

 |
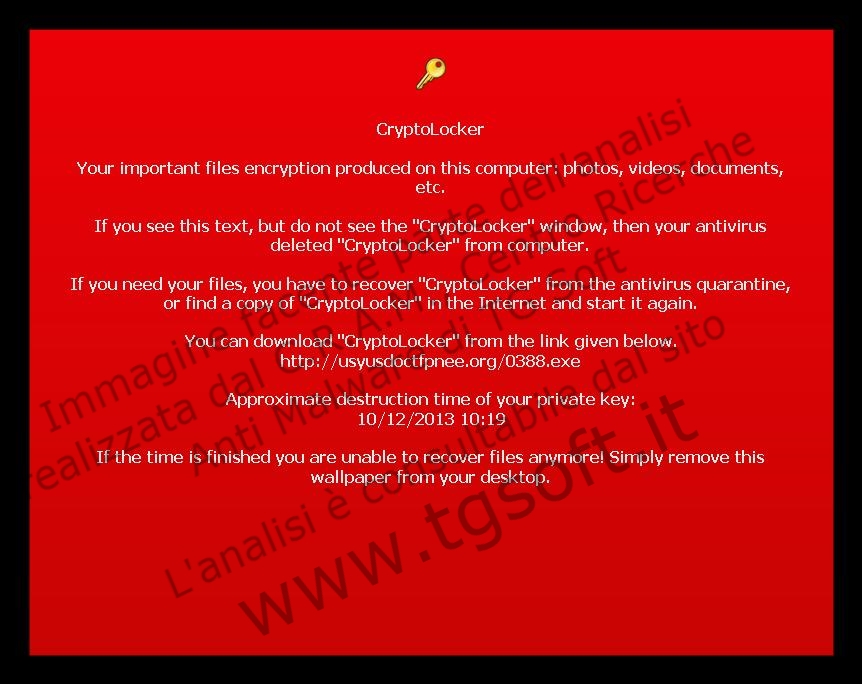
On December 3, 2013, there has been a new variant of ransomware CryptoLocker, classified as Trojan.Win32.CryptoLocker.B The CryptoLocker is a ransomware that encrypts documents all drives (local and remote) connected to your computer, demanding a ransom of 300 $ / EUR or in equivalent currency. The CRAM (Anti-Malware Research Center of TG Soft) team has analyzed this new variant of CryptoLocker. |
 |
 |
 |
| Url: | usyusdoctfpnee.org |
|
| IP address: | 188.65.211.137 | |
| Host: | host-188.65.211.137.knopp.ru | |
| Contry: | Russian Federation | |
| City: | - | |
| Organization / ISP: | Limited Liability Company KNOPP | |
| Latitude: | 60°00'00" North | |
| Longitude: | 100°00'00" East |
| lobrtucswpyeajq.net | non raggiungibile | - |
| nrtroiauihtcmys.org | non raggiungibile | - |
| opunyapqmiavvtg.co.uk | 212.71.250.4 | United Kingdom |
| pjrinsnwctgotet.info | non raggiungibile | - |
| qhsexkdsgumitmp.com | non raggiungibile | - |
| ybcgtpgmkqlxrrr.biz | non raggiungibile | - |
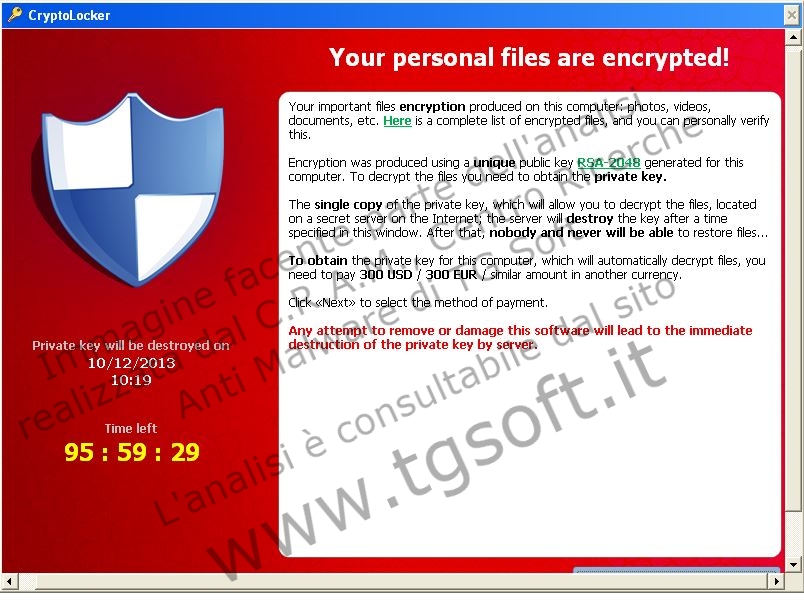
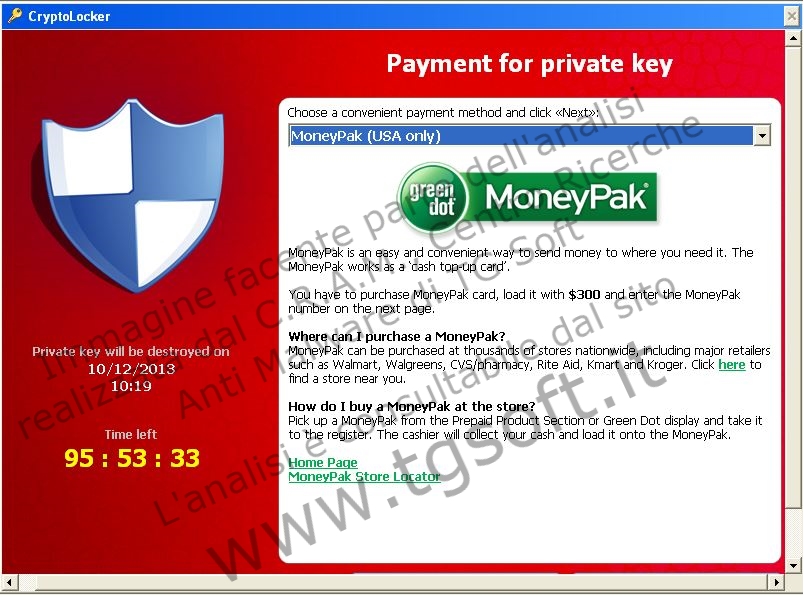
| Info payment: | Your important files encryption produced on this computer: photos, videos, documents, etc. Here is a complete list of encrypted files, and you can personally verify this. Encryption was produced using a unique public key RSA-2048 generated for this computer. To decrypt the files you need to obtain the private key. The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that, nobody and never will be able to restore files... To obtain the private key for this computer, which will automatically decrypt files, you need to pay 300 USD / 300 EUR / similar amount in another currency. Click «Next» to select the method of payment. Any attempt to remove or damage this software will lead to the immediate destruction of the private key by server. |
|
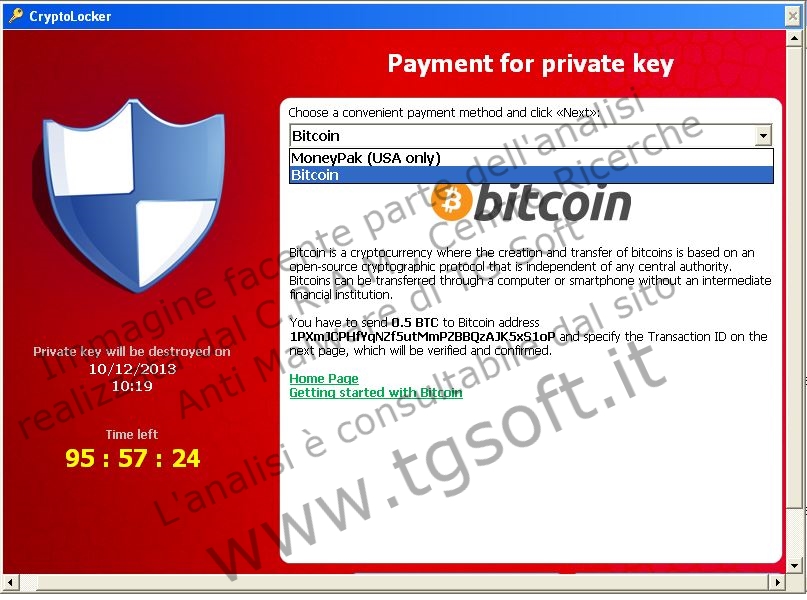
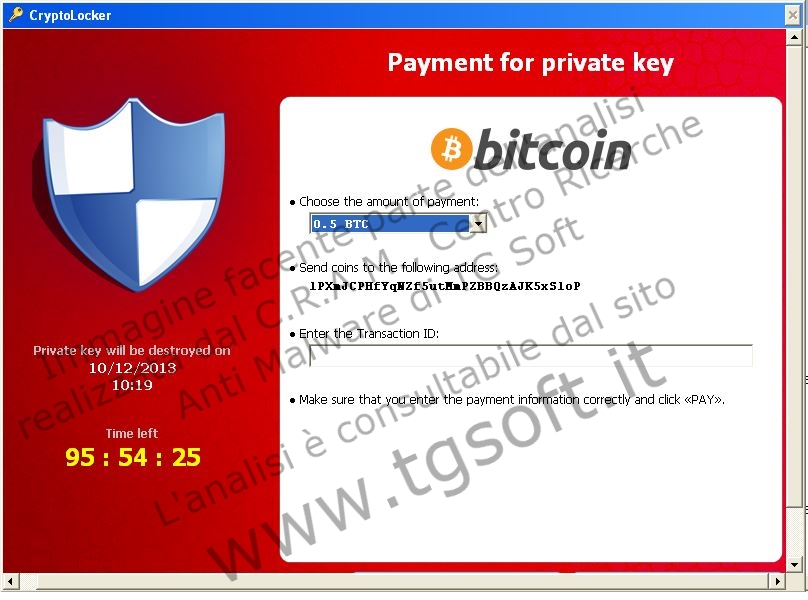
| Bitcoin: | Bitcoin is a cryptocurrency where the creation and transfer of bitcoins is based on an open-source cryptographic protocol that is independent of any central authority. Bitcoins can be transferred through a computer or smartphone without an intermediate financial institution. You have to send 0.5 BTC to Bitcoin address 1PXmJCPHfYqNZf5utMmPZBBQzAJK5xS1oP and specify the Transaction ID on the next page, which will be verified and confirmed. Home Page Getting started with Bitcoin |
|
| MoneyPak | MoneyPak is an easy and convenient way to send money to where you need it. The MoneyPak works as a ‘cash top-up card’. You have to purchase MoneyPak card, load it with $300 and enter the MoneyPak number on the next page. Where can I purchase a MoneyPak? MoneyPak can be purchased at thousands of stores nationwide, including major retailers such as Walmart, Walgreens, CVS/pharmacy, Rite Aid, Kmart and Kroger. Click here to find a store near you. How do I buy a MoneyPak at the store? Pick up a MoneyPak from the Prepaid Product Section or Green Dot display and take it to the register. The cashier will collect your cash and load it onto the MoneyPak. Home Page MoneyPak Store Locator |
|
| Inetnum : 188.65.211.0 - 188.65.211.255 Netname : RU-KNOPP Mnt-domains : MNT-KNOPP Descr : KNOPP datacenter network 2 Country : RU Admin-c : VLEF2009-RIPE Tech-c : DMGR2009-RIPE Status : ASSIGNED PA Mnt-by : MNT-KNOPP Mnt-lower : MNT-KNOPP Mnt-routes : MNT-KNOPP Person : Vladimir Efremov Address : 4/1, Kolpachny per., 101000 Moscow, RUSSIAN FEDERATION Phone : +74956410410 Nic-hdl : VLEF2009-RIPE Mnt-by : MNT-KNOPP Person : Dmitriy Grishin Address : 4/1, Kolpachny per., 101000 Moscow, RUSSIAN FEDERATION Phone : +74956410410 Nic-hdl : DMGR2009-RIPE Mnt-by : MNT-KNOPP Route : 188.65.208.0/21 Descr : RU-KNOPP route object Origin : AS6719 Mnt-by : MNT-KNOPP |