After the new discovery on December 11th, 2015 of Trojan.Win32.CryptoFF.C, a new variant of this family of crypto-malware was discovered.
This new variant is called Trojan.Win32.CryptoFF.D and is very similar to Trojan.Win32.CryptoFF.A.
The file analyzed "
17F.tmp" was found in the temporary folder of a computer hit by
Trojan.Win32.CryptoFF.D
We don't have any more information as this malware spreads.
File name: 17F.tmp
MD5: 5366277c20458c8b08eb9c0bb2dc5528
Size: 202515 byte
Time Stamp (header): 15/12/2015 - 08.17.03
When running the
Trojan.Win32.CryptoFF.D, it immediately starts to encrypt the files.
When it finds the first victim, it will do the following things:
1) open the document
2) encrypt the document
3) rename the original file with extension "
.him0m" (e.g. mydocument.doc -> mydocument.doc.him0m)
The first 64 KB of files will be encrypted by
Trojan.Win32.CryptoFF.D
If size of file is below 64 KB, then whole document will be encrypted.
The malware uses AES 256 bit to encrypt the files.
Inside the malware there is a bug when it encrypts file with size below 64 KB, in this case the decrypt of these files makes documents corrupted at end of files.
In each folder it will create 2 files:
- SECRETKEYISHIDINGHERE.KEY (size 1.368 byte)
- READTHISSHITNOWORELSE.TXT (size 1.248 byte)
The file "
SECRETKEYISHIDINGHERE.KEY" contains a key in UUencode, after it's decoded, it will obtain a key of 1024 byte.
The file "
READTHISSHITNOWORELSE.TXT" contains instructions to recover the file encrypted:
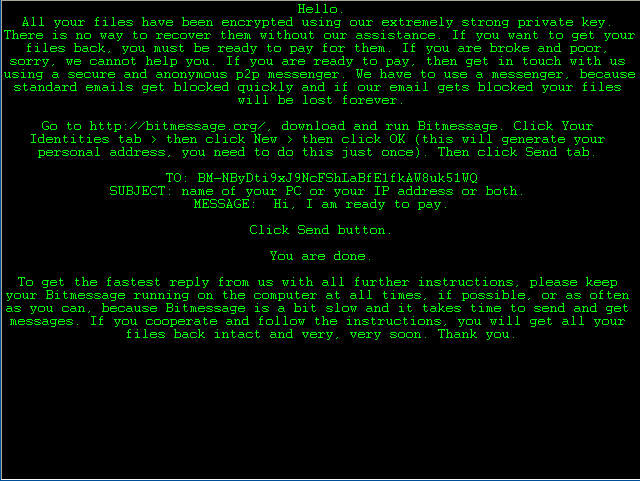
Hello.
All your files have been encrypted using our extremely strong private key. There is no way to recover them without our assistance. If you want to get your files back, you must be ready to pay for them. If you are broke and poor, sorry, we cannot help you. If you are ready to pay, then get in touch with us using a secure and anonymous p2p messenger. We have to use a messenger, because standard emails get blocked quickly and if our email gets blocked your files will be lost forever.
Go to http://bitmessage.org/, download and run Bitmessage. Click Your Identities tab > then click New > then click OK (this will generate your personal address, you need to do this just once). Then click Send tab.
TO: BM-NByDti9xJ9NcFShLaBfE1fkAW8uk51WQ
SUBJECT: name of your PC or your IP address or both.
MESSAGE: Hi, I am ready to pay.
Click Send button.
You are done.
To get the fastest reply from us with all further instructions, please keep your Bitmessage running on the computer at all times, if possible, or as often as you can, because Bitmessage is a bit slow and it takes time to send and get messages. If you cooperate and follow the instructions, you will get all your files back intact and very, very soon. Thank you. |
When Trojan.Win32.CryptoFF.D will terminate to encrypt all document, it will show this image:
The
Trojan.Win32.CryptoFF.D removes the volume shadow copies with this command:
cmd.exe /Q /C vssadmin.exe delete shadows /all /quiet
Clean:
VirIT version 8.0.69 and later.
Analysis by eng. Gianfranco Tonello
C.R.A.M. (Anti-Malware Research Center) by TG Soft


