The
C.R.A.M. of
TG Soft is analyzing a new type of CryptoMalware called
Petya ransomware whose first reports of diffusion/attack have been detected, for now, in Germany, but the cryptomalware, as is easily understood, have no boundaries.
FILENAME: Bewerbungsmappe-gepackt.exe
MD5: af2379cc4d607a45ac44d62135fb7015
SIZE: 230912 byte |
 |
How PETYA manifests
Currently we do not know the origin of the file sample sent to our laboratories, while the mode of infection, analyzing Petya attacks in Germany, it would seem to take place with the now well-known mass dispatch of e-mail with an attachment that invites the person receiving opening / activate the file that causes the MBR infection (Master Boot Record) and encryption MFT (Master File Table) of the disk.
The mail reported in Germany, is of course written in German, and invites you to download from a Dropbox folder two documents:
- a .jpg photo files named Bewerbungsfoto.jpg
- an executable file Bewerbungsmappe-gepackt.exe
Anti Malware Research Center of TG Soft has verified that by running the Bewerbungsmappe-gepackt.exe file is displayed the blue screen BSOD (Blue Screen of Death) reported here by side.
At this point the malware has infected the MBR (Master Boot Record) of the hard disk and has not yet begun to encrypt the MFT (Master File Table).
It was verified that, at this point, if you disconnect the hard drive and connect it to another computer as a secondary, data are still visible/accessible. |
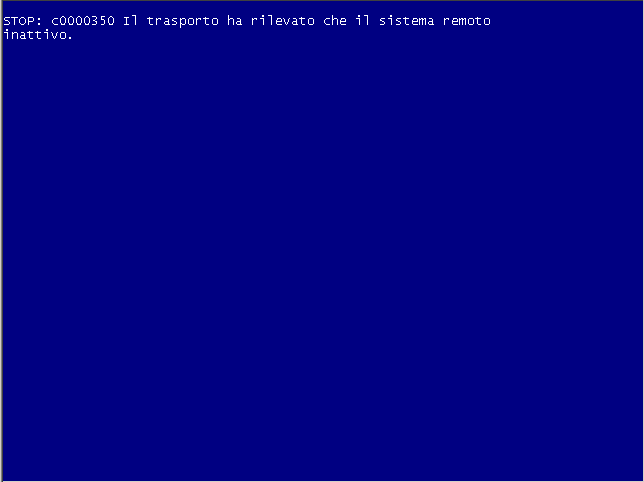 |
Under ordinary conditions, the unsuspecting user, seeing the previous screen, similar to the classic blue BSOD (Blue Screen of Death screen), proceed to restart his PC / SERVER uploading MBR infected with Petya that will display a "chkdsk" which would seem to make the operation of "repair" the file system but instead will encrypt the MFT.
|
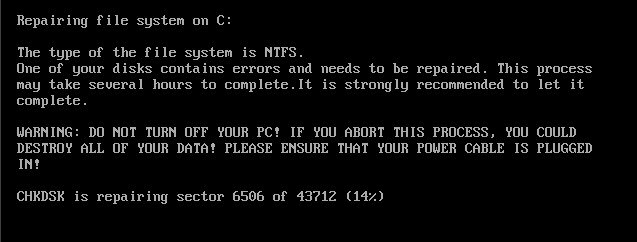 |
| Completed the "chkdsk", PC restarts automatically and you will see the symbol of death and in order to continue you will have to press a key (PRESS ANY KEY!) As you can see in the image by side. |
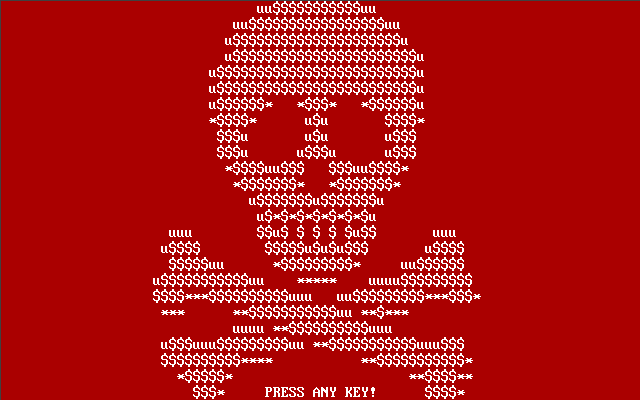 |
|
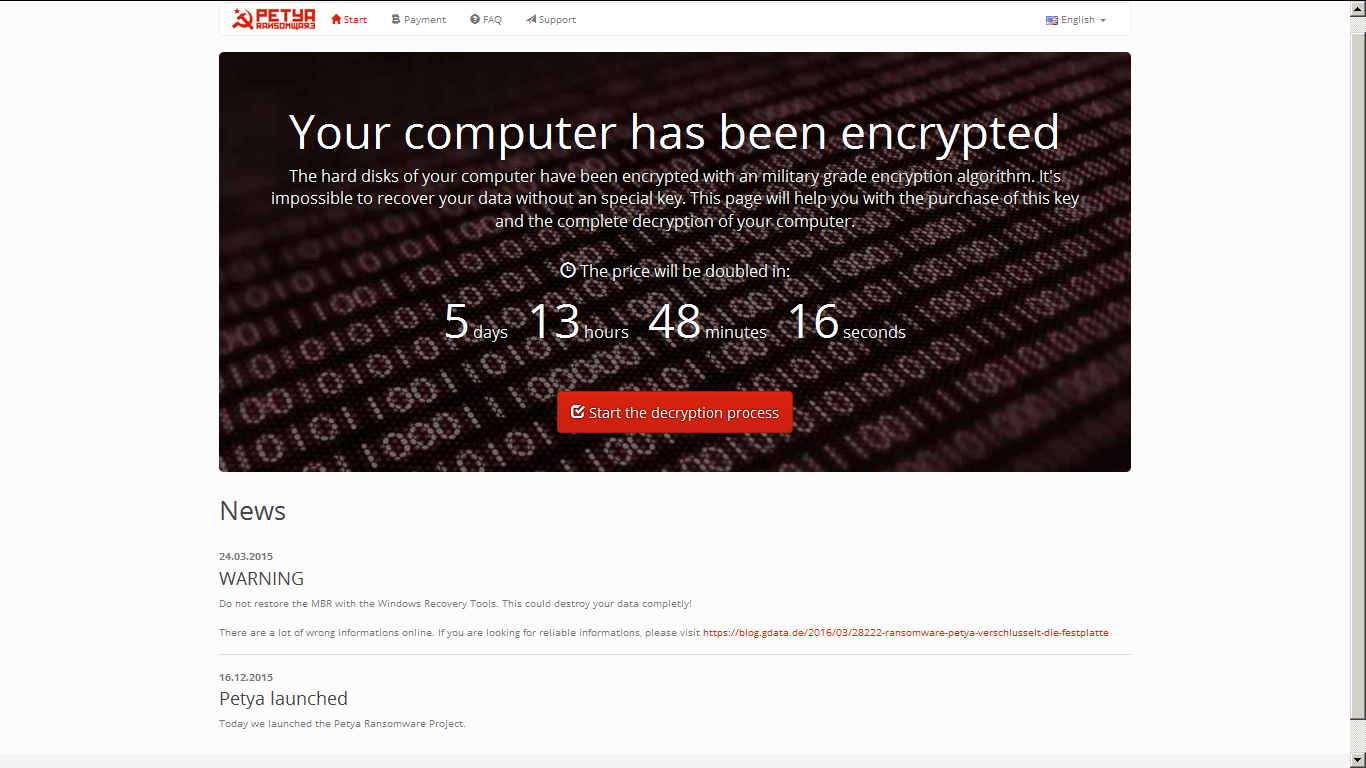
The next screen warns that you have been the victim of PETYA RANSOMWARE and to pay the ransom as you can see in the right hand screen:
- at point 2 there are reported the sites accessible through TOR Browser to make contact with the blackmailers;
- at point 3 is shown the code to insert into the TOR network for the payment of the ransom.
|
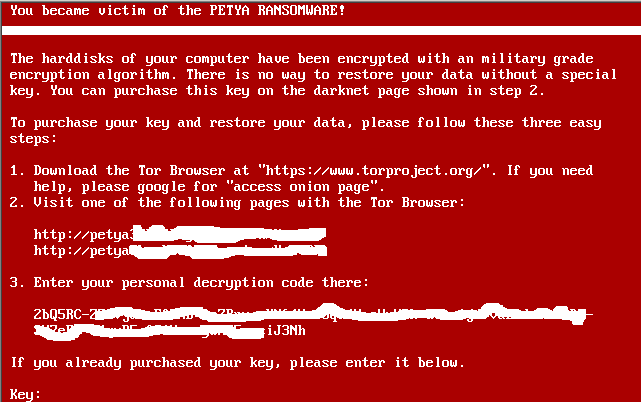
|
A payment made, the unfortunate victim will have to insert the key to decrypt the MFT and remove MBR infection.
With MBR (Master Boot Record) infected and MFT (Master File Table) coded the machine becomes completely inaccessible and will remain so even if you were groped to overwrite a new MBR or connect the disk as secondary to another PC to try to carry out removal.
The ransom demanded by PETYA
As you can see from the image to the right, connecting to the TOR-Onion page indicated, after entering a Captca you will display the count-down for the payment of the ransom. If the ransom was not paid within 6 days and 11 hours, approximately, the amount requested in the first instance of about 0.99 BitCoin will be doubled.
The authors of this new type of Cryptomalware attack call themselves "Janus Cybercrime SolutionsTM"
By clicking on the red button in the figure "Start the decryption process" will be displayed on the control page under reported: |
Click to enlarge |
Click to enlarge |
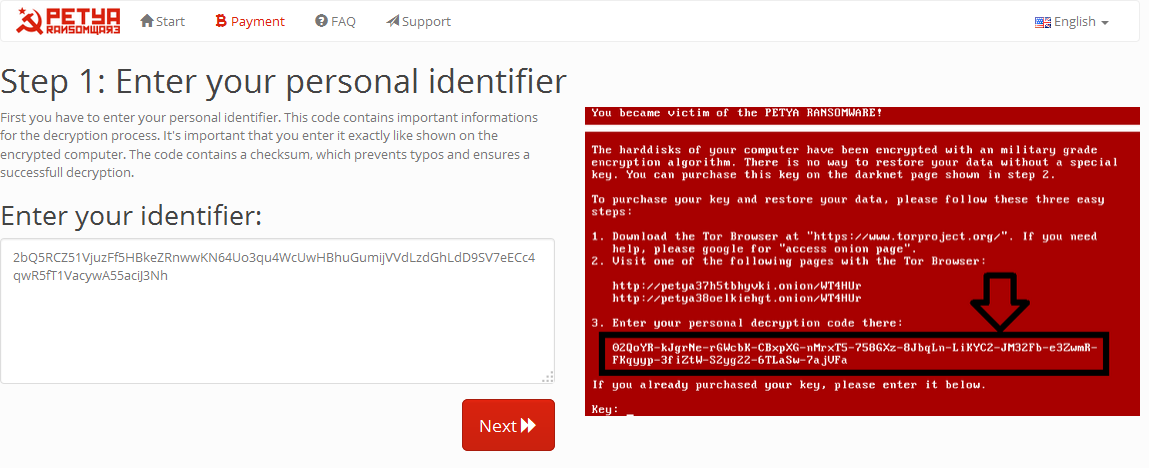
On the left in the field "Enter to identifier:" blackmailers invite you to enter the Id identifier of the victim.
Pressing the "Next>>" button you will access the image below. |
Reached the Bitcoins purchase page, the surrender value requested in Bitcoin is shown, which can be varied according to the time when you connect to the page. This is related to the daily price of Bitcoin.
Pressing the "Next>>" button you will access the image below.
|

Click to enlarge |
Click to enlarge |
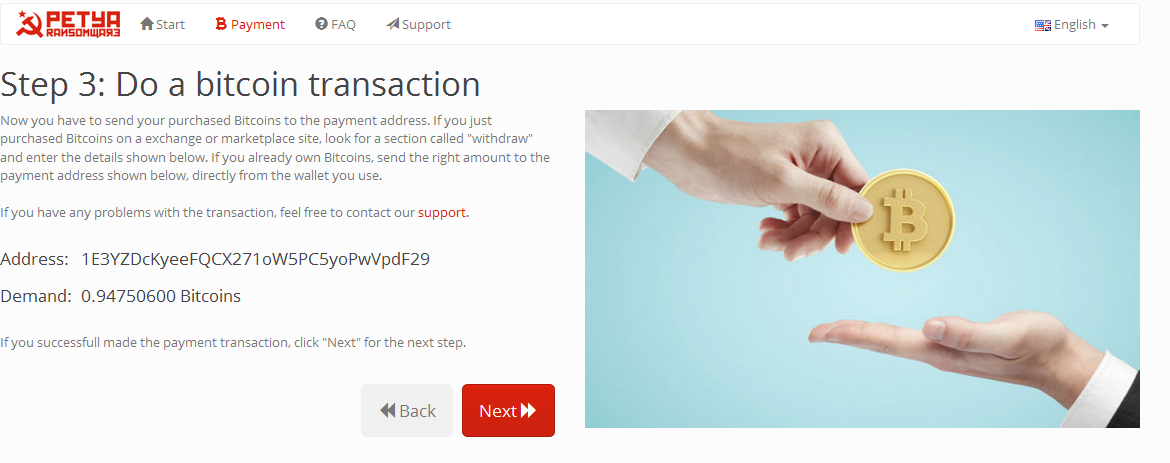
On the screen you can see the coordinates of the Bitcoin account and the amount to be paid. In the specific screen 0.9475 Bitcoin. |
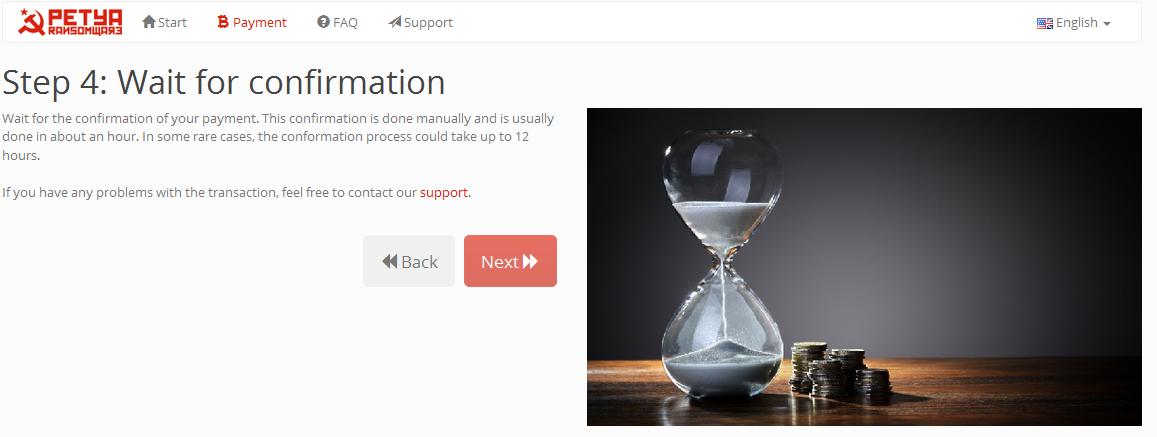
After pressing the "Next>>" button you reach the screen Step 4: where, in summary, the payment made is waiting for confirmation and in rare cases the confirmation takes place within 12 hours.
|
Click to enlarge |
In the screen below the site of the "Janus Cybercrime Solutions" it is also available a FAQ page, that is, answers to frequently asked questions.
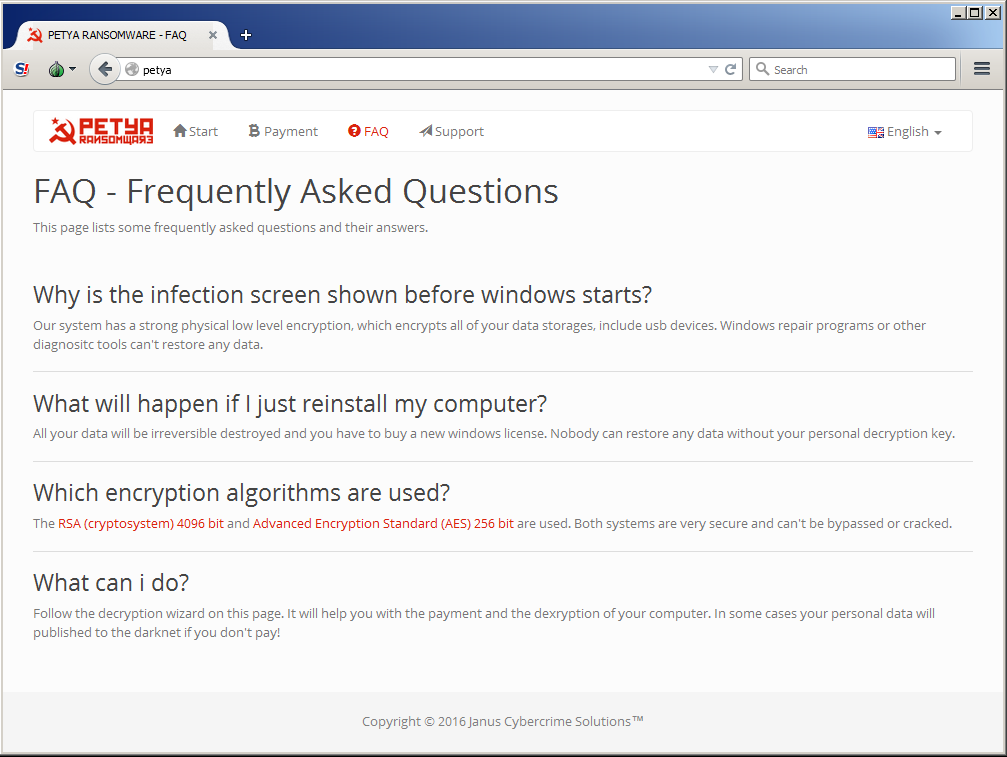 |
In addition there is also a system of sending messages to communicate with the "Janus Solutions Cybercrime"
 |
How to protect yourself from PETYA
As a general rule, we should never forget that behind every link or any attachments of each email could hide malware or Crypto-Malware.
Good practice would avoid clicking on links or on e-mail attachments that arrive as strangers or by people who seem known but with unexpected attachments.
For now, to counter these new generation of Crypto Malware attacks, the only defense is to make BackUp copies of their data on non-connected drives to the computer, where the everyday files which you want to preserve with the copies are placed in safety.
Back to top
Can I recover the disk access ?
If the malware has encrypted MFT (Master File Table), for now, you can not make disk access without paying the ransom. But the virus / malware is still being analyzed by researchers of C.R.A.M. TG Soft.
The FixMBR operation can only be performed if the MFT is not yet encrypted.
If you execute FIXMBR with the encrypted MFT, Windows will not load properly and it will alert the disk corruption and invite to use a utility like %quot;chkdsk". The use of this utility could further damage the MFT and make it even more difficult to recover disk data, even after the payment.
Back to top
Final thoughts
Of course we invite everyone to be careful when opening/run email attachments, even if they arrive from a known sender or browsing disreputable sites.
Please check in advance the sender's email address before you open/run the attachment.
TG Soft
External Relations
Back to top



