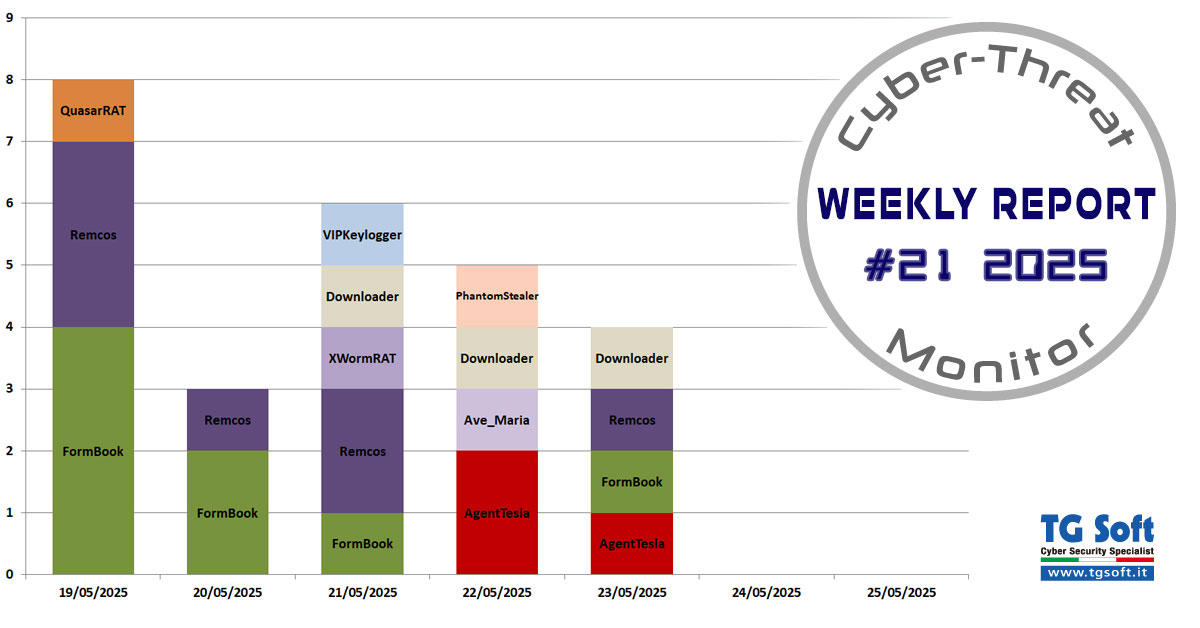
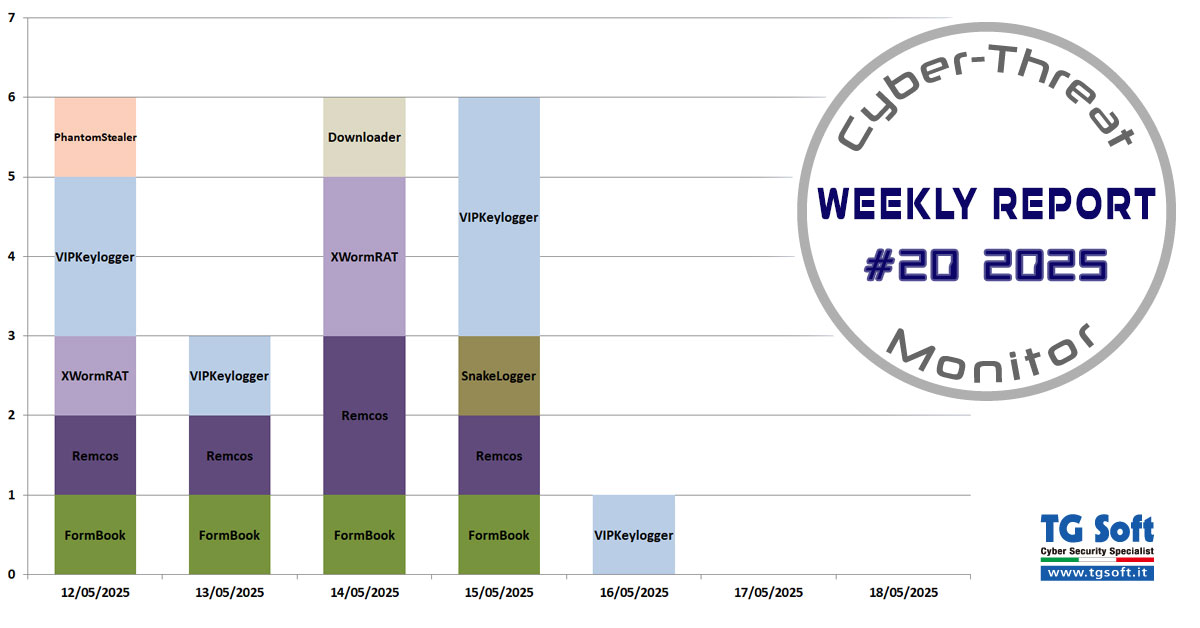
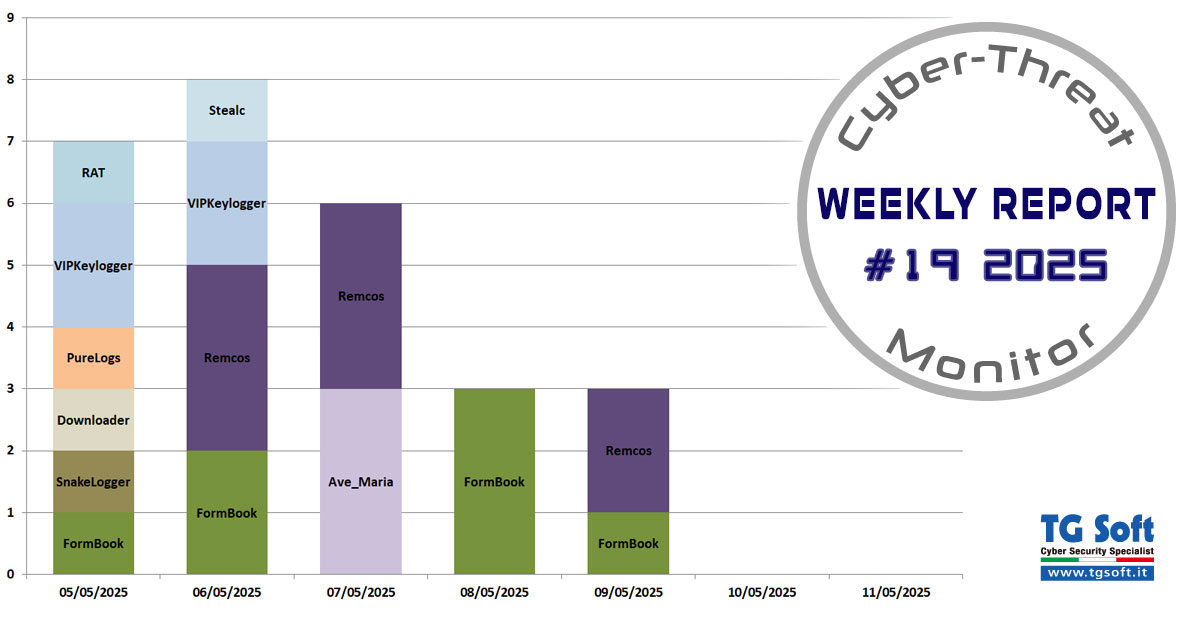
Cookie necessary to make certain specific contents usable such as: access to protected areas of the site, sending requests or subscribing to newsletters. The specific features of these sections will not be usable without this cookie.
_GRECAPTCHA [x1]
Necessary to verify human interaction.
Used to send quotes, access restricted areas and all those points where security is a fundamental component.
Expiration: 6 month/s
Type: HTTP
cookie_google [x1]
Flag for acceptance of Google reCAPTCHA cookies
Expiration: 6 month/s
Type: HTTP
Accept the reCAPTCHA Terms of Service:
By accessing or using the reCAPTCHA APIs, you agree to the Google APIs Terms of Use, Goodle Terms of Use, and to the Additional Terms below. Please read and understand all applicable terms and police before accessing the APIs.
reCAPTCHA Terms of Service:
You acknowledge and understand that the reCAPTCHA API works by collecting hardware and software information, such as device and application data and the results of integrity checks, and sending that data to Google for analysis. Pursuant to Section 3(d) of the Google APIs Terms of Service, you agree that if you use the APIs that it is your responsibility to provide any necessary notices or consents for the collection and sharing of this data with Google.
Data collected by reCAPTCHA:
- The reCAPTCHA algorithm will check for the presence of a Google cookie (usually _ga)
- If not present, a specific reCAPTCHA cookie will be added to the browser of the user and will be captured - pixel by pixel - a complete snapshot image of the user's browser window at that time.
Some of the browser and user information currently collected includes:- All cookies placed by Google in the last 6 months
- How many mouse clicks did you make on that screen (or touch if on a touch device)
- The CSS information for that page
- The exact date
- The language in which the browser is set
- Any plug-in installed in the browser
- All Javascript objects