Starting from Monday 3-25-2013, the
C.R.A.M. has detected several attacks at various Windows-based Servers.
A new kind of malware, the
Trojan.Win32.ACCDFISA.A and the
Trojan.Win32.ACCDFISA.B is infecting Windows-based Servers crypying documents or other file formats in the pc.
Files crypted will be renamed in this way:
<Filename>
will be crypted and renamed as:
<Filename>(!! to get password email id ????????? to italyhelp1@gmail.com !!).exe
Where the ID ????????? is a unique number which change from pc to pc.
e.g.: invoice.doc becomes
fattura.doc(!! to get password email id 1288927338 to italyhelp1@gmail.com !!).exe
The PC gets penetrated by a cracker that exploits a Windows vulnerability.
The cracker infects the PC by placing the following files in some autorun keys:
[HKLM\Software\Microsoft\Windows\CurrentVersion\Run]
[svchost] = %programdata%\<random folder>\svchost.exe -->
Trojan.Win32.ACCDFISA.A
[HKLM\System\CurrentControlSet\Services\WinSamSs]
[image path] = %system%\lsassw86s.exe -->
Trojan.Win32.ACCDFISA.B
The
Trojan.Win32.ACCDFISA.A uses the following modules:
- svchost.exe (182.784 byte): it's used mainly to show the ransom full-screen popup that blocks the PC.
- scsvserv.exe (17.920 byte): edit the Windows' registry, disabling errors report and deleting all voices from Run in HKCU and HKLM.
Inside "C:\programdata" there are several folders with numeric names(e.g.: 03230240582). You can find these files into each of them:
- <random number>.dll
- <random number>.bat
- <random number>fspall1.dll
- <random number>.dll.dlls
- BKR<random number>.dll
- S1_<random number>.dlls
- DB1_<random number>.dlls
E.g.: 032302405814.dll
<random number>.dll contains a very long random number:
3423434534512333466576743532423423545657567657465345345234234
Also <random number>fspall1.dll contains a random generated number:
768969456453464765875345436568679678673453457568679678678567767
The file <random number>.dll.dlls is the RAR crypted version of <random number>.dll.
The file
<random number>.bat execute the following command:
netsh.exe Interface ip Set address "Network connections" Static 172.245.0.1 255.255.0.0 172.245.0.1 1
The file BKR<random number>.dll contains a list of .log files.
The file S1_<random number>.dll contains a list of .jp. txt, pdf and other file extensions files.
The file DB1_<random number>.dll contains a list of .DB files.
The
Trojan.Win32.ACCDFISA.B is composed by following file:
- lsassw86s.exe (80.896 - 84.480 byte): its the executable in charge of crypting files, it's executed as a service.
The
Trojan.Win32.ACCDFISA.B deletes the registry key "SafeBoot", so that it becomes impossible to restart the PC in safe mode.
The malware downloads the following files:
svchost.exe (404.992 byte) - > RAR Command line tool
cfwin32.dll (404.992 byte) - > RAR Command line tool
sdelete.dll (155.936 byte) -> Sysinternals' dll, digitally signed from Microsoft, that deletes permanently files from disk without any possibility to recover them.
nsf.exe (48.640 byte) -> Executable infected by
Trojan.Win32.NoSafeMode.A
NoSafeMode.dll (12.800 byte) -> Executable infected by
Trojan.Win32.NoSafeMode.B
The malware uses the "Command Line RAR" tool to crypt documents.
The Windows' exploit permits at the cracker to log onto the machine with terminal server using an external ip; this allow the cracker to bruteforce the accounts' passwords on the server.
We strongly recommend these three simple operations to protect yourselves from these kinds of attacks:
1) Install all Windows Updates and reboot the server to apply them, since the vulnerability exploited by the cracker has been fixed with the
KB2621440 released almost an year ago, (13th of March 2012), and not installed because of poor maintenace of the server.
2) The System Admin should modify Windows' settings to prevent external IP from loggin into the terminal server;
3) You should always set very complex passwords (with numbers, lowecase and uppercase letters, special characters etc. and of a minimum length of 12 characters) on every account of the server, so the individuation of them by the cracker is very difficult if nearly impossible.
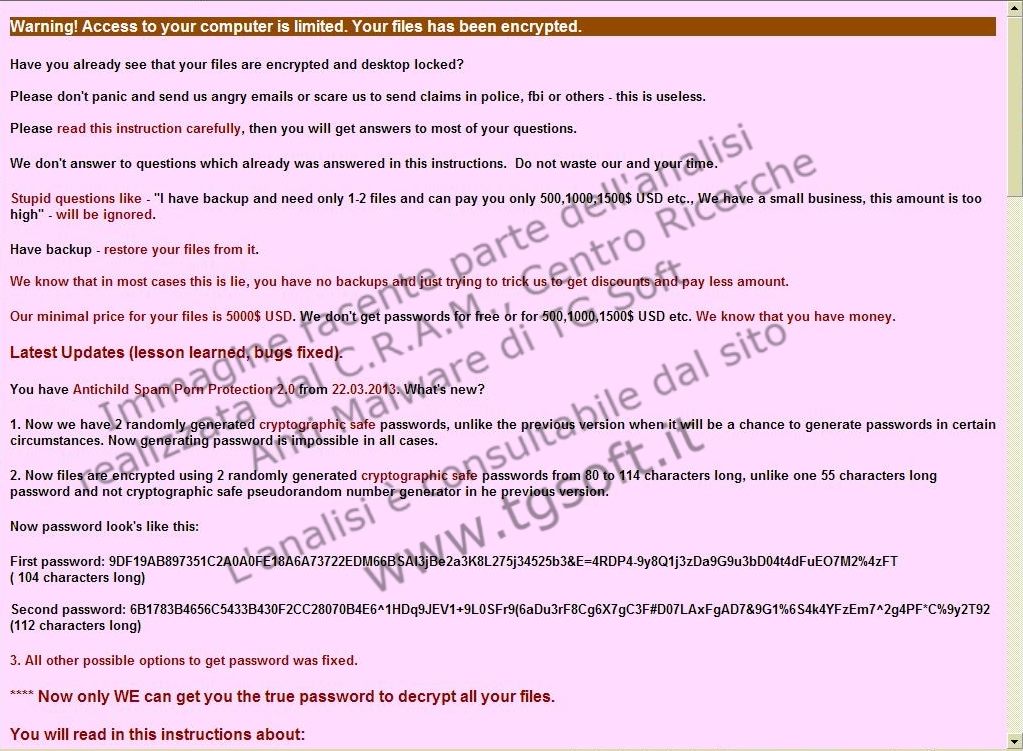 |
This malware, crypts all text files (.txt, .doc, .dat, ecc...) in self-extract archives protected by a complex password sent to the cracker and impossible to recover.
On top of that, it creates a service which crypts all files that weren't crypted the first time, with a new generated password different from the first. |
At the moment there is no possible way to decrypt the files that are crypter with RAR encryption based on the AES algorithm.
Analysis by eng. Gianfranco Tonello
C.R.A.M. (Anti-Malware Research Center) by TG Soft

