C.R.A.M.'s attention (Anti-Malware Research Center of Soft TG) was focused on customer's smartphone that clearly appeared affected by one or more viruses / malware. We found abnormal behavior during the device use, specifically a Yashi MySmart OS 5.0 (YP5009).
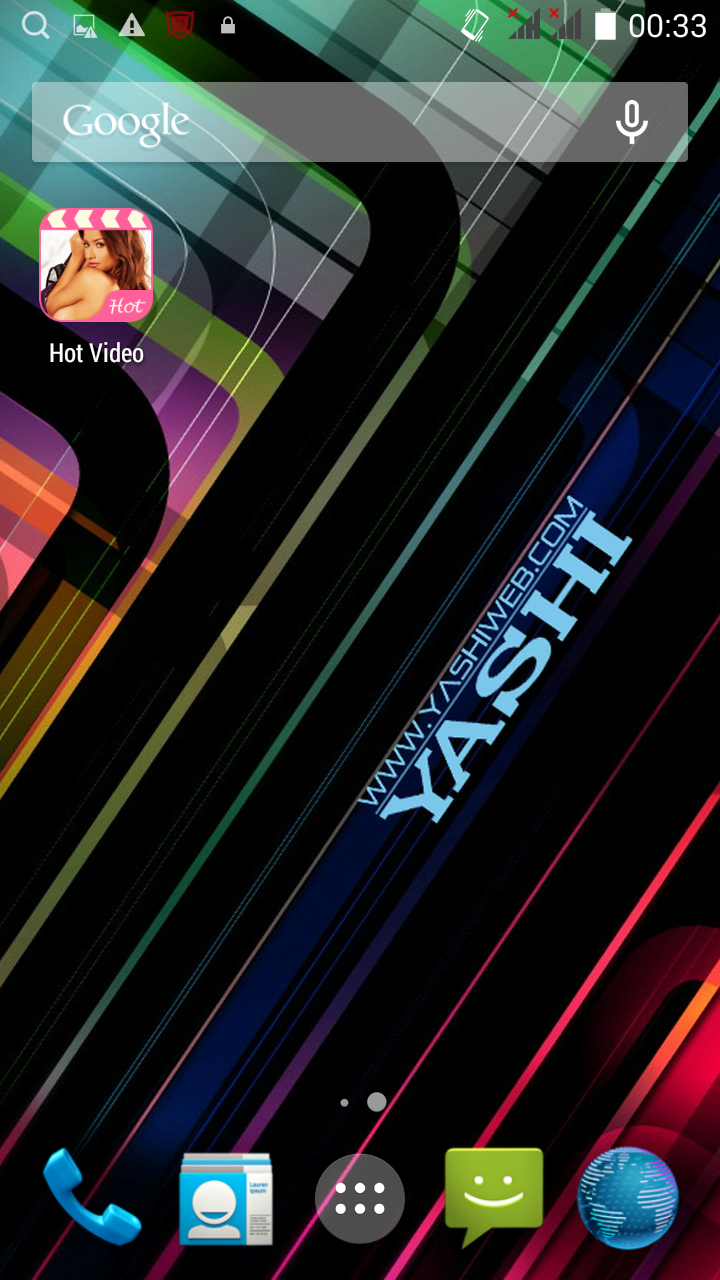
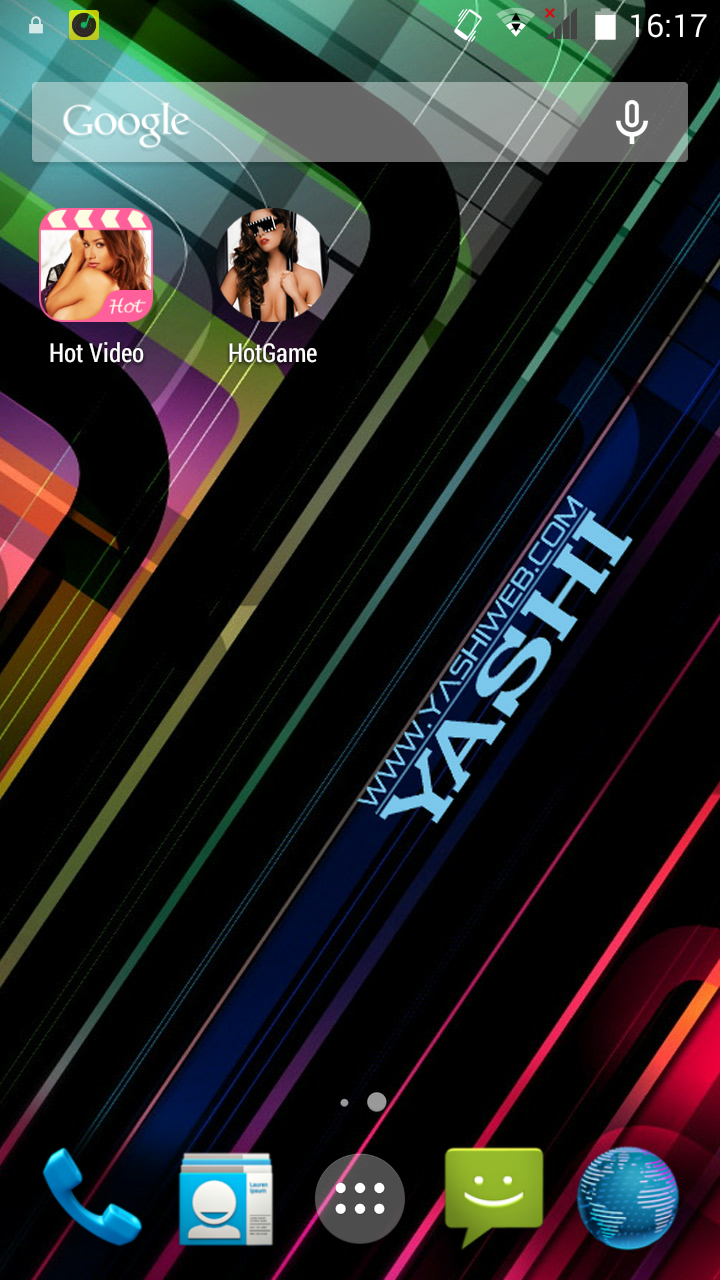
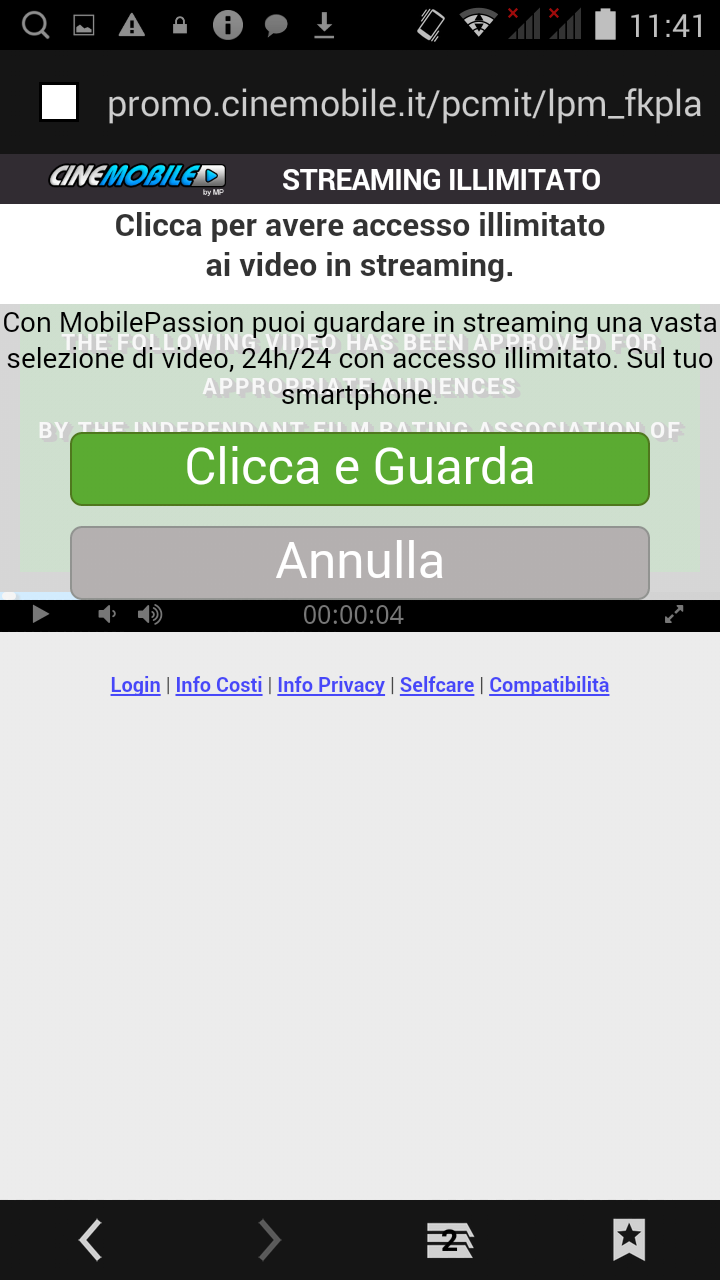
The malware presence is highlighted by the appearance of unwanted shortcuts (ie icons that refer to applications installed on the device) and loading of banner ads independently by the user's will. |
 |

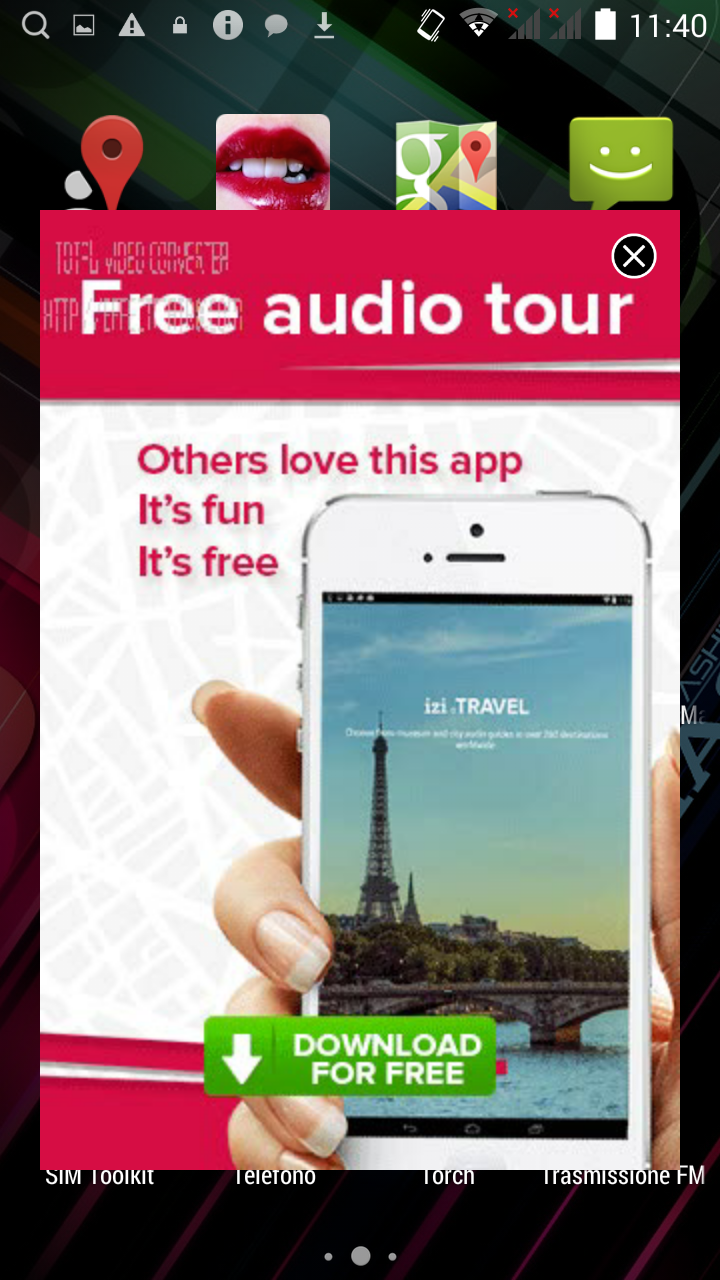
[ - The images depict banner ads that open automatically and the app icons that are being automatically installed.- ]
The device has also shown a "physical" stress, derived by malware, that requires a massive use of the memory and processor, causing frequently restarts and stepping into safe mode, resulting unusable by the user.
In general, the device running slower than normal because of a succession of unwanted screens that have been activated during connection to the network, be it 3G, 4G or Wi-Fi.
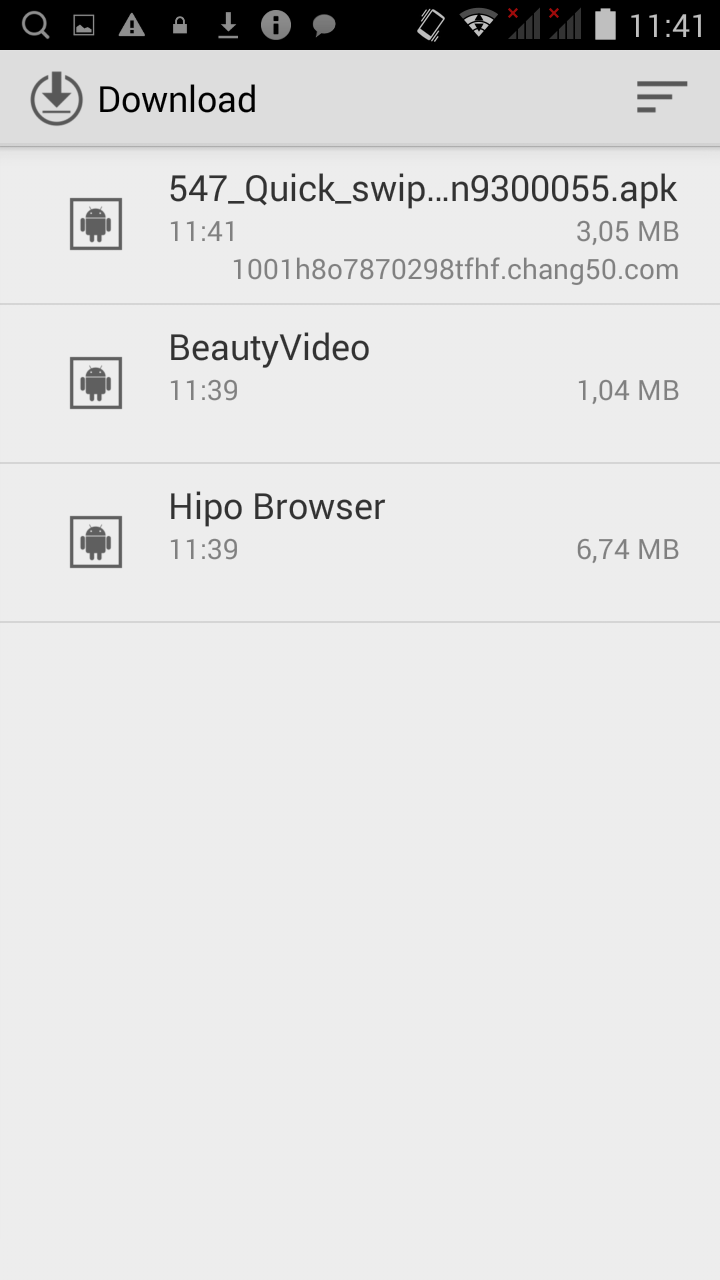
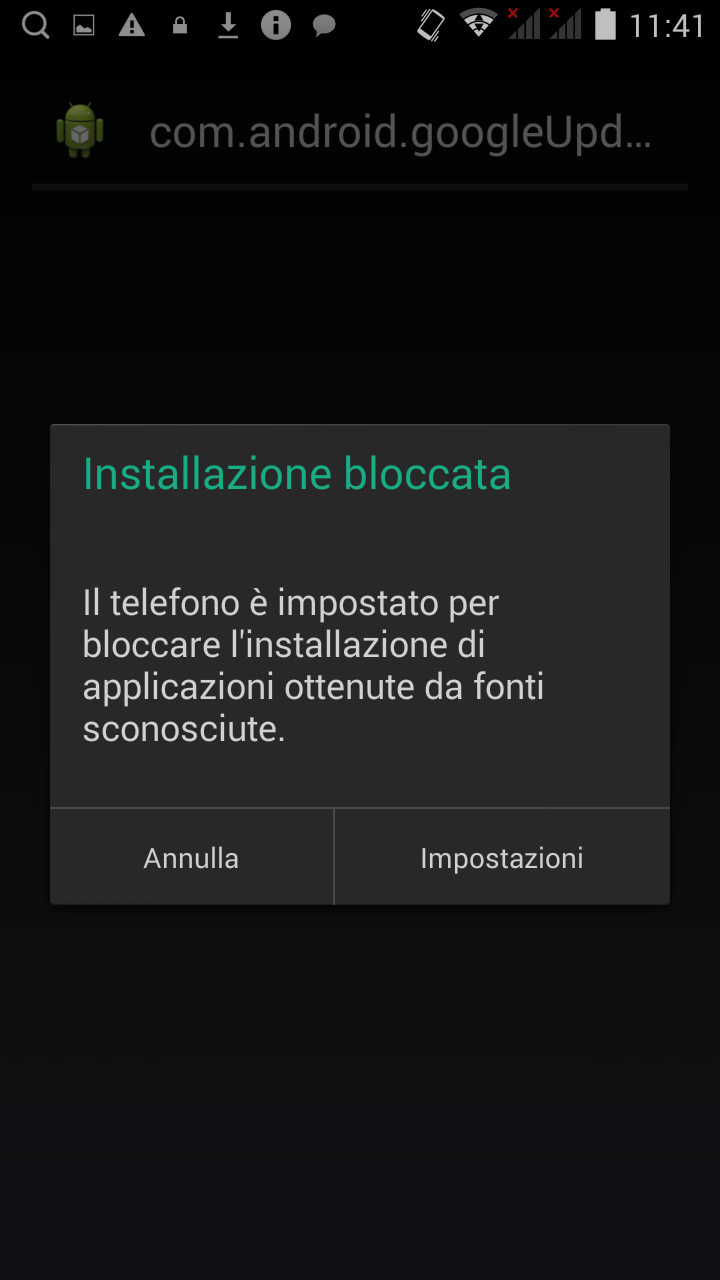
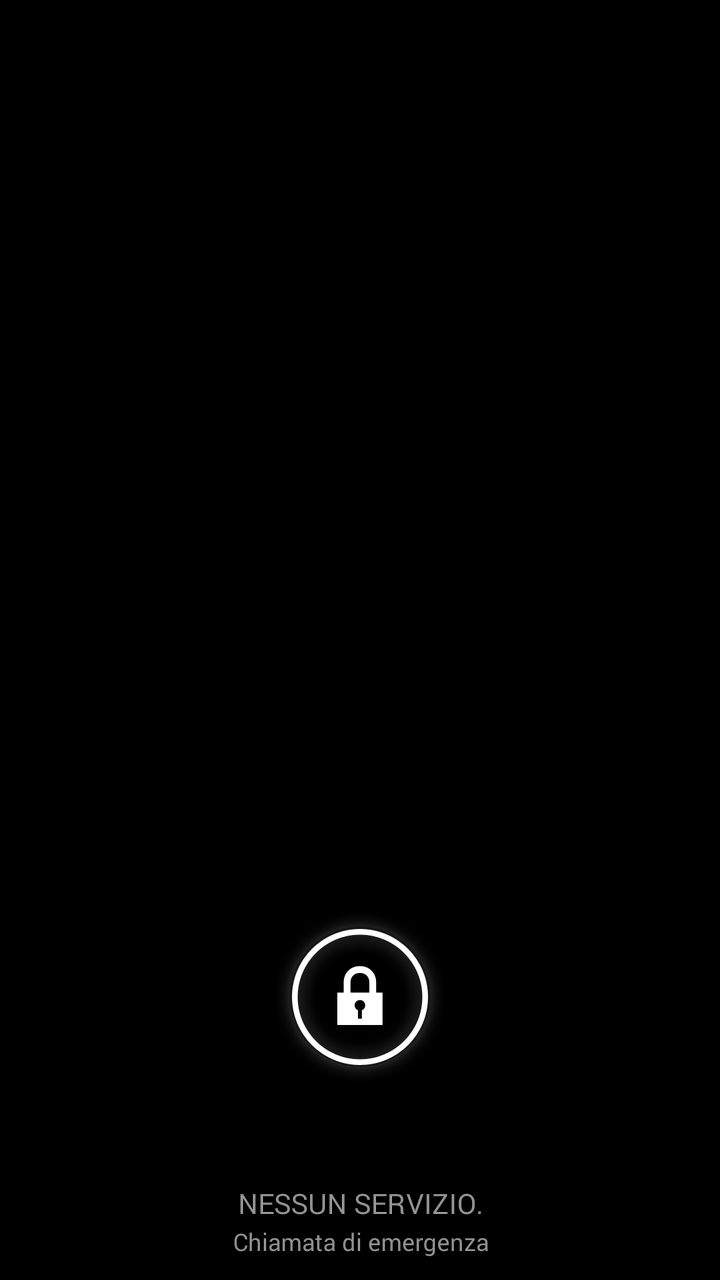
[ - The first three images showing the app during their automatic download, while the last one shows the screen when your smartphone goes into protection mode - ]
So the C.R.A.M. (Centro Ricerca Anti-Malware) has conducted tests and analyzed in detail the behavior of this malware to understand origin and type.
During the analysis, intended to restore the normal functioning of the device, we have tried to remove every unwanted apps that have been installed independently. Also has proven inefficient the reset operation, initiated by the safe (recovery) mode available in every Android device bootable pressing a specific key combination (usually home + volume up / volume down). |
 |
Using this booting mode the phone restores the original factory configuration, resetting all user data. With
Yashi this did not happen, indeed, seemed to clean up but a few seconds after reboot malware reactivates and resumes its malicious actions.
This made us think of a very specific malware type called
Bootkit.
Often the majority of malware ends up on Android devices through third-party apps installation (unknown origin) that are not examined by the
Google Play Store filter. The bootkit already resides in the ROM of the device and runs at startup of the operating system. These malwares were identified in 2014 as highlighted in the article
"Oldboot the first bootkit on Android" and by
Alexander Burris
G Data Software in his speech at the
25th Virus Bulletin Conference held in Prague from 30th september to 2nd october 2015.

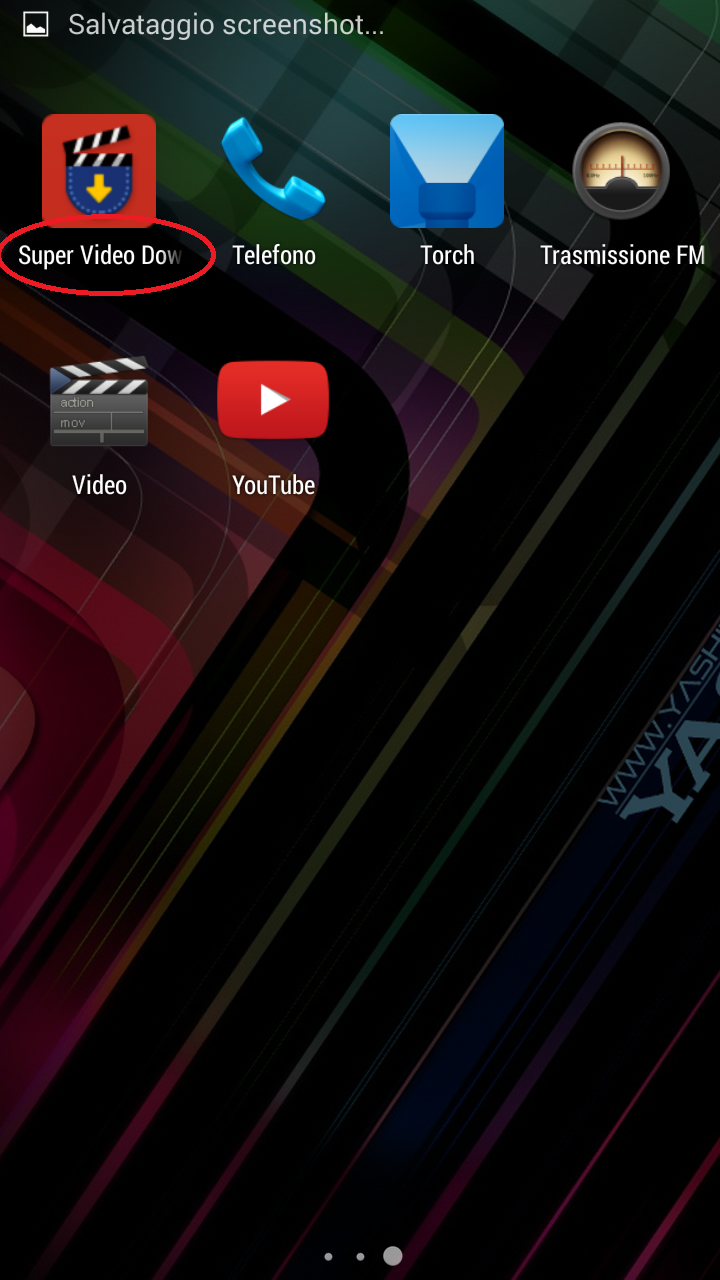
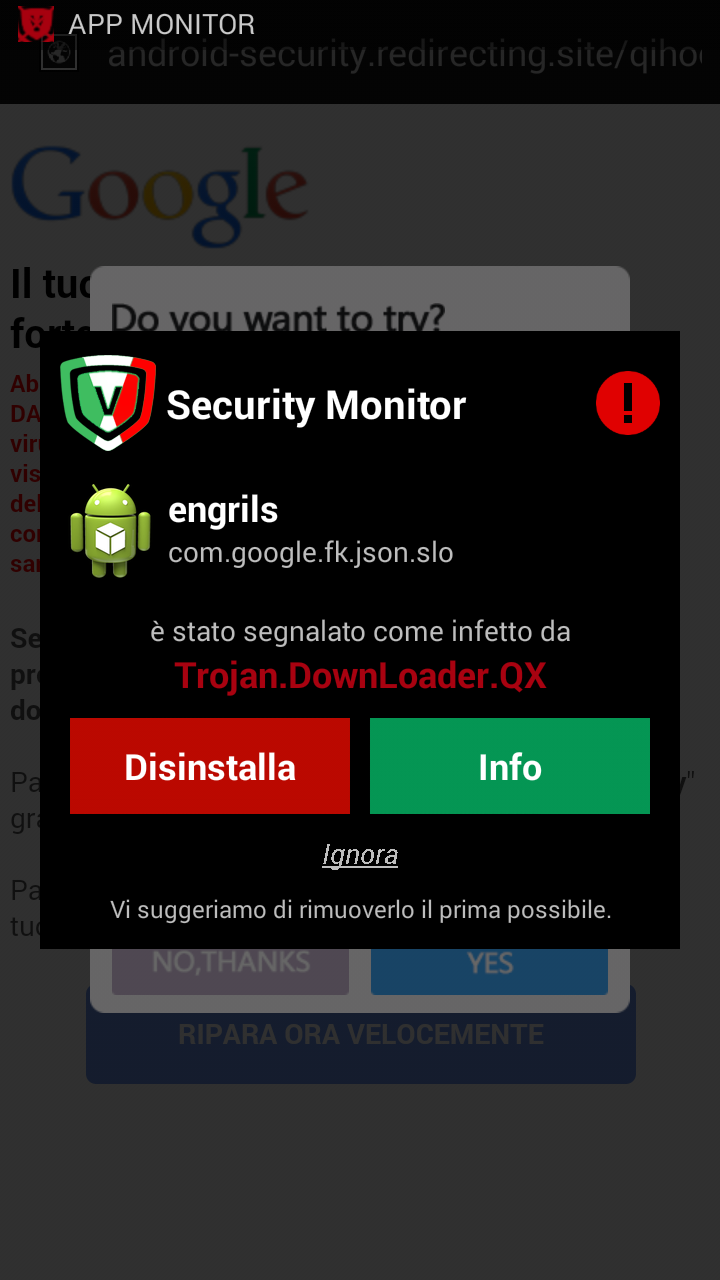
[ - Above the images of icons appeared after installation generated by malware - ]
Bootkits infect the boot system file and modifies the "init" script that charge operating system components. When device starts, this script loads the
update.jar file (containing the trojan
Android.Trj.DownLoader.KA) that extracts
is.jar and
GoogleSafe.apk files, copying them, respectively, in
/ system / lib and
/ system / app.
Some parts of the bootkit are being installed as a system service, by connecting to a remote server, from which they receive various commands, including download, installation and removal of user applications. They do this in loop at every network access.
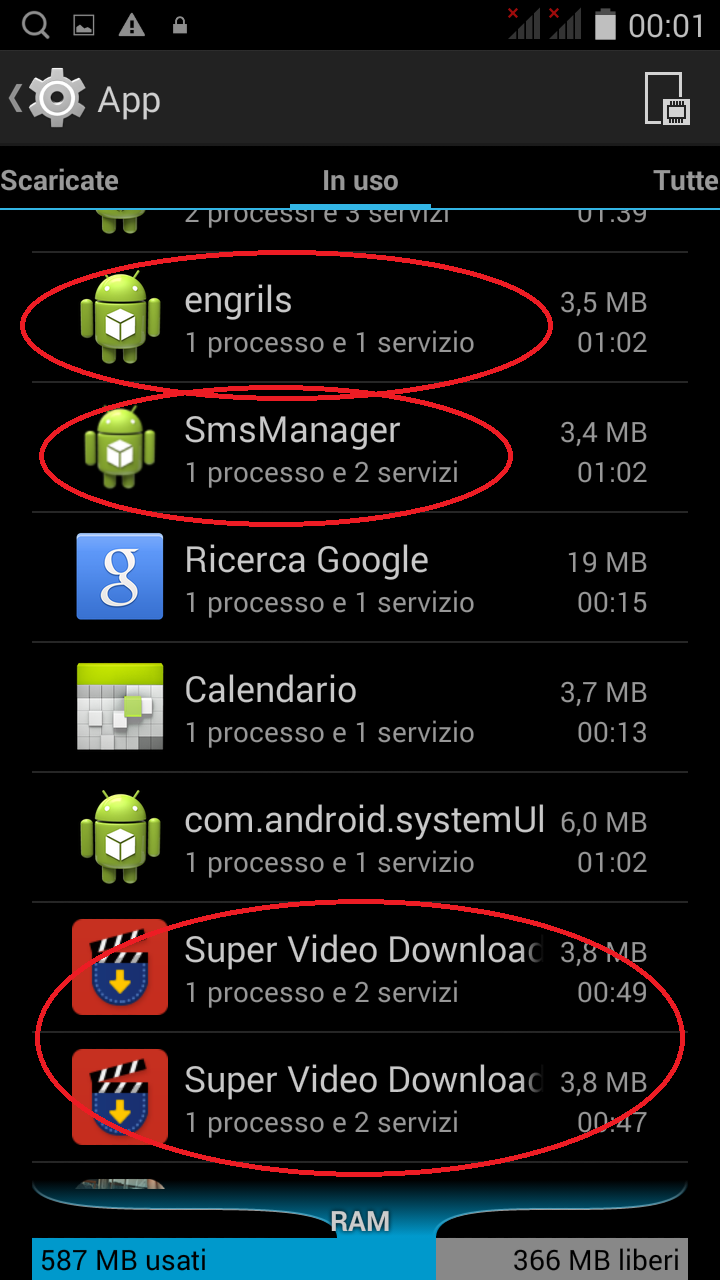
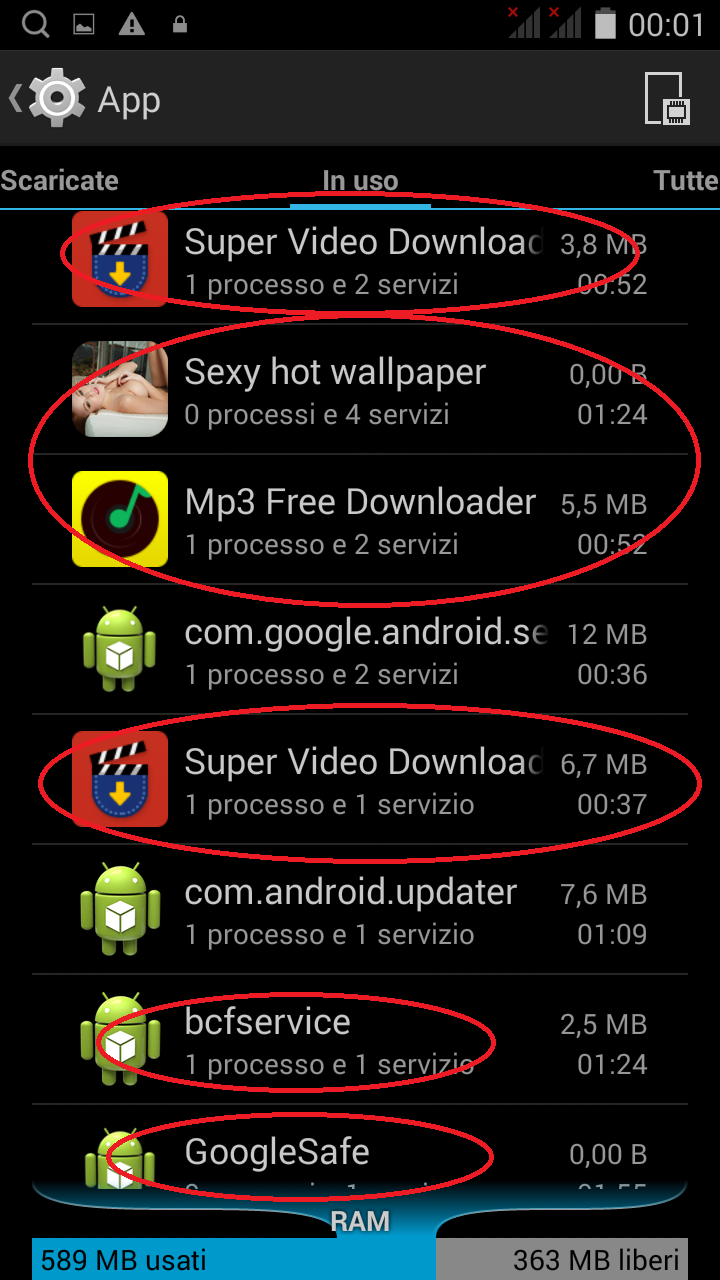
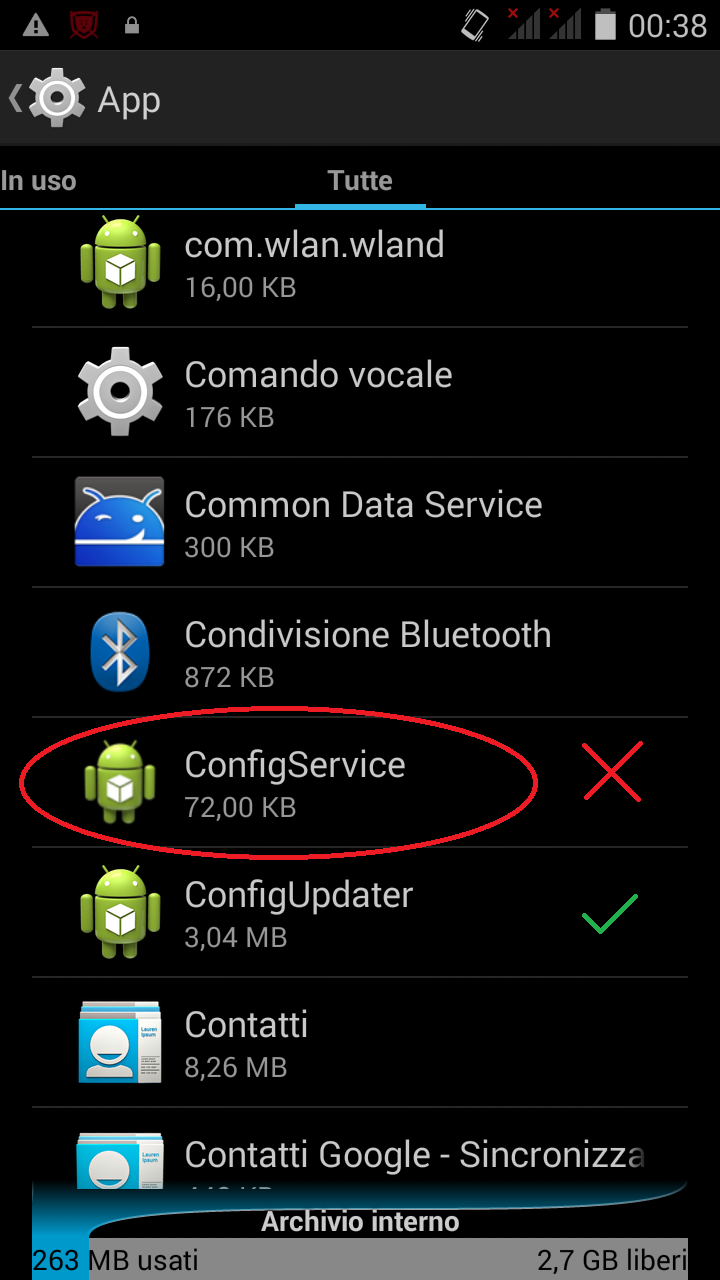
[ - These three images taken within the system settings, show malicious apps installed and their related services running. - ]
The malware has three key features. First it is installed in the ROM,
protected memory, difficult to access without superuser privileges and therefore difficult to detect.
Second feature appears to be the fact that this malware runs as a system service each time you start the smartphone, executing
trojans and
downloaders. Those components (applications or system services) are loaded and run, without your consent, applications and advertising of various kind.
Third aspect, even more disturbing is that
malware has access to all user data, is able to send and receive messages, phone calls, write on the system memory, perform any type of superuser command.
In conclusion, all these features make the
bootkit a serious threat to the user and to the integrity of his privacy.
Second part of the analysis on the infected smartphone was conducted using the mobile suite of the antivirus
VirIT eXplorer, named
VirIT Mobile Security. We have identified, through a memory scan, all bootkit's components, as shown in the image below that reports the results.
After that, connecting to a protected network, we checked some malicious apps in the exact moment when they tried to access the external network in order to download more malware.
One of the most used domains to download this malware appears to be
"upaiyun.com". We also noticed the presence of a text file named "FP.txt" containing part of the URLs to which the Bootkit connects.
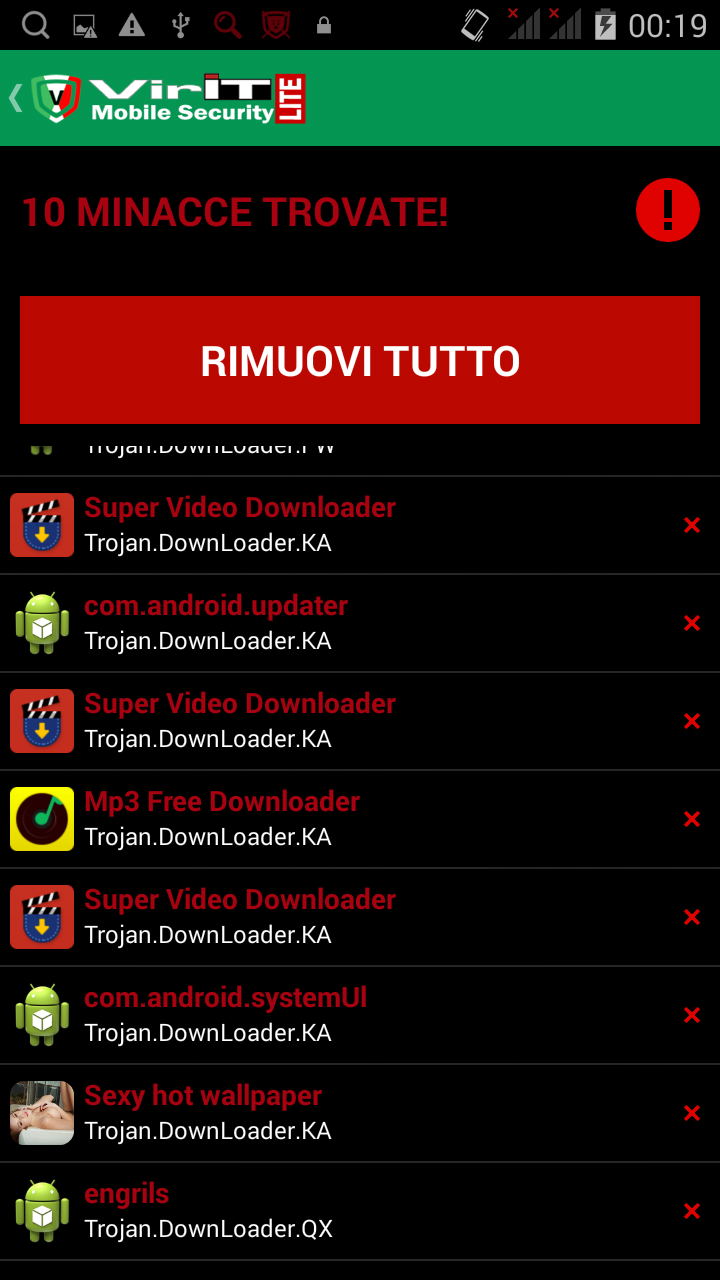
[ - The images above are part of the screenshots captured during the analysis with our antivirus VirIT Mobile Security - ]
In conclusion, is not possible to remove this malware directly, by uninstalling or deleting the infected apps because is pre-installed on the device and has been activated later.
It is likely therefore that the malware is present in some modified devices (custom ROMs) and redistributed in the market.
Unanswered were also our attempts to contact Yashi company to notify the problem in order to have a confrontation about a possible resolution. So for now customer's smartphone remains unusable.
Below, in the table, the report of the analysis conducted on all apps infected detected in the device.
| APK Name |
VIRUS Name and MD5 |
| 33f564d41261de0b99a77ee26cd888d1.apk |
Android.Trj.DownLoader.KA |
| FC8029D8F7F14543484EC5AAF36DCC2E |
| 111228_1_ddl.apk |
Android.Trj.DownLoader.NE |
| 6C95F4DCA1564E434FD22C175B492FE0 |
| 6391638e56fc94bb74f99ee769ada74b.apk |
Android.Trj.DownLoader.KA |
| BE7F80F099BFA005ED9935B1CCC872E9 |
| com.andr0id.lauchinmg.apk |
Android.Trj.DownLoader.KA |
| FC8029D8F7F14543484EC5AAF36DCC2E |
| com.as.youtube.downloader.a5.apk |
Android.Trj.DownLoader.KA |
| 3EC9F295093DCBABC2CDB5F8E570A657 |
| com.as.ytb.a5.apk |
Android.Trj.DownLoader.KA |
| 8EA2642883EA2C03C3080EA6E9B81C7A |
| com.config.n.service.apk |
Android.Trj.DownLoader.FW |
| AC3B3382D1C8447CB7B90237C8985859 |
| com.example.homeof01111beauty.apk |
Android.Trj.DownLoader.KA |
| 4885072427DF72A6C7C7B0C44B501998 |
| com.free.all.mptree.music.b.apk |
Android.Trj.DownLoader.KA |
| 090A449533BB157B8875D5A51F9EC291 |
| com.sms.sys.manager.apk |
Android.Trj.DownLoader.KA |
| 555921F5D2E8C3793CD019BE5BCA59A3 |
| com.sv.downloader.s1.apk |
Android.Trj.DownLoader.KA |
| 3EA37C94F291842A2B282E45BFBC21F1 |
| com.system.cap.hm.gupdater.apk |
Android.Trj.DownLoader.KA |
| CB7BD086C9E77917B3C8CD7DC63DB24C |
| com.system.cap.hm.gupdater.apk |
Android.Trj.DownLoader.KA |
| CB7BD086C9E77917B3C8CD7DC63DB24C |
| dd85bd64496b23ba07e5c890e742782b.apk |
Android.Trj.Triada.A |
| 55CC4C2FDD7F709B599216976D31BDFC |
| GoogleSafe2016020301.apk |
Android.Trj.Backdoor.LY |
| 6F34AFEDDFAAF3E6329D1B296691CB48 |
| 111228_1_ddl.apk |
Android.Trj.DownLoader.NE |
| 803FCAFAD57FFA0E760065F8146DF3D7 |
| update.jar |
Android.Trj.DownLoader.KA |
| 0EE881F2CA0048FD414A5E30FAA1599F |
| 1327.apk |
Android.Trj.Rootkit.R |
| B76B0893281896AA7D1BEF56CF421DB6 |
| 111234.apk |
Android.Trj.Rootkit.R |
| CF112AC831EAEED3A0228CFBE9FB3BD3 |
| SystemUpdate.apk |
Android.Trj.Triada.A |
| 149F2EB149D56E24682F91D53EA68447 |
| CCleaner.ok.apk |
Android.Adw.Deng.TVX |
| 3E3A5CF4958910B9A49429A79A4DEAC8 |
















