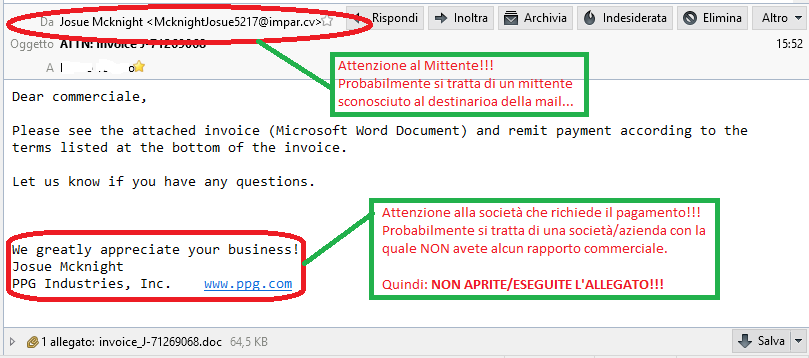
Today Tuesday 16th February the C.R.A.M. TG Soft has encountered a massive sending of e-mail requesting payment with attached a false invoice having the structure as shown below:
- Note that the e-mail appears to come from a user, probably unknown to the receiver, as you can see in the RED ellipse highlighted.
- The company requesting the payment, or alleged creditor, probably is not known to the recipient, as shown in the red box highlighted with rounded edges.
|
Click to enlarge image |
The body of the message, written in an orderly manner, is in English language. If you haven't made foreign purchases and you not have dealings with the indicated companies, it is important
NOT OPEN / RUN the mail attachment!!!
The analyzed emails seems to be different from each other, although maintaining the same structure. For the mentioned reasons, should not lead us into temptation opening the attachment even if it would seem to be a Word file, it is quite different:
- invoice_<random string>.doc
It is a seemingly innocuous .doc files but that downloads and runs the CryptoMalware called
CryptoLocky alias LockyCripter.
Avoid absolutely to Open / Run the mail attachment which triggers the encryption of data files in
.Locky of the PC / SERVER as well as in shared folders with this.
When the document
"invoice_<random string>.doc" is being opened, a macro will be executed that downloads and runs an executable file with a random name that contains the
CryptoLocky.
The executable file with random name, it copies itself in the %temp% of the user, named
SVCHOST.EXE..
At this point CryptoLocky performs the cancellation of the "shadow copy" with the command:
vssadmin.exe Delete Shadows / All / Quiet
When this is done, it performs a series of parallel threads for the encryption of documents (in our test had runs 13 threads).
CryptoLocky malware encrypts each file with the following extensions:
| .m4u .m3u .mid .wma .flv .3g2 .mkv .3gp .mp4 .mov .avi .asf .mpeg .vob .mpg .wmv .fla .swf .wav .mp3 .qcow2 .vdi .vmdk .vmx .gpg .aes .ARC .PAQ .tar .bz2 .tbk .bak .tar .tgz .gz .7z .rar .zip .djv .djvu .svg .bmp .png .gif .raw .cgm .jpeg .jpg .tif .tiff .NEF .psd .cmd .bat .sh .class .jar .java .rb .asp .cs .brd .sch .dch .dip .pl .vbs .vb .js .h .asm .pas .cpp .c .php .ldf .mdf .ibd .MYI .MYD .frm .odb .dbf .db .mdb .sql .SQLITEDB .SQLITE3 .asc .lay6 .lay .ms11 (Security copy) .ms11 .sldm .sldx .ppsm .ppsx .ppam .docb .mml .sxm .otg .odg .uop .potx .potm .pptx .pptm .std .sxd .pot .pps .sti .sxi .otp .odp .wb2 .123 .wks .wk1 .xltx .xltm .xlsx .xlsm .xlsb .slk .xlw .xlt .xlm .xlc .dif .stc .sxc .ots .ods .hwp .602 .dotm .dotx .docm .docx .DOT .3dm .max .3ds .xml .txt .CSV .uot .RTF .pdf .XLS .PPT .stw .sxw .ott .odt .DOC .pem .p12 .csr .crt .key wallet.dat |
The
CryptoLocy will encrypt all documents renaming them with random name and .Locky extension.
The file with .Locky extension will be named
.locky
Esempio:
- 1DD6FF20B0293D341C12403B3C699ADF.locky
- 1DD6FF20B0293D348FE972E2C3923FEC.locky
After that, the original document files will be fully overwritten with the character "
U"and deleted.
The malware modifies the following registry keys to get into automatic run:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
[
Locky] =
%temp%\svchost.exe
After files encryption,
CryptoLocky creates
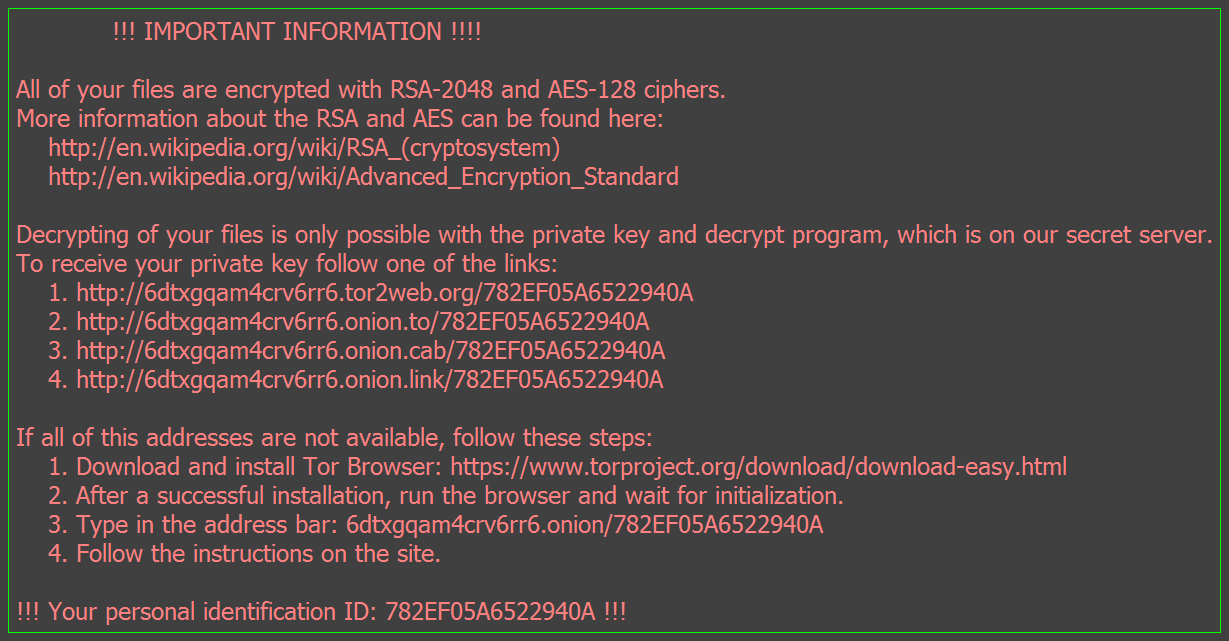
_Locky_recover_instructions.txt files containing the instructions for the ransom, which is shown below:
!!! INFORMAZIONI IMPORTANTI!!!!
Tutti i tuoi file sono stati criptati con algoritmo asimettrico RSA-2048 e algoritmo simmetrico AES-128.
Ulteriori informazioni sugli algoritmi sono disponibili su:
http://it.wikipedia.org/wiki/RSA
http://it.wikipedia.org/wiki/Advanced_Encryption_Standard
La decriptazione dei tuoi file è possibile solo con la chiave privata e il programma di
decriptazione che si trova sul nostro server segreto.
Per ricevere la tua chiave privata vai a uno dei seguenti link:
1. http://6dtxgqam4crv6rr6.tor2web.org/1DD6FF20B0293D34
2. http://6dtxgqam4crv6rr6.onion.to/1DD6FF20B0293D34
3. http://6dtxgqam4crv6rr6.onion.cab/1DD6FF20B0293D34
4. http://6dtxgqam4crv6rr6.onion.link/1DD6FF20B0293D34
Se nessuno dei precedenti indirizzi è disponibile, segui i passaggi successivi:
1. Scarica e installa Tor Browser: https://www.torproject.org/download/download-easy.html
2. Dopo la corretta installazione, avvia il browser e attendi l’inizializzazione.
3. Nella barra degli indirizzi digita: 6dtxgqam4crv6rr6.onion/1DD6FF20B0293D34
4. Segui le istruzioni a video.
!!! Il tuo numero d’identificazione personale è: 1DD6FF20B0293D34 !!! |
Change the desktop background image in _Locky_recover_instructions.bmp:
It creates the following registry key:
HKEY_CURRENT_USER\Software\Locky:
[id] = victim id
[pubkey] = RSA public key
[paytext] = redemption information
[completed] = if it is 1 then it has completed the encryption of the entire disk
When the CryptoLocky completed the entire disk, the malware modifies the registry key "pending rename file" in order to cancel itself the next reboot of the computer, leaving only the instructions for the redemption.
The ransom demanded by CryptoLocky:
Encrypted files by
CryptoLocky to be deencrypted require the payment of a ransom of 0.5 or 1.00 BitCoin.
How to protect yourself from CryptoLocky
As a general rule, we should never forget that behind every link or any attachments of each email could hide malware or Crypto-Malware.
Good practice would avoid clicking on links or on e-mail attachments that arrive as strangers or by people who seem known but with unexpected attachments. If you unfortunately has been executed the mail attachment which unleashes the hell of this new family of Crypto-Malware called
CryptoLocky and you are customer Vir.IT eXplorer PRO, you can restore any files encrypted by the attack using da
Vir.IT BackUp, when properly configured and used.
| To keep safe your valuable work we invite you to proceed as quickly as possible, in case you hadn't already done so, to configure and activate Vir.IT BackUp in order to have always available a recent backup protected by encryption from any new generation of Crypto-Malware like this. |
 |
What to do to mitigate the damage from CryptoLocky
As reported for other Crypto-Malware is appropriate, as soon as we notice the encryption of data in place, proceed to::
- DISCONNECT the LAN cable to prevent the Crypto-Malware might accidentally encrypt network drives (NAS, Server, etc.)
- DO NOT reboot the machine to prevent the restart of encrypting files by Crypto-Malware; if you restart the machine you should turn it off and keep turned it off until you get in touch with the technical support of TG Soft at phone numbers 049/631748
 049/631748 and 049/632750
049/631748 and 049/632750 049/632750 from Monday to Friday 8:30 a.m. to 12:30 p.m. / 14:30 p.m. to 18:30 p.m.
049/632750 from Monday to Friday 8:30 a.m. to 12:30 p.m. / 14:30 p.m. to 18:30 p.m.
This new Crypto-Malware family, till now, is being analyzed..
Final thoughts
We invite you to keep calm and, if not already done that, proceed to activate
Vir.IT BackUp on the main folders where the data files of your valuable work are being saved.
TG Soft
External Relations



