|
A nightmarish return from vacation for Italian users who found their NAS emptied.TG Soft's C.R.A.M. has detected a new type of attack affecting user data in Iomega NAS devices.
|
INDEX
==> The case examined by C.R.A.M
==> Useful Tips |
NAS (
Network Attached Storage) is a network mass storage device used to centrally store data. This makes data available to all machines connected to the LAN or even remotely through the Internet.
However, especially when exposed to the Internet, these devices can become a weak point, and thus can be subject to attacks designed to encrypt/delete or steal data/files stored on the device.
The case analyzed by C.R.A.M.
The case analyzed occurred on August 5, 2019 at 10:19 p.m., and affected a Iomega
HMND2 NAS when the company was closed for vacation.
Upon his return on September 2, the bitter surprise of finding their
NAS completely emptied with a ransom text file inside.
In the analyzed
NAS, the files were completely deleted (same as
Wiper-type attack), leaving only the text file with ransom instructions, as shown in the image below.
The text file contains details of the attack and instructions on how to proceed with file recovery: the amount of
BitCoins to be paid, the Wallet where to make the payment, the email to be contacted, and the personal id to be provided in the email.
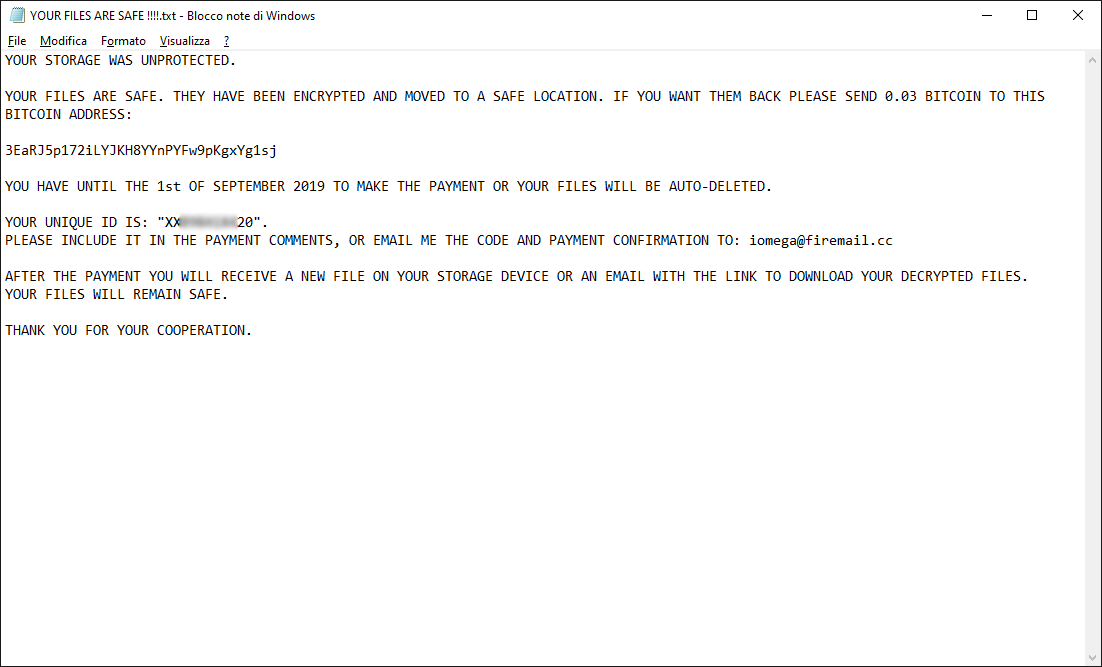
The Wallet listed is:
3EaRJ5p172iLYJKH8YYnPYFw9pKgxYg1sj and the demand from the CyberCriminal is
0.03 BitCoin equal to about
300 USD.
The Wallet on 02/09/2019 received 2 payments: one of
0.05 BitCoin and one of
0.03 BitCoin for a total of
0.08 BitCoin which is equivalent to about
781.58 USD equal to
712.97€.
It is still unclear whether the
NAS files were just deleted or stolen by the CyberCriminal.
In case they were simply deleted, we are dealing with a
Wiper, and therefore paying the ransom would still not lead to the recovery of the files but only to an economic loss.
Whereas in the case they were stolen by the CyberCriminal, we are dealing with a data breach that, in addition to the ransomware attack, must therefore also be handled under
GDPR.
In both cases, this type of attack does not encrypt the data.
How Iomega's NAS devices are accessed via the Internet remains unknown but there is a number of known vulnerabilities that could be exploited to gain access to the device panel with the ability to even file management (copy, delete, download, upload, etc.).
There is therefore a strong suspicion that CyberCriminals have used these vulnerabilities.
We also report
BleepingComputer's information regarding these types of attacks that occurred between late July and early August:
Attackers Are Wiping Iomega NAS Devices, Leaving Ransom Notes
Useful tips
TG Soft's C.R.A.M. found that gross errors are often made in the configuration of NAS devices in these types of attacks.
It is advisable to consider some technical arrangements including:
- Do not authorize access to the NAS from the Internet network or set up stricter rules in the firewall configuration to limit access to only authorized IPs and possibly only at set times .
- Always make offline backup copies of devices.
- Make Firmware updates regularly so as to avoid exploits (vulnerabilities).
- Always change the default device passwords.
C.R.A.M.
TG Soft's Anti-Malware Research Center
Back to top of page


