|
Report settimanale delle campagne italiane di malspam a cura del C.R.A.M. di TG Soft.
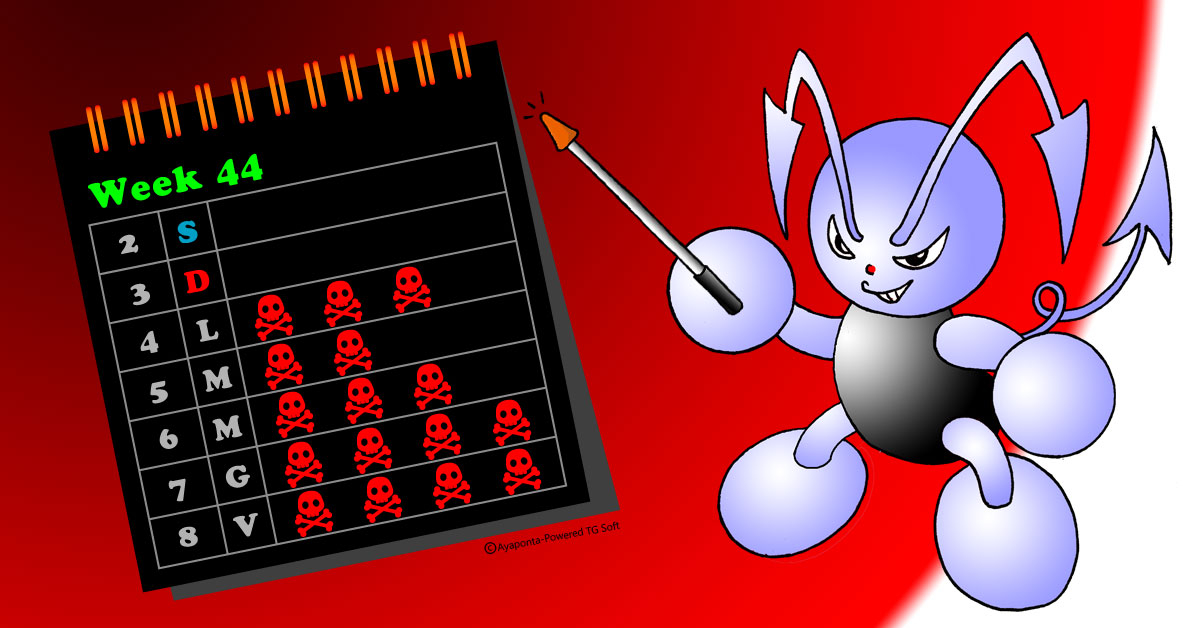
Di seguito i dettagli delle campagne diffuse in modo massivo nella settimana appena trascorsa dal 02 novembre 2019 al 08 novembre 2019: Ursnif, Emotet, Remcos, HawkEye, PWStealer, LokiBot, Adwind
|
INDICE
==> 04 novembre 2019 => HawkEye, Emotet, Ursnif
==> 05 novembre 2019 => Emotet, Remcos
==> 06 novembre 2019 => Emotet - PWStealer
==> 07 novembre 2019 => Emotet - LokiBot - PWStealer - Ursnif
==> 08 novembre 2019 => Emotet - PWStealer - Adwind - LokiBot
==> Consulta le campagne del mese di Ottobre
|
HawkEye
Elenco di spedizione_00000233473.exe
MD5: cb13b75a754e6cb60f99333e9eb2ed82
Dimensione: 2028544 Bytes
VirIT: Trojan.Win32.Genus.BUL
IOC:
cb13b75a754e6cb60f99333e9eb2ed82
Emotet
DATI_2019_T_6127051.doc
MD5: e8bac745a415fd03c5bde25c362b2251
Dimensione: 166383 Bytes
VirIT: W97M.Downloader.BUL
termscalar.exe
MD5: 5ff32c3abffdd9d17b7a9b41aad9a93d
Dimensione: 340006 Bytes
VirIT: Trojan.Win32.Emotet.BUO
IOC:
e8bac745a415fd03c5bde25c362b2251
5ff32c3abffdd9d17b7a9b41aad9a93d
p://76.69.29[.]42
51.254.218[.]210
239.255.255[.]250
Ursnif
Ft_0022000358_001_008970.xls
MD5: 9fd28d08497495bacf1959240ca67a4f
Dimensione: 6400 Bytes
VirIT: X97M.Downloader.HV
IOC:
9fd28d08497495bacf1959240ca67a4f
Emotet
messaggio 05 US_769503.doc
MD5: e47f4f07c170b2ea472dfc6523fda54b
Dimensione: 269449 Bytes
VirIT:
W97M.Downloader.BUN
termscalar.exe
MD5: e18e6666652c48bfee8f68ba4cd50c5a
Dimensione: 340104 Bytes
VirIT:
Trojan.Win32.Emotet.BUO
IOC:
e47f4f07c170b2ea472dfc6523fda54b
e18e6666652c48bfee8f68ba4cd50c5a
p://76.69.29[.]42
189.189.56.216
51.255.165.160
Remcos
Invio Fattura.exe
MD5: 5a066a50717b5aadc9a953df01cef70a
Dimensione: 614400 Bytes
VirIT:
Trojan.Win32.PSWStealer.BUO
IOC:
5a066a50717b5aadc9a953df01cef70a
79.134.225[.]90
Emotet
Fattura n. 6363527 del 06.11.2019.doc
MD5: f5496c5f7ec2c0b2fb0f148ca5128584
Dimensione: 237030 Bytes
VirIT:
W97M.Downloader.BUP
termscalar.exe
MD5: 690be7e699e4ae5366bc04aa261a0536
Dimensione: 786432 Bytes
VirIT:
Trojan.Win32.Emotet.BUP
IOC:
f5496c5f7ec2c0b2fb0f148ca5128584
690be7e699e4ae5366bc04aa261a0536
s://165.227.156[.]155
p://139.162.183[.]41
PWStealer
Ordine di Acquisto 584-2.exe
MD5: 0fa5fdfd2a223c2288e817344dafaf97
Dimensione: 602112 Bytes
VirIT: Trojan.Win32.PSWStealer.BUI
IOC:
0fa5fdfd2a223c2288e817344dafaf97
Emotet
DATI_112019_501_04044.doc
MD5: 0e60c7f4cc76d75d749533905c96b2c6
Dimensione: 167084 Bytes
VirIT:
W97M.Downloader.BUR
185.exe
MD5: cb2448a07a09f51ed7a6886797b6a85c
Dimensione: 42938 Bytes
VirIT:
da vedere
IOC:
0e60c7f4cc76d75d749533905c96b2c6
cb2448a07a09f51ed7a6886797b6a85c
LokitBot
SWIFT.exe
MD5: aabc064bdba695571cab0b43bb6e5e44
Dimensione: 1191936 Bytes
VirIT:
Trojan.Win32.Genus.BUJ
IOC:
aabc064bdba695571cab0b43bb6e5e44
matbin[.]com
85.187.128[.]8
PWStealer
00173011985311.exe
MD5: 117d5ae395bc7588a208ba2e9385af7f
Dimensione: 581632 Bytes
VirIT:
Trojan.Win32.Genus.BUR
IOC:
117d5ae395bc7588a208ba2e9385af7f
Ursnif
info_11_07.doc
MD5: 67623a86d3daa99ae7b2d8e893c2b57c
Dimensione: 100155 Bytes
VirIT: W97M.Downloader.BUR
953.exe
MD5: 4af0359319f4fbb7f5e2573f12d4b4f5
Dimensione: 309248 Bytes
VirIT: Trojan.Win32.Ursnif.BUR
IOC:
67623a86d3daa99ae7b2d8e893c2b57c
4af0359319f4fbb7f5e2573f12d4b4f5
83.166.240[.]86
216.58.206[.]46
216.58.206[.]68
152.199.19[.]161
93.184.220[.]29
t6kamillemoshe[.]com
194.87.144[.]66
137.117.243[.]30
93.184.220[.]29
Emotet
6071226 G_05159.doc
MD5: 346d2ba646f202e735535b9d80ca217c
Dimensione: 224188 Bytes
VirIT:
W97M.Downloader.BUT
IOC:
346d2ba646f202e735535b9d80ca217c
p://langchaixua[.]com
PWStealer
SPEDIZIONE UPS_pdf.exe
MD5: b796ccb5c71056003b1a1f97a7fa53d3
Dimensione: 581632 Bytes
VirIT: Trojan.Win32.Genus.BUT
IOC:
b796ccb5c71056003b1a1f97a7fa53d3
Adwind
Invoice11-08-2019-PDF.jar
MD5: 3c371193b871e17000e6172d2dffdc1a
Dimensione: 511448
VirIT: Trojan.Java.Adwind.BUU
Retrive7702109354503637846.vbs
MD5: 3bdfd33017806b85949b6faa7d4b98e4
Dimensione: 276 Bytes
VirIT: Trojan.VBS.Agent.AU
Retrive557713677600779021.vbs
MD5: a32c109297ed1ca155598cd295c26611
Dimensione: 281
VirIT: Trojan.VBS.Agent.AU
0.00277072144636125733599132884258641873.class
MD5: 781fb531354d6f291f1ccab48da6d39f
Dimensione: 247088 Bytes
VirIT: Trojan.Java.Agent.IKB
IOC:
3c371193b871e17000e6172d2dffdc1a
3bdfd33017806b85949b6faa7d4b98e4
a32c109297ed1ca155598cd295c26611
781fb531354d6f291f1ccab48da6d39f
LokiBot
SWIFT.exe
MD5: 3d99134fadbad1a390264c02088c40fa
Dimensione: 1138688 Bytes
VirIT: Trojan.Win32.Genus.BUU
IOC:
3d99134fadbad1a390264c02088c40fa
p://matbin[.]com
85.187.128[.]8
Consulta le campagne del mese di Ottobre
Vi invitiamo a consultare i report del mese di Ottobre, per rimanere aggiornati sulle campagne di malspam circolanti in Italia:
28/11/2019 =
Report settimanale delle campagne italiane di Malspam dal 28 ottobre al 31 Ottobre 2019
21/10/2019 =
Report settimanale delle campagne italiane di Malspam dal 21 ottobre al 25 ottobre 2019
14/10/2019 =
Report settimanale delle campagne italiane di Malspam dal 14 ottobre al 18 ottobre 2019
C.R.A.M.
Centro Ricerche Anti-Malware di TG Soft