
11/11/2019
15:42

|
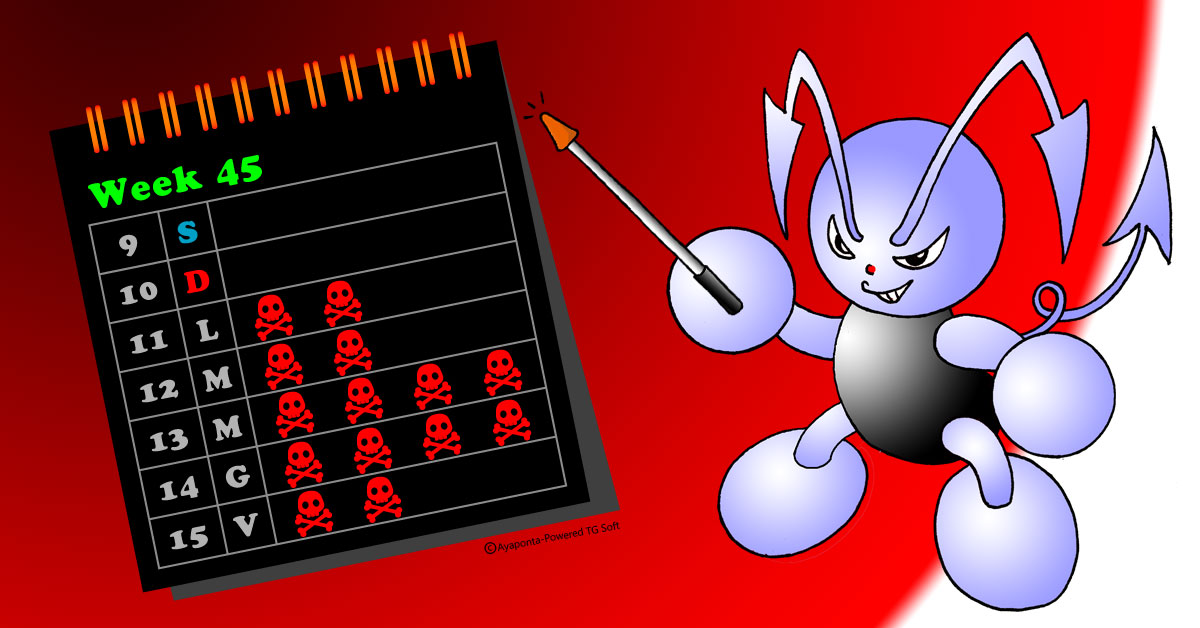
Report settimanale delle campagne italiane di malspam a cura del C.R.A.M. di TG Soft. Di seguito i dettagli delle campagne diffuse in modo massivo nella settimana appena trascorsa dal 11 novembre 2019 al 15 novembre 2019: Ursnif, Emotet, LokiBot, Adwind, Genus |
INDICE==> 11 novembre 2019 => Emotet - Adwind==> 12 novembre 2019 => Emotet - Password Stealer ==> 13 novembre 2019 => Emotet - Adwind - LokiBot - Ursnif ==> 14 novembre 2019 => Emotet - Password Stealer ==> 15 novembre 2019 => Emotet - Adwind ==> Consulta le campagne del mese di Ottobre |
|
Fattura 2019 - IT 002654.doc
MD5: 0393ac6cf8a357338aac032650cae82c
Dimensione: 215345 Bytes
VirIT: W97M.Downloader.BUV
siteprivacy.exe
MD5: 8caada83d6b76d578b45a9a3ae53c384
Dimensione: 738642 Bytes
VirIT: Trojan.Win32.Emotet.BUV
IOC:
0393ac6cf8a357338aac032650cae82c
8caada83d6b76d578b45a9a3ae53c384
9901524e9a141d274702143aee85e5e8
p://104.239.175[.]211
p://67.225.179[.]64
p://31.172.240[.]91/
p://179.12.170[.]148
p://46.105.131[.]87
s://37.157.194[.]134
p://181.57.193[.]14
p://46.101.7[.]140
p://181.57.193[.]14
Invoices-11-2019-PDF.jar
MD5: c8a90f5eb7694e1e75a9a7815360539c
Dimensione: 510849 Bytes
VirIT: Trojan.Java.Adwind.BUW
Retrive6212323720970522129.vbs
MD5: 3bdfd33017806b85949b6faa7d4b98e4
Dimensione: 276 Bytes
VirIT: Trojan.VBS.Agent.AU
Retrive6212323720970522129.vbs
MD5: a32c109297ed1ca155598cd295c26611
Dimensione: 281 Bytes
VirIT: Trojan.VBS.Agent.AU
IOC:
c8a90f5eb7694e1e75a9a7815360539c
3bdfd33017806b85949b6faa7d4b98e4
a32c109297ed1ca155598cd295c26611
p://jbond[.]sytes[.]net/
Invio ns. ord.forn.n°1696 del 13.11.2019.exe
MD5: 8f4f4d1bdd314affb55e3791b5576b32
Dimensione: 1150976 Bytes
VirIT: Trojan.Win32.Genus.BVA
IOC:
8f4f4d1bdd314affb55e3791b5576b32
p://sglobal[.]online/
N_860 del 06_10_19.xls
MD5: e28e1ce26c528b945079676cfd64fe4b
Dimensione: 54272 Bytes
VirIT: X97M.Downloader.HW
IOC:
e28e1ce26c528b945079676cfd64fe4b
Documenti contrattuali.pdf.exe
MD5: 5f04f2d19960a42a81b7fa8336c7f1a6
Dimensione: 371712 Bytes
VirIT: Trojan.Win32.Genus.BVB
IOC:
5f04f2d19960a42a81b7fa8336c7f1a6
656655677doc.exe
MD5: 8436808ba46240e1f5eb4e9e8194c69e
Dimensione: 293668 Bytes
VirIT: Trojan.Win32.Genus.BVB
IOC:
8436808ba46240e1f5eb4e9e8194c69e
2019-11-14DFRM.jar
MD5: cb40a95ebcf0919006b02cc24ef43c91
Dimensione: 510849 Bytes
VirIT: Trojan.Java.Adwind.BUW
Retrive6737736402426360148.vbs
MD5: 3bdfd33017806b85949b6faa7d4b98e4
Dimensione: 276 Bytes
VirIT: Trojan.VBS.Agent.AU
Retrive5781066781607137463.vbs
MD5: a32c109297ed1ca155598cd295c26611
Dimensione: 281 Bytes
VirIT: Trojan.VBS.Agent.AU
IOC:
cb40a95ebcf0919006b02cc24ef43c91
3bdfd33017806b85949b6faa7d4b98e4
a32c109297ed1ca155598cd295c26611
p://jbond[.]sytes[.]net/