Now TeslaCrypt is striking back, with a brand new core (version 3.0).
Computers are being infected by TeslaCrypt in two ways:
- the cryptomalware is downloaded by other malwares, such as SathurBot, or
- it is delivered via email.
The emails that carry the malware have a pretty simple layout:
- subject: "<recipient>"
- message body: "DATE:1/26/2016 2:26:46 PM"
- attachment: .zip file, its name being 3 random characters
The message body contains various blank lines, the last one beginning with "DATE:" and the hour of dispatch. |
TeslaCrypt Attack
Flowchart
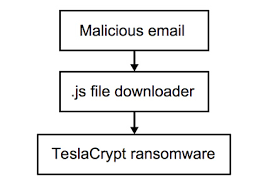 |
The attachment is a
.zip archive with a random name; it contains a
javascript (
.js) file, its name being similar to:
- invoice_SCAN_<random>.js;
- invoice_copy_<random>.js;
- invoice_<random>.js
Once the javascript file has been executed, it will download and start the TeslaCrypt executable file.
Below are some details on the executable.
<random>he45.exe
| Name |
MD5 |
Size |
| RDCWJHE45.exe |
F366798A03E0CF9F8492EA1198F7FB5B |
585728 |
| TMWLCHE45.exe |
DEE372F96C13203DAFA03DA0AC92B810 |
589824 |
| WNFLOHE45.exe |
65F225234F235BD36ED3E789F5D0B7BC |
585728 |
| MYNHDHE45.exe |
5520D165361BDB5F87DEB343E34DC8E7 |
585728 |
TeslaCrypt also alters a registry key, in order to be executed at every login:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
[zsevice-455] = C:\USERS\<username>\APPDATA\ROAMING\<random>HE45.EXE
The encryption algorithm used by TeslaCrypt is a 256 bit AES CBC.
The encryption key is not stored in the attacked computer, but it is sent to a server via TOR-Onion network.
To generate the public key, this cryptomalware uses ECDH (Ellipitc Curve Cryptography Diffie-Hellman) algorith.
It is still impossible to decrypt encrypted files, unless the private 256 bit key is known. |
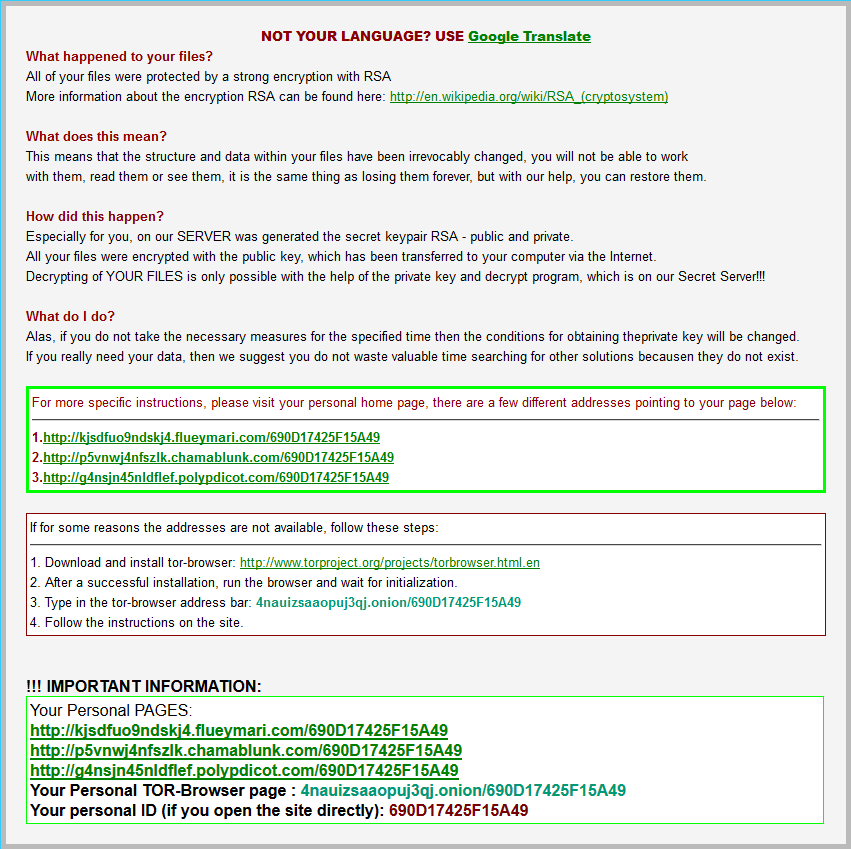
Click here to show the picture fullscreen |
Those files that have been encrypted by
TeslaCrypt 3.0 bear its signature
.micro extension; furthermore, the malware leaves instructions on how to pay the ransom:
- help_recover_instructions.BMP
- help_recover_instructions+xjp.txt
- help_recover_instructions+xso.html
Below are some details on the "recovery" files.
help_recover_instructions+<3 random characters>.txt/.html/.bmp
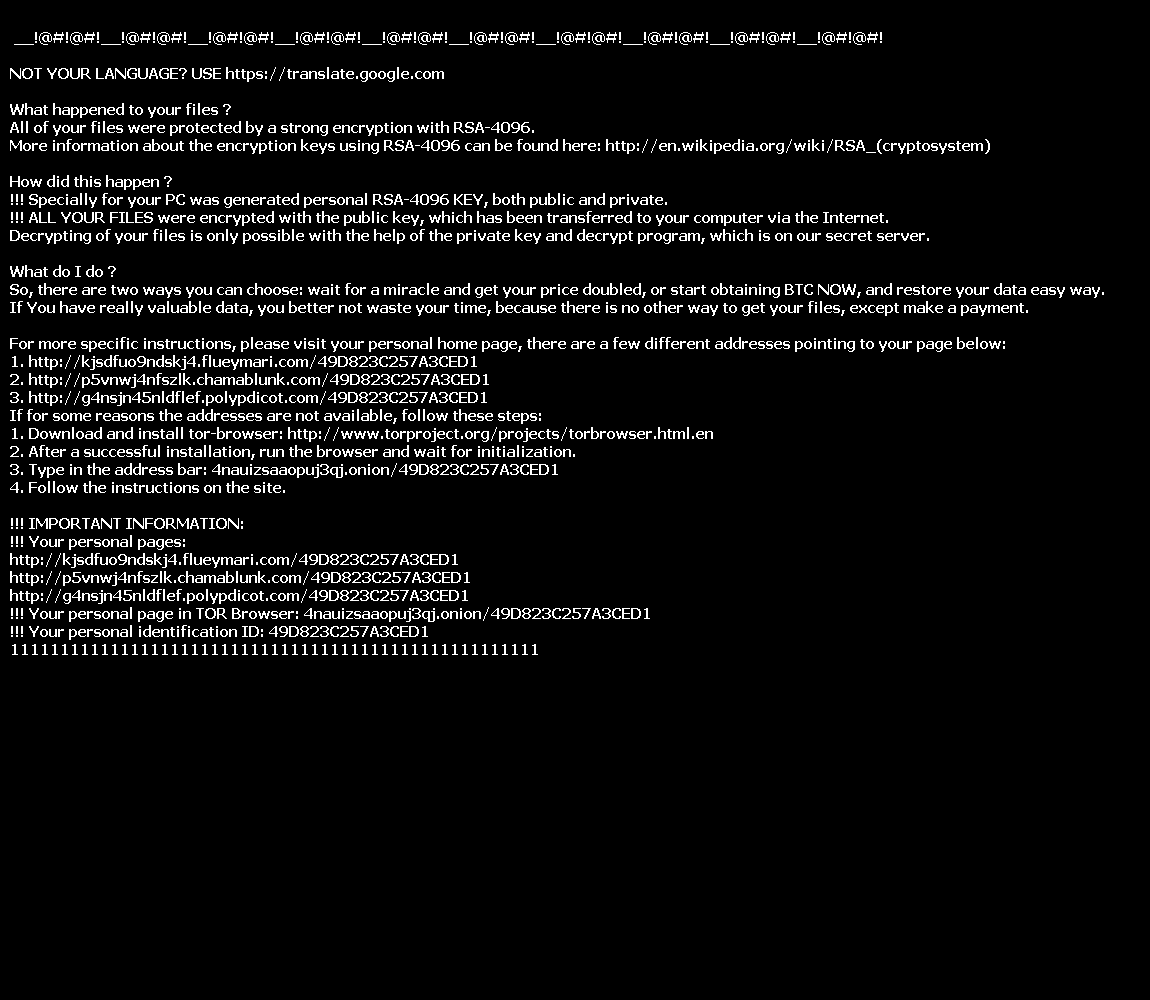 |
__!@#!@#!__!@#!@#!__!@#!@#!__!@#!@#!__!@#!@#!__!@#!@#!__!@#!@#!__!@#!@#!
__!@#!@#!
NOT YOUR LANGUAGE? USE https://translate.google.com
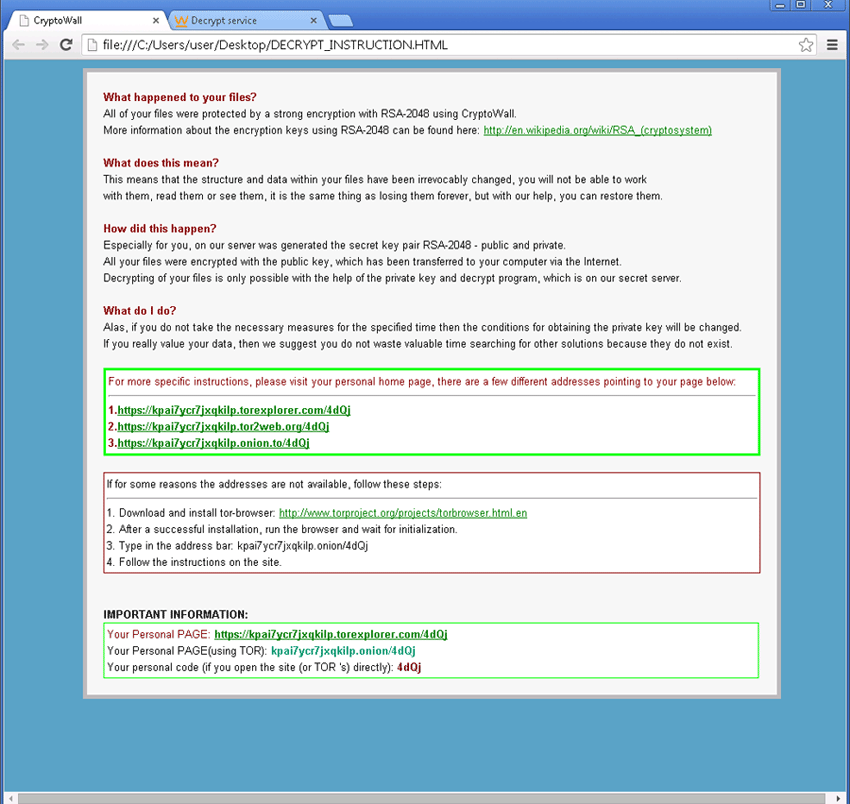
What happened to your files ?
All of your files were protected by a strong encryption with RSA-4096.
More information about the encryption keys using RSA-4096 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA-4096 KEY, both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
So, there are two ways you can choose: wait for a miracle and get your price doubled, or start obtaining BTC NOW, and restore your data easy way.
If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment.
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1. http://kjsdfuo9ndskj4.flueymari.com/690D17425F15A49
2. http://p5vnwj4nfszlk.chamablunk.com/690D17425F15A49
3. http://g4nsjn45nldflef.polypdicot.com/690D17425F15A49
If for some reasons the addresses are not available, follow these steps:
1. Download and install tor-browser: http://www.torproject.org/projects/torbrowser.html.en
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: 4nauizsaaopuj3qj.onion/690D17425F15A49
4. Follow the instructions on the site.
!!! IMPORTANT INFORMATION:
!!! Your personal pages:
http://kjsdfuo9ndskj4.flueymari.com/690D17425F15A49
http://p5vnwj4nfszlk.chamablunk.com/690D17425F15A49
http://g4nsjn45nldflef.polypdicot.com/690D17425F15A49
!!! Your personal page in TOR Browser: 4nauizsaaopuj3qj.onion/690D17425F15A49
!!! Your personal identification ID: 690D17425F15A49
11111111111111111111111111111111111111111111111111111 |
Vir.IT eXplorer PRO's
Anti-CryptoMalware module, thanks to its heuristic-behavioural technologies, can limit damage caused by cryptomalwares including
TeslaCrypt and new generation ones. Moreover, the
Anti-CryptoMalware module is able to "snatch" the encryption key on-the-fly, hence making decryption of encrypted files possible.
We will now explain what cryptomalwares are and how they operate.
Cryptomalwares: what they are and how they work
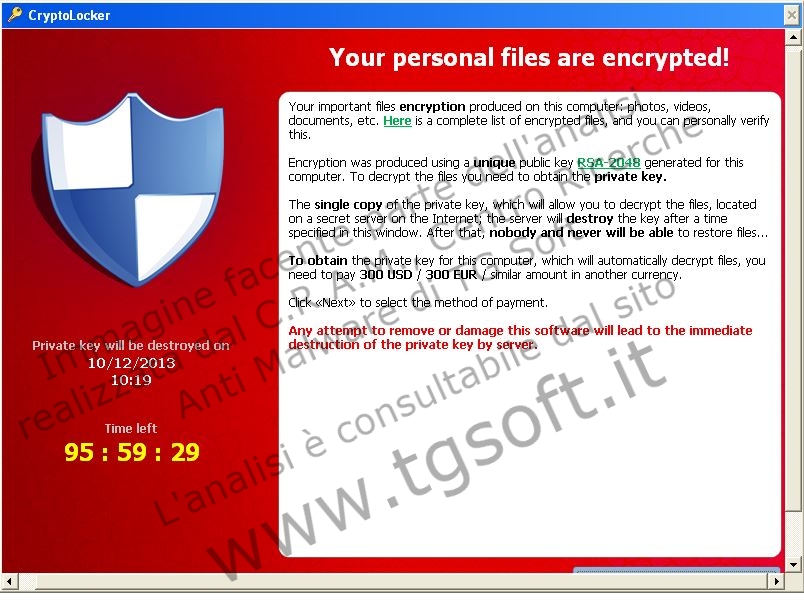
Cryptomalwares are a type of ransomware: files are made inaccessible through encryption, and to have them decrypted the user has to pay a ransom. A new variant is released every hour or so; the most infamous ones are CryptoLocker, CTB-Locker, CryptoWall and TeslaCrypt. Because of this rapid turnover, intercepting them using a method based on identification signatures is virtually impossible; signature-based real-time protection is ineffective.
|
 |
 |
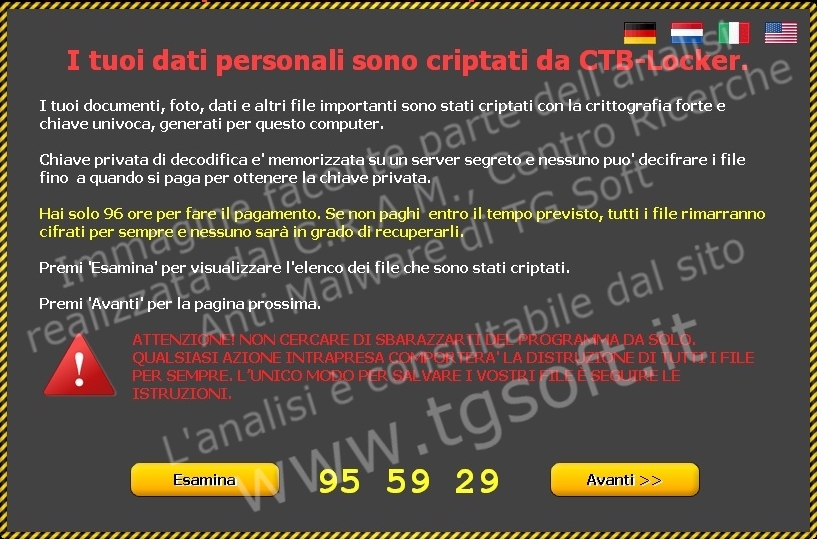 |
Cryptomalwares have these peculiar features:
- They generally are "polymorphic" malwares, meaning that they can self-mutate. This polymorphism is achieved by activating totally different files from the same link in a very short time span (sometimes even 15 minutes); such links spawn cryptomalwares or other types of viruses/malwares, such as droppers, rootkits, etc. Because of this frequence, an antimalware software relying on the traditional, signature-based real-time protection technique will never be able to intercept and stop these threats.
- They have a very short, sometimes null, incubation period. The activation is immediate and its effects (encryption of .doc, .xls, .mdb, .jpg, but also backup files) take place very quickly.
- Their encryption algorithms are extremely sophisticated, sometimes 2.048 bit long, thus making them irrecoverable.
- They ask for a ransom to have files decrypted. Ransoms are paid via Tor-Onion network (deep/dark-web), and the BitCoin virtual currency is used in virtually all cases.
|
How to stay safe from cryptomalware attacks with Vir.IT eXplorer PRO technologies
In our 26/11/2015 bulletin, we tried to describe those technologies built into Vir.IT eXplorer PRO and how to use them properly.
|
TG Soft's Research Centre (C.R.A.M.) has been analyzing the most widespread cryptomalware types for three years, and has developed two technologies:
- Vir.IT BackUp, an advanced backup utility devised to protect every user's most precious files. Vir.IT BackUpis very simple and straightforward to use; it allows the user to select the files and folders they want to have a backup copy of. The copy is an automated and scheduled process. Should a computer be infected by a new generation and yet-to-be-identified cryptomalware causing widespread encryption, Vir.IT BackUp copies can be reverted, since an advanced BackUp system is used, so that these copies can hardly be accidentally deleted or "forcefully" altered by some malware.
- A real-time protection module based on a heuristic and behavioural approach. It is capable of identifying those tasks that behave in a similar way to cryptomalwares and, once identified, it can halt them, thus stopping the encryption and saving more than 99.63% of data files.
It was verified on real attacks that the minimum number of encrypted files, in the early stages of cryptomalware attacks (even new generation ones), is 5 - thus sparing every other file. Potentially encryptable files are approximately 10'000, so this technology effectiveness stands at (1-5/10.000)*100 = 99,95%.
- In the very short time span when the cryptomalware has just begun encrypting data and the heuristic automata has yet to intervene, Vir.IT eXplorer PRO AntiCryptoMalware module enacts a techique called "On-The-Fly Backup", which:
- creates a backup copy of document files (such as .doc, .xls, .pdf, .jpg) between 2KB and 3MB;
- stores these copies for 48 hours to allow recovery in case of necessity.
|



99,63%*
Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO

|
 |
If Vir.IT eXplorer PRO has been correctly set up, it is possible to save up to 100% of data in case of cryptomalware. Those file that may have been encrypted in the early stages of the attack can be restored thanks to Vir.IT BackUp, thus reducing the loss to 15/20 files - in the case they were created/edited before a new backup could be made.
|
Vir.IT eXplorer PRO users can take advantage of these technologies, especially
Vir.IT Backup, in order to save their precious data from cryptomalware or other yet-to-be-discovered malicius software and their variants.
How and where to buy Vir.IT eXplorer PRO security suite
Decryption of files, which have been encrypted with 2048 bit long keys, is only theoretically possible, but it is technically impracticable. We invite you to consider the purchase of
Vir.IT eXplorer PRO since
prevention is the only way to contrast cryptomalwares.
Vir.IT eXplorer PRO can be purchased in the following ways:
TG Soft - Public Relations
*Mean percentage of files saved from encryption thanks to Vir.IT eXplorer PRO technologies - data gathered from actual cryptomalware attacks by TG Soft's Research Centre (C.R.A.M), October 2015.









