TGSoft's
C.R.A.M. after having collected numerous reports about this new malware, the
Worm.Win32.Dorkbot, have decided to analyze the viral code to explain how it works and the best methods to prevent the infection.
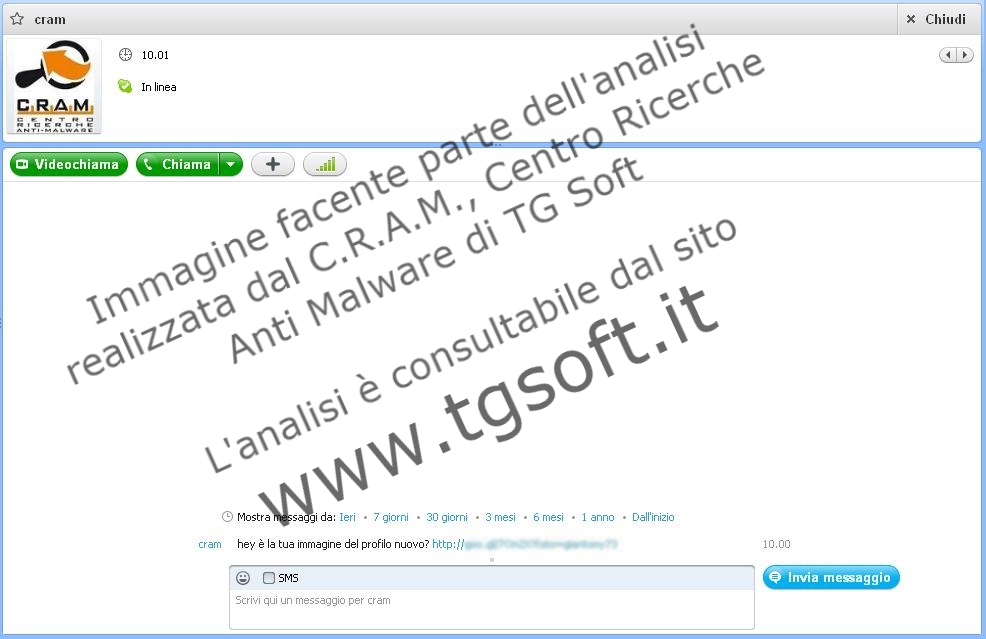
This malware spread itself through Skype messages, they come from another contact which have contracted the infection before.
The virus sends a message similar to this to every contact in our list, once we're infected:
The unaware user won't see outgoing malicious messages, once infected, because the malware will hide every message sent from the pc to the contacts. Users can follow these little tips to prevent or be aware of the infection:
- Ask to your contacts wether they have received a malicious message like the example above or not;
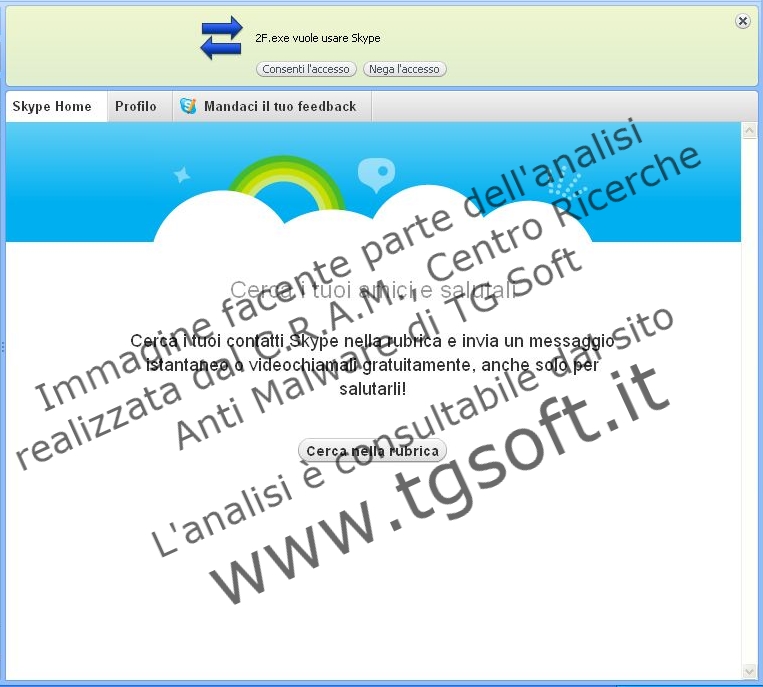
- Verify if, during skype daily usage, appear messages like this:"xxx.exe wants to use skype. Allow - Deny" (file name is random) as you can see in the picture below:
Click per ingrandire |
These pop-ups acknowledge the user about every program that tries to use skype, in this case the program is the malware; this is a basic skype protection that can prevent the infection from spreading through our contact list. The final decision is on the user, usually users tends to click on ALLOW but we always suggest to click on DENY, because if the application is a good one you can always change this preference by going into skype options.
|
To contract the infection you have to click on the malicious link:
"http://goo.gl/xxxxx?foto=skype_id"
The link has the following syntax: websitename?foto=skype_id where the skype_id is your own skype id. In this way, malware creators always known how many skype users got infected from the virus.
By clicking on the link, user's browser will visit a russian website that will download a .zip file. An executable file containing the virus will be found inside this compressed archive, obviously it will have a misleading name such as: "Skype_(actual-date)_foto.exe".
Here are some version of the virus we have intercepted:
| Nome Malware |
Nome File |
Dimensioni |
MD5 |
| Worm.Win32.Dorkbot.A |
Cqgggi.exe |
480.256 byte |
b9f6b844599bd50e67c3337d14eff8cf |
| Worm.Win32.Dorkbot.A |
Mstitu.exe |
494.080 byte |
1c9bcdb4362c581d4a1836585e01ea78 |
| Worm.Win32.Dorkbot.B |
Hulclj.exe |
494.080 byte |
ebf75b1191ef718519a89670bb1bf4de |
| Worm.Win32.Dorkbot.B |
Zzjijh.exe |
494.080 byte |
ebf75b1191ef718519a89670bb1bf4de |
| Worm.Win32.Dorkbot.C |
Dyzszv.exe |
477.696 byte |
424ff5318f166686df49a56b49a285b9 |
| Worm.Win32.Dorkbot.D |
Cqgggi.exe |
1.040.384 byte |
737a8888937e6a105ee5d47af48f0fe1 |
| Worm.Win32.Dorkbot.D |
Nvcwcj.exe |
119.808 byte |
68568239412f5f93d572c3813a5dc390 |
| Worm.Win32.Dorkbot.E |
DJDUDX.EXE |
97.280 byte |
f84178426ab688ea35ec4d96d18537f9 |
| Worm.Win32.Dorkbot.F |
Skype_10172012
_foto.exe |
155.136 byte |
8a7330f30e2c806d6eac66815bed517a |
The
Dorkbot worm, will be executed at every PC startup because he will create the following registry key:
[HKEY_CURRENT_USER->Software->Microsoft- >Windows->CurrentVersion->Run]
[name of the executable] = %appdata%\[name of the executable]
where %appdata% (WindowsXp) = C:\Documents and Settings\Utente\Application Datai\
(WinVista and/or Win7) = C:\Users\Utente\AppData\Roaming\
Inside the same virus directory, with random file neames, we will find other viruses identified as
Trojan.Win32.Pornoasset and
Trojan.Win32.Crypt, that will be used by the malware.
To completely remove the malware, it's necessary to boot the pc into safe boot (F8 at the PC startup, before the window logon) where it won't be executed. If the virus won't be found by VirIT eXplorer because it's a new iteration of the malware, PRO version's clients can call TG Soft remote assistance.
Go to the remote assistance page
The malware uses another technique to spread itself faster: when a removable drive (e.g.: a usb key) gets inserted into a PC with the malware it will be infected so that it could be executed on a non-infected PC, and then spread from the other PC.
Infected usb keys use the Link Spread method:
- Every folder and file inside the USB key will become "invisibles" because the malware add the "hidden" and the "system file" attributes; It will be possible to see them again by editing folder option preferences->Show hidden files and folders and by remove the tick from "hide protected operating system files"
- It will be created an hidden folder named "RECYCLER" where the malware will copy itself into it with a random name;
- The virus will create a link for every folder and file that have been hidden (LNK Spread), once the user opens a lnk the malware will be launched and then the file or the folder will be opened normally;
To clean the infected drive, after a deep PC scan from a non-infected PC, we will have to restore files and folders normal state, to do this we have to do the following operations::
- Open windows' notepad and copy the following line:
attrib -s -h DriveLetter:\*.* /d /s
where DriveLetter is the letter of the removable drive;
- Save the file in a folder of preference with the name "fixusb.bat" and select save as "All files (*.*) "
- Execute the file you've just created and wait for the operation to be completed.
Analysis done by TG Soft's
C.R.A.M. Centro Ricerche Anti Malware