TG Soft' s C.R.A.M. (Anti-Malware Research Center) analyzed the email campaign spreading the Trojan Banker GootKit malware on June 20, 2018.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research) How to identify a fake email
|
INDEX
|
"GootKit" malware campaign.
Name: Trojan.Win32.
GootKit
Malware Family: GootKit
VirIT: JS.Dropper.PN, Trojan.Win32.GootKit.AT
Description:
The email was detected this morning on June 20, 2018.
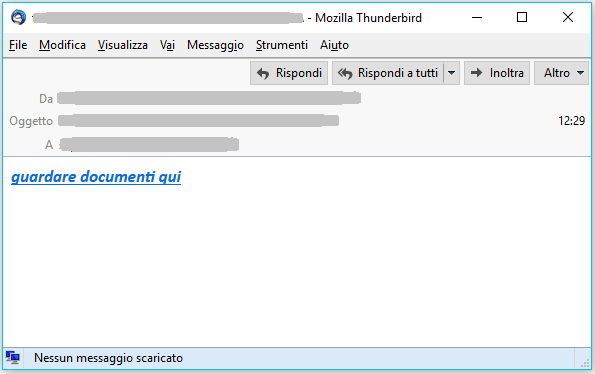
Example of examined email:
|
Subject: variable based on a previous email
|
guardare documenti qui (look at documents here)
|
 |
How it spreads:
The email is very basic with a simple link named "look at documents here". The link points to the site
http://www[.]emailcharities[.]com/ifsn?fmav=34095 and, when clicked, leads to the download of a .ZIP archive file named "New Document 2018.zip"
The .ZIP archive contains a JavaScript file named "
Nuovo documento 2018.js" which, if executed, will result in the download and execution of the GootKit malware.
When the JavaScript file is opened, it downloads the malware to the user's temporary folder (%temp%) and then executes it.
The JavaScript file analyzed, downloads malware from the following site:
- http://klmnopq[.]com/pagenewex12[.]php
The payload examined has the following characteristics:
File Name: haytheorystate.exe
Size: 270336 byte
MD5: 3A37505683F72D9F7A71D8B33D3BCC99
The Trojan.Win32.GootKit.AT, once executed, creates in the same folder a file with the extension .inf and name "haytheorystate.inf" containing the following instructions:
[Version]
signature = "$CHICAGO$"
AdvancedINF = 2.5, "You need a new version of advpack.dll"
[DefaultInstall]
RunPreSetupCommands = hqtwyavveuoyvmsifxistirboynzrs:2
[hqtwyavveuoyvmsifxistirboynzrs]
[%temp%]\haytheorystate.exe |
and automatically runs, modifying the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\IEAK\GroupPolicy\PendingGPOs
[Count] = 1
[Path1] = "[%temp%]\haytheorystate.inf"
[Section1] = "DefaultInstall"
Il Trojan.Win32.GootKit is part of the Banker macrofamily, its peculiarities are to steal passwords for access to important sites such as may be home banking, e-mail, ftp etc.
IOC:
MD5:
3A37505683F72D9F7A71D8B33D3BCC99
F81D2316C9BB011405736A291EFBF912
ADABF0C4FBB93FA12DEBAC774EFC4928
B271EAEF6C0851A4DC12D978F01D6CAD
B4FF1D5CF5D2A69FEEE6174B81AA704F
23EEB807B3F68372326FF49C50459B92
BF860696630A43EE1D66A1C7B6CF54F5
3E776BA9D3D9E4BABA4371504BAD40FB
DE96D156377F77DA46364C606D03F1BE
URL:
http://www[.]emailcharities[.]com/ifsn?fmav=34095
http://klmnopq[.]com/pagenewex12[.]php
198.54.115.35
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of ZIP-formatted attachments and, if possible, DO NOT enable automatic macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening Word and Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a Banker, the advice from TG Soft's C.R.A.M., is to take appropriate security precautions even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the wokstation involved is used for home-banking transactions, an assessment with your credit institution is also recommended. .
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to the TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page INVIO File Sospetti (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- Through the Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center




