|
Sometimes business needs (and too much haste to achieve goals) can distract from what has become a global and unavoidable issue today: CYBER SECURITY. More and more users need technologies that allow them to work and access data and programs remotely, especially as a result of the spread of CLOUD systems.
These needs expose to cyber attacks by CyberCriminals.
|
INDEX
==> A case detected by the C.R.A.M..
==> Evidence confirming the intrusion
==> Useful tips
|
In fact attacks persist with remote desktop access (RDP) to PCs/Servers aimed at encrypting files with Ransomware/CryptoMalware, for ransom purposes.
RDP protocol
(Remote Desktop Protocol) is a remote management protocol developed by Microsoft and found in all Windows® Operating Systems used for remote PC/Server management that, if not configured properly, can be exploited as a point of attack.
In fact, PCs/Servers with active
RDP and exposed to the Internet are subject to attacks aimed at obtaining login credentials.
Usually the initial phase of the attack is by "
brute forcing" credentials to gain access to the machine.
Once access is gained, the CyberCriminal can perform various operations:
- Theft of passwords/information/data.
- Running Ransomware/CryptoMalware.
- Lateral movement.
- Tampering with security systems.
Actually, there is a growing increase in "lateral movements": the attacker can move through the internal network (LAN) either through the incorrect, but now established, habit of storing passwords for access to other networked systems, or through the use of ad hoc tools capable of extracting passwords.
In this way the attacker can enlarge the attack surface increasing the range of potential damage.
Finally the Ransomware/CryptoMalware is executed so that the data is encrypted and then the ransom demand is made. In these first 8 months of 2019, the main Ransomware/CryptoMalware used are:
- Dharma/Phobos
- GandCrab (service officially ended in the period of May and June 2019)
- Sodinokibi/REvil
The analysis of the
CryptoMalware Sodinokibi/REvil, that seems to have officially replaced
GandCrab, can be seen at this address:
REvil ransomware technical analysis - Sodinokibi and Threat Intelligence Report
The focus by CyberCriminals on RDP access is also favoured by the recent vulnerabilities discovered on this protocol, such as:
It is crucial, to defend yourself, in addition to an active and up-to-date antivirus, antispyware, antimalware, and antiransomware solution, to perform Operating System updates regularly so as to avoid exploitation of protocol flaws.
In the next section, we will illustrate how some CyberCriminals materialized unauthorized access via
RDP and then infected the machine with Ransomware/CryptoMalware. As previously reported in the August 2017 news: "
Remote Desktop, if misconfigured, becomes an easy entry for CryptoMalware"
The actual case examined by C.R.A.M.
The case we will perform as an example concerns an unauthorized access, which actually occurred, affecting a client machine with Windows 7 Professional Sp1 installed.
Other operating systems including server versions are not exempt from this threat.
When we asked some preliminary questions to the users involved, no one recalled opening any suspicious emails or otherwise clicking some untrustworthy links.
Then, excluding e-mail as a vehicle of infection, the search for the cause began. The only certain thing known by C.R.A.M. were some encrypted files (extension ".crypton") and the presence of the file with the ransom instructions (photo at right). |
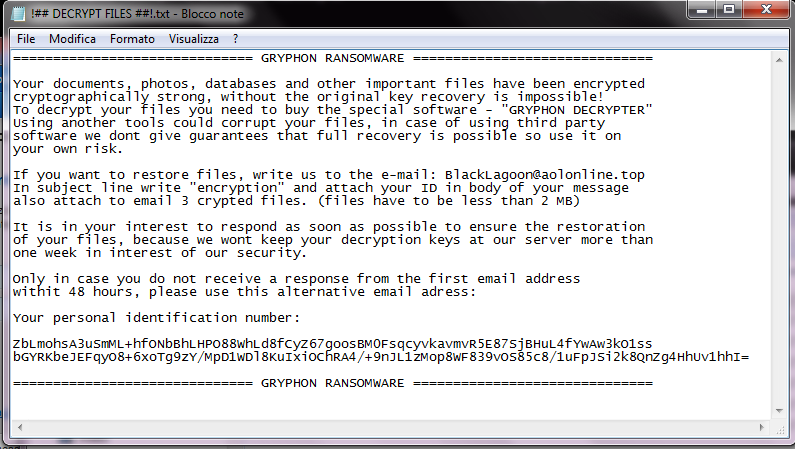
|
Evidence confirming the intrusion
Once verified that the PC could be accessed by remote desktop - a function often
clumsily enabled for technical needs - the Windows event log was then analyzed, particularly in the security section.
To start the Event Viewer with the Windows interface:
-
Click the Start button.
-
Select Control Panel.
-
Click System and Maintenance.
-
Choose Administrative Tools.
-
Double-click Event Viewer.
To start the Event Viewer with a command line:
-
Open a command prompt. To open a command prompt, click the Start button, choose All Programs, Accessories, and then Command Prompt.
-
Type in eventvwr.
When faced with the event/security log, a filter was run for ID 4624, resulting in a list of successful accesses.
Then scrolling through the various filtered rows, especially one was detected that reported an RDP access (access type 10, see img.1 at right) that occurred a few minutes before the files were encrypted. |
|
The IP address (source network address) recorded in the event, does not belong to the corporate network but is located in Russia. (See IMG.2 at right).
In this case, it was easy to find out the details of the intrusion and its origin: the criminal failed to erase his tracks. In other cases analyzed, the event log was found empty or with event lines deleted. |
|
We need to know that once the CyberCriminal gains access to the system, he can potentially:
- Make security systems, including antivirus, defenseless.;
- Run CryptoMalware or other Malware in general;
- Capture credentials saved in mail programs or browsers;
- exfiltrate data;
- Create additional access to the corporate network and/or system.
Useful tips
TG Soft's C.R.A.M. found that in these types of attacks, gross errors are often made in the configuration of the affected machines that facilitate the success of the attack. Before making remote access via RDP protocol possible, we should consider some technical measures including:
- Do not allow RDP access to either the "everyone" group or the "guest" user .
- Set up stricter rules in the firewall configuration to restrict access to only authorized IPs and possibly only at set times.
- Consider for access from outside, VPN technology.
- Use strong passwords and change them regularly (at least every 3 months).
- Limit the maximum number of failed logins per account.
- Prevent users authorized for RDP access from belonging to the "administrators" group.
- Monitor access logs for any suspicious activity.
- Avoid storing passwords for access to other systems in the network.
- Always perform Operating System updates.
It remains critical to have an active and up-to-date antivirus, antispyware, antimalware, and antiransomware solution such as the
Vir.IT eXplorer PRO suite.
C.R.A.M.
TG Soft's Anti-Malware Research Center
Back to top of page


