
09/02/2016
17:38

Starting from 8th February 2016, a new wave of infected emails, carrying a TeslaCrypt 3.0 variant, has been registered by TG Soft's Research Centre (C.R.A.M.). These emails in particular try to imitate DHL invoices. The user is invited to download and open the attachment. By doing so, encryption of local and shared data starts to take place. |
INDEX==> How TeslaCrypt 3.0 works==> The ransom demanded by TeslaCrypt 3.0 ==> How to stay safe from TeslaCrypt 3.0 ==> How to contain TeslaCrypt 3.0 encryption damage ==> Is it possible to decrypt .micro files? |
|
| This encryption is due to a TeslaCrypt 3.0 attack - encrypted files are also renamed with .micro extension, and a ransom is demanded for their decryption. |  |
|
|
This wave of fake DHL invoices have the following subject:
DHL DeliverNow Notification Card on lost shipment (First Notice) orDHL DeliverNow Notification Card on lost shipment (Second Notice) The attachment is a .zip archive contained into another .zip archive, which contains a Javascript file named INVOICE_SCAN_<random>.XLS.js or INVOICE_SCAN_<random>.DOC.js.
Attachment structure: DHL_Notification_card.zip → FILE.ZIP → INVOICE_SCAN_<random>.XLS.js
Javascript files' naming pattern is similar to the following:
The size of DHL_Notification_card.zip is about 2 KB.
The size of the Javascript file is about 5 KB (5,010 byte)
|
Click to show the picture fullscreen |
This only occurs if Vir.IT eXplorer PRO is:
Starting with version 8.0.98, Vir.IT eXplorer PRO can "snatch" TeslaCrypt 3.0 encryption key on-the-fly in the early stages of the attack, thus making a decryption feasible - it can be done with the assistance from TG Soft's tech support.
Remember - every time the malware is executed, a new encryption key is used. This means that every time the computer is rebooted and the malware is still active, TeslaCrypt will use a different key (n reboots → n+1 different keys).
Since a new key is created every time the malware is executed - which only happens when the computer is rebooted - the computer should always stay turned on, in order to have the minimun number of keys possible, and qualified tech support (such as TG Soft's) should be contacted immediately.
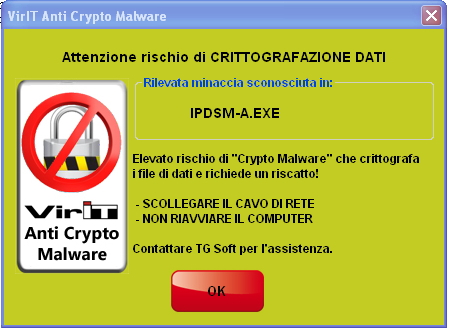
When the Alert shown in the picture pops up on the screen, Vir.IT eXplorer PRO's Anti-CryptoMalware module has come into action, halting the malware. Do not panic and perform these operations:
In case of cryptomalware attack you should get in touch with Vir.IT eXplorer PRO's Tech Support as soon as possible. You can write an email to assistenza@viritpro.com, or call +39 049 631748 - +39 049 632750, Mon-Fri 8:30-12:30 and 14:30-18:30.
|
 Click to show the picture fullscreen 99,63%* Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO |
| We invite you to be very careful when opening email attachments. If you are not waiting for a parcel then you really shouldn't open emails like the one we analyzed. Always double-check the sender's email address (which is not the sender's name) before opening an attachment: in our sample email there is a mismatch between the name and the address: SENDER:
DHL DeliverNow Network ljjzwctwhs@kabulwala.com Note that the email address is totally random and is not related with DHL. This also applies to other fake invoices. |
 Click to show the picture fullscreen |