
14/03/2016
16:44
Statistics viruses/malware in February 2016 in Italy
Every month C.R.A.M. TG Soft analyze circulating virus/malware in Italy.

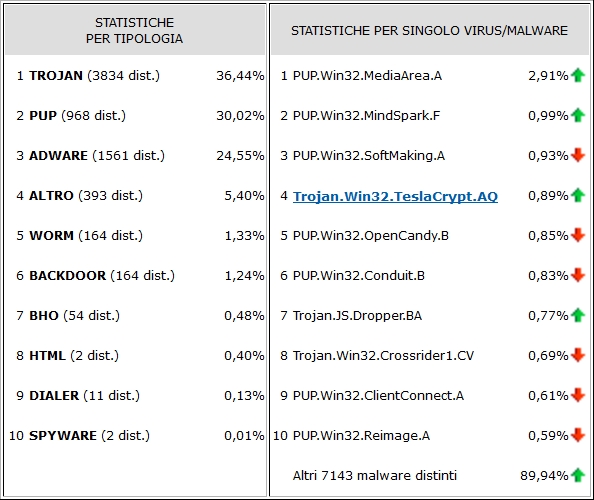
| The C.R.A.M. (Anti-Malware Research Center) of TG Soft has released statistics of actually circulating virus/malware in February 2016 in Italy. Let's find out what are the families and variants of malware that infected users' PCs. |  |
 Click per ingrandire |
Analyzing the statistics shown on the left you can see how the Trojan family is definitely the most widespread malware family and right after, as for many months now, there are two categories that include advertising programs: ADWARE and PUP. It's always advisable to check the actual usefulness of the software that you download from the Internet: they are often passed off as only existing solution to solve any problems. In truth, when used, they create more damage and worsen the situation. |
|
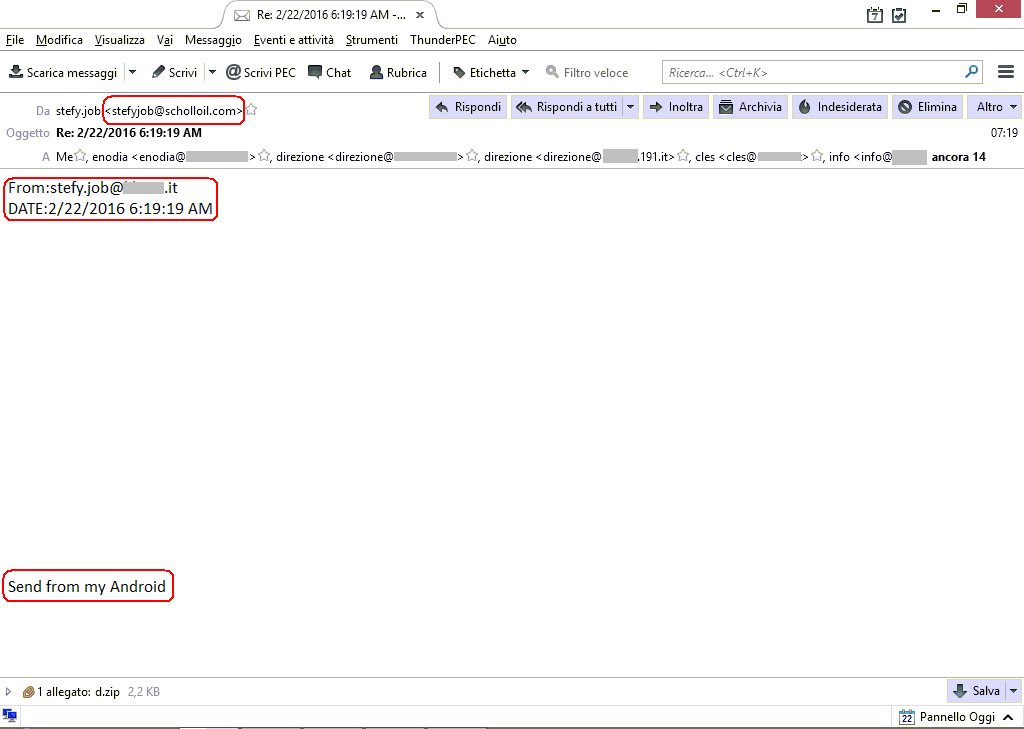
For the spread of Teslacrypt were used email scam (like the one you can see on the right) containing zipped file (in our example d.zip). Within that archive is hidden javascript that if extracted and executed, it downloads and executes the file cryptomalware.
It's possible to see more details on the samples of the Teslacrypt.AQ collected from C.R.A.M. of TG Soft viewable in the table at the following link: sample table Teslacrypt.AQ |
 |
Among the really circulating virus / malware that spread via email in this month C.R.A.M. of TG Soft has analyzed numerous incidents of scam emails containing fake attachments (such as invoices, delivery notes etc ...). We analyze the reports arrived
| CAs expected after the massive spreading campaign of Teslacrypt in February 2016, among the first positions are present Trojan.JS.Dropper with variantBA and BC. However, here we find the fake invoices and / or intercepted documents by Vir.IT eXplorer as Trojan.Win32.Dropper with variants TV, UC and TX. These malware are always spread with email "lark" where is indicated to open the attachement or download it from some website. |
|
As we can see from the rankings there's the PUP.Win32.OOO.Q that, although reported as Potentially Unwanted Program, which is an advertising program, it is a Trojan.Win32.CTBLocker which is another cryptomalware.
Almost certainly the creators of malware have stolen the digital signature to a software house that produces advertising programs and they use in turn to digitally sign illegally numerous samples of cryptomalware. |
| We point out that all the viruses / malware actually circulating are identified and, in many cases, also removed from Vir.IT eXplorer Lite -FREE Edition- that TG Soft makes freely used by both individuals both within the company. Vir.IT eXplorer Lite is interoperable with other AntiVirus already on your computer, without having to uninstall, and then allowing the cross-check that nowadays is no longer a whim, but a necessity. Go to the download page. |  |