| Here are the most common phishing emails, acknowledged during the last week of March 2016 by TG Soft's Research Centre. The main goal of these emails is to trick the receiver into giving their credit card and bank account details. |
|
INDEX
|
29/03/2016 ==> Fake email from Barclays
A new wave of emails prompts the user to verify and "certify" the email address paired with a bank account; in our case the emails bear the Barclays' logo (please note that Barclays banking company IS NOT responsible for this wave of emails). The user is somehow warned to do said operations before a 24h deadline, implicitly threating the block of the account if the deadline is not met.
These are phishing emails, whose goal is to obtain (or better, steal) sensitive data such as bank account credentials. This is what these emails look like.
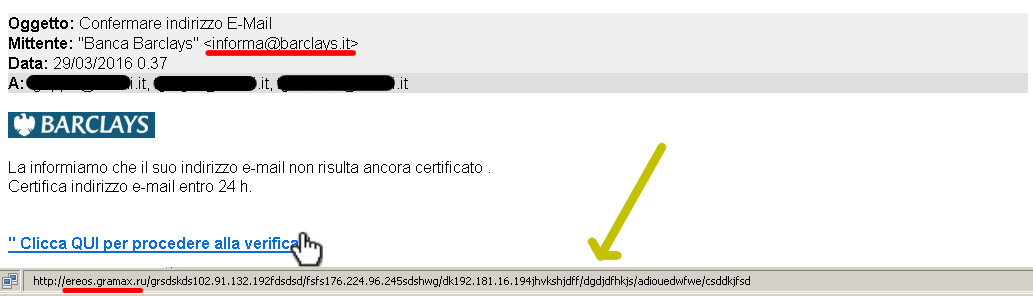
Translation of the email
Subject: Confirm your email address
From: "Barclays Bank" <informa@barclays.it>
Date: 29/03/2016 0.37
To: <recipient's address>
We inform you that your email address has not been certified yet.
Please certify your email address within 24 hours.
"Click HERE to proceed with verification"
Please note that the web address that can be read hovering the mouse over the link is not even closely related do the banking company: it points to a website hosted on a Russian server.
By clicking on the link, the user is redirected to a webpage which is similar to those ones used to log into banking portals; but this is a fake webpage, created to store user-inserted data in order to steal bank account credentials.
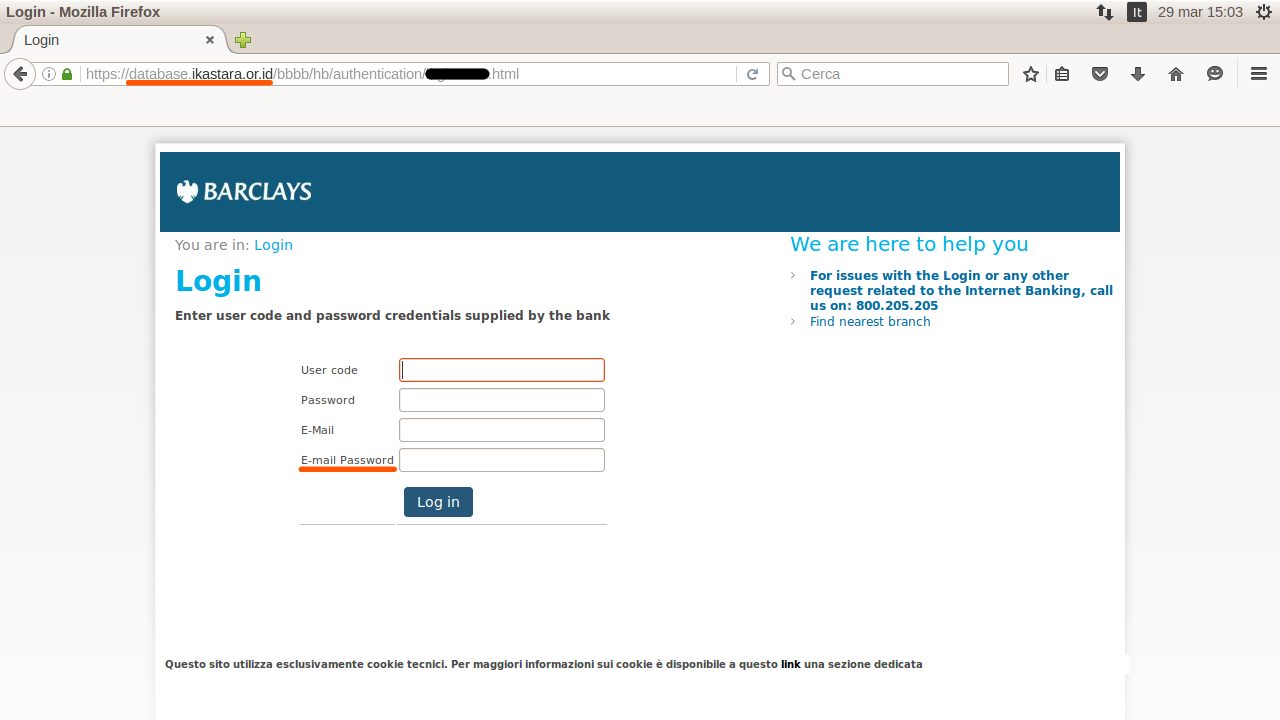
Again, pay attention to the address in the navigation bar: the address is not related to the bank in this case either. This should be an important warning sign!
Furthermore, among the standard credentials needed to log into the bank portal, the email account's password is also required: one has to become suspicious since a bank should not be interested in knowing such information - and in this case there is the risk of email account theft.
30/03/2016 ==> Fake email from PayPal
Also in this case the user is asked to validate their bank account credentials.
The email seems to come from
PayPal, the notorious online payment system, and invites the user to download the attached form and to fill it out.

Translation (please note that the email has been
purposely translated with incorrect grammar, since the original ones were not grammatically correct either).
Subject: Your online PayPal account has been frozen !
From: PayPal Italia <sicurezza@it.paypal>
Date: 30/03/2016 11.00
To: *****@***.**
Dear customer,
for security reasons your account has been blocked.
Following unusual activities, we have come to the conclusion that
someone has used your card without your permission,
for your safety, we blocked your account.
To unblock your account download the attached document fill in the form and follow the steps to update your credentials.
Note : If you don't update your cretentials your card will be suspended.
[...]
The attached HTML file, once opened, will look like this one below.

The required fields are email address; PayPal password; name and surname; date of birth; home address; city; province; ZIP code; telephone number; debit/credit card number; expiration day and month; CVV; One-Time-Password; fiscal code.
By carefully reading the code of the form, by clicking
Accetta e Invia ("Agree and Submit") the values will not be sent to
PayPal. Instead they will be processed by a PHP script loaded on a website that has nothing to do with
PayPal.
Once
Accetta e Invia is pressed, all the bank account information will be made available to the criminal organization that created the scam.
Be attentive to avoid troubles...
Every major banking company has published bulletins stating that emails prompting the user to validate and confirm their banking account credentials should be distrusted, since these companies do not operate in such way.
In order to avoid credentials theft, it is recommended to:
- enable Vir.IT WebFilter Protection, if you are a Vir.IT eXplorer PRO licencee. This can be done from the setting tab in Vir.IT eXplorer PRO, by unchecking Disable Vir.IT WebFilter Protection and rebooting the system. This module, once activated, will block infected and dangerous websites, and it is kept up-to-date in order to stop users from visiting malicious pages. WebFilter Protection is included with Vir.IT eXplorer Lite (it works with Internet Explorer only) and Vir.IT eXplorer PRO (it works with every web browser).
- Distrust special offers received via email.
- In cases like these ones, validate the credentials by manually going to the bank's webpage and personally typing the address and not by clicking the link contained in emails.
- Do not trust emails that require the insertion of sensitive data in webpages attached to an email.
For further information, check our bulletin:
Phishing: always present danger.
| Every known malware can be identified and, in most cases, removed by Vir.IT eXplorer Lite -FREE Edition-, freely made available by TG Soft for both private and corporate sectors. Vir.IT eXplorer Lite is interoperable with any AntiVirus that should be already installed on a PC, without the need to be uninstalled, thus allowing an useful cross check. Visit the download page. |
 |
TG Soft
Anti-Malware Research Centre (C.R.A.M.)



