How Saraswati CryptoEncoder works
|
The means of distribution of the Trojan.Win32.CryptoEncoder Saraswati are unknown, probably it is spread via tainted websites whose vulnerabilites in Java, Adobe Flash Player and Adobe Reader have been exploited.
Trojan.Win32.CryptoEncoder Saraswati comes in the form of an executable file, called saraswati.exe, which is copied inside the user's roaming folder: %user%\appdata\roaming\:
- FILENAME: saraswati.exe
- SIZE: 114688 byte
- MD5: 67f54ddc01178bb5878fe14a567813fc
Name of the project file found inside the cryptomalware: C:\crysis\Release\PDB\payload.pdb |
|
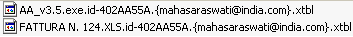
The Saraswati CryptoEncoder encrypts document files (such as .doc, .xls. .ppt, .jpg, etc) and binary files (such as .exe, .dll, etc) alike, and adds to their name the extension:
".id-????????.{mahasaraswati@india.com}.xtbl". |
 |
Trojan.Win32.CryptoEncoder Saraswati autostarts itself adding the following Windows Registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
[lttmrsuc] = %windir%\System32\Saraswati.exe
Istructions about how to pay the ransom are also automatically run after logging in:
%user%\Start Menu\Programs\Startup\Saraswati.exe
%user%\Start Menu\Programs\Startup\How to decrypt your files.jpg
%user%\Start Menu\Programs\Startup\How to decrypt your files.txt
On the user's desktop the following file is copied:
%user%\Desktop\How to decrypt your files.txt
On the user's folder the following file is copied:
%user%\How to decrypt your files.jpg
The ransom demanded by Saraswati CryptoEncoder
In order to know the details about the ransom, one must send an email to mahasaraswati@india{dot}com, as stated in the instruction files.
At the end of the encryption process, the Saraswati CryptoEncoder creates two instruction files with the details on how to pay the ransom where it operated:
- How to decrypt your files.txt
- How to decrypt your files.jpg
To decrypt your data write me to mahasaraswati@india.com
|
We wrote an email to said address and the following is their reply.
Good morning, dear friend!
We are writing to inform you that our team of network security specialists has analyzed your system and has identified vulnerabilities in the protection.
We kindly draw your attention that defensive operation on your computer is not running properly and now the whole database is at risk.
All your files are encrypted and can not be accepted back without our professional help.
Obviously vulnerability analysis, troubleshooting, decoding the information and then ensuring safety are not a simple matter.
And so our high-grade and quick service is not free.
Please note that today the price of your files recovery is 3 Bitcoins, but next day it will cost 5 Bitcoins.
You should buy bitcoins here https://localbitcoins.com/faq
Read the paragraphs:
1. How to buy Bitcoins?
2. How do I send Bitcoins and how can I pay with Bitcoins after buying them?
The Bitcoin wallet for payment is 1DGMeKSALSkYGkedYDUgcvV8mP77WEGusQ
After the transfer of bitcoins please send email with screenshot of the payment page.
We does not advise you to lose time, because the price will encrese with each passing day.
As proof of our desire and readiness to help you, we can decipher a few of your files for test.
To check this you can upload any encrypted file on web site dropmefiles.com, size no more than 10 MB (only text file or a photo) and send us a download link.
Certainly after payment we guarantee prompt solution of the problem, decrypt the database to return to its former condition and consultation how to secure the rules of the system safety.
Kind regards, Saraswati. |
How to stay safe from Saraswati CryptoEncoder
The current version of Vir.IT eXplorer PRO's Anti-Ransomware (the heuristic-behavioural automaton) can already halt Saraswati CryptoEncoder in the early stages of the encryption.
It has been stated stated in our previous bulletins that
Vir.IT eXplorer PRO's Anti-CryptoMalware module was able to stop these attacks saving up to 99.63% of files, allowing a complete recovery of encrypted files thanks to backup technologies, namely:
- On-The-Fly Backup;
- Vir.IT BackUp.
This only occurs if
Vir.IT eXplorer PRO is:
- correctly INSTALLED;
- UP-TO-DATE;
- properly CONFIGURED - Anti-Crypto Malware technology has to be active in the Settings tab of Vir.IT Security Monitor (it is active by default); plus Vir.IT BackUp has to be configured and running.
How to minimize Saraswati CryptoEncoder damage
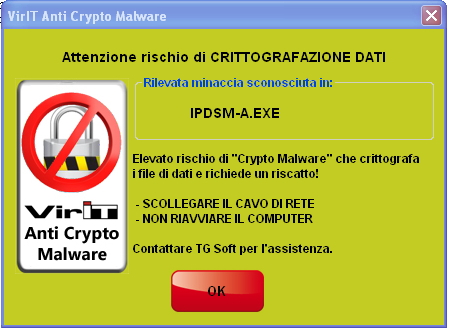
When the Alert shown in the picture pops up on the screen, Vir.IT eXplorer PRO's Anti-CryptoMalware module has come into action, halting the malware. Do not panic, do not close the alert and perform these operations:
- Make sure that Vir.IT eXplorer PRO is UP-TO-DATE and if not proceed to UPDATE it.
- UNPLUG ETHERNET and/or EVERY NETWORK CABLE - by doing this, the computer will be phisically isolated from the network, thus containing the attack inside just one machine.
- PERFORM a FULL SCAN using Vir.IT eXplorer PRO.
- DO NOT REBOOT OR TURN OFF THE COMPUTER in order to avoid further encryption.
In case of cryptomalware attack you should get in touch with Vir.IT eXplorer PRO's Tech Support as soon as possible. You can write an email to assistenza@viritpro.com, or call +39 049 631748 - +39 049 632750, Mon-Fri 8:30-12:30 and 14:30-18:30.
|
Show the picture fullscreen
99,63%*
Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO
|
Can I recover the encrypted files?
With the Anti-CryptoMalware protection given by VirIT, the files encrypted by
Saraswati CryptoEncoder rarely will exceed eight units.
Lost files will have to be replaced with backup copies. One can also try some existing tools to recover the encrypted files with the extension
.id-????????.{mahasaraswati@india.com}.xtbl.
In the analysis carried out by the Research Centre,
shadow copies could not be recovered since they had been deleted by the ransomware.
Final thoughts
In the eventuality of an ecryption, you could either:
- have Vir.IT eXplorer PRO installed, correctly set up, up-to-date and running on your pc - in this case, you must follow the instructions on the Alertmessage and you will manage to save AT LEAST 99.63% of your data;
- have a AntiVirus software that doesn't detect, signal and halt the ongoing encryption - in this case you still may want to
- UNPLUG EVERY NETWORK CABLE.
- LEAVE YOUR COMPUTER TURNED OFF in order to minimize the number or encrypted files.
- Get in touch with a trusted technician support telling the criticity of the situation; you can also refer to this bulletin.
In the case #1, where thanks to Vir.IT eXplorer PRO and its Anti-Ransomware technologies you are almost totally sure to save up to 100% of your data from encryption, we strongly invite you to get in touch with TG Soft tech support.
In the case #2, we can only invite you to stay calm and seek for trusted tech support and consider buying a Vir.IT eXplorer PRO licence in order to prevent these attacks.
TG Soft
Anti-Malware Research Centre



