The new variant of Petya Goldeneye spreads through e-mails. The spam campaign which has been observed starting from the 6th of December hit mainly the german market and, like all previous cases, the e-mail still refers to recruitment possibilities. In this case the e-mail was a candidacy for a work place in the production of optoelectronic devices.
The subject of the e-mail can have the similar form:
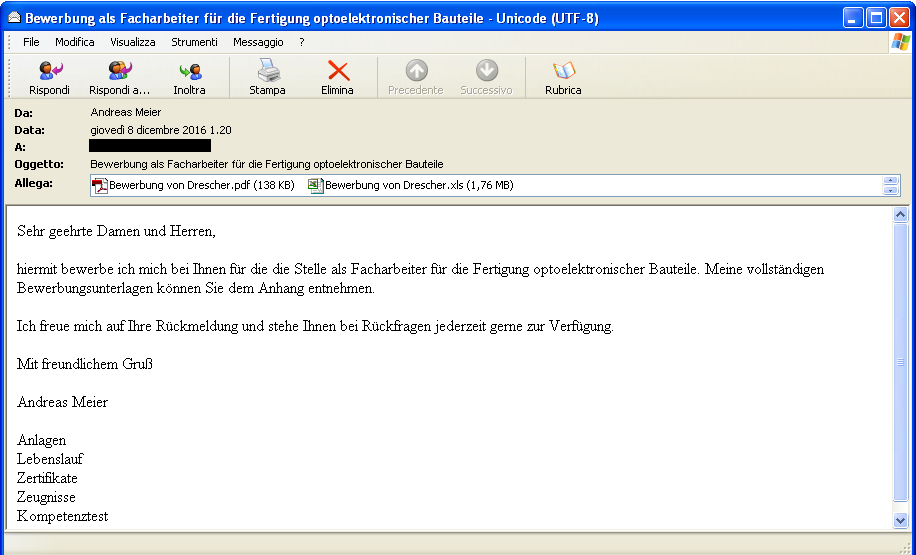
Bewerbung als Facharbeiter für die Fertigung optoelektronischer Bauteile
|
Click to enlarge |
Message body:
Sehr geehrte Damen und Herren,
hiermit bewerbe ich mich bei Ihnen für die die Stelle als Facharbeiter für die Fertigung optoelektronischer Bauteile. Meine vollständigen Bewerbungsunterlagen können Sie dem Anhang entnehmen.
Ich freue mich auf Ihre Rückmeldung und stehe Ihnen bei Rückfragen jederzeit gerne zur Verfügung.
Mit freundlichem Gruß
Andreas Meier
Anlagen
Lebenslauf
Zertifikate
Zeugnisse
Kompetenztest |
The message infected by Petya contains 2 attachments:
- Bewerbung von Drescher.xls (size: 1804800 byte, MD5: FEF25AFCCEBE63858C093CB716D03203)
- Bewerbung von Drescher.pdf (size: 138540 byte, MD5: 16E41EBD9414E9327E9D447E4B5A6FE4)
The Bewerbung von Drescher.xls file contains Excel macros which create and run from the %temp% folder the following file:
Name: rad0A3AB.exe
Size: 368640 byte
MD5: 08828DAF9A027E97FEE2421AC6CBC868
Running Goldeneye: Mischa ransomware
Opening the
Bewerbung von Drescher.xls file with the macros activated will result in the running of the
rad0A3AB.exe file from the %temp% folder.
In this first fase the Mischa ransomware will run, encrypting all document files inside the c:\user(%user%) folder of Windows.
The encrypted documents will be renamed by adding a new casual extension of 8 random characters, for example:
Sheet1.xlsx ==> Sheet1.xlsx.rCazhYJU
The Mischa ransomware will release in every subfolder of the %user% folder the file "YOUR_FILES_ARE_ENCRYPTED.TXT" with the following ransom instructions:
You became victim of the GOLDENEYE RANSOMWARE!
The files on your computer have been encrypted with an military grade encryption algorithm. There is no way
to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy steps:
1. Download the Tor Browser at "https://www.torproject.org/". If you need help, please google for
"access onion page".
2. Visit one of the following pages with the Tor Browser:
http://golden5a4eqranh7.onion/rCazhYJU
http://goldeny4vs3nyoht.onion/rCazhYJU
3. Enter your personal decryption code there:
rCazhYJUF1pRVywmEsuUey9LrqMAAQ4yYrdeoNHB93eikeexJNBjaRL64UWfNG6PNSo9us5v9[..] |
Running Goldeneye: Petya ransomware phase 1
 After Mischa
After Mischa ransomware has finished the encryption of the document files inside the %user% folder,Goldeneye will run the Petya ransomware.
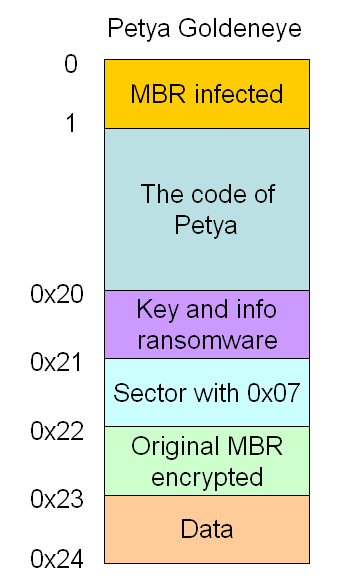
The dropper of Petya (rad0A3AB.exe) is able to bypass the intermediate level of the User Account Control (UAC), infecting the Master Boot Record of the hard drive by overwriting the first 36 sectors, as represented in the following scheme ==>
The sector 0 of the MBR is infected by the Petya loader code and, as we can see in the following image, the length of this code is of 147 byte.
From sector 1 to 0x20 we can find the viral code of Petya.
|
 |
Interesting is the sector 0x20:
This sector is structured in this way:
- Off. 0x00 (1 byte): disk status
- 0: disk to encrypt
- 1: encrypted disk
- 2: decrypted disk
- Off. 0x01 (32 byte): key used for encryption
- Off. 0x21 (8 byte): initializing vector for the encryption
- Off. 0x29 (128 byte): Tor-Onion addresses for the payment of the requested ransom
- Off. 0xa9 (90 byte): Victim's ID
|
Sector 0x21, during the first phase, is only filled with the byte 0x07.
This sector however will be encrypted during phase 2 and during the 3rd and final phase it will be used to ensure the correction of the key.
|
 |
Sector 0x22 contains the Master Boot Record encrypted with either xor 0x07 as we can observe in the following image.
Sector 0x23, during this phase only contains 0.
|
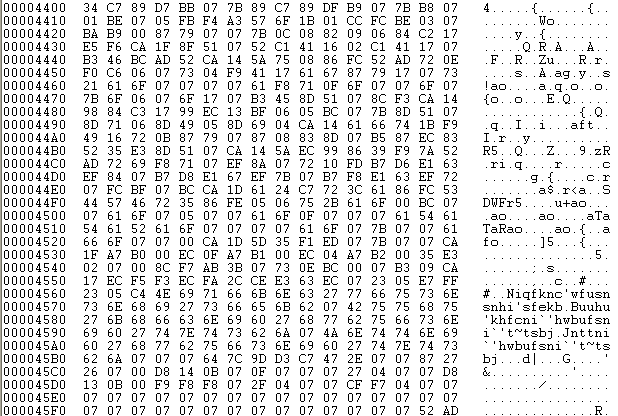 |
At the end of this phase, Petya Goldeneye simulates the BSOD (Blue Screen of Death)
Petya Goldeneye during phase 1 hasn't yet started to encrypt the Master File Table (MFT) but it has solely infected the Master Boot Record. In case of BSOD, If the automatic restart service of the computer has been disabled, the machine freezes and it only displays the fake BSOD error.
If we find ourselves in this situation with the BSOD error it is possible to shutdown or restart the computer with a bootable CD/DVD of Windows in order to run "fixmbr" and remove Petya from the Master Boot Record.
Otherwise, if the computer is manually restarted or it has restarted automatically, then the bootloader of the Petya infected MBR will run, initializing the 2nd phase of the Master File Table encryption.
Running Goldeneye: Petya ransomware phase 2
The second phase of
Petya begins from the first boot, the MBR code gets loaded at address 0:7c00. The infected MBR by
Petya reads 0x20 sectors starting from sector 1 and loads them at address 0:8000.
If the fist byte of the sector 0x20, i.e. that of the field "disk state" has 0 as value then it will start the encryption procedure of the Master File Table of each partition of the disk.
The encryption algorithm used is still Salsa20; here we can see the initialization routine of the input array of Salsa20:
During this phase Petya views a fake chkdsk which in reality is only encrypting the Master File Table. The viewed percentage indicates the portion of the encrypted Master File Table.
During this phase, the 0x20 sector gets updated:
The first byte of the 0x20 sector gets updated with the value 1 (encrypted disk) and the 32 bytes of the encryption key get canceled with zeroes. The initialization vector remains intact with an 8 byte value.
| On the other hand, sector 0x21 will also result encrypted, as we can see in the following image: |
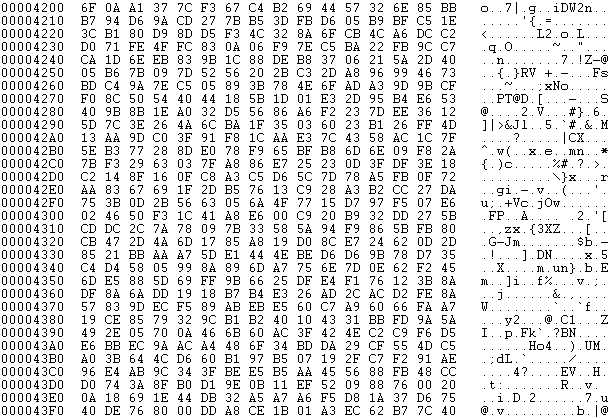 |
| In sector 0x23 we can find the number of encrypted clusters, as we can see in the following image: |
 |
At the end of phase 2 of the MFT encryption, the computer will be automatically restarted by Petya.
Running Goldeneye: Petya ransomware phase 3 ransom request
During the following boot,
Petya reads sector 0x20 and, if the first byte ("disk state") has value 1 then the skull of Petya will be viewed alternating the colors yellow and black.
The image of the skull (drawed with ASCII characters) will flicker between the two images:
By pressing any key, we will be notified that we are victims of GOLDENEYE RANSOMWARE:
Petya Goldeneye indicates the .onion sites on which the payment of the ransom should be carried out and the victim's ID.
At this point
Petya remains idle until the decryption key for the MFT is inserted.
The key that has to be inputed is a string of 32 characters taken from the following set:
0123456789abcdef
From this 32 character key, Petya will make further operations in order to obtain a new and final 32 byte key.
Petya, in order to verify the correctness of this last generated 32 byte key, obtained from the typed one, will attempt to decrypt the sector 0x21. If each byte of the sector after the decryption has the value 0x07, then the key which has been previously inserted is correct and will proceed to decrypt the MFT.
Conclusions
This new version of Petya Goldeneye has doubled it's ransom request in order to re-obtain the usability of our PC first and of our files secondly:
- Petya encrypting the MFT asks for a ransom in order to decrypt it;
- Mischa encrypts data files and asks for another ransom in order to decrypt them.
In previous versions of Petya the encryption of the MFT was successful only in case the dropper was ran with Administrator priviledges, otherwise it resulted in the encryption of the document files through the Mischa ransomware.
This new release first chain runs the Mischa ransomware and after that it's capable of by-passing the intermediate level the User Account Control (UAC) infecting the Master Boot Record.
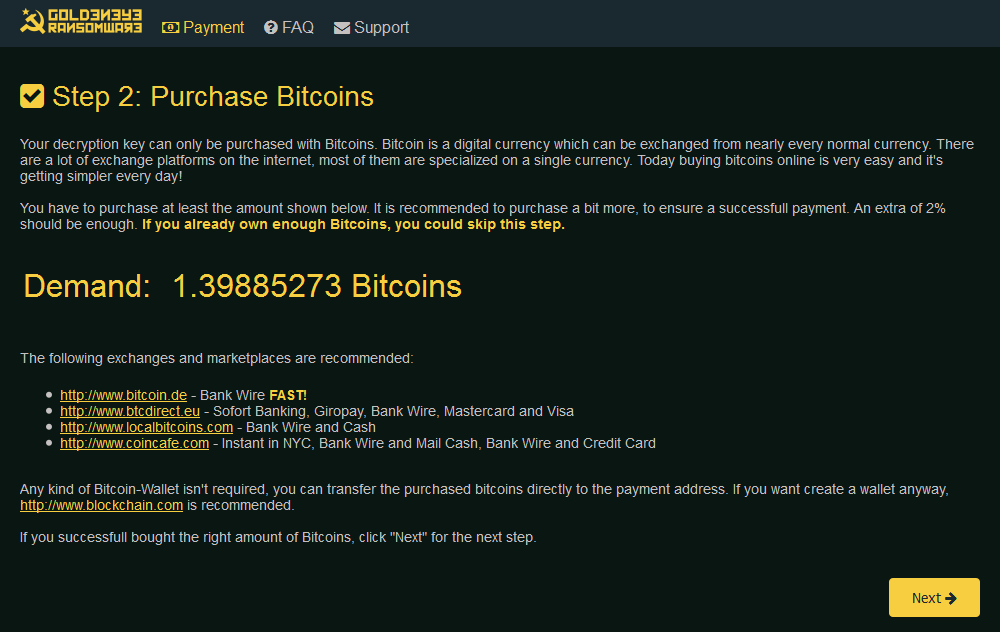
The unfortunate victim will be facing the following situation in which he or she will have to pay both the ransom for the decryption of the Master File Table and for the decryption of the data files ciphered by Mischa. In our test the ransoms requested were of 1,39 and 1,32 Bitcoin respectively, as indicated in the two images below:
|
Petya:
|
Mischa:
|
Petya's evolution
| Name |
Date |
Notes |
| Petya 1. 0 Red version |
March 2016 |
It's possible to decrypt the MFT with genetic or metaeuristic algorithms such as "Cuckoo Search" |
| Petya 2.0 Green version + Mischa |
May 2016 |
Petya or Mischa get run.
It's possible to decrypt the MFT through Brute Force (num. of combinations 548) |
| Petya 3.0 Green version + Mischa |
July 2016 |
Petya or Mischa get run.
It's possible to decryopt the MFT during phase 1. After this phase it becomes impossible to decrypt the MFT. |
| Petya Goldeneye Yellow version + Mischa |
December 2016 |
First, the data files are encrypted by Mischa, afterwards the MBR gets infected bypassing the intermediate level of the UAC.
It's possible to decrypt the MFT during phase 1. After this phase it becomes impossible to decrypt the MFT. |
As previously mentioned, the creator of
Petya likes to call himself
Janus.
