the body of the message has the following form:
Spett. le COMUNE,
si richiede cortesemente certificato storico di residenza
del soggetto con dati allegati, per accertamento irreperibiità.
Si ringrazia.
Cordiali saluti
Il Segretario Comunale
<nome della persona>
Comune di <nome del comune>
<indirizzo>
<recapiti telefonici>
|
Attachments:
- Dati_Anagrafici_Per_Accertamento_Irreperibilita_ DE_JESUS_MILAGROS-BEROYA-FILIPPINE_ RP-DJSMGR73S51Z216Z.rtf.zip
- Anagrafica.rtf.zip
The attachments have a double extension: .rtf.zip
Inside the respective zip file is present a file with name: <nome file zip>.rtf.vbe
example: Anagrafica.rtf.vbe
Filename: Anagrafica.rtf.vbe
Size: 7.589 byte
MD5: 5D429355B4510AECFE27723FAFC6EAB2
Date: Tuesday 28 Febraury 2017, 23.28.04
The file <nome file zip>.rtf.vbe is a VBScript file that is identified by VirIT eXplorer as infects by "Trojan.VBS.Orziveccho.D".
The email infected by "Orziveccho" are sent from the following pec addresses:
- comunediburgio@pec.it
- info@pec.comune.sanvittoredellazio.fr.it
The municipalities in which the credentials of institutional PEC were compromised are:
- Comune di Burgio
- Comune di San Vittore del Lazio
From the analysis of the infected email, the IP addresses from which the infected mail were shipped may be located in Tallinn in Estonia, or in USA:
- 104.160.19.236
- 104.160.19.111
These IP addresses belong to the American provider CachedNet LLC, through the geolocation of the IP addresses they are located in Estonia or in USA.
Both the City of Burgio and the City of "San Vittore del Lazio" are working to solve the problem of compromised accounts.
The City of Burgio has signaled inside its website the problem related to sending of infected emails:
Running of Orziveccho
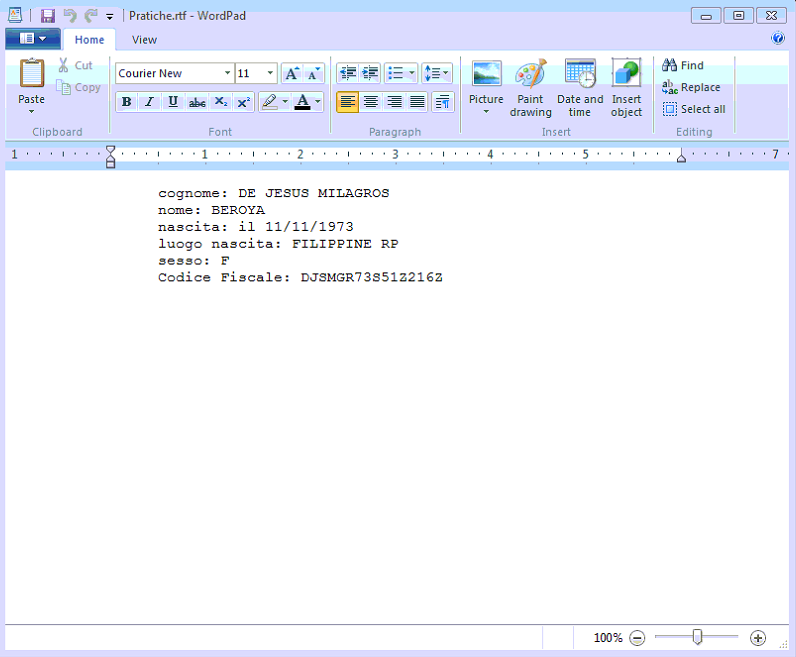
The r
unning the infected VBScript creates inside the folder "Documents" the file "Pratiche.rtf" with the request information:
At this point it is created "download.vbe" file in the Startup folder and then executed.
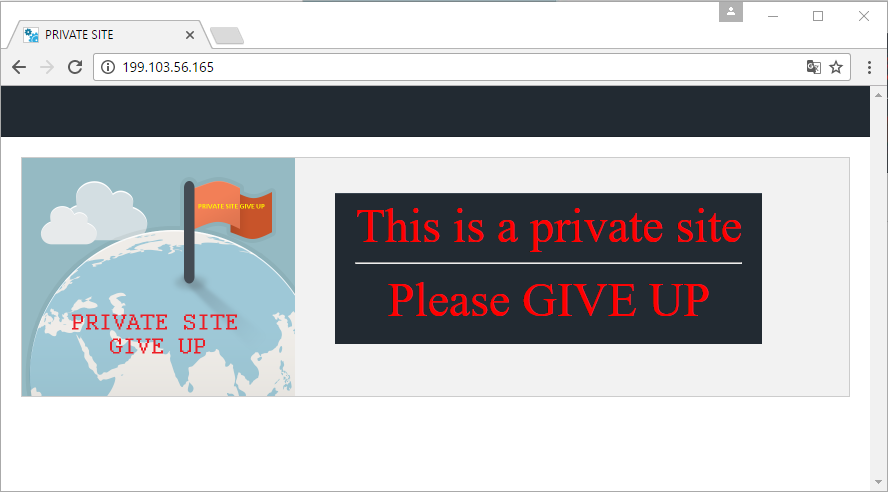
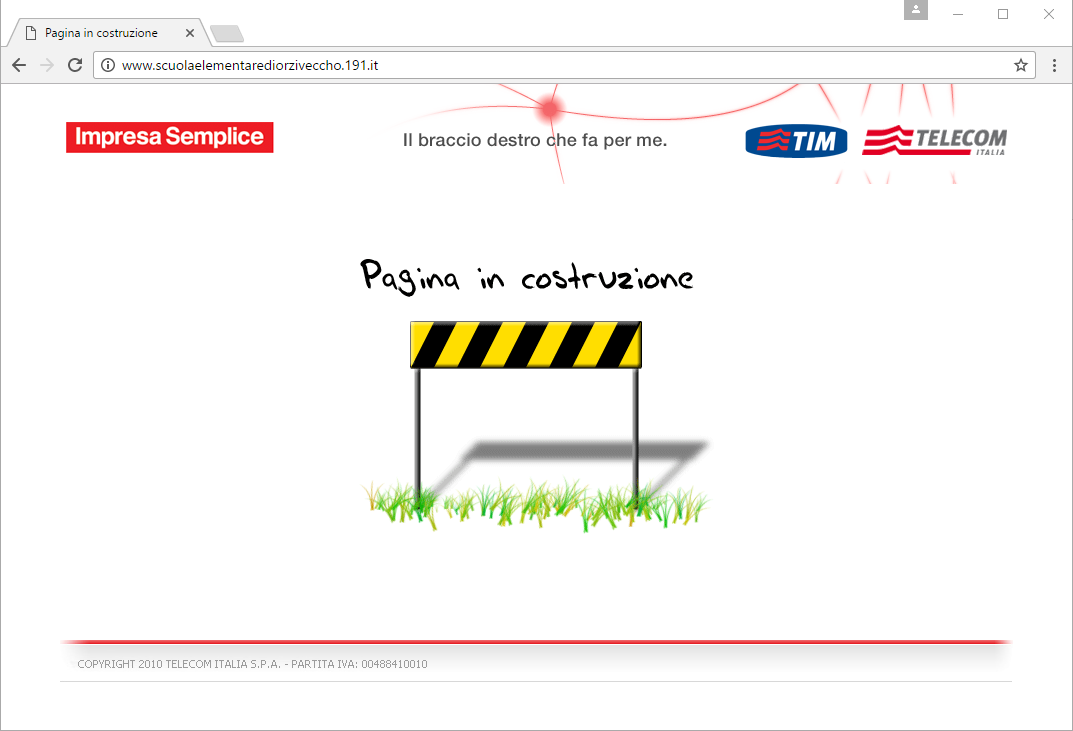
The file "download.vbe" tries to connect at the following domains:
- 199[.]103[.]56[.]165
- www[.]scuolaelementarediorziveccho[.]191[.]it
The first domain
199[.]103[.]56[.]165 is localized in Toronto (Canada), instead the second
www[.]scuolaelementarediorziveccho[.]191[.]it is localized in Italy and is a domain registered by
Tim Telecom Italia.
|
199[.]103[.]56[.]165
|
www[.]scuolaelementarediorziveccho[.]191[.]it
|
 |
 |
These domains are used as C&C server to donwload a file called "
ORD-2020.txt", it contains the payload of malware.
Filename:
ORD-2020.txt
Size: 3.309.187 byte
MD5: 271CA65D23F0DB9044E0F5B166FDD462
On 09/03/2017:
Filename: ORD-2020.txt
Size: 3.309.196 byte
MD5: D70CD766BD0796CFFCF3E32C5A8F9DAE
The file "ORD-2020.txt" is saved inside the startup folder under the name "ORDINI.exe".
The file "ORDINI.exe" is a self extract RAR and it is identified by VirIT eXplorer as infects by "Trojan.Win32.Orziveccho.A"
Inside the file "ORDINI.exe" we cann find the following file:
- admin.vbe
- NTR.msi
- vai.vbe
Filename:
admin.vbe
Size: 3.491 byte
MD5: DB5E6722916387E4968994C90A78C530
Filename:
NTR.msi
Size: 3.872.768 byte
MD5: EC857EED2FFE74BE892E373312C20470
Filename:
vai.vbe
Size: 3.346 byte
MD5: 93AF69B1F0D73589CB87E8E5586CEC73
On 09/03/2017:
Filename: NTR.msi
Size: 3.872.768 byte
MD5: D205DAF0F8DF73F59C06091B4DCA76F3
Running the file "ORDINI.exe" involves the extraction of the above files and execution of VBScript files "vai.vbe". This file checks if your computer is already infected, otherwise run the "admin.vbe" file.
The file "admin.vbe" installs the package software NTR.msi with command:
msiexec.exe /package NTR.msi /quiet
that involves the silent installation of the software NTR.msi.
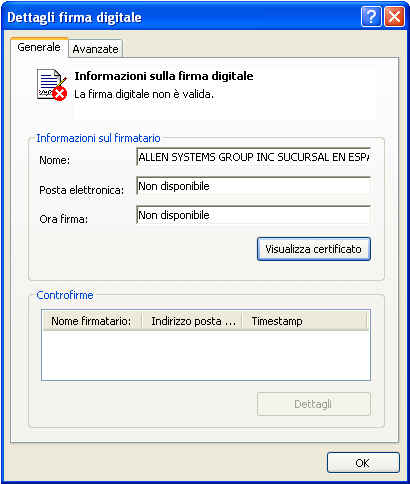
Inside the package NTR.msi you will find the software NTR Cloud (http://www.ntrglobal.com) for remote control of the PC, this package has been modified to match each installation infects with the account of the criminal who assumed to be: michel.piccoli@hotmail.com
In this way the criminal can connect at the site http://www.ntrglobal.com/it/freecloud/login with their credentials and he has the control of each infected computer.
| The package NTR.msi has been modified to match every infected computer with the criminal account, as you can see from the digital signature. |
 |
The remote control software will be installed as a service:
Filename: NTRCloud
Description: NTR Cloud agent
Path: "C:\Program Files\NTR Global (an ASG company)\NTRCloud\agent.exe" NTRCloud
At this point at startup the computer will run the file:
- download.vbe
- C:\Program Files\NTR Global (an ASG company)\NTRCloud\agent.exe
Back on top
Command & Control
The victim's computer is controlled by the attacker through the service of "NTR Global" "C: \ Program Files \ NTR Global (an ASG company) \ NTRCloud \ agent.exe".
During the installation of the software "NTR Global" it is automatically matched to the account of the criminal. The attacker by logging on to http://www.ntrglobal.com/it/freecloud/login will have access to the computers of their victims to spy or steal confidential documents.
At startup it will run the file "download.vbe", that it will try to connect to:
- 199[.]103[.]56[.]165
- www[.]scuolaelementarediorziveccho[.]191[.]it
Here a simple communication system with C&Cl server, as well as performing a direct "upgrade" of the malware, it lets you to download "custom update" according to the following scheme: userName & separ & computerName & "/ORD-2020.txt" .
Where:
- userName: user name
- separ: "--"
- computerName: computer name
Back on top
Remove Orziveccho
To see if the computer is infected by malware Orziveccho you can download the free version of VirIT eXplorer Lite: http://www.tgsoft.it/italy/download.asp
You can manually check for the presence of some infection indicators:
File:
- C:\Users\<nome utente>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Download.vbe
- C:\Program Files\NTR Global (an ASG company)\NTRCloud\agent.exe
Service:
Manual remove:
- delete the file: C:\Users\<nome utente>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Download.vbe
- stop and disable the automatic start of service: NTRCloud
To access at the services from "Start-> Run":
services.msc
Back on top
Conclusions
The campaign of spear phishing of the malware "Orziveccho" with the target the italian municipalities seems to have been well organized. Between Saturday 4th and Tuesday 7th march, there was a massive sending of spear phishing emails with the subject of the message "Richiesta certificato" where both the sender and the recipient were Italian municipalities.
The information contained in the body of the message about the sender, as the name of the municipality, address and contact person are real. This makes us think that the attack was well thought out and no detail has been left to chance.
Could make suspicious the certificate request for the person with the name "DE JESUS MILAGROS BEROYA" (the miracle of Jesus), although in the second email the attachment name was "Anagrafica.rtf.zip" and related to "DE JESUS MILAGROS BEROYA" was shown only in "pratiche.rtf "document to already occurred infection.
What are they looking for in the Italian Municipalities computer? Who is the director of this espionage attack?
For now we do not have enough information to answer these questions.
From the analysis of IP addresses we obtained the following geographic features:
- Italy
- Canada
- Estonia / USA
but that does not allow us to make any assumptions.
From the
analysis of the viral code, there are some elements that could indicate that the country assaulter is precisely Italy. In fact within the viral code it is used as temporary file "ORDINI.exe" file which is then deleted. Also within self-extracting RAR archive is the "vai.vbe" file, where "vai" is an italian word. Why use Italian terms for filenames after they are deleted?
We are not aware of how long are plotting this attack, but the site
www[.]scuolaelementarediorziveccho[.]191[.]it has downloaded for 24h the "
Orziveccho" malware from the afternoon of 6th march 2017. A very fast attack at the predetermined target.
Authors: Gianfranco Tonello, Federico Girotto