TG Soft' s C.R.A.M. (Anti-Malware Research Center) analyzed an email campaign spreading the Trojan Banker TinyNuke on June 25, 2018
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
If you received a suspicious email, send it to C.R.A.M. (Center for Anti-Malware Research): How to send suspicious emails
|
INDEX
|
"TinyNuke" malware campaign.
Name: Trojan.Win32.
TinyNuke
Malware Family: Trojan Banker
VirIT: Trojan.Win32.TinyNuke.A, Trojan.Win32.TinyNuke.B
Description:
The email campaign started this morning on June 25, 2018
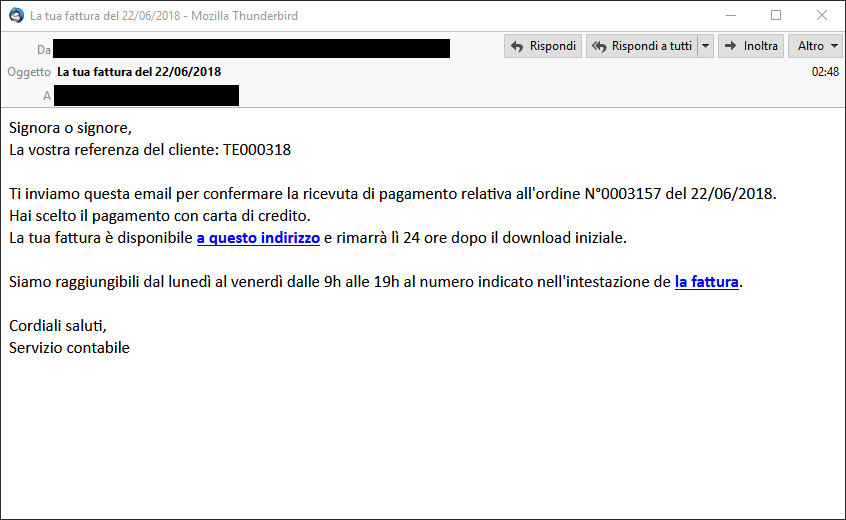
Example of examined email:
|
Subject: La tua fattura del 22/06/2018
|
Signora o signore,
La vostra referenza del cliente: TE000318
Ti inviamo questa email per confermare la ricevuta di pagamento relativa all'ordine N°0003157 del 22/06/2018.
Hai scelto il pagamento con carta di credito.
La tua fattura è disponibile a questo indirizzo e rimarrà lì 24 ore dopo il download iniziale.
Siamo raggiungibili dal lunedì al venerdì dalle 9h alle 19h al numero indicato nell'intestazione de la fattura.
Cordiali saluti,
Servizio contabile (Madam or Sir,
Your customer reference: TE000318 We are sending you this email to confirm the payment receipt for order No. 0003157 dated 06/22/2018. You chose credit card payment. Your invoice is available at this address and will remain there 24 hours after the initial download. We can be reached Monday through Friday from 9h to 19h at the number indicated in the header of the invoice. Best regards,
Accounting department)
|
 |
How it spreads:
The email looks like a payment receipt for a supposed order for which you need to download the corresponding invoice. The 2 links point to the site
http://mail[.]sandwichisland[.]com/fattura/ and, when clicked, lead to the download of a .ZIP archive file named "
fattura_22-06-18_1227572.zip"
This first .ZIP archive contains an empty text file named "
checksum.txt" and an additional .ZIP archive named
"fattura_22-06-2018.zip".
The second .ZIP archive contains an executable file named "fattura_22-06-2018.exe"
The campaign led to the spread of other infected emails from which malware is downloaded from the following URLs:
- http://mail[.]sandwichisland[.]com/fattura/
- http://mail[.]artisancloud[.]net/fattura/
- http://mail[.]investforshow[.]com/fattura/
- http://mail[.]breezypointdaycamp[.]com/fattura/
- http://mail[.]kidcompanions[.]net/fattura/
- http://mail[.]franciscopupo[.]com/fattura/
- http://mail[.]spectrumcommunicationstv[.]com/fattura/
The payload examined has the following characteristics:
File Name :
fattura_22-06-2018.exe
Size: 4492049 byte
MD5: 9A08AF60A5265EDF245D412B9A1A9351
When the file is run, it unzips into the [%temp%]\[time folder] folder. Inside it we can find a copy of the Firefox.exe browser (MD5: 52FFABA4273678BAE75442F2BC85B470) complete with its DLLs and, in addition, are present:
- the programTor.exe (MD5: 092E1A9BA12BE5B7E035BC9179C090BF)
- the image count_it_up.jpg (MD5: C75397B7F42B9DD8E07B0FEF7923CBAD)
- the Dll6.dll (MD5: E260BB10DC6EF85370E90F2281692742) size 223744 bytes
| The image "count_it_up.jpg" downloaded from the Banker Trojan.Win32.TinyNuke |
|
Contained within the
Dll6.dll library is the malware
Trojan.Win32.TinyNuke
In order for the infected module
Dll6.dll to be loaded automatically when Firefox opens, there is a file "
dependentlibs.list" that is used by Firefox precisely to load DLLs present in the ROOT of the program itself.
The Firefox program is then run for the first time, and will load the malware contained in the Dll6.dll library inside itself; a new Firefox process will then be run again, which will run a Tor process. Then another Firefox process will be run from the %appdata%\[User ID] example folder (
%userprofile%\AppData\Roaming\2C73FCE9544F925C\firefox.exe).
The new Firefox process will run a new instance of TOR every second and try to connect to the following domain:
http://sxgqppyilieqi2vi[.]onion/admin/_[.]php?2C73FCE9544F925C
The victim's ID is passed to the onion site page (
_.php) which, in our example is "
2C73FCE9544F925C," so that it can identify itself to the C&C (Command and Control) server.
The exchange of information between Firefox and Tor is done through the use of a local port which is 9050 TCP, which is created by the first TOR process and exploited by the malicious DLL (
Dll6.dll).
The following information is exchanged through this port:
"
nikoumouk sxgqppyilieqi2vi.onion"
The malware contained in the
Dll6.dll library includes another malicious DLL that is infected by
Trojan.Win32.TinyNuke.B and is part of the Banker Trojan family.
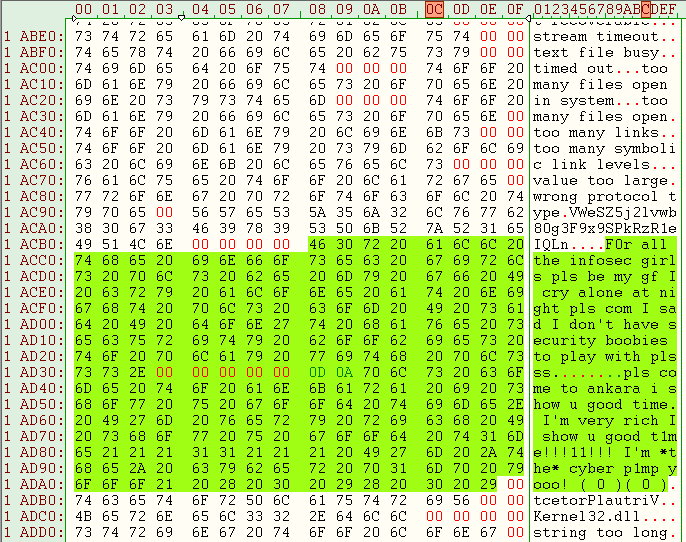
Interestingly, there are some strings within the
Dll6.dll module:
STRING 1:
"F0r all the infosec girls pls be my gf I cry alone at night pls com I sad I don't have security boobies to play with plsss.
pls come to ankara i show u good time. I'm very rich I show u good t1me!!!11!!! I'm *the* cyber p1mp yooo! ( 0 )( 0 )"
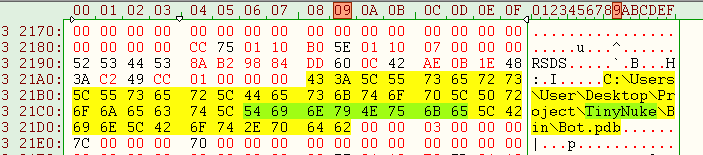
STRING 2:
"C:\Users\User\Desktop\Project\TinyNuke\Bin\Bot.pd"
Linking to http://sxgqppyilieqi2vi[.]onion, it displays the following image depicting " Mustafa Kemal Atatürk" who was a Turkish military man and politician, founder and first president of Turkey. He is considered Turkey's national hero, and father of "modern Turkey"(Source: WIKIPEDIA).
With the message " Armut pis agzima düs," which translated from the Turkish language reads " The pear is dirty."
|
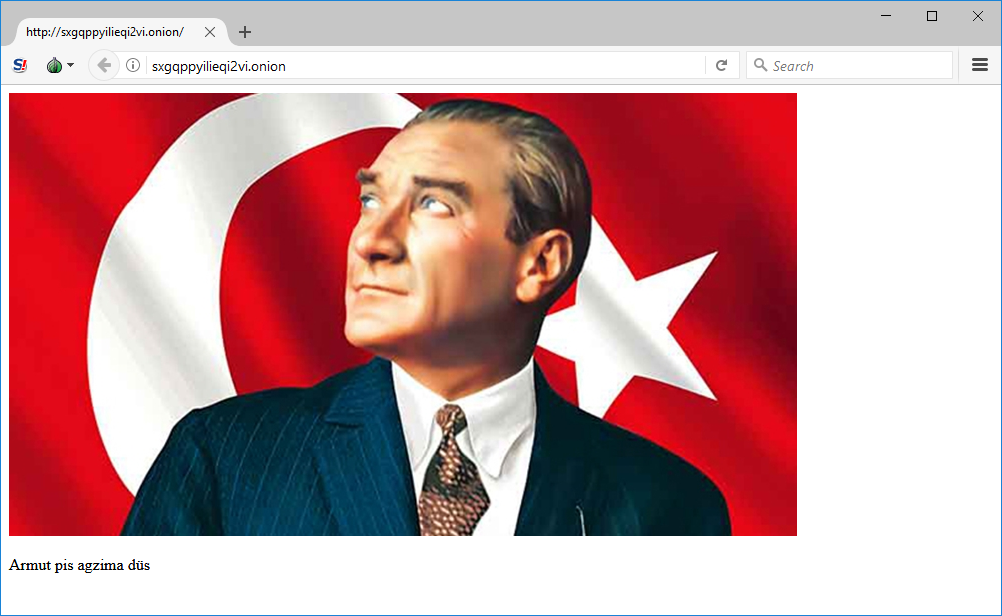 |
The image of Mustafa Kemal Atatürk is uploaded from the site
https://richardlangworth[.]com/wp-content/uploads/2010/07/f089b3f5045557f987b5ce90c3ea0609786fcd0e[.]jpg.
The Firefox.exe file, that loads the malicious DLL, is placed into automatic execution by creating a link in the user's startup folder:
%userprofile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\2C73FCE9544F925C.lnkwith destination: %userprofile%\AppData\Roaming\2C73FCE9544F925C\firefox.exe
The Trojan.Win32.TinyNuke is part of the Banker macrofamily, its peculiarities are to steal access passwords to important sites such as may be home banking, e-mail, ftp etc.
IOC:
MD5:
FDD3D87AD53C506AB172D415729A5914
9EF0D6BCEA1141DB49C973B21B307915
9A08AF60A5265EDF245D412B9A1A9351
E260BB10DC6EF85370E90F2281692742
C75397B7F42B9DD8E07B0FEF7923CBAD
URL:
http://mail[.]sandwichisland[.]com/fattura/
http://mail[.]artisancloud[.]net/fattura/
http://mail[.]investforshow[.]com/fattura/
http://mail[.]breezypointdaycamp[.]com/fattura/
http://mail[.]kidcompanions[.]net/fattura/
http://mail[.]franciscopupo[.]com/fattura/
http://mail[.]spectrumcommunicationstv[.]com/fattura/
193.124.92.163
193.124.92.217
193.124.92.213
193.124.92.167
193.124.92.165
193.124.92.172
193.124.92.219
sxgqppyilieqi2vi[.]onion
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of
ZIP-formatted attachments and, if possible, DO NOT enable automatic
macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening
Word and
Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a
Banker, the advice from TG Soft's C.R.A.M. is to take appropriate security precautions
even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the location involved was used for home-banking transactions, an assessment with your
credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to the TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to the TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs.We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- Through the Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center