| TG Soft's Anti-Malware Research Centre has acknowledged a sharp increase in CryptoLocker attacks. This cryptomalware has done widespread damage thanks to a fake email from ENEL (Italian State-owned electricity provider), bearing the following subject: |
Subjects of this bullettin
|
==> "[Recipient's name] bolletta per la fornitura di energia elettrica"
==> bolletta per la fornitura di energia elettrica |
 |
|
New CryptoLocker variants, like older ones, are delivered through a fake email from ENEL, bearing a rather unpleasant subject:
"[Recipient's name] bolletta per la fornitura di energia elettrica", roughly meaning "Electricity Bill".
The goal is to trick the recipient into clicking misleading links and buttons inside the mail, driven by the curiosity to find out whether the bill they received is actually theirs, especially because the alleged due amount is substantial.
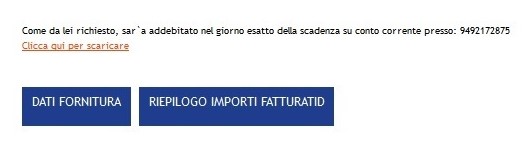
The email bears striking similarity to actual ENEL bills; a closer and more careful look, however, would reveal some inconsinstencies: there is not the recipient's full name - just a random number, and the fiscal code (Codice Fiscale) is totally random and is no way associated with the recipient. The layout alone, though, could trick lots of people into clicking the links and buttons. |

Click here to show the picture fullscreen |
In our sample email, the links looked like these:
Clicca qui per scaricare
DATI FORNITURA
RIEPILOGO IMPORTI FATTURATID |
 |
Once these links or buttons are clicked, the user is redirected to a website, its layout being similar to ENEL website's, with a CAPTCHA input text field. This
fake website is hosted on a Russian server (the
.su domain being reserved to post-Soviet States): the fact that an Italian website is hosted under a Russian domain (notice the Russian Federation flag on the navigation bar) should be another warning sign.
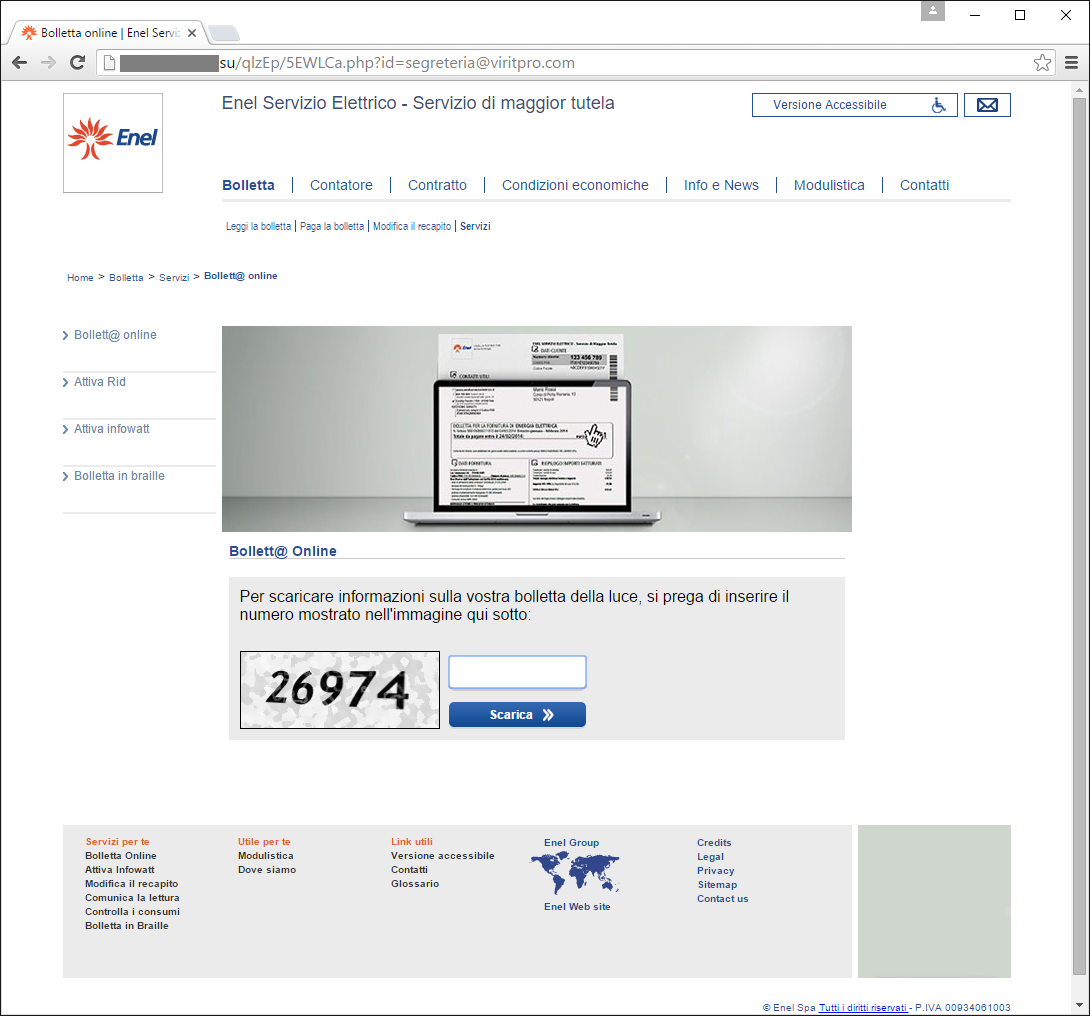
| What happens after the CAPTCHA is typed in and the [ Scarica >> ] (download) button is pressed? The CryptoLocker attack starts and the encryption of every file (either local or shared, visible or hidden) begins. |
 |
Should you receive emails like this, do not get overwhelmed by curiosity, and avoid clicking buttons and links found inside emails. Our advice is to forward these mails to our Research Centre for further analysis - the email address is lite@virit.com
CrytpoLocker's family was first analized by
TG Soft's Research Centre (C.R.A.M.) back in 2013. For further details, please read our bulletin dated 06/12/2013 "
Bad news with Cryptolocker".
TG Soft has developed new technologies to protect from cryptomalware attacks, and integrated them into
Vir.IT eXplorer PRO.
Learn how to protect your data from new generation cryptomalware!
We will now explain what cryptomalwares are and how they operate.
Cryptomalwares: what they are and how they work
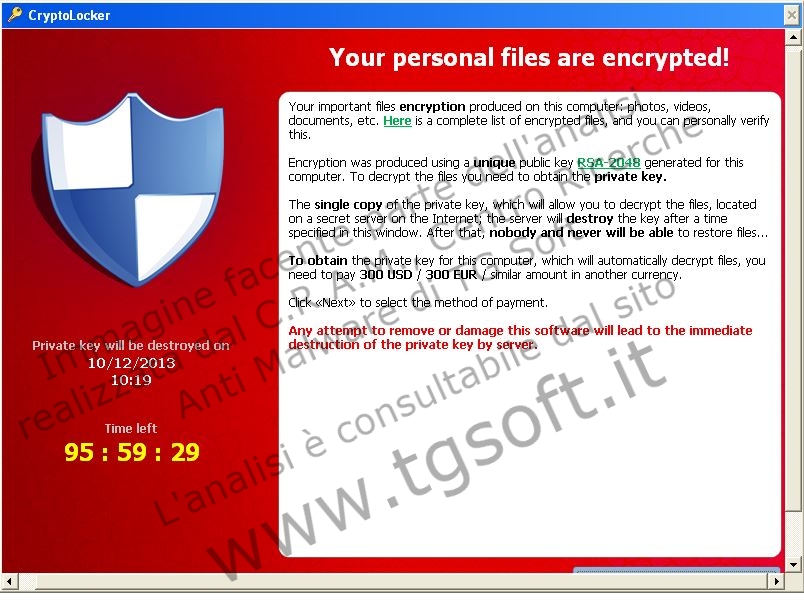
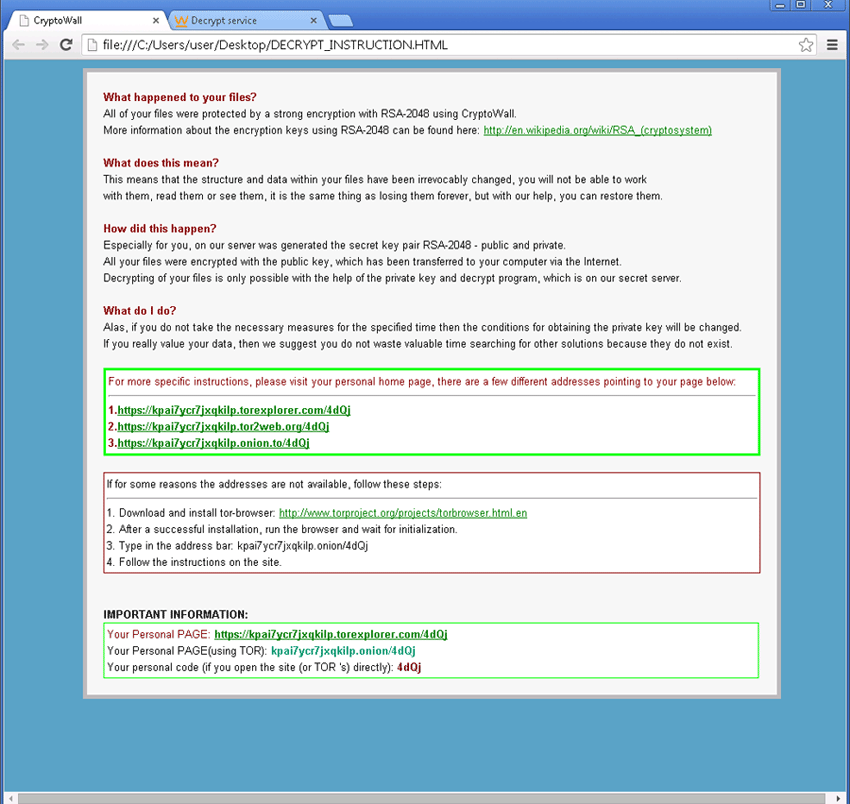
Cryptomalwares are a type of ransomware: files are made inaccessible through encryption, and to have them decrypted the user has to pay a ransom. A new variant is released every hour or so; the most infamous ones are CryptoLocker, CTB-Locker, CryptoWall and TeslaCrypt. Because of this rapid turnover, intercepting them using a method based on identification signatures is virtually impossible; signature-based real-time protection is ineffective.
|
 |
 |
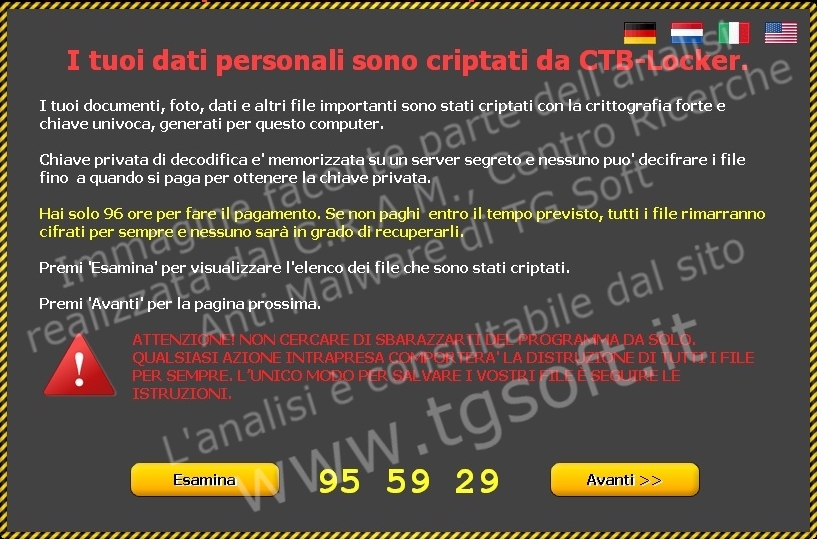 |
Cryptomalwares have these peculiar features:
- They generally are "polymorphic" malwares, meaning that they can self-mutate. This polymorphism is achieved by activating totally different files from the same link in a very short time span (sometimes even 15 minutes); such links spawn cryptomalwares or other types of viruses/malwares, such as droppers, rootkits, etc. Because of this frequence, an antimalware software relying on the traditional, signature-based real-time protection technique will never be able to intercept and stop these threats.
- They have a very short, sometimes null, incubation period. The activation is immediate and its effects (encryption of .doc, .xls, .mdb, .jpg, but also backup files) take place very quickly.
- Their encryption algorithms are extremely sophisticated, sometimes 2.048 bit long, thus making them irrecoverable.
- They ask for a ransom to have files decrypted. Ransoms are paid via Tor-Onion network (deep/dark-web), and the BitCoin virtual currency is used in virtually all cases.
|
How to stay safe from cryptomalware attacks with Vir.IT eXplorer PRO technologies
In our 26/11/2015 bulletin, we tried to describe those technologies built into Vir.IT eXplorer PRO and how to use them properly.
|
TG Soft's Research Centre (C.R.A.M.) has been analyzing the most widespread cryptomalware types for three years, and has developed two technologies:
- Vir.IT BackUp, an advanced backup utility devised to protect every user's most precious files. Vir.IT BackUpis very simple and straightforward to use; it allows the user to select the files and folders they want to have a backup copy of. The copy is an automated and scheduled process. Should a computer be infected by a new generation and yet-to-be-identified cryptomalware causing widespread encryption, Vir.IT BackUp copies can be reverted, since an advanced BackUp system is used, so that these copies can hardly be accidentally deleted or "forcefully" altered by some malware.
- A real-time protection module based on a heuristic and behavioural approach. It is capable of identifying those tasks that behave in a similar way to cryptomalwares and, once identified, it can halt them, thus stopping the encryption and saving more than 99.63% of data files.
It was verified on real attacks that the minimum number of encrypted files, in the early stages of cryptomalware attacks (even new generation ones), is 5 - thus sparing every other file. Potentially encryptable files are approximately 10'000, so this technology effectiveness stands at (1-5/10.000)*100 = 99,95%.
- In the very short time span when the cryptomalware has just begun encrypting data and the heuristic automata has yet to intervene, Vir.IT eXplorer PRO AntiCryptoMalware module enacts a techique called "On-The-Fly Backup", which:
- creates a backup copy of document files (such as .doc, .xls, .pdf, .jpg) between 2KB and 3MB;
- stores these copies for 48 hours to allow recovery in case of necessity.
|



99,63%*
Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO

|
 |
If Vir.IT eXplorer PRO has been correctly set up, it is possible to save up to 100% of data in case of cryptomalware. Those file that may have been encrypted in the early stages of the attack can be restored thanks to Vir.IT BackUp, thus reducing the loss to 15/20 files - in the case they were created/edited before a new backup could be made.
|
Vir.IT eXplorer PRO users can take advantage of these technologies, especially
Vir.IT Backup, in order to save their precious data from cryptomalware or other yet-to-be-discovered malicius software and their variants.
How and where to buy Vir.IT eXplorer PRO security suite
Decryption of files, which have been encrypted with 2048 bit long keys, is only theoretically possible, but it is technically impracticable. We invite you to consider the purchase of
Vir.IT eXplorer PRO since
prevention is the only way to contrast cryptomalwares.
Vir.IT eXplorer PRO can be purchased in the following ways:
TG Soft - Public Relations
*Mean percentage of files saved from encryption thanks to Vir.IT eXplorer PRO technologies - data gathered from actual cryptomalware attacks by TG Soft's Research Centre (C.R.A.M), October 2015.









