PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in
June 2023:
24/06/2023 =>
Amazon
16/06/2023 =>
Aruba - Conferma rinnovo (Renewal confirmation)
14/06/2023 =>
Account Posta Elettronica (Email Account)
12/06/2023 =>
Account Posta Elettronica (Email Account)
12/06/2023 =>
Mooney
07/06/2023 =>
Netflix
06/06/2023 =>
Aruba - Importanti promemoria (Important reminders)
06/06/2023 =>
Aruba - Dominio in scadenza (Expiring domain)
02/06/2023 =>
Istituto Bancario (Bank)
02/06/2023 =>
Account Posta Elettronica (Email Account)
02/06/2023 =>
Aruba - Scadenza Dominio (Expiring domain)
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible easily imaginable consequences .
June 24, 2023 ==> Phishing Amazon
«SUBJECT: <
Re: account in scadenza, conferma l'iscrizione per guadagnare con Amazon >
(Re: expiring account, confirm membership to earn with Amazon)
We examine below a new phishing attempt behind a message, that seems to be from
Amazon.
The email refers to an expiring
Amazon account that has been reserved specifically for the recipient, who was selected along with a few others in Italy, and would allow them to invest and earn from home. To use it and avoid assignment to someone else, the user is asked to fill out a form, by clicking on the link:
CLICCA QUI (Click here) (Cli
Examining the text, we should already be suspicious about the email's origin. In fact, the message comes from two email addresses that do not seem referable to the official Amazon domain and namely <info(at)couponandomail(dot)ovh> and <noreply(at)promodelmese(dot)ovh>.
Anyone who unluckily clicks on the link
CLICCA QUI (Click here), will be redirected to a graphically well-designed WEB page, that invites the user to immediately start using the Amazon Code account, promising large earnings (even in just 24 hours).
To persuade the recipient to fill out the login form - which initially requires first and last name and phone number - some nominal reviews of program members are also given, who allegedly earned ''over €1,739,000''!!!
However, the page you are being referred to, is hosted on an anomalous address/domain, which is not at all referable to Amazon's legitimate site. We list it below:
https[:]//amazoncode[.]info/fx-amz-code-long-it....
We remind you that Amazon never requires you to provide sensitive data via email and doesn't propose monetary gains.
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks, with all the associated easily imaginable risks .
June 14, 2023 ==> Phishing Account Posta Elettronica
«SUBJECT: <
Action Required: Mailbox Storage Out Of Space>
We examine below another phishing attempt aimed to steal the credentials of the victim's e-mail account.
The message informs the recipient that he has 9 pending messages, because he has reached the maximum storage space limit. It then invites him to increase the storage space, otherwise he will no longer be able to send or receive messages, through the following link:
UPDATE STORAGE
If we examine the email, we see that the message comes from an email address not referable to the server that hosts the mailbox <
noreply(at)cpanel(dot)com>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
UPDATE STORAGE ,will be redirected to an anomalous WEB page, which, as you can see from the image on the side, has nothing to do with the e-mail account manager.
The page to which you are redirected, to enter your email account credentials, is hosted on an abnormal address/domain, which we show below:
https[:]//ipfs[.]io/ipfs/bafybeifwtldig24fsmrgbwlm2vr2gll4axhcdrp....
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks with all the associated easily imaginable risks .
June 12, 2023 ==> Phishing Account Posta Elettronica
«SUBJECT: <
***** password scadrà>
(password will expire)
We examine below another phishing attempt aimed to steal the credentials of the victim's e-mail account.
The message informs the recipient that his mailbox password, whose address is reported, will soon expire. It then invites him to confirm the password to continue using his account, via the following link:
CONTINUA AD UTILIZZARE LA PASSWORD ATTUALE (KEEP USING YOUR CURRENT PASSWORD)
Examining the email, we see that the message comes from an email address not referable to the server that hosts the mailbox <
info(at)boa(dot)org>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
CONTINUA AD UTILIZZARE LA PASSWROD ATTUALE (KEEP USING YOUR CURRENT PASSWORD), will be redirected to an anomalous WEB page, which, as you can see from the image on the side, has nothing to do with the e-mail account manager.
The page to which you are redirected to enter your email account credentials, is hosted on an abnormal address/domain, which we show below:
https[:]//ipfs[.]io/ipfs/QmXECw3gHfLk49eXmCZ5rsAZY....
We always urge you to be careful and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as they will be sent to a remote server and used by cyber crooks, with all the associated easily imaginable risks.
June 12, 2023 ==> Phishing Mooney
«SUBJECT: <
Avviso >
(warning)
Again this month we find the following phishing attempt, coming as a false communication from
Mooney, the Italian Proximity Banking & Payments company.
The message informs the recipient, that his account is suspended, due to an update that is still pending.
It then invites him to check the phone number connected to his device, to confirm the update and continue using his card, via the following link:
Continua il processo di convalida (Continue the validation process)
This time the phishing campaign simulates a communication from the Italian online payment company
Mooney, which is clearly unrelated to the mass sending of these emails, that are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we see, in addition to the Company Logo, the sender's e-mail address that disguises the original one, to further mislead the user. However it is a label created for this purpose <
jelfasah1(at)unla(dot)edu(dot)ar>. Let's always pay close attention before clicking on suspicious links.
Anyone who unluckily clicks on the link
Continua il processo di convalida (Continue the validation process) will be redirected to an anomalous WEB page, which has nothing to do with
Mooney's official website, but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
.
07 Giugno 2023 ==> Phishing Netflix
«SUBJECT: <
Netflix>
This new phishing attempt originates with a fake e-mail from
Netflix.
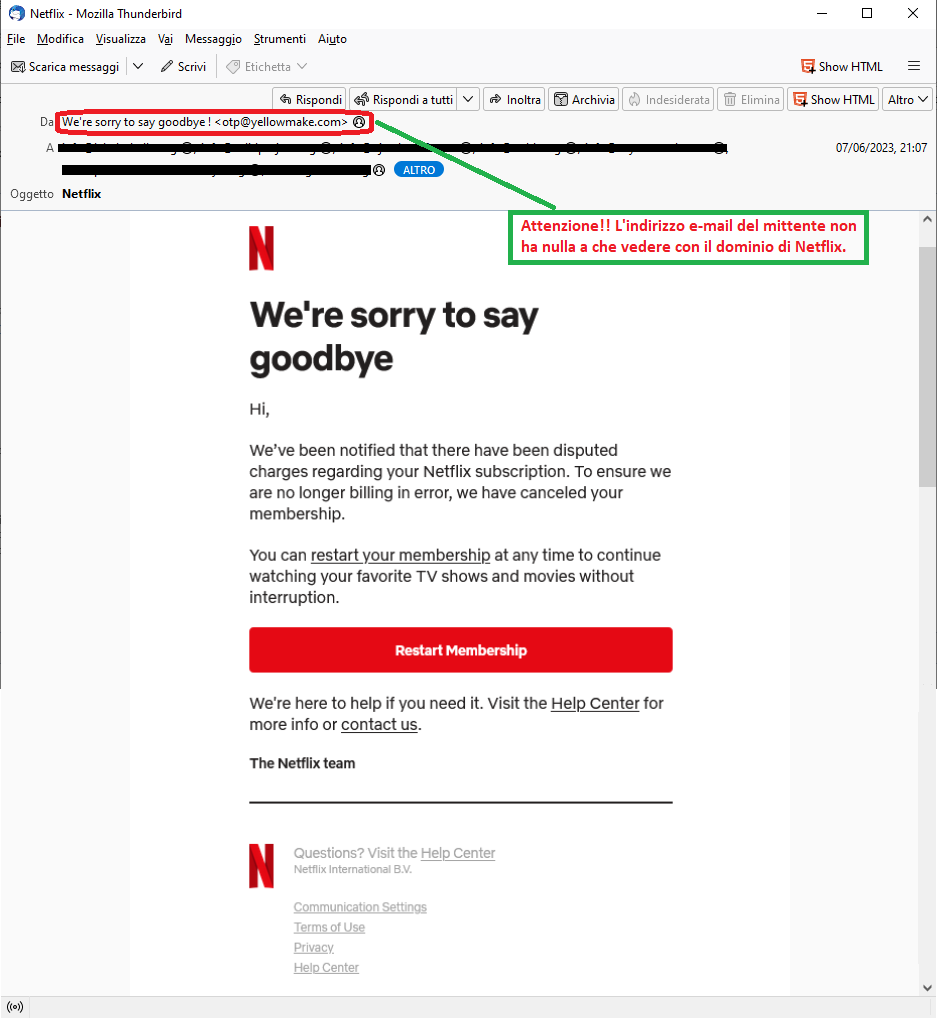
The message, in English, notifies the unsuspecting recipient that problems have been encountered with the charging of subscription renewal fees. To avoid billing errors, it informs him that his Netflix subscription has been cancelled. He can proceed at any time to renew his membership and continue to watch his favorite movies and TV series, by clicking on the following link:
Restart Membership
The alert message comes from an email address <otp(at)yellowmake(dot)com> unrelated to the Netflix domain and contains very generic text, although the cybercriminal had the graphic foresight to include the well-known logo of the streaming distribution company for movies and TV series.
The intention is to lead the recipient to click on the link Restart Membership which, we would like to point out, redirect to a page that has nothing to do with the Netflix's website, but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data in order to use them for criminal purposes.
June 06, 2023 ==> Phishing Aruba
SUBJECT: <
Importanti promemoria!>
(Important reminders)
Here we find another phishing attempt that comes again from a false communication by
Aruba.
The message informs the recipient that his domain, hosted on Aruba and linked to his e-mail account, has insufficient storage space and that there are 2 new outstanding messages that have been rejected. It then advises him to update the storage space, to avoid losing more incoming messages, through the following link
:
>>>Aggiorna ora (Update now)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address
<gianluca(dot)gabba(at)ggs-rappresentanze(dot)it> does not come from the official domain of
Aruba.
Anyone who unluckily clicks on the link
>>> Aggiorna ora (Update now), will be redirected to an anomalous WEB page, which has nothing to do with the official
Aruba's website, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
June 02, 2023 ==> Phishing Istituto Bancario (Bank)
SUBJECT <
Assistenza clienti - Attiva il nuovo sistema di sicurezza> (
Customer service - Activate the new security system)
We find again this month the phishing campaign that - through an e-mail exploiting graphics stolen from, or similar to, those of a well-known national banking institution - tries to pass itself off as an official communication, in order to induce the unsuspecting recipient to do what requested and falling into a trap based on social engineering techniques.
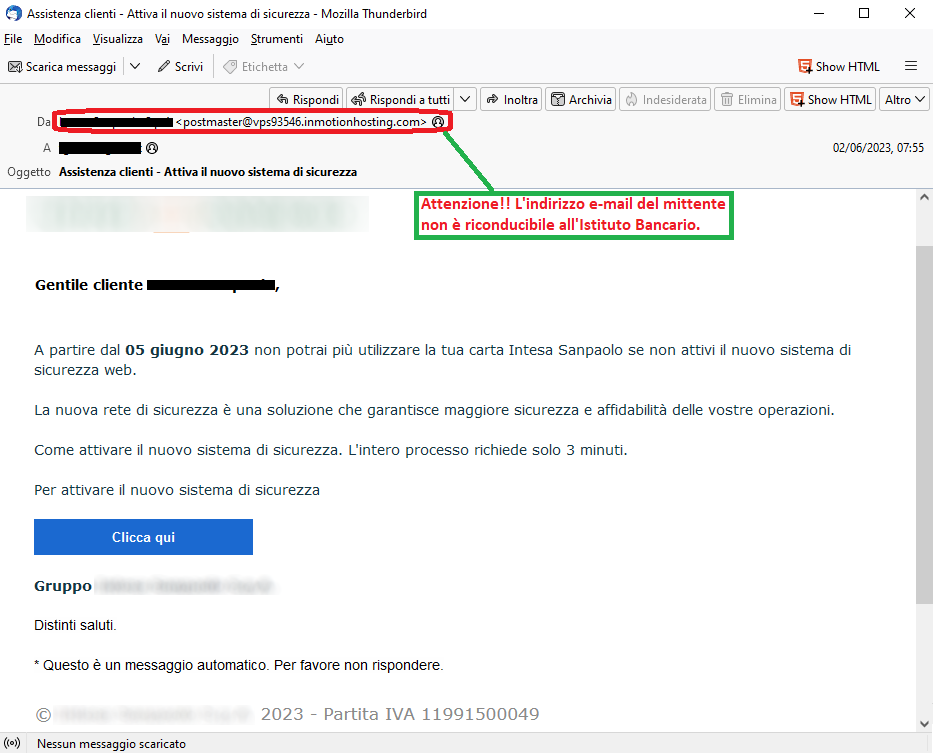
The message notifies the unsuspecting recipient that, since June 05, 2023, he will no longer be able to use his card unless he activates the new web security system, which provides greater security and reliability to transactions. Then it invites him to activate the new security system. The operation is simple and takes only 3 minutes, through the following link:
Clicca qui (Click here)
We can immediately see that the alert message comes from an e-mail address <postamaster(at)vps93546(dot)inmotionhosting(dot)com> that is highly suspicious and contains very general text, although the cybercriminal had the graphic foresight to include the well-known banking institution logo, that could mislead the user.
The aim is to lead the recipient to click on the link Clicca qui (click here) which, we would like to point out, links to a page that has nothing to do with the official site but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
June 02, 2023 ==> Phishing Account Posta Elettronica (Email Account)
SUBJECT: <
WARNING: E-MAIL ACCOUNT TERMINATION>
Let's examine below the phishing attempt that aims to steal the credentials of the victim's e-mail account.
The message, in English, informs the recipient that it is necessary to confirm his e-mail address, so that it is not deleted. It then invites him to click on the link provided in the e-mail, to verify that he is the owner of the associated e-mail address, via the following link:
verify your email address
Examining the email, we notice that the message comes from an email address not referable to the server hosting the mailbox<
accounts(at)emytyenergy(dot)com>. This is definitely abnormal and should, at the very least ,make us suspicious.
Anyone who unluckily clicks on the link
verify your email address, will be redirected to an anomalous WEB page, which has nothing to do with the official site, but has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals whose goal is to get hold of your most valuable data, in order to use them for criminal purposes...
02 - 06 June 2023==> Phishing Aruba - Dominio scaduto (Domain expired)
Below are the phishing attempts we find this month, which appear to come from a false communication from
Aruba.
EXAMPLE 1
< Avviso - Scadenza Dominio - N° Ordine: 46603599> (Notice - Domain Expiration)
EXAMPLE 2
«Dominio in scadenza, per rinnovare?» (Expiring domain, to renew?)
In the examples above, which are very similar, the customer is notified that his domain hosted on Aruba is about to expire and then invites him to renew before the expiration date. It informs him that, if the domain is not renewed, all services associated with it will be deactivated, including e-mail boxes. Therefore he will no longer be able to receive and send messages. It then invites the user to re-new the domain, by completing the order, through the links listed in the email.
The aim is clearly to get the user to click on the link in the email:
RINNOVA IL DOMINIO o Rinnova Dominio (RENEW THE DOMAIN)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
To detect these phishing attempts, it is first necessary to examine the sender's e-mail address which, as we can see in the 2 cases shown (<support(at)andrastore(dot)es> and <staff-communicazioni(at)lotusresidentialuk(dot)com> ), do not come from Aruba's official domain.
Very often these messages are poorly written emails that contain spelling errors or renewal requests for not expiring services, since they use urgency or data security to obtain user's information.
It's also important to examine the links or attachments that these messages contain, which usually redirect to a counterfeit website asking to enter your personal information (such as account username and password, or credit card number to make account renewals). If these data are entered, will be used by cyber criminals for criminal purposes.
A little bit of attention and glance, can save a lot of hassle and headaches....
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on Phishing techniques for more details:
05/04/2023 17:34 - Phishing: the most common credential and/or data theft attempts in April2023...
03/03/2023 16:54 - Phishing: the most common credential and/or data theft attempts in March 2023..
06/02/2023 17:29 - Phishing: the most common credential and/or data theft attempts in February 2023...
02/01/2023 15:28 - Phishing: the most common credential and/or data theft attempts in January 2023...
02/12/2022 15:04 - Phishing: the most common credential and/or data theft attempts in December 2022...
04/11/2022 17:27 - Phishing: the most common credential and/or data theft attempts in November 2022...
05/10/2022 11:55 - Phishing: the most common credential and/or data theft attempts in October 2022...
06/09/2022 15:58 - Phishing: the most common credential and/or data theft attempts in September2022...
04/08/2022 16:39 - Phishing: the most common credential and/or data theft attempts in August2022...
06/07/2022 12:39 - Phishing: the most common credential and/or data theft attempts in July2022...
06/06/2022 14:30 - Phishing: the most common credential and/or data theft attempts in June 2022...
02/05/2022 11:06 - Phishing: the most common credential and/or data theft attempts in May2022...
Try Vir.IT eXplorer Lite
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition-.to supplement the antivirus in use to increase the security of your computers, PC and SERVER.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- fully interoperable with other AntiVirus software and/or Internet Security products (both free and commercial) already installed on your computer. It doesn't need any uninstallation and it doesn't cause slowdowns, as some features have been appropriately reduced to ensure interoperability with the AntiVirus software already on your PC/Server. This, however, allows cross-checking through the scan
- It dentifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security, the Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).
 TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center that allowed us to make this information as complete as possible.
How to send suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways::
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify";
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)


 TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) where you can download the Lite version, which can be freely used in both private and business settings For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis