PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in
June 2022:
29/06/2022 =>
CREDEM
29/06/2022 =>
Webmail
28/06/2022 =>
Banco BPM
28/06/2022 =>
Account di posta (Email Account)
27/06/2022 =>
Poste il tuo pacco è ora disponibile (italian postal service: your package is now available)
24/06/2022 =>
InBank
24/06/2022 =>
Nexi
21/06/2022 =>
EuroPages
20/06/2022 =>
Aruba -Rinnova il dominio (Renew the domain)
17/06/2022 =>
Aruba - Chiusura del tuo account (Termination of your account)
15/06/2022 =>
Aruba
15/06/2022 =>
EuroPages
07/06/2022 =>
EuroPages
03/06/2022 =>
Account di posta elettronica (Email Account)
03/06/2022 =>
EuroPages
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible, easily imaginable, consequences.
June 29, 2022 ==> Phishing CREDEM
«SUBJECT:<
Re: >
This new phishing attempt comes as a fake e-mail from
CREDEM.
The message, allegedly from CREDEM, informs the unsuspecting recipient that, for security reasons, his account has been restricted and, in order to use it, the new security application must be installed. This is necessary to ensure security in payments. In addition, in order to induce the user to upgrade as soon as possible, the new security app has no additional cost if it is done within 14 business days.
It then invites him to download the update through the following link:
Avvia il processo (Start the process))
The alert message comes from an email address <belinda(dot)snow(at)ns(dot)sympatico(dot)ca>, unrelated to CREDEM's official domain, and contains very generic text, since no identifying information about the current account holder is given. Obviously, no credit institution sends notices regarding security or sensitive data asking for personal data, therefore it is important to be cautious.
The purpose is to lead the recipient to click on the link:
Avvia il processo (Start the process))
which, we would like to point out, links to a page that has nothing to do with the site of
CREDEM but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
June 29, 2022 ==> Phishing Webmail
«SUBJECT: <
La tua richiesta è attualmente in corso e sarà completata in 48 ore. >
(Your request is currently in process and will be completed in 48 hours)
This phishing attempt aims to steal the password to access the mailbox hosted on
Webmail.
The message informs the user that his supposed request to deactivate/terminate webmail, has arrived. The procedure is currently in progress and will be completed in 48 hours.
It then warns the user that he can always cancel/terminate the request from the following link:
Annulla/Interrompi processo (Cancel/Stop Process)
Examining the email we notice that the message, marked by the concise and essential text layout, comes from an email address that cannot be traced back to the email server <
info(at)finvail(dot)com>.
Anyone who unluckily clicks on the link
Annulla/Interrompi processo (Cancel/Stop Process), will be redirected to an anomalous WEB page, which has nothing to do with the
Webmail's site, but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
June 28, 2022 ==> Smishing Banco BPM
We examine below a new smishing attempt hiding behind a fake text message from
Banco BPM.
The message, which we display on the side, notifies the unsuspecting recipient that he has received (1) new message and invites him to click on the following link to view it:
https[:]//e-bpm[.]me
At first we notice that the message is very generic, although in this case the name of the recipient, is provided.
The purpose is clearly to get the user to click on the link:
https[:]//e-bpm[.]me
As we can see from the image on the side, the web page to which we are redirected by the link, mimics quite well the official website of
Banco BPM.
At a glance, the web page where we are redirected seems trustworthy, especially due to the graphic devices used, that can mislead the user.
The access page for Account management, however, is hosted on an anomalous address/domain that cannot be traced back to
Banco BPM's official domain, which we report below:
e[.]bpm[.]me
By entering the Banco BPM account login information on this FORM to log in to the checking account, this information will be sent to a remote server and used by cyber crooks with all the risks easily imaginable.
June 28, 2022 ==> Phishing Account di posta (Email Account)
«SUBJECT:
< Check Recent Activities! >
We examine below the phishing attempt aimed at stealing the mailbox of the victim.
The message, in English, informs the recipient that three incoming messages are blocked. The victim, to view them, has to validate his identity, confirming the ownership of the mail account specified in the message. To do this, he must click on the following link:
CONFIRM NOW
When we examine the email, we notice that the message comes from an email address not traceable to any email provider <
server1(at)moov(dot)ng>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
CONFIRM NOW, will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
June 27, 2022 ==> Phishing PosteItaliane: Consegna del pacco (Italian postal service: your package is now available)
«SUBJECT
: < Il tuo pacco e ora disponibile per la spedizione 📦 > (Your package is now available for shipping)
Here comes back the phishing attempt hiding behind a false communication from an unidentifiable sender, concerning the delivery of an alleged package.
The message notifies the unsuspecting recipient that his package is available for shipment. We notice from the very generic message, that neither the courier to whom the shipment has been entrusted nor any reference about the package delivery, is given. These messages are increasingly being used to scam consumers who, more and more, use e-commerce for their purchases.
The message, then, invites the user to click on the following link:
In attesa di distribuzione, apre subito!!>> (Pending distribution, opens immediately!!)
The alert email comes from an email address <
mail(at)zaful(dot)com> that is not from any known courier. Anyone who clicks on the link will be redirected to a web page, which graphically mimics the
PosteItaliane (Italian postal service) page and which alerts the user about 1 pending message inviting him to open it.
We notice, however, in the side image, that the url address on the broswer bar, has nothing at all to do with the authentic
PosteItaliane (Italian postal service) domain:
https[:]//finixmelobeat[.]com/?!!AZ-09-(20)!
Then by clicking ''Confermare'' '(Confirm'), we are redirected to another screen where we are told that the delivery of the package is pending, and a supposed tracking code is given to track the package...
Moving on, after clicking on ''Pianifica la tua consegna'' (Schedule your delivery'), we are presented with a new screen that gives us information about the status of the package and invites us to choose how to arrange the new delivery.
|
The next screen asks us how we prefer the package to be delivered: "Voglio che mi venga consegnato" "I want it delivered to me" or "Vado a prenderlo io stesso" "I'll pick it up myself.".
|
This is followed by 2 more questions like the previous one, asking where we prefer the package to be delivered:: "
A casa" (At home) or "
A lavoro" (At work), and when we prefer it to be delivered: "Giorni lavorativi" (Weekdays) or "Fine settimana" (Weekends).
After selecting our preferences, we finally arrive at a new screen, confirming the sending of the package, with estimated delivery in 3 days....Then we are redirected to a further page to enter our contact details and pay the shipping costs of €2.
From the side image we notice that our personal information is actually being requested to send the package and then the payment. As you can see, the login page is hosted on an abnormal address/domain, that clearly has nothing to do with
Poste Italiane (Italian postal service)...
https[:]//acevalue[.]online/c/rKw1mVyOr?s1....
The purpose of this elaborate fake email, is to induce the user to enter his personal information.
To conclude, we always urge you to be wary of any email asking for confidential data, and avoid clicking on suspicious links which could lead to a counterfeit site, difficult to distinguish from the original, thus putting your most valuable data in the hands of cyber crooks for their use and profit.
June 24, 2022 ==> Phishing InBank
SUBJECT
: <
Lapplicazione ιnΒank, nuovo aggiornamento>
(The ιnΒank application, new update)
This new phishing attempt pretends to be a communication from
InBank.
The message notifies the recipient that the Inbank application has been updated to protect banking transactions. He is then prompted to log into his
InBank account to perform the update, via the following link:
Il mio account (My account)
At first we notice that the text of the email is very generic and there is no identifying information about the client or the linked account. The alert email comes from an email address <
email(at)deals(dot)priceline(dot)com> that is clearly not from
InBank's official domain.
Anyone who unluckily clicks on the link
Il mio account(My account), will be redirected to a WEB page which has nothing to do with the
InBank's site, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
June 24, 2022 ==> Phishing Nexi
SUBJECT
: <
FVD: Transazione (transaction) 2725691 /U>
This new phishing attempt pretends to be a communication from
Nexi.
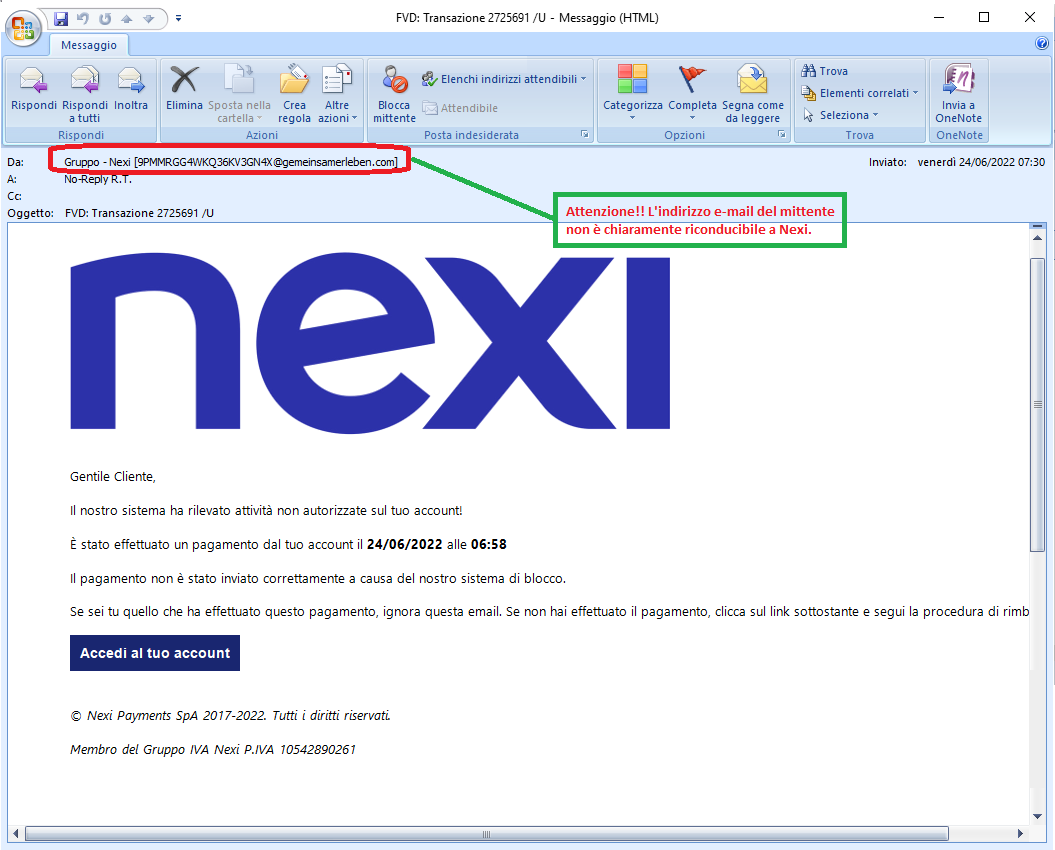
The message notifies the recipient that an unauthorized activity has been detected in his account; in fact, he is notified that a payment was made on
06/24/2022 at
06:58. It informs that the payment has been blocked, and that if the customer did not authorize it, he has to log into his
Nexi account, to request a refund via the following link:
Accedi al tuo account (Login to your account)
At first we notice that the text of the email is very generic and there is no identifying information about the client or the linked account. The alert email comes from an email address <
9PMMRGG4WKQ36KV3GN4X(at)gemeinsamerleben(dot)com> that is clearly not from
Nexi's official domain.
Anyone who unluckily clicks on the link
Accedi al tuo account (Login to your account), will be redirected to a WEB page which has nothing to do with the
Nexi's site, but which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for illegal purposes.
June 21, 2022 ==> Phishing EuroPages
«SUBJECT
: <Hai (1) nuovo messaggio di richiesta sul tuo prodotto su Europages.it> (You have (1) new inquiry message about your product on Europages.it)
This month prevails the following phishing attempt, allegedly a communication from
EuroPages, that aims to steal the login credentials of the victim's account.
The message, seemingly from
EuroPages (the largest international B2B sourcing platform), notifies the user of an incoming message from a certain "
Noah Gunther", concerning his product listed on EuroPages. It then invites the user to log into his account to view the request message, via the following link:
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT)
If we examine the email, we see that the message comes from an email address not traceable to the official
EuroPages' domain <
holger(dot)reimer(at)mytng(dot)de>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT), will be redirected to an anomalous WEB page.
From the side image we notice that you are asked to log into your
EuroPages account, by entering your credentials. At a glance, however, we notice that the login page is hosted on an anomalous address/domain.
https[:]//create[.]applicable[.]space/[.]well-known/Europages[.]it/inquiry[.]messageCenter....
If you enter your data on this FORM to perform verification/confirmation of your data, the data will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
June 20, 2022 ==> Phishing Aruba "Rinnova il tuo dominio" (Renew your domain)
«SUBJECT
: <
[ Aruba.it ] : Notifica nuovo messaggio! >
([ Aruba.it ] : New message notification!)
«SUBJECT
: <
Avviso Di Rinnovo >
(Renewal Notice)
Below are two more e-mails coming as a false communication from
Aruba, informing the recipient that his domain, hosted on Aruba, will expire on
06/21/2022.
If the domain is not renewed by that date, it will be deactivated togheter with all associated services - including mailboxes - so it won't be possible to send and receive messages. It then invites the user to renew the domain through the following link:
Clicca qui (Click here)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
If we examine the text of the messages, we notice right away that both of the sender's e-mail addresses <
pporttsupposuppno-replybilling(at)hyperhost(dot)ua> and <
staff-avviso-rinnivo(at)info.it> are not from
Aruba's official domain
Anyone who unluckily clicks on the link
Clicca qui (Click here), will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
June 17, 2022==> Phishing Aruba
«SUBJECT:
<La chiusura del tuo account "Aruba Email" è in corso> (The closure of your "Aruba Email" account is in progress)
We find another phishing attempt that comes as a false communication from
Aruba and aims to steal the webmail login credentials of the victim.
The message notifies the user that a request has recently been made to close the account and that the process for closure has been initiated. It then warns the user that he has 12 hours to cancel the request - if it was made in error or he was unaware of it - through the link below:
>>>Clicca qui per annullare la richiesta di cancellazione (Click here to undo your cancellation request)
Examining the text of the message, we notice right away that the sender's e-mail address <
holger(dot)reimer(at)mytng(dot)de>, is not from
Aruba's official domain.
Anyone who unluckily clicks on the link
>>>Clicca qui per annullare la richiesta di cancellazione (Click here to undo your cancellation request), will be redirected to an anomalous WEB page, which has nothing to do with
Aruba.
From the side image we notice that you are prompted to log in to your Aruba account by entering your credentials. At a glance, however, we realize that the login page is hosted on an anomalous address/domain...
https[:]//evilinc[.]biz/[.]well-known/webmailbeta[.]Aruba[.]it/user[.]account/aruba[.]mail/login/index[.]htm
If you enter your data on the deceptive PAGE / WEBSITE that has already been reported, to log in, this data will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks .
June 15, 2022 ==> Phishing Aruba "Rinnova il tuo dominio" (Renew your domain)
«SUBJECT: <
[ Aruba.it ] : Notifica nuovo messaggio! >
(New message notification!)
Here is a new phishing attempt this month, that comes as a fake communication from
Aruba.
The message informs the recipient that his domain, hosted on
Aruba, will expire on
16/06/2022. If the domain is not renewed by that date, it will be deactivated togheter with all associated services - including mailboxes - so it won't be possible to send and receive messages. It then invites the user to renew the domain through the following link:
Clicca qui (Click here)
Clearly, the well-known web hosting, e-mail and domain registration services company
Aruba, is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
Examining the text of the message, we notice right away that the sender's e-mail address <
pporttsupposuppno-replybilling(at)hyperhost(dot)ua>, is not from
Aruba's official domain.
Anyone who unluckily clicks on the link
Clicca qui (Click here), will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
June 15, 2022==> Phishing EuroPages
«SUBJECT:
<STEPHAN BAUER: DALLA GERMANIA TI HA INVIATO MESSAGGIO DI RICHIESTA SU EUROPAGES> (STEPHAN BAUER: FROM GERMANY SENT YOU REQUEST MESSAGE ON EUROPAGES)
We find again the following phishing attempt, a communication allegedely from
EuroPages, aimed at stealing the victim's account login credentials.
The message, seemingly from
EuroPages (the largest international B2B sourcing platform), notifies the user of an incoming message from a certain "
STEPHAN BAUER", concerning his product listed on
EuroPages. It then invites the user to log into his account to view the request message, via the following link:
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT)
If we examine the email, we see that the message comes from an email address not traceable to the official
EuroPages' domain <
holger(dot)reimer(at)mytng(dot)de>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT) will be redirected to an anomalous WEB page.
From the side image we notice that you are asked to log into your
EuroPages account by entering your credentials. At a glance, however, we notice that the login page is hosted on an anomalous address/domain.
https[:]//mail[.]howtoopenacompany[.]com/[.]well-known/Europages[.]it/inquiry[.]messageCenter....
If you enter your data on this FORM to perform verification/confirmation of your data, the data will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks .
June 07, 2022==> Phishing EuroPages
«SUBJECT:
<Hai (1) nuovo messaggio di richiesta sul tuo prodotto su Europages.> (You have (1) new request message about your product on Europages)
We find again the following phishing attempt, a communication allegedely from
EuroPages, aimed at stealing the victim's account login credentials.
The message, seemingly from
EuroPages ( the largest international B2B sourcing platform), notifies the user of an incoming message from a certain "
Mathew Hans", concerning his product listed on EuroPages. It then invites the user to log into his account to view the request message, via the following link:
ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT)
If we examine the email, we see that the message comes from an email address not traceable to the official
EuroPages' domain <
holger(dot)reimer(at)mytng(dot)de>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT), will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes
June 03, 2022 ==> Phishing Account di Posta elettronica (Email Account)
«SUBJECT:
< Avviso importante: la password della cassetta postale è scaduta - ****** - 2022 .> (Important notice: mailbox password has expired - ****** - 2022)
This month again we find the following phishing attempt aimed at stealing the mailbox of the victim.
The message notifies the user that his mailbox password has expired and a new password will be generated automatically by the system, 3 hours after the e-mail is opened. It then informs the user that he can continue to use his current password, via the following link:
Mantenere la password corrente (Keep the current password)
If we examine the email, we notice that the message comes from an email address not traceable to any email provider <
newsletter(at)blendicel(dot)cloudns(dot)ph> and it clearly does not come from the recipient's domain. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
Mantenere la password corrente (Keep the current password), will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
June 03, 2022==> Phishing EuroPages
«SUBJECT:
<Thomas Klaus: dalla Germania ti ha inviato un messaggio di richiesta relativo al tuo prodotto elencato su Europages.> (Thomas Klaus: from Germany sent you a request message about your product listed on Europages)
We find again the following phishing attempt, a communication allegedely from
EuroPages, aimed at stealing the victim's account login credentials.
The message, seemingly from
EuroPages (the largest international B2B sourcing platform), notifies the user of an incoming message from a certain "
Thomas Klaus", concerning his product listed on EuroPages. It then invites the user to log into his account to view the request message, via the following link:
ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT)
If we examine the email, we see that the message comes from an email address not traceable to the official
EuroPages' domain <
holger(dot)reimer(at)mytng(dot)de>. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on the link
>>>ACCEDI AL MIO ACCOUNT (LOGIN TO MY ACCOUNT), will be redirected to an anomalous WEB page, which has already been reported as a DECEPTIVE PAGE/ WEBSITE. In fact it is run by cyber-criminals, whose goal is to get hold of your most valuable data, in order to use them for criminal purposes.
A little bit of attention and glance, can save a lot of hassle and headaches..
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on Phishing techniques for more details:
02/05/2022 11:06 - Phishing: the most common credential theft attempts in May 2022..
06/04/2022 16:51 - Phishing: the most common credential theft attempts in April 2022.
08/03/2022 17:08 - Phishing: the most common credential theft attempts in March 2022
03/02/2022 16:25 - Phishing: the most common credential theft attempts in February 2022...
04/01/2022 09:13 - Phishing: the most common credential theft attempts in January 2022..
03/12/2021 15:57 - Phishing: the most common credential theft attempts in December 2021..
04/11/2021 09:33 - Phishing: the most common credential theft attempts in November 2021...
07/10/2021 14:38 - Phishing: the most common credential theft attempts in October 2021..
10/09/2021 15:58 - Phishing: the most common credential theft attempts in September 2021
05/08/2021 18:09 - Phishing: the most common credential theft attempts in August 2021...
01/07/2021 15:58 - Phishing: the most common credential theft attempts in July 2021
07/06/2021 16:44 - Phishing: the most common credential theft attempts in June 2021...
.
Try Vir.IT eXplorer Lite
 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Vir.IT eXplorer Lite has the following special features:
- freely usable in both private and corporate environments with Engine+Signature updates without time limitation;
- interoperable with any other AntiVirus, AntiSpyware, AntiMalware or Internet Security already present on PCs and SERVERs. We recommend to use it as a supplement to the AntiVirus already in use as it does not conflict or slow down the system but allows to significantly increase security in terms of identification and remediation of infected files
- it identifies and, in many cases, even removes most of the viruses/malware actually circulating or, alternatively, allows them to be sent to the C.R.A.M. Anti-Malware Research Center for further analysis to update Vir.It eXplorer PRO;
- through the Intrusion Detection technology, also made available in the Lite version of Vir.IT eXplorer, the software is able to report any new-generation viruses/malware that have set in automatically and send the reported files to TG Soft's C.R.A.M
- proceed to download Vir.IT eXplorer Lite from the official distribution page of TG Soft's website.
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
VirIT Mobile Security, the Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer).
 TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can pick up the Lite version, which can be freely used in both private and business settings.
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can pick up the Lite version, which can be freely used in both private and business settings.
You can upgrade to the PRO version by purchasing it directly from our website: https://www.tgsoft.it/italy/ordine_step_1.asp
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center that allowed us to make this information as complete as possible.
How to send suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
- Any suspect email can be sent directly by the recipient's e-mail, to the following mail lite@virit.com,choosing as sending mode "Forward as Attachment" and inserting in the subject section "Possible phishing page to verify" rather than "Possible Malware to verify"
- Save the e-mail to be sent to TG Soft's C.R.A.M. for analysis as an external file to the e-mail program used. The resulting file must be sent by uploading it from the page Send Suspicious Files (http://www.tgsoft.it/italy/file_sospetti.asp). Obviously if you want a feedback on the analysis of the data submitted, you have to indicate an e-mail address and a brief description of the reason for the submission (for example: possiible / probable phishing; possible / probable malware or other).
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)


 If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS. TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can pick up the Lite version, which can be freely used in both private and business settings.
TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can pick up the Lite version, which can be freely used in both private and business settings. For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis