As of 2nd February 2016,
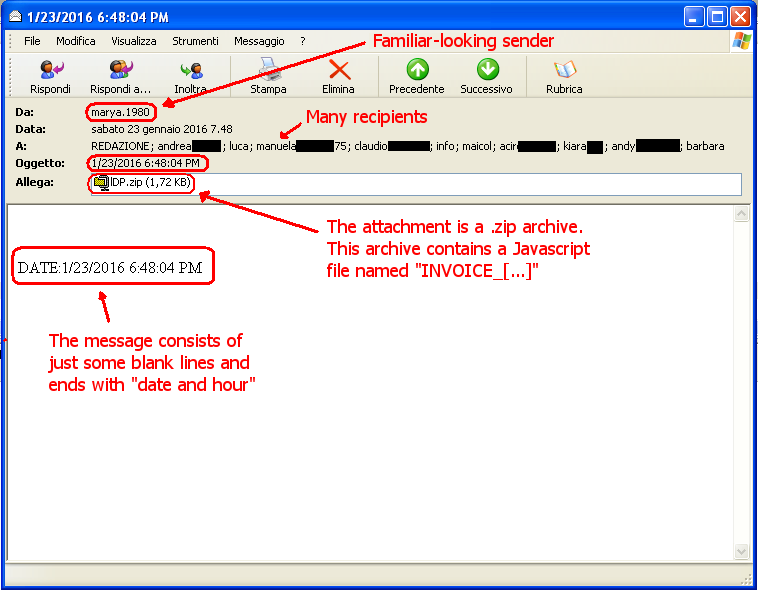
TeslaCrypt 3.0 attack is still going on. A huge amount of emails containing the malware has been delievered; these emails bear these subjects:
- Sender's name;
- Date and hour;
- Hi.
The body contains various blank lines, the last one quotes date and hour. There is also an attachment, a .zip file, its name being 3 random characters; inside, there is a javascript file, its name being similar to the following:
- invoice_SCAN_qH7le.js;
- invoice_copy_StXQDm.js;
- invoice_GavJVj.js;
|
Click here to show the picture fullscreen |
TeslaCrypt 3.0 was first recorded on 25th January; then, between 30th and 31st January, a huge number of users were sent a mail like the one described above, and considering this email reliable they opened and executed the attachmen - then hell broke loose.
The ransom demanded by TeslaCrypt 3.0
TeslaCrypt 3.0 demands a ransom to have data decrypted - the equivalent of 500 USD in BitCoin for every key. This means that if the user reboots the computer
n times, files are going to be encrypted with
n+1 different keys, so the amount of money that will have to be paid to have all files decrypted will be 500*(
n+1). For exapmple: 2 reboots, 3 keys → 3*500 = 1'500 USD in BTC.
How to stay safe from TeslaCrypt 3.0
One should never forget that links and email attachments could hide viruses/malwares. This rule applies to emails coming from unknown addresses, but also to apparently familiar ones from which an email with attachment (such as an invoice) was not expected.
Vir.IT eXplorer PRO users have a great chance to save all their data from encryption!
It was stated in our previous bulletins that
Vir.IT eXplorer PRO's
Anti-CryptoMalware module was able to stop these attacks saving up to 99.63% of files, allowing a
complete recovery of encrypted files thanks to backup technologies, namely:
- On-The-Fly Backup;
- Vir.IT BackUp.
This only occurs if Vir.IT eXplorer PRO is:
- correctly INSTALLED;
- UP-TO-DATE;
- properly CONFIGURED - Anti-Crypto Malware technology has to be active in the Settings tab of Vir.IT Security Monitor (it is active by default); plus Vir.IT BackUp has to be configured and running.
Starting with version 8.0.98, Vir.IT eXplorer PRO can "snatch" TeslaCrypt 3.0 encryption key on-the-fly in the early stages of the attack, thus making a decryption feasible - it can be done with the assistance from TG Soft's tech support.
Remember - every time the malware is executed, a new encryption key is used. This means that every time the computer is rebooted and the malware is still active, TeslaCrypt will use a different key (n reboots → n+1 different keys).
How to contain damage
Since a new key is created every time the malware is executed - which only happens when the computer is rebooted - the computer should always stay turned on, in order to have the minimun number of keys possible, and qualified tech support (such as TG Soft's) should be contacted immediately.
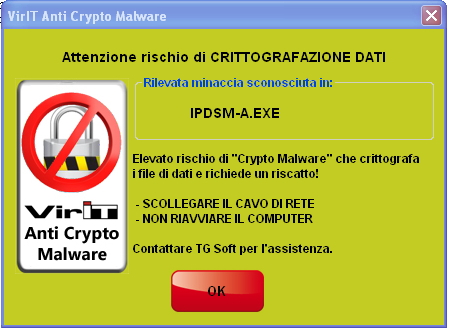
When the Alert shown in the picture pops up on the screen, Vir.IT eXplorer PRO's Anti-CryptoMalware module has come into action, halting the malware. Do not panic and perform these operations:
- Make sure that Vir.IT eXplorer PRO is UP-TO-DATE;
- UNPLUG EVERY NETWORK CABLE - by doing this, the computer will be phisically isolated from the network, thus containing the attack to just one machine.
- PERFORM a FULL SCAN using Vir.IT eXplorer PRO.
- DO NOT REBOOT OR TURN OFF THE COMPUTER in order to avoid further encryption, as stated before.
In case of cryptomalware attack you should get in touch with Vir.IT eXplorer PRO's Tech Support as soon as possible. You can write an email to assistenza@viritpro.com,
or call our hotlines:
- +39 049 631748
- +39 049 632750
Mon-Fri 8:30-12:30 and 14:30-18:30.
|
Click to show the picture fullscreen
99,63%*
Mean percentage of files protected from encryption thanks to Vir.IT eXplorer PRO ==>
|
Can .micro encrypted files be decrypted?
Yes, if
Vir.IT eXplorer PRO was correctly set up before the attack and it snatched encryption keys.
Final thoughts
Please remain calm and be patient. This is a very widespread emergency - many people were tricked into opening the email by the
familiar-looking sender address.
TG Soft
Public Relations


