
18/02/2016
15:50

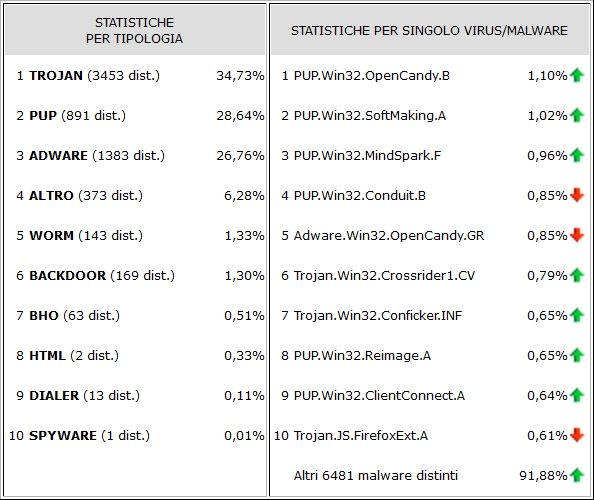
| The C.R.A.M. (Anti-Malware Research Center) of TG Soft has released statistics of actually circulating virus / malware in January 2016 in Italy. Let's find out what are the families and variants of malware that infected users' PCs. |  |
 Click to enlarge |
Analyzing the statistics shown on the left you can see how the Trojan family is definitely the most widespread malware family and right after, as for many months now, there are two categories that include advertising programs: ADWARE and PUP. Too often we trust websites considered "safe" that distribute software. |
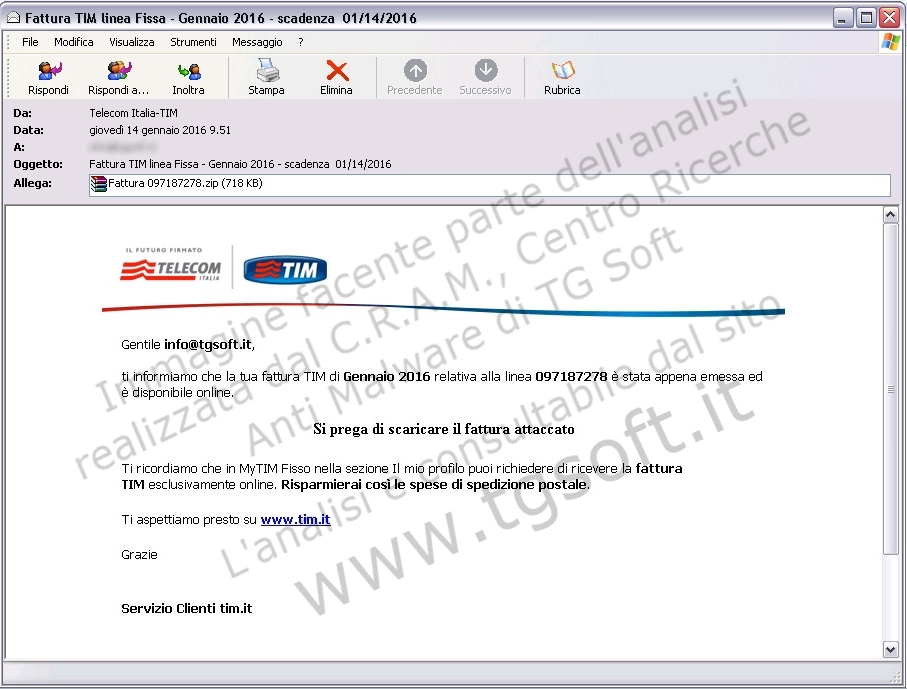
1) 14-01-2016 -> "False email TELECOM Italia-TIM unleashes new variants of CTB-Locker to encrypt the data files of the PC / SERVER and demand ransom!"
2) 19-01-2016 -> "New year ... old friends ... CryptoLocker is back!"
3) 25-01-2016 -> "First cases of the new TeslaCrypt 3.0 in Italy."
4) 01-02-2016 -> "Black Monday: new massive attacks by TeslaCrypt 3.0" that even if dated the first day of February, sending massive emails is occurred between the last days of January and early February.
The many CRYPTOMALWARE variants are not present in the ranking because most deletes its executable file, guilty of encryption, at the end of the procedure to prevent its detection.
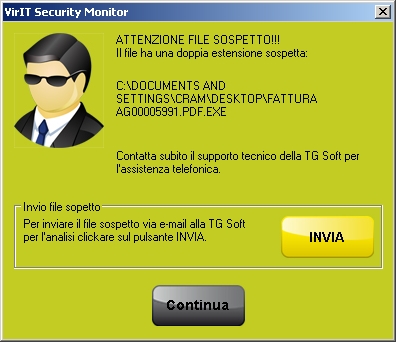
| To the right you can see the code into javascript that were sent as email attachments scam. The malicious javascript, intercepted by Vir.IT eXplorer PRO as Trojan.JS.Dropper.BA, downloads the Teslacrypt, in the example 80.exe file and saves it in the %TEMP% directory where there are saved to the user's temporary files. Then it is renamed with the name contained in the "FILE_NAME" variable and finally runs. The file name of the javascript, content as an email attachment was composed of: invoce_scan_<randomstring>.js invoice_copy_<randomstring>.js invoice_<randomstring>.js |
Among the really circulating virus / malware that spread via email in this month C.R.A.M. TG Soft has analyzed numerous incidents of scam emails containing fake attachments (such as invoices, delivery notes etc ...). We analyze the reports arrived
| As we can see from ranking of the most widespread viruses / malware in January 2016, in first place, we find the W97M.Downloader.AZ, macro contained inside a fake Word document passed off invoice. Following we find the infected macros always inside fake Excel documents, X97M/Downloader.H and W97M/Generic.K, some cryptomalware as Trojan.Win32.CTBLocker.BK e Trojan.Win32.CryptLocker.EA. The C.R.A.M. di TG Soft has already analyzed these cryptomalware also during the same month. |
 Click to enlarge |
 |
| We point out that all the viruses / malware actually circulating are identified and, in many cases, also removed from Vir.IT eXplorer Lite -FREE Edition- that TG Soft makes freely used by both individuals both within the company. Vir.IT eXplorer Lite is interoperable with other AntiVirus already on your computer, without having to uninstall, and then allowing the cross-check that nowadays is no longer a whim, but a necessity. Go to the download page. |  |